By: Shavi Bansal, Insights2Techinfo, India Email: shavi@insights2techinfo.com
Abstract
As the Internet of Things (IoT) continues to revolutionize industrial and consumer ecosystems, ensuring robust security has become a mission-critical priority. From small-scale deployments using Raspberry Pi to large-scale edge infrastructures, the landscape of IoT security is evolving rapidly. This blog delves into practical, research-backed insights on IoT security, exploring lightweight intrusion detection systems (IDS), digital twins for threat detection, cross-domain authentication protocols, and the use of artificial intelligence (AI) for forgery prevention. By highlighting scalable and cost-effective approaches, especially in constrained environments, this article offers a comprehensive guide to building real-time defenses across the IoT spectrum.
Introduction
IoT [1][2] is a cornerstone of Industry 4.0 [3][4], enabling real-time communication between billions of devices, sensors, and controllers. These devices power everything from industrial automation and smart homes to healthcare monitoring and intelligent transportation systems. However, their vast attack surface, limited resources, and heterogeneity make them prime targets for cyber threats.
One of the most promising approaches to secure IoT ecosystems lies in lightweight, real-time defense systems—especially those deployable on low-cost hardware such as Raspberry Pi. This article synthesizes key findings from recent academic and applied research to present practical techniques that help fortify IoT environments with minimal resource overhead.
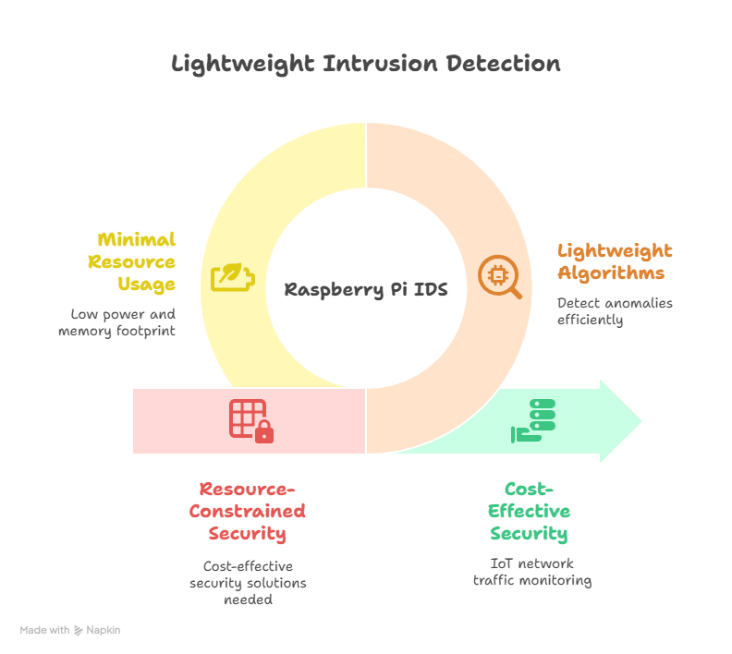
1. Lightweight Intrusion Detection on Raspberry Pi
In resource-constrained settings—rural deployments, remote monitoring sites, and smart agriculture—the need for cost-effective security solutions is paramount. Sai et al. [5] introduced a lightweight intrusion detection system (IDS) using Raspberry Pi 3B+ to monitor IoT network traffic. The system leveraged lightweight algorithms to detect anomalies such as brute force and denial-of-service (DoS) attacks while keeping power consumption and memory usage minimal.
This approach demonstrated that real-time detection doesn’t require enterprise-grade hardware. Instead, embedded AI models can be optimized for edge devices, making them an ideal defense line for vulnerable, distributed systems.
2. Digital Twin-Based Security for Connected Systems
Digital twins are virtual models that replicate physical devices or systems in real-time. In security applications, digital twins can be used to simulate threats, detect anomalies, and support proactive defense.
Arya et al. [6] implemented digital twins to detect malicious nodes in vehicular ad hoc networks (VANETs). Their approach monitored real-time network behavior and compared it against the virtual twin’s expectations to flag deviations. This paradigm is now being extended to broader IoT applications, including smart manufacturing, energy grids, and autonomous logistics, where simulation-driven defense is both scalable and precise.
3. Cross-Domain Authentication in Industrial IoT
IoT devices often need to interact with different systems, cloud platforms, and applications—many of which operate across domains. Traditional authentication models are often too heavy and slow for such dynamic, distributed environments.
Zhang et al. [7] developed a lightweight cross-domain authentication protocol specifically for the Industrial Internet. This protocol ensures secure device communication across cloud-edge systems, reducing reliance on centralized trust authorities. In IoT environments, where devices might roam or change networks frequently, such authentication models reduce latency while preserving data integrity.
4. AI for Digital Forgery and Interaction Monitoring
IoT security isn’t just about devices—it also concerns the data they generate. In smart communities, surveillance systems, or consumer IoT applications, attackers can forge sensor readings, video footage, or environmental signals.
Sedik et al. [8] proposed an AI-enhanced system for digital forgery analysis and critical interaction monitoring. Their model combines computer vision and statistical analysis to detect tampered data streams. For example, if a smart doorbell camera’s footage is manipulated, the system can flag inconsistencies in the metadata and pixel anomalies in the video. These solutions are crucial for privacy assurance and legal compliance in smart homes and public infrastructure.
5. Edge AI for Attack Detection in Transportation Networks
Edge computing plays a vital role in time-sensitive systems like intelligent transportation. Here, the ability to detect and respond to Distributed Denial of Service (DDoS) attacks must happen at the edge rather than relying on centralized servers.
Gaurav et al. [9] presented a real-time edge-based DDoS detection system tailored for connected vehicles and traffic infrastructure. The system combines AI models with local network monitoring on edge gateways to identify abnormal packet flows and trigger countermeasures in milliseconds. Such systems are increasingly important in autonomous driving, fleet management, and smart traffic control, where delays in response can compromise safety.
6. Practical Deployment Strategy
To implement a robust IoT defense mechanism—especially in cost-constrained settings—the following layered approach is recommended[10-12]:
Table 1: Multi-Layered IoT Security Strategy
Layer | Technology / Approach | Key Benefit |
Device Layer | Raspberry Pi + Lightweight IDS [5] | Low-cost, edge-level protection |
Network Layer | Cross-Domain Authentication [7] | Secure communication across systems |
Twin Layer | Digital Twins for Threat Simulation [6] | Proactive detection |
Data Layer | AI for Forgery Detection [8] | Data authenticity & user trust |
Application Layer | Edge AI for DDoS Detection [9] | Real-time response in critical systems |
This strategy ensures that every layer of the IoT stack is protected, from device hardware to the application interface, and can be adapted to various industries.
7. Challenges and Future Directions
Despite promising results, IoT security still faces significant hurdles:
- Scalability: Lightweight models need to scale across thousands of devices without manual configuration.
- Energy Constraints: Battery-powered devices must run security features without draining power.
- Standardization: A lack of universal protocols complicates interoperability and compliance.
- Adversarial Attacks: AI models used in IDS and forgery detection are susceptible to adversarial manipulation.
Ongoing research is exploring federated learning, quantum-resistant encryption, and zero-trust architectures to mitigate these challenges and support long-term scalability.
Conclusion
Securing the Internet of Things is not just about preventing attacks—it’s about enabling trust in connected ecosystems. As devices become smarter and more ubiquitous, the tools to defend them must be equally intelligent, adaptive, and resource-conscious.
From Raspberry Pi-powered intrusion detection to digital twins and AI-enhanced forgery analysis, the research highlighted in this blog offers a practical roadmap for building real-time, scalable, and affordable IoT defenses. Whether in smart cities, rural monitoring, industrial automation, or transportation, these innovations are paving the way for a secure and sustainable connected future.
References
- Ali, A., Shaukat, H., Elahi, H., Taimur, S., Manan, M. Q., Altabey, W. A., … & Noori, M. (2025). Advancements in energy harvesting techniques for sustainable IoT devices. Results in Engineering, 104820.
- Chandrasekaran, G., Kumar, N. S., A, C., V, G., Priyadarshi, N., & Khan, B. (2025). IoT enabled smart solar water heater system using real time ThingSpeak IoT platform. IET Renewable Power Generation, 19(1), e12760.
- Taqi, H. M. M., Nayeem, I., Bari, A. M., Anam, M. Z., & Ali, S. M. (2025). Addressing challenges to cloud manufacturing in industry 4.0 environment using an integrated approach: Implications for sustainability. Green Technologies and Sustainability, 100166.
- Queiroz, M. M., Fosso Wamba, S., Chiappetta Jabbour, C. J., Lopes de Sousa Jabbour, A. B., & Machado, M. C. (2025). Adoption of Industry 4.0 technologies by organizations: a maturity levels perspective. Annals of Operations Research, 348(3), 1989-2015.
- Sai, K. M., Gupta, B. B., Hsu, C. H., & Peraković, D. (2021, December). Lightweight intrusion detection system in IoT networks using Raspberry Pi 3B+. In SysCom (pp. 43–51).
- Arya, V., Gaurav, A., Gupta, B. B., Hsu, C. H., & Baghban, H. (2022, December). Detection of malicious node in VANETs using digital twin. In International Conference on Big Data Intelligence and Computing (pp. 204–212). Springer.
- Zhang, T., Zhang, Z., Zhao, K., Gupta, B. B., & Arya, V. (2023). A lightweight cross-domain authentication protocol for trusted access to industrial internet. International Journal on Semantic Web and Information Systems, 19(1), 1–25.
- Sedik, A., Maleh, Y., El Banby, G. M., Khalaf, A. A., Abd El-Samie, F. E., Gupta, B. B., … & Abd El-Latif, A. A. (2022). AI-enabled digital forgery analysis and crucial interactions monitoring in smart communities. Technological Forecasting and Social Change, 177, 121555.
- Gaurav, A., Gupta, B. B., & Chui, K. T. (2022). Edge computing-based DDoS attack detection for intelligent transportation systems. In Cyber Security, Privacy and Networking (pp. 175–184). Springer.
- Panigrahi, R., Bele, N., Panigrahi, P. K., & Gupta, B. B. (2024). Features level sentiment mining in enterprise systems from informal text corpus using machine learning techniques. Enterprise Information Systems, 18(5), 2328186.
- Gupta, B. B., Gaurav, A., Chui, K. T., & Arya, V. (2024, January). Deep learning-based facial emotion detection in the metaverse. In 2024 IEEE International Conference on Consumer Electronics (ICCE) (pp. 1-6). IEEE.
- Gaurav, A., Gupta, B. B., & Chui, K. T. (2022). Edge computing-based DDoS attack detection for intelligent transportation systems. In Cyber Security, Privacy and Networking: Proceedings of ICSPN 2021 (pp. 175-184). Singapore: Springer Nature Singapore.
Cite As
Bansal S. (2023) From Raspberry Pi to Real-Time Defense: Practical Insights on IoT Security, Insights2Techinfo, pp.1