By: Reka Rius , CCRI, Asia University, Taiwan
Abstract
The increasing number of mobile users makes them an attractive target for phishing attackers. There are several attack methods commonly used by attackers, as summarized in this article. Solutions that can be used to detect and counter phishing attacks include user education which can be implemented through games, S-Detector, SMSAssassin, DCA-based, VeriUI, StopBankun, and confidential data leakage prevention.
Keywords: phishing, mobile platforms, attack methods, solutions
Introduction
Phishing is an online spoofing mechanism in which social engineering messages are communicated via electronic communication channels to prompt users to perform certain actions for the benefit of attacker [6]. Phishing attacks can target platforms such as mobile devices, email, social media, etc.
During the last 10 years, mobile devices technologies have grown rapidly due to the daily increase in the number of users and facilities [1]. According to , the number of mobile users has become 5.62 billion global users in 2024 [9].
Current mobile devices can be used for many private and financial applica- tions as Facebook, mobile bank, etc. Android and iOS are the two dominant operating systems with 99.62% market share distributed as 71.47% for Android and 28.15% for iOS in 2025 [5].
Due to the large number of mobile users, they have become a prime target for phishing attacks.
Method of Mobile Phising
In mobile technology, several attack techniques are used by phishers to carry out phishing attacks, such as the following:
Financial Fraud
Financial fraud is an attack method aimed at gaining access to the victim’s financial assets by collecting their financial credentials. One example of financial fraud is a fake update request for an internet banking account [1]. The user follows a link in a message that appears legitimate and is then redirected to a page resembling the bank’s login page .
Service Updates
This attack method works by having the attacker create a fake message that may include a request for a service update and account verification. The message is crafted to appear as though it comes from a popular and trusted service known to the victim, such as Google Drive. In this method, various attack techniques are used, such as fake login pages and social engineering tactics with persuasive or urgent language to pressure the victim into entering their credentials.
Promotional Offers
The promotional offers method does not directly steal data from the victim, but instead deceives them into voluntarily providing their private information—such as email, username, and password. This is done by sending promotional offer messages to a number of users, requiring them to create an account. During the registration process, users are asked to input their credentials. The danger lies in the fact that many users use the same credentials for other services such as email, social media, online shopping accounts, or even internet banking.
Spear Phising
The spear phishing method is carried out by specifically targeting victims. In- formation related to the victims is gathered and later used to deceive them by impersonating someone known to the victims in order to obtain their sensitive data.
Solution
Several solutions proposed to address phishing attack methods on mobile devices are presented below:
User Education
User education is important in order to create awareness among the users about phishing attacks. Phishing is a social engineering attack. Hence, educating the user is important to avoid phishing attack. Education based approaches include showing warnings, and online training through games [4].
Train user through mobile games
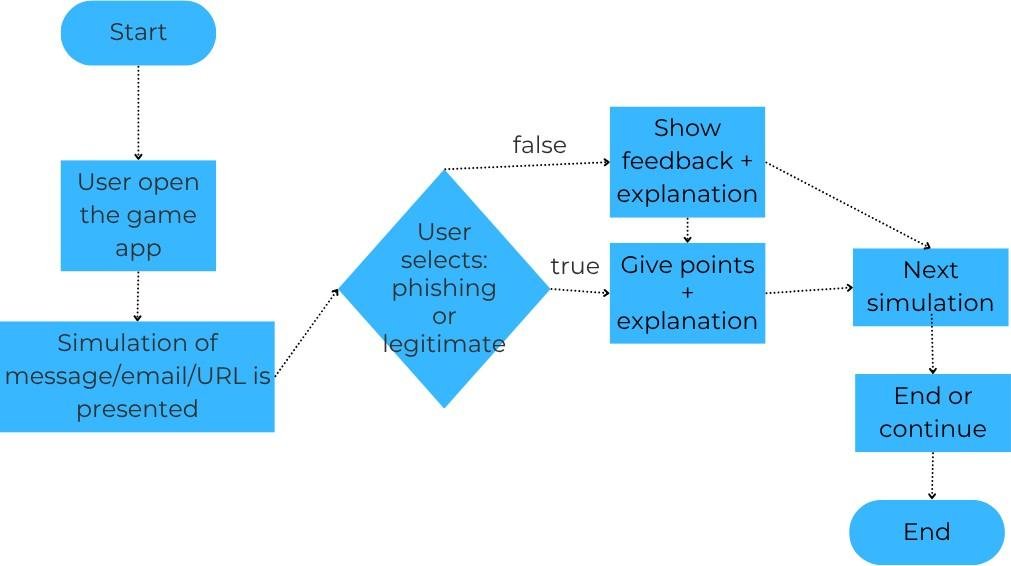
One of the important factors in avoiding phishing attack is to train users which leads to correct identification of phishing and legitimate instances [4]. So this researcher [2] designed one such game. The game is about educating the users about phishing emails and phishing URLs so that the user is able to differentiate between phishing and legitimate emails and URLs. The prototype of the game was implemented on Google App Inventor Emulator. The use of the game is illustrated in the flowchart shown in Figure 1.
Detection of smishing and spam SMSes
according to [4] smishing messages consist of a text message and a URL which when opened perform malicious activity. Attackers use social engineering ap- proach to target victims and users are easily attacked by it. (Table 1) presents several detection approaches and their purposes [10-15].
Table 1: Table of Smishing Detection Approaches
Approach Name | Purpose |
|---|---|
S-Detector | Detects and blocks smishing messages |
SMSAssassin | Filters spam and smishing based on crowdsourcing |
DCA-based | Filters spam messages based on text and email |
Spam Detection using Text Content | Classifies spam messages based on semantic meaning |
Smishing Defender | Android app to detect and block smishing |
MDLText | Fast and efficient spam message classification |
Malicious mobile applications detection
Various approaches to detect malicious applications and methodologies to pre- vent data leakage from the mobile applications are discussed below.
VeriUI
researcher [8] proposed a system “VeriUI” based on attested login, which is a password protection mechanism for mobile devices. It provides a secure and hardware isolated surroundings to input password so as to prevent phishing attacks that occur through mobile applications.
StopBankun
researcher [7] proposed a method StopBankun to prevent replacement of banking applications with the malicious applications.
Confidential data leakage prevention
researcher [3] proposed a system for Android devices to prevent confidential data leakage. It uses J48 clas- sification algorithm to detect applications that leak sensitive information.
References
- Belal Amro. “Phishing techniques in mobile devices”. In: arXiv preprint arXiv:1802.04501 (2018).
- Nalin Arachchilage, Steve Love, and Michael Scott. “Designing a mobile game to teach conceptual knowledge of avoiding’phishing attacks’”. In: In- ternational Journal for e-Learning Security 2.1 (2012), pp. 127–132.
- Yavuz Canbay, Mehtap Ulker, and Seref Sagiroglu. “Detection of mobile applications leaking sensitive data”. In: 2017 5th International Symposium on Digital Forensic and Security (ISDFS). IEEE. 2017, pp. 1–5.
- Ankit Kumar Jain Diksha Goel. “Mobile phishing attacks and defence mechanisms: State of art and open research challenges”. In: Computers Security 73 (2018), pp. 519–544. issn: 0167-4048. doi: https://doi.org/ 10.1016/j.cose.2017.12.006.
- StatCounter GlobalStats. Mobile Operating System Market Share World- wide – 2024. Accessed on August 5, 2025. 2024. url: https://gs.statcounter. com/os-market-share/mobile-tablet-/worldwide/2024.
- Mahmoud Khonji, Youssef Iraqi, and Andrew Jones. “Phishing Detection: A Literature Survey”. In: IEEE Communications Surveys Tutorials 15.4 (2013), pp. 2091–2121. doi: 10.1109/SURV.2013.032213.00009.
- Dongwoo Kim, Chankyu Park, and Jaecheol Ryou. “StopBankun: Counter- measure of app replacement attack on Android”. In: 2015 seventh interna- tional conference on ubiquitous and future networks. IEEE. 2015, pp. 603– 605.
- Dongtao Liu and Landon P Cox. “Veriui: Attested login for mobile devices”. In: Proceedings of the 15th workshop on mobile computing systems and applications. 2014, pp. 1–6.
- We Are Social. Digital 2024 April Global Statshot Report. Accessed on Au- gust 5, 2025. 2024. url: https://wearesocial.com/uk/blog/2024/04/ digital-2024-april-global-statshot-report.
- Gupta, B. B., Gaurav, A., Arya, V., & Alhalabi, W. (2024). The evolution of intellectual property rights in metaverse based Industry 4.0 paradigms. International Entrepreneurship and Management Journal, 20(2), 1111-1126.
- Zhang, T., Zhang, Z., Zhao, K., Gupta, B. B., & Arya, V. (2023). A lightweight cross-domain authentication protocol for trusted access to industrial internet. International Journal on Semantic Web and Information Systems (IJSWIS), 19(1), 1-25.
- Lu, Y., Guo, Y., Liu, R. W., Chui, K. T., & Gupta, B. B. (2022). GradDT: Gradient-guided despeckling transformer for industrial imaging sensors. IEEE Transactions on Industrial Informatics, 19(2), 2238-2248.
- Birthriya, S. K., Ahlawat, P., & Jain, A. K. (2025). Detection and prevention of spear phishing attacks: A comprehensive survey. Computers & Security, 104317.
- Chinta, P. C. R., Moore, C. S., Karaka, L. M., Sakuru, M., Bodepudi, V., & Maka, S. R. (2025). Building an Intelligent Phishing Email Detection System Using Machine Learning and Feature Engineering. European Journal of Applied Science, Engineering and Technology, 3(2), 41-54.
- Ho, G., Mirian, A., Luo, E., Tong, K., Lee, E., Liu, L., … & Voelker, G. M. (2025, May). Understanding the efficacy of phishing training in practice. In 2025 IEEE Symposium on Security and Privacy (SP) (pp. 37-54). IEEE.
Cite As
Rius R. (2025) Phishing on Mobile Platforms: Attack Methods and Solutions, Insights2Techinfo, pp.1