By: Brij B. Gupta, Department of Computer Science and Information Engineering, Asia University, Taichung 413, Taiwan.
Secure Coding Practices You Need Today refers to the essential strategies and methodologies developers must adopt to enhance the security of their software applications throughout the development lifecycle. As cyber threats grow increasingly sophisticated, understanding and implementing secure coding practices has become critical to protect user data and maintain organizational integrity. This topic is particularly notable as the economic and reputational conse- quences of security breaches can be devastating, leading to substantial financial losses, regulatory fines, and erosion of customer trust.[1][2][3]
At the core of cyber hygiene is the awareness of common security vulnerabilities, such as Cross-Site Scripting (XSS), SQL injection, and insecure deserialization, that can compromise application security.[2][4] Developers must actively engage in practices such as input validation, robust authentication and authorization, and proper error handling to mitigate these risks. By prioritizing secure coding from the outset, organizations can significantly reduce the likelihood of vulnerabilities emerging in production environments.[3][5]
Key to successful secure coding is the adoption of comprehensive training pro- grams that promote a culture of security awareness among development teams. Furthermore, leveraging automated security tools and integrating security testing within the Continuous Integration/Continuous Deployment (CI/CD) pipeline are vital to maintaining a proactive security posture.[6][7] Such measures not only fortify applications against potential threats but also streamline the development process, reducing costs associated with post-release vulnerabilities.[8]
Despite the clear benefits of secure coding practices, many organizations still grapple with implementing these measures effectively. Controversies surrounding the bal- ance between rapid development and stringent security protocols persist, as some developers may view security requirements as impediments to productivity.[2][4]
However, embracing a security-focused mindset can lead to greater efficiency and innovation in the long run, making secure coding an indispensable aspect of modern software development.
Common Security Vulnerabilities
Cyber hygiene for developers encompasses an understanding of common security vulnerabilities that can compromise applications. Developers must be vigilant about these vulnerabilities to ensure the security of their software.
Cross-Site Scripting (XSS)
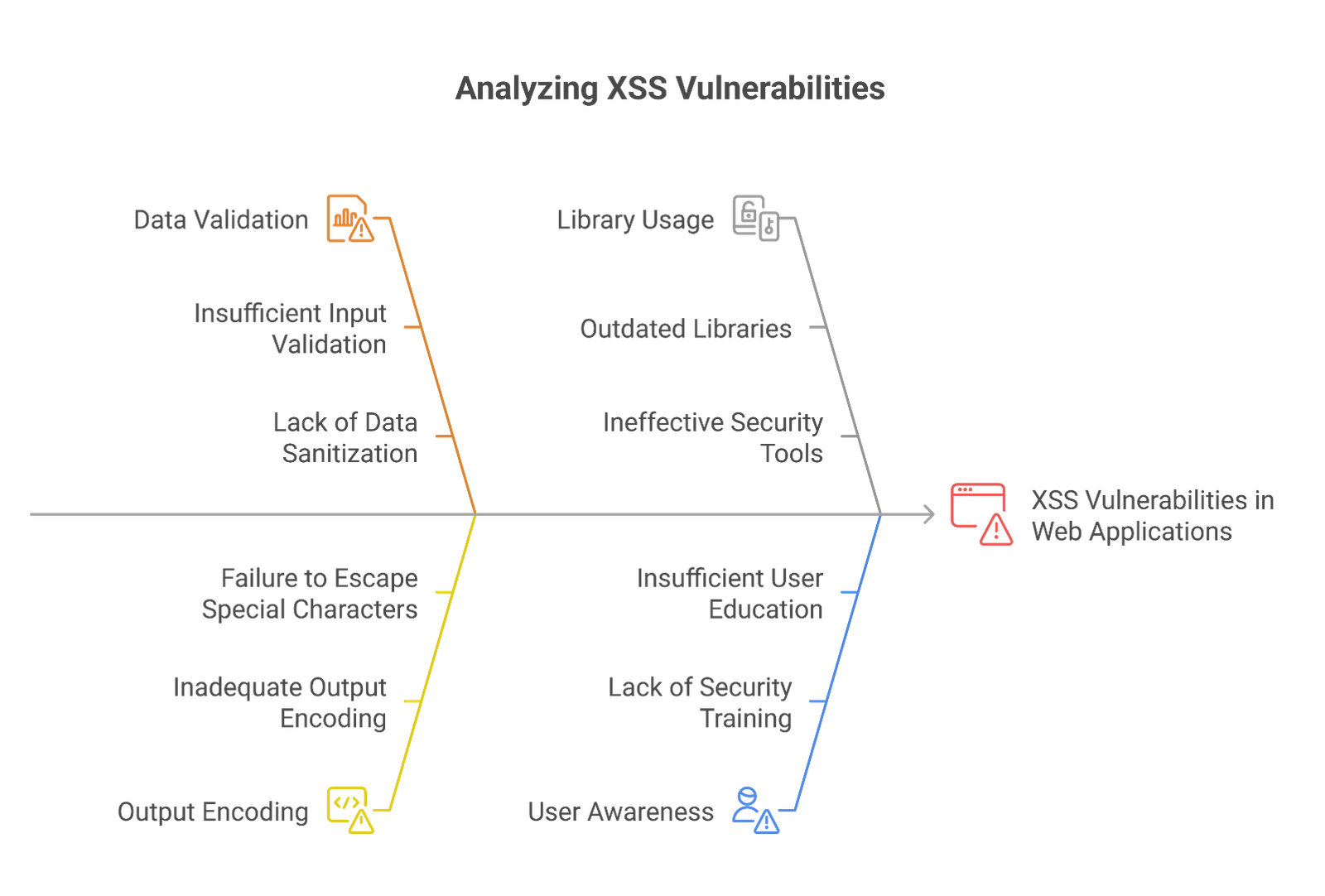
Cross-Site Scripting (XSS) is a critical web security vulnerability that allows attackers to inject malicious scripts into web pages viewed by users. XSS vulnerabilities arise from failing to validate or encode untrusted data. The consequences of successful XSS attacks can include session token theft, credential manipulation, and the dis- tribution of malware. Preventative measures include proper output encoding, input validation, and using libraries designed to mitigate XSS risks.[1]
Insecure Deserialization
Insecure deserialization is a risk particularly associated with Java’s native serialization mechanism, which can lead to remote code execution if untrusted data is processed. Developers are advised to avoid using native serialization with untrusted input and instead opt for safer formats, such as JSON, alongside secure libraries.[2]
Security Misconfiguration
Security misconfigurations are common vulnerabilities that arise from insufficient security controls or improper system settings. This includes failing to log critical security events, inadequate monitoring, and exposing sensitive data through un- secured configurations. To mitigate these issues, developers should implement a comprehensive logging and monitoring strategy, ensuring logs are protected from unauthorized access.[2]
Injection Vulnerabilities
Injection vulnerabilities, such as SQL, Command, and LDAP injection, remain prevalent threats in web applications. These flaws occur when untrusted input is executed as part of a command or query. To mitigate these risks, developers should utilize safe programming practices, such as using for SQL queries and employing safe APIs for executing operating system commands.[2]
Dependency Vulnerabilities
The reliance on third-party libraries (JARs) introduces potential security risks. Developers must regularly update these dependencies and utilize tools such as OWASP Dependency-Check to scan for known vulnerabilities. Keeping libraries up to date is crucial for minimizing risks associated with dependency vulnerabilities.[2]
CSRF Attacks
Cross-Site Request Forgery (CSRF) attacks exploit the authenticated session of a victim, allowing unauthorized actions to be performed on behalf of the user. To prevent CSRF, developers should generate cryptographically secure tokens tied to the user’s session and validate them on the server side. Setting the attribute for cookies can also help limit exposure to such attacks.[1]
Economic and Reputational Impact
The implications of insecure code are significant, often leading to substantial finan- cial losses from remediation costs, regulatory fines, and reputational damage. The expense of addressing security flaws after deployment can be up to 100 times greater than addressing them during the design or coding phases. Additionally, breaches can erode customer trust and damage brand reputation, making the case for rigorous secure coding practices even more compelling.[2]
Secure Coding Practices
Secure coding practices are essential guidelines that developers follow to create soft- ware that is robust, reliable, and resistant to vulnerabilities and cyber threats.[3][4]. These practices encompass a variety of techniques and methodologies aimed at enhancing the security of applications throughout the software development lifecycle.
Key Practices
Input Validation
One of the foundational elements of secure coding is validating user input. Developers must ensure that all incoming data is scrutinized for syntactic and semantic correctness, treating it as untrusted. This includes validating HTTP headers, cookies, GET and POST parameters, and file uploads on the server side.[5] Client-side validation can also improve user experience but should not be relied upon as the sole line of defense.
Authentication and Authorization
Implementing robust identity verification and access controls is critical. Authentication confirms that users are who they claim to be, while authorization governs what actions they can perform within the application. Strong mechanisms such as multi-factor authentication and secure password storage are vital for protecting sensitive information and maintaining the integrity of the application.[6][7].
Data Protection
Data protection techniques, including encryption for both data at rest and in transit, are essential for safeguarding sensitive information. Developers should utilize established cryptographic libraries and implement proper key management practices to prevent unauthorized access.[1][7] Additionally, parameterized queries should be used to protect against SQL injection attacks by avoiding direct concatenation of user inputs in SQL commands.[6].
Error and Exception Handling
Effective management of errors and exceptions is crucial to prevent inadvertent information exposure that could be exploited by attackers. It is advisable to centralize error handling, avoid logging sensitive data, and regularly review the implementation to identify vulnerabilities. Employing techniques such as negative testing can also help in identifying potential weaknesses in error handling.[1].
Logging and Monitoring
Establishing comprehensive logging and monitoring mechanisms allows developers to detect and respond to security incidents proactively. Logs should not expose sensitive information and should be retained according to defined policies. Implementing alert systems to flag unusual activities can help in quickly identifying and mitigating potential threats.[1][7].
Encoding and Sanitization
Encoding data plays a significant role in protecting against injection attacks such as SQL injection and cross-site scripting (XSS). Developers should apply context-specific encoding techniques and utilize libraries that automatically handle output encoding to mitigate risks associated with untrusted data.[6][7].
By adopting these secure coding practices, developers can significantly reduce vulnerabilities and enhance the overall security posture of their applications, ensuring better protection for user data and organizational assets in an increasingly sophisti- cated threat landscape.[4][5][7].
Tools and Resources
Collaboration Platforms
Effective communication is crucial for successful software development.
Slack: Widely recognized as a leading team communication platform, Slack offers integrations with numerous development tools, facilitating seamless collaboration among team members[8].
Microsoft Teams: This platform combines chat, video meetings, and document collaboration, making it particularly beneficial for enterprise environments[8].
Project Management Tools
Managing tasks and projects efficiently is vital for maintaining productivity in development teams.
Jira: A robust option for Agile teams, Jira provides features for sprint planning, backlog management, and reporting, making it suitable for complex project environments[8].
Trello: Known for its simplicity and visual approach, Trello is ideal for smaller teams or less complex projects, allowing for easy task tracking[8].
Asana: Focused on task management and workflow automation, Asana offers a clean interface that helps teams stay organized and on track[8].
Security Testing Tools
Incorporating regular security testing into the development lifecycle is essential for identifying and mitigating vulnerabilities:
Static Application Security Testing (SAST): Tools like SonarQube and Checkmarx analyze source code for vulnerabilities before deployment, flagging issues such as hardcoded passwords and unsafe dependencies[8]. Integrating SAST into CI/CD pipelines ensures continuous security assessment without hindering developer pro- ductivity[9].
Dynamic Application Security Testing (DAST): Tools such as Burp Suite and OWASP ZAP simulate real attacks on running applications to uncover vulnerabilities like SQL injection or XSS, ensuring robust defenses against external threats[8].
Dependency Scanning: Regular scanning of third-party libraries with tools like Dependabot or Snyk can help maintain security by promptly identifying outdated or vulnerable dependencies[8][9].
Knowledge Sharing and Code Review
Establishing a culture of knowledge sharing through code reviews enhances code quality and team collaboration. This process allows developers to catch errors early, promote consistency, and foster mentorship opportunities among team members[8].
By leveraging these tools and resources, development teams can significantly enhance their cyber hygiene practices, ultimately leading to more secure software applications.
Best Practices for Developers
Overview of Secure Coding
Secure coding practices are essential in ensuring that software applications are robust and trustworthy. By integrating security measures throughout the software development lifecycle (SDLC), developers can mitigate vulnerabilities and enhance the overall security posture of their applications[8][1]. This proactive approach not only protects applications from threats but also reinforces the trust between users and businesses[1].
Training and Education
One of the most effective ways to promote secure coding is through comprehensive training programs for developers. Regular training sessions can help cultivate a security-conscious mindset within teams, enabling them to recognize and address security risks effectively during development[10][11]. Additionally, appointing security champions within Agile and DevOps teams fosters collaboration and communication between security and development, ensuring that security considerations are incorporated into the project from the outset[11][12].
Code Quality and Static Analysis
Enforcing code quality gates using tools such as static analysis software can help identify potential security issues before they reach production. This practice encour- ages developers to adopt secure coding standards consistently, which minimizes the risk of vulnerabilities[8][1]. By implementing these measures, teams can ensure that only clean, maintainable code is deployed, thus improving software quality and reducing costs associated with post-release fixes.
Agile Development and Iterative Improvements
Adopting Agile methodologies allows for flexibility and responsiveness to changing requirements. Through iterative development and small batch deployments, teams can deploy incremental updates regularly, which not only lowers risk but also facil- itates streamlined feedback loops from users[8][13]. This approach enables developers to course-correct swiftly and enhances collaboration among cross-functional teams, breaking down silos between development and operations[13][11].
Threat Modeling and Risk Management
Integrating threat modeling into the development process enables teams to identify and prioritize potential security risks proactively. By understanding the threats their applications may face, developers can implement appropriate security controls and safeguards[11][12]. A holistic approach to Developer Risk Management focuses on code contributors and encourages a culture of accountability within the development team[14].
Automated Security Practices
Automating security within the CI/CD pipeline can significantly enhance the secure development lifecycle. Tools like Infrastructure as Code (IaC) enable the automated provisioning and configuration of secure infrastructure, ensuring that security controls are consistently applied across environments[11]. This integration allows developers to focus on creativity and innovation rather than firefighting, ultimately leading to faster delivery and reduced costs[8][10].
Continuous Learning and Engagement
To maintain a strong security posture, organizations should foster a culture of continuous learning. Regularly scheduled training and engaging methods such as tournaments can help keep developers motivated and informed about the latest security practices[10]. By measuring the success of these training programs through metrics like knowledge gain, teams can continually adapt and improve their secure coding practices[10][12].
Case Studies
Importance of Secure Coding Case Studies
Case studies in secure coding provide valuable insights into real-world applications of secure coding practices and the implications of security vulnerabilities. They illus- trate how organizations have faced and mitigated security threats, thereby serving as educational tools for developers to understand the importance of incorporating security measures into their coding processes. By analyzing these cases, developers can learn about the potential risks associated with insecure coding and the consequences of failing to implement best practices[1][15].
Key Examples and Lessons Learned
Example of a Security Breach
One notable case involves an e-commerce platform that stored user passwords in plain text. A data breach exposed its database, compromising usernames and passwords, which could then be exploited due to users reusing credentials across
multiple platforms. This incident highlighted the critical importance of secure password storage practices, such as proper hashing and encryption, as well as the necessity of robust user authentication mechanisms[1][6].
Successful Implementation of Secure Coding
Conversely, another case illustrates the successful implementation of secure coding practices within a financial institution. By adopting a secure development lifecycle, the organization prioritized regular vulnerability assessments and penetration testing. This proactive approach helped the institution identify and remediate vulnerabilities early in the development cycle, ultimately preventing potential security breaches.
The case underscores the effectiveness of integrating security practices into the development workflow and prioritizing high-risk code segments[15][2].
Continuous Learning and Adaptation
Studying secure coding case studies enables developers to stay updated on industry trends and emerging threats. By reflecting on these real-world scenarios, they can enhance their problem-solving and decision-making skills, ensuring they are better equipped to address security challenges in their own projects. Moreover, these case studies facilitate ongoing professional development, as teams engage in discussions about lessons learned and best practices derived from these experiences[16][17].
References
- : Secure Coding: Top Risks, Best Practices, and Techniques – Jit.io
- : Secure Coding Practices Guide: Principles, Vulnerabilities, and …
- : Secure Coding: Learn the Fundamentals and Best Practices Today
- : Best Practices for Secure Coding in Web Applications
- : 10 Secure Coding Practices You Can Implement Now
- : Secure Coding Best Practices – CloudRaft
- : Secure Code Reviews: Checklist for Developers – Jit.io
- : Software Development Best Practices: From Agile to Secure Coding
- : Secure Software Development: What It Is and Best Practices [10]: The Admin’s Guide to Secure Coding Training Success
- : Implementing Secure Coding Practices in Agile and DevOps … – Xcidic
- : Software Security Coding Courses
- : DevOps Success Stories: Real-Life Case Studies | Attract Group
- : Secure Code Warrior: Secure Code Learning for Developers
- : What are the best practices for secure data transmission in web …
- : Top Agile Case Studies: Examples Across Various Industires
- : Real-World DevOps Case Studies: Success Stories
- Deveci, M., Pamucar, D., Gokasar, I., Köppen, M., & Gupta, B. B. (2022). Personal mobility in metaverse with autonomous vehicles using Q-rung orthopair fuzzy sets based OPA-RAFSI model. IEEE Transactions on Intelligent Transportation Systems, 24(12), 15642-15651.
- Gupta, B. B., Li, K. C., Leung, V. C., Psannis, K. E., & Yamaguchi, S. (2021). Blockchain-assisted secure fine-grained searchable encryption for a cloud-based healthcare cyber-physical system. IEEE/CAA Journal of Automatica Sinica, 8(12), 1877-1890.
- Nguyen, G. N., Le Viet, N. H., Elhoseny, M., Shankar, K., Gupta, B. B., & Abd El-Latif, A. A. (2021). Secure blockchain enabled Cyber–physical systems in healthcare using deep belief network with ResNet model. Journal of parallel and distributed computing, 153, 150-160.
Cite As
Gupta B.B. (2025) Cyber Hygiene for Developers Secure Coding Practices You Need Today, Insights2Techinfo, pp.1