By: Rekarius, Asia University, Taiwan
Abstract
Phishing email attack are a type of cybersecurity attack where the attacker contacts a potential victim by sending them an email that makes them think it came from a reliable source. With the use of generative AI, attackers may quickly produce a wide variety of human-looking emails. Even when delivered to a vast number of recipients, the messages are no longer the same or repetitious, which makes spam identification more challenging. According to the analysis, there are noticeable differences between emails produced by AI and those sent by humans; in fact, machine learning is very good at spotting phishing emails produced by AI. All of the results are statistically significant. AI-generated phishing emails are distinct from both manually created phishing scam emails and regular emails. Some of the specific traits that show how emails generated by generative AI are distinct from those written by humans in that the former have a different basic writing style can be profiled.
Keyword Phishing, Artificial Intelligence, Email
Introduction
Phishing email attack are a type of cybersecurity attack where the attacker contacts a potential victim by sending them an email that makes them think it came from a reliable source [3]. This attack exploit human vulnerabilities through deceptive emails, tricking users into disclosing sensitive information such as passwords, financial details, or personal data [5].
Traditional Phishing Detection Techniques. Early phishing detection methods relied heavily on heuristic-based and rule-based techniques manually configured to detect specific phishing patterns. These systems focused on identifying suspicious URLs, misspelt domain names, or deceptive email keywords [6].
Machine Learning for Phishing Detection.
Machine learning models, mainly supervised learning techniques, are trained on large datasets containing phishing and legitimate samples. By learning the distinguishing features of phishing emails, websites, or messages, these models can predict the likelihood of a phishing attempt based on new, unseen data [7].
Deep Learning in Phishing Detection.
Recurrent neural networks (RNNs) and convolutional neural networks (CNNs) have been success fully applied to phishing detection tasks. For instance, CNNs have been used to analyse the visual representation of phishing websites, identifying subtle differences between legitimate and fraudulent websites based on pixel patterns and layout structures [1]. Similarly, RNNs have been employed to detect phishing emails by analysing the sequential nature of email content, such as the flow of text and metadata [2].
While Generative AI has substantial useful applications, in some cases that technology can be used for malicious purposes. Given that phishing email assaults are typically carried out by sending un- solicited emails to finding a big number of identical emails in the mail server received in a comparatively short period of time is one method of protecting against phishing emails. time frame. Although that method is popular, generative artificial intelligence (AI) can be used to avoid recognizing emails that are identical or strikingly similar that have been sent repeatedly from outside sources. With little effort on the part of the attacker, generative AI tools can produce various email messages that appear to have been written by a human but were actually created by a machine. As a result, they can be distributed to a huge number of recipients. It is also more difficult for spam detection systems to detect repetitive emails sent from an outside source to a big number of recipients when an attacker has the ability to generate a large number of distinct email messages in order to avoid utilizing the same or similar email message. This paper discusses the problem of a phishing email attack that uses generative AI to create a large number of different emails automatically.
Methodology
This study [3] proposes a novel email corpus that is unique in the sense that the phishing emails were generated by AI. To study the ability of automatic text analysis to identify AI-generated phishing emails, several different text analysis approaches are tested.
Data
This research [3], To train and test machine learning model, a sufficiently large dataset of AI-generated phishing emails is required. To create a sufficiently large dataset of AI-generated phishing emails, the API of the DeepAI platform was used. DeepAI is enabled by OpenAI, and provides the API that allows the automation of the generation of large numbers of text files. The emails in the dataset are in plain text format. The average length of each email is 545 characters, where the longest email is 1810 characters and the shortest email is 280 characters long.
Methods
Machine Learning for Language Toolkit (MALLET)
MALLET is a well-established open-source topic modeling software program that is frequently used for automatic document classification. MALLET uses machine learning algorithms to allow the automatic classification of text documents into classes. Tokenization and stop word removal are the next steps in MALLET’s process, which starts with text segmentation to identify the various sections of the document.
Then, lemmatization is used to identify the parts of speech of each word. This makes it possible to create a dictionary, and the feature space is determined by how frequently dictionary words appear in each document. Following the creation of the feature space, the classification is done using a machine learning method. MALLET, a classifier that uses topic modeling, is able to recognize variations in word usage. when an AI-generated email is contrasted with one penned by a human. Table 1 shows the confusion matrix of the classification when using the Naive Bayes classifier.
AI-Generated | Enron | Ling-Spam | Nigerian Phishing | |
AI-generated | 99 | 1 | 0 | 0 |
Enron | 0 | 99 | 1 | 0 |
Ling-Spam | 0 | 1 | 99 | 0 |
Nigerian phishing | 1 | 2 | 0 | 97 |
Table 1: Confusion matrix of the classification results of the AI-generated emails, the Enron emails, the manually crafted Nigerian phishing scam emails, and Ling-Spam emails when using MALLET and Naive Bayes classifier. The values are in percentage.
Universal Data Analysis of Text (UDAT)
UDAT is based on the analysis of style elements such as the use of parts of speech, repetition of parts words, punctuation, and more [3]. UDAT is a non-parametric method that uses a comprehensive set of descriptors extracted from the text. summary, these include the distribution of the lengths of the words, diversity of the words appearing in the text, changes in the frequency of words throughout the document, use of punctuation characters, use of upper case letters, frequency and length of quotations, use of emoticons, distribution of sentence length, use of numbers in the text, distribution of sounds as reflected by the Soundex algorithm, readability index, distribution of parts of speech, repetitive patterns in the use of parts of speech, and analysis of the sentiments and their distribution throughout the document.
UDAT is able to recognize variations in the text’s style elements. Therefore, even if the distribution of topics and words in the emails makes it difficult to identify the phishing emails, UDAT will be able to recognize AI-generated phishing emails if they contain particular stylistic elements that set them apart from emails written by humans. In order to give a more thorough defense, such analysis can be employed in conjunction to MALLET’s word-based analysis. One of UDAT’s benefits is that it offers a distinctive style aspect that sets the classes apart.
Deep Neural Network
The neural network is relatively simple, and based on the common Long Short Term Memory (LSTM) architecture [4]. The first layer is an embedding layer with the maximum number of words set to 20,000, the maximum sequence length set to 50, and 100 embedding dimensions. That layer is followed by LSTM with an input size of 100 and dropout and recurrent dropout both set to 0.2. The activation function is tanh, and the recurrent activation function is sigmoid.
The loss function was the common Categorical Crossentropy, and the Adam optimizer was used for training. The last layer is a fully connected layer with softmax activation. The methods were used by randomly allocating 600 text samples from each class for training, and 100 for testing. The analysis was conducted with 10-fold cross-validation.
The evaluation of the results was determined by classification accuracy, precision, recall, and F1. In addition to these methods, an ensemble method was used. The ensemble classifier was made of the deep neural network described above, UDAT, and MALLET with Naive Bayes classifier. The final classification was made by a simple majority rule. That makes a single text classifier made of three different text classifiers such that each one uses a different text analysis approach.
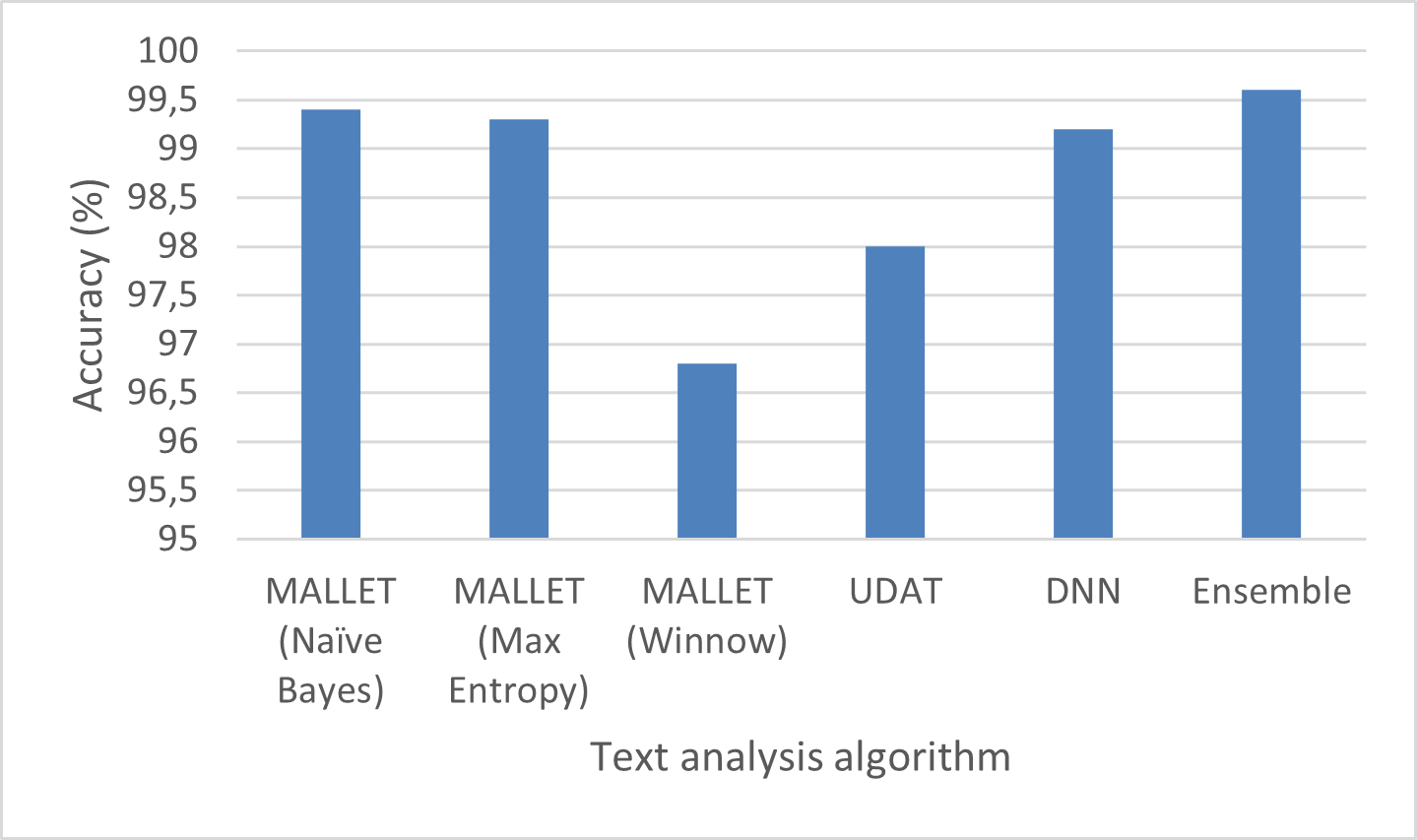
Results Three separate machines are used while classifying between the four classes using MALLET. The Winnow, maximal entropy, and Naive Bayes learning algorithms were employed. With the Naive Bayes classifier, the classification accuracy was 99.3%, and with the Maximum 97% using Winnow as a classifier, and 97% using an entropy classifier.
When the four classes are classified using UDAT, the classification accuracy is 98% (p ¡ 105). yielding an F1 of 0.985 with a recall of 1 and precision of 0.97. The AI-generated phishing emails were classified using an artificial neural network, which distinguished them from the other classes. Like the other approaches, this one has a high classification accuracy. The accuracy of the classification between Nigerian phishing fraud and AI-generated phishing emails is 100% (p ¡ 105). The classification accuracy of 99%, recall of 0.99, precision of 0.98, and F1 of 0.985 are achieved while distinguishing between the AI-generated phishing emails and emails from the Enron corpus. Using the Ling-Spam corpus, the classification accuracy between AI-generated phishing emails and spam emails is 99% as well. The odds of witnessing such classification accuracy or strength by chance are always (p <105). Figure 1 shows the classification accuracy of the different algorithms that were tested.
Conclusion
Given that manually generated data is used to train generative AI, it may be assumed that phishing emails created by AI are comparable to those created by hand. However, the investigation reveals that there are discernible variations between human-generated and emails created by AI; in fact, machine learning is highly accurate at identifying phishing emails created by AI. Every outcome is statistically significant. Both manually-generated phishing scam emails and standard emails are not the same as AI-generated phishing emails. It is possible to profile some of the specific characteristics, which demonstrate that emails written by generative AI differ from those written by humans in that the former’s fundamental writing style is different.
References
- Alejandro Correa Bahnsen, Ivan Torroledo, Luis David Camacho, and Sergio Villegas. Deepphish: simulating malicious ai. In 2018 APWG symposium on electronic crime research (eCrime), pages 1–8, 2018.
- Vishal Borate, Alpana Adsul, Rohit Dhakane, Shahuraj Gawade, Shubhangi Ghodake, and Mr Pranit Jadhav. A comprehensive review of phishing at- tack detection using machine learning techniques. International Journal of Advanced Research in Science, Communication and Technology (IJARSCT), 4(3), 2024.
- Chibuike Samuel Eze and Lior Shamir. Analysis and prevention of ai-based phishing email attacks. Electronics, 13(10):1839, 2024.
- Sepp Hochreiter and Ju¨rgen Schmidhuber. Long short-term memory. Neural computation, 9(8):1735–1780, 1997.
- Oladimeji Azeez Lamina, Waliu Adebayo Ayuba, Olubukola Eunice Adebiyi, Gracious Ebunoluwa Michael, Ojo-Omoniyi Damilola Samuel, and Kesh inro Olushola Samuel. Ai-powered phishing detection and prevention. Path of Science, 10(12):4001–4010, 2024.
- Janice Y Tsai, Serge Egelman, Lorrie Cranor, and Alessandro Acquisti. The effect of online privacy information on purchasing behavior: An experimental study. Information systems research, 22(2):254–268, 2011.
- Rakesh Verma and Nabil Hossain. Semantic feature selection for text with application to phishing email detection. In international conference on in- formation security and cryptology, pages 455–468. Springer, 2013.
- Gupta, B. B., Gupta, S., Gangwar, S., Kumar, M., & Meena, P. K. (2015). Cross-site scripting (XSS) abuse and defense: exploitation on several testing bed environments and its defense. Journal of Information Privacy and Security, 11(2), 118-136.
- Negi, P., Mishra, A., & Gupta, B. B. (2013). Enhanced CBF packet filtering method to detect DDoS attack in cloud computing environment. arXiv preprint arXiv:1304.7073.
- Gupta, B. B., Gupta, S., & Chaudhary, P. (2017). Enhancing the browser-side context-aware sanitization of suspicious HTML5 code for halting the DOM-based XSS vulnerabilities in cloud. International Journal of Cloud Applications and Computing (IJCAC), 7(1), 1-31.
Cite As
Rekarius (2025) Email Phishing: An AI-Based System for Detecting Human- versus AI-Generated Emails, Insights2Techinfo, pp.1