By: C S Nakul Kalyan, CCRI, Asia University
Abstract
Systems like Facial recognition and authentication become vulnerable to biomet- ric attacks such as Face Morphing. The morphing attack, which is created by combining the facial features of many individuals, can easily trick many detec- tion systems, which comes under the category of identity fraud and other illegal activities. This article mainly focuses on the difficulties of detecting morphing attacks with respect to the variations in age, illumination, and the accessories in which the morphing techniques are unknown. To improve the detection performance, a deep learning -based Feature extraction framework is proposed in which is a combination of image enhancement and feature fusion. An adaptable dataset is developed using 8 Face datasets, which contain – Celebrity2000, Ex- tended Yale, FEI, FGNET, GT-DB, MULTI-PIE, FERET, and FRILL, which include both Morph-2 and Morph-3 images, which are generated through professional morphing tools. In addition, a morphing attack detection scheme that utilizes Photo Response Non-Uniformity (PRNU) analysis is added, which utilizes spatial and spectral features among the image cells to differentiate from morphed images. The experimental evaluations for this proposed approach give good results and perform well among several detectors in real-world conditions.
Keywords
Face Morphing, Identity Frauds, Photo Response Non-uniformity (PRNU), Morphing attacks, Deep Learning
Introduction
Facial recognition systems have become the main feature of modern authentication, since they provide quick and accurate identification verification for users, including border control, electronic passports, banking, and secure access management. However, these systems have been threatened by advanced biometric
attacks, where face morphing is said to be more severe among the other attacks [5]. This attack involves combining the facial features of 2 or 3 individuals into a single image in which will produce a biometric similarity to all the contributors [2]. When such a morphed image is used in the enrollment phase, such as a passport application, it can be easily accepted, and multiple individuals will be granted access by using a single identification document as shown in (Figure 1).
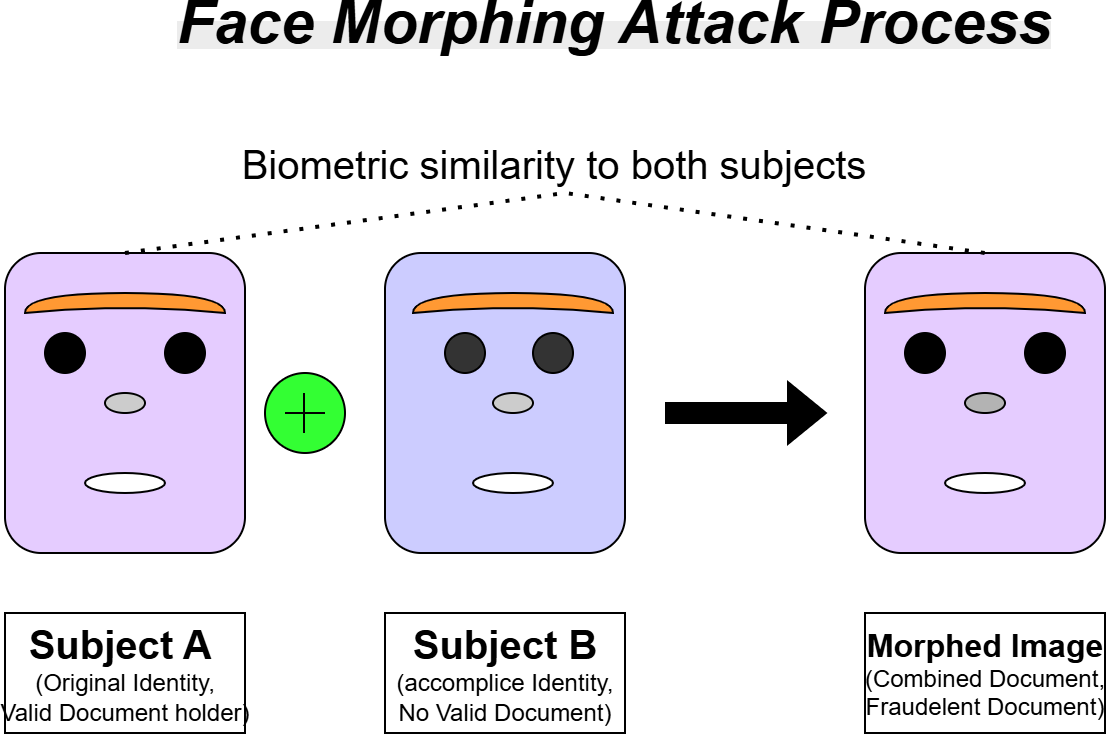
Regarding the real-world scenarios, the threat is more concerning. For ex- ample, if an individual may morph their image with their look-alike accomplice and they receive a travel document using the morphed image, both individuals can access the document to pass through the border control systems or even manual inspections, where this forgery breaks the basic principle of biometrics. By using the advanced morphing software, the risk is further amplified. The morphing attack can occur in both physical and digital workflows, such as when submitting the printed documents, the photos can be morphed before the printing and scanning process is done. And in some of the countries, the digital document submission is allowed, which allows the attackers to import morphed images into the portals without any direct verification. These difficulties are the reason to the introduction of creating Morphing Attack Detection (MAD) methods [1][5]. In this article, we will go through the risks of morphing in identity fraud and go through the various detection approaches for these modern authentication systems [3].
Proposed Methodology
The methodology for Detecting Morphing attacks in facial recognition includes a multi-stage pipeline as shown in (Figure 2) that consists of:
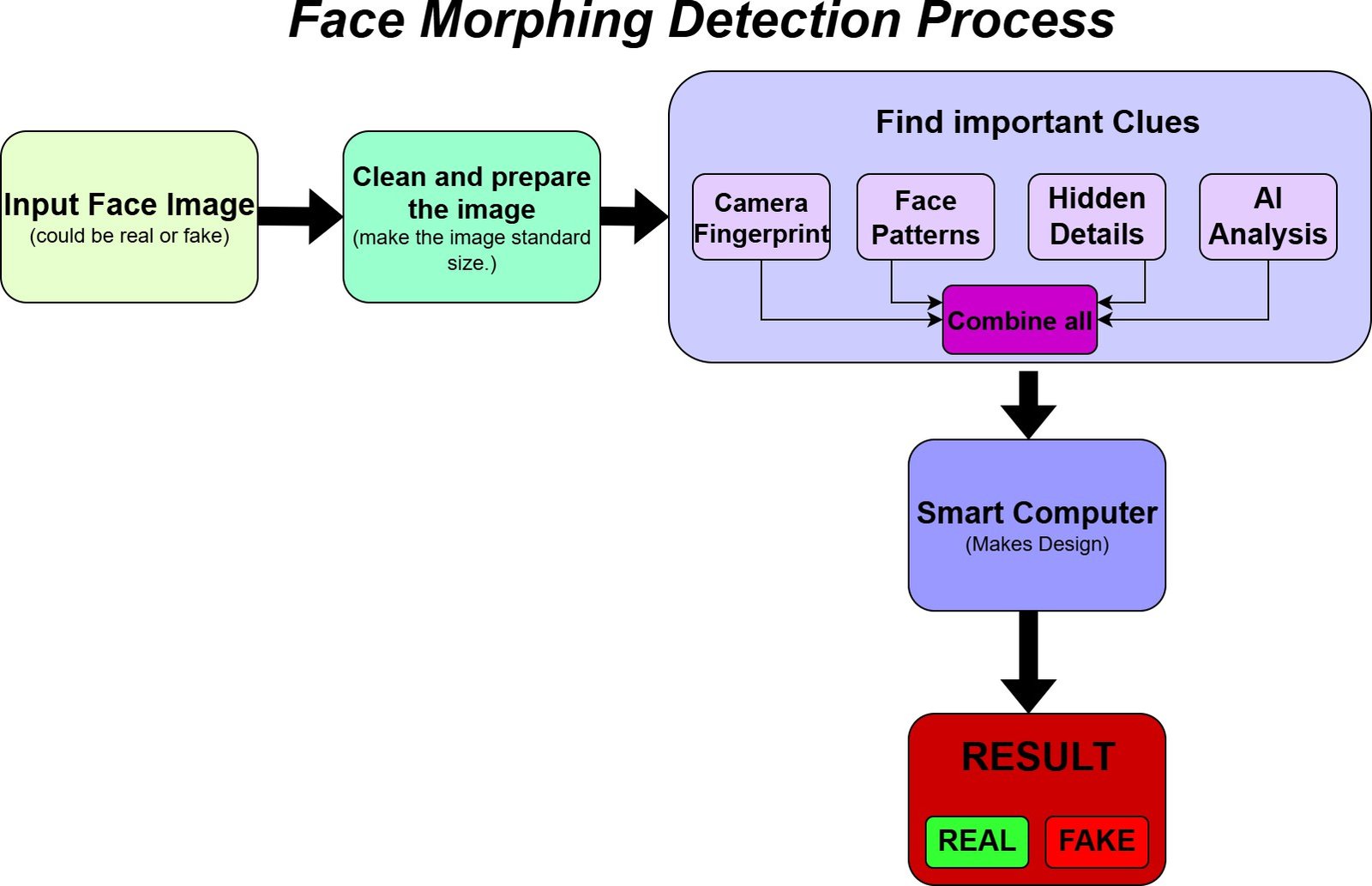
Dataset Selection
Three Datasets have been used for evaluating the robustness of the morphing attack detection framework, which consists of:
Morph 2 and Morph 3 Datasets
Contains digital facial images of high quality with Various combinations in pose, background lighting, and age, and it adds more Variations to test the robustness of the images under different conditions.
Printed-Scanned Morphed Dataset
This dataset will generate images by printing selected images and scanning them back to the digital format, which will be used in real-world document verification scenarios.
Image pre-processing
To ensure consistency and noise prevention, all the images have been pre- processed for Photo-Response Non-Uniformity (PRNU) extraction. The pre- processing Techniques will consist of:
Face alignment and cropping
In this technique, the facial marks have been identified, and the images have been placed in a fixed region around the face.
Image Normalization
In this technique, the Pixel intensities were normalized to reduce the brightness inconsistencies in the images.
Resizing
To match the input requirements of the Deep learning models, the images were resized to a uniform design to match them.
Feature Extractions
The Feature extraction Strategy is integrated to capture cues from facial, spec- tral, and noise residual domains, such as:
PRNU Based Features
From each image, the sensor noise patterns will be extracted to generate the PRNU signatures [4]. These extracted features help to detect the inconsistencies produced during the morph creation or printing-scanning.
Spatial and Spectral Domain Features
The Spatial domain will capture the tiny artifacts in facial regions in which the gray-level co-occurrence matrices (GLCM) and local binary Patterns (LBP) were calculated.
The Spectral domain will find the anomalies in the high frequency components, where the analysis is carried out using the wavelet decomposition and the Discrete Cosine Transform (DCT).
Deep Convolutional Features
The high-level Semantic features were obtained from the Pre-Trained CNN architecture, which is fully tuned for morph detection.
Feature Fusion
From the extracted features, like PRNU, Spatial, Spectral, and deep learning features, a single representational vector has been created, which includes dimensionality reduction where it uses principal component Analysis (PCA) to reduce dimensionality and usage of z-score normalization, which ensures the equal contribution of all types.
Classification and Model training
The above fused feature representation is mainly used to find the differences between the original and the morphed images in which the feature is used to train the binary classifier to find the differences. Two classifiers were used:
1) Support vector machines (SVM) containing a basis function kernel used for handcrafted features. 2) Fully connected neural network layers, which are used to append the deep feature extractor for end-to-end training as mentioned in (Table 1).
Table 1: Comparison of Face morphing attack detection Techniques
DETECTION METHOD | FEATURE TYPE | ADVANTAGES | REAL WORLD APPLICATIONS |
PRNU- Based Analysis | Sensor noise patterns | high accuracy for Printed-scanned images | High |
Deep CNN Features | High-level semantic features | Automatic feature learning | High |
Spatial Domain | Statistical features | Fast computation | Medium |
Spectral domain | Frequency domain features | Robust for noise | Medium |
Multi-Model feature | Combined(PRNU+deep+handcrafted) | Leverages multiple cues | Very high |
SVM | Traditional ML Approach | Fast inference | Medium |
Conclusion
This article presented a generalized Face morphing attack detection framework that has been trained with a highly diverse morphed face database to be used in the real life scenarios. By working with automatically and manually created morphed images, the proposed model has been improved its detection performance. The model has been improved its detection accuracy across the variations in age, posture, and expression by using the feature concentration and SVM classifiers, which can be used to give the best detection accuracy. The PRNU-based analysis helped further enhance morph detection, in which it can be used for printing and scanning images, which highlights its practical use in real world scenarios. The upcoming studies should focus on including the real- world morphed images and developing flexible detection systems to address the evolving morphing techniques.
References
- Muhammad Hamza, Samabia Tehsin, Mamoona Humayun, Maram Fa- haad Almufareh, and Majed Alfayad. A comprehensive review of face morph generation and detection of fraudulent identities. Applied Sciences, 12(24):12545, 2022.
- Muhammad Hamza, Samabia Tehsin, Hanen Karamti, and Norah Saleh Al- ghamdi. Generation and detection of face morphing attacks. IEEE Access, 10:72557–72576, 2022.
- Pavel Korshunov and Touradj Ebrahimi. Using face morphing to protect privacy. In 2013 10th IEEE international conference on advanced video and signal based surveillance, pages 208–213. IEEE, 2013.
- Ulrich Scherhag, Luca Debiasi, Christian Rathgeb, Christoph Busch, and Andreas Uhl. Detection of face morphing attacks based on prnu analysis. IEEE Transactions on Biometrics, Behavior, and Identity Science, 1(4):302– 317, 2019.
- Sushma Venkatesh, Raghavendra Ramachandra, Kiran Raja, and Christoph Busch. Face morphing attack generation and detection: A comprehensive survey. IEEE transactions on technology and society, 2(3):128–145, 2021.
- Goyal, S., Kumar, S., Singh, S. K., Sarin, S., Priyanshu, Gupta, B. B., … & Colace, F. (2024). Synergistic application of neuro-fuzzy mechanisms in advanced neural networks for real-time stream data flux mitigation. Soft Computing, 28(20), 12425-12437.
- Panigrahi, R., Bele, N., Panigrahi, P. K., & Gupta, B. B. (2024). Features level sentiment mining in enterprise systems from informal text corpus using machine learning techniques. Enterprise Information Systems, 18(5), 2328186.
- Gupta, B. B., Gaurav, A., Chui, K. T., & Arya, V. (2024, January). Deep learning-based facial emotion detection in the metaverse. In 2024 IEEE International Conference on Consumer Electronics (ICCE) (pp. 1-6). IEEE.
- Gaurav, A., Gupta, B. B., & Chui, K. T. (2022). Edge computing-based DDoS attack detection for intelligent transportation systems. In Cyber Security, Privacy and Networking: Proceedings of ICSPN 2021 (pp. 175-184). Singapore: Springer Nature Singapore.
- Venkatesh, S., Ramachandra, R., Raja, K., & Busch, C. (2021). Face morphing attack generation and detection: A comprehensive survey. IEEE transactions on technology and society, 2(3), 128-145.
- Korshunov, P., & Ebrahimi, T. (2013, August). Using face morphing to protect privacy. In 2013 10th IEEE international conference on advanced video and signal based surveillance (pp. 208-213). IEEE.
- Raghavendra, R., Raja, K., Venkatesh, S., & Busch, C. (2017, October). Face morphing versus face averaging: Vulnerability and detection. In 2017 IEEE International Joint Conference on Biometrics (IJCB) (pp. 555-563). IEEE.
Cite As
Kalyan C S N (2025) Face Morphing in Identity Fraud: Threats to Authentication Systems, Insights2Techinfo, pp.1