By: Jampula Navaneeth1
1Vel Tech University, Chennai, India
2International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan Email: navaneethjampula@gmail.com
Abstract
The main aim of this article is to utilize the various neural networks for identifying phishing emails. It is all about the implementing the neural network systems. For various neural networks there is a meaningful usage and process. Emails are a major concern to most individuals and organizations since phishing is a major threat. The above messages are crafted with the intent of making the receiver reveal some personal information like passwords and financial information. The vast majority of classical anti-phishing methods fail when it comes to evasion of advanced phishing schemes. This is where neural network, one of the branches of artificial intelligence, becomes of use.
Keywords: Neural Networks, Email, Phishing, Artificial Intelligence
Introduction
With the improvements in computer security there is trust in safety on the internet hence leading to e-business, dealing with money through the internet, and other methods of sending, handling and receiving of money today. Regrettably, the use of the Internet in service delivery has come hand in hand with unlawful efforts to duplicate such transactions to the advantage of wrong-doors. One of the most common and very simple to implement attack types, which is a threat to organisations, institutions and simple users is phishing [1].
Neural Networks
Specifically, an artificial neural network, or just neural network, is a mathematical model that mimics a biological neural network. This is a developing structure of a system that alters in phases of learning. Neural networks come in many varieties some of which are highlighted below. When it comes to the problem of phishing detection, which can be regarded as a classification task, a multilayer feedforward neural network is selected. The connection between neurons in the feedforward neural network does not include a directed cycle [2].
Neural networks are developed basing themselves on biological neural networks. In real neurons, these the input data is being processed and shared using electricity, which is in whichever form. In artificial neural networks, if the system, input nodes are referred to as neurons, edges are considered as functions of the layers, and output neurons make up the system. They concern with the nodes and the edges of the mentioned network. Supplier neurons with other neurons through functions [2].
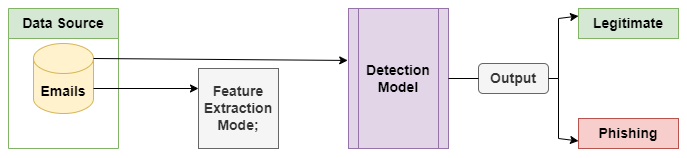
Let’s see various networks that can used for identifying phishing attacks. ANN is a technical tool that mimics a biological neural network in its operating feature. ANN such as,
- Feed Forward Neural Networks
FFN determines a directed graph containing the nodes also known as neurons and the edges too. In FFN information is propagated between two nodes along the edges without the possibility to return to the node it was originally sent from. Multi-layer perceptron is one of the feed forward neural network that has more than two layers of layers where; it contains the input layer, more than one hidden layers or one and the output layer where in every layer, there are multiple neurons commonly known as units mathematically [3].
- Convolutional Neural Networks
A Convolutional neural network is one of the neural networks which are used in the deep learning to upgrade the computer visions. Hence, if turning to the results of the Machine Learning, it is possible to say that the Artificial Neural Networks reveal rather high results. Neural Networks are applied on kinds of datasets: images, audio and text. There are various types of Neural Networks with different uses; for sequence generation we use Recurrent Neural Networks especially LSTM and for image classification we use Convolution Neural networks [3].
- Recurrent neural networks
The recurrent neural network is a variation of feed forward networks each of which was invented mid 1980s for working on time series. It also makes it possible to incorporate information from previous times steps in the computation of current times steps because RNN has feedback connections to its units, this makes it useful [4]. In other related long-standing artificial intelligence problems, particularly those that concern computer vision, natural language processing and speech processing, a good performance has been realised with this technique [3].
Future Work
That requires, while the Future works, by reducing the time of the state’s execution and increasing the productivity of the system, full-scale use of the Graphics Programming Units [5]. Other categories of the DL like the recurrent neural networks, the convolutional neural networks and the LSTM can also be tried to enhance the performance of the system [2].
Conclusion
Neural networks can therefore be concluded to be a strong weapon against phishing emails. With the given ability in pattern recognition, they present high accuracy, scalability, and optimization to one of the most crucial security issues. The importance of the neural networks in the context of the email security will only increase with the progress of the technology to protect the valuable data and information to build the level of trust in the digital world.
References
- L. Halgaš, I. Agrafiotis, and J. R. C. Nurse, “Catching the Phish: Detecting Phishing Attacks Using Recurrent Neural Networks (RNNs),” in Information Security Applications, I. You, Ed., Cham: Springer International Publishing, 2020, pp. 219–233. doi: 10.1007/978-3-030-39303-8_17.
- O. K. Sahingoz, S. Işılay Baykal, and D. Bulut, “PHISHING DETECTION FROM URLS BY USING NEURAL NETWORKS,” in Computer Science & Information Technology (CS & IT), AIRCC Publication Corporation, Dec. 2018, pp. 41–54. doi: 10.5121/csit.2018.81705.
- V. Ravi, B. G. Hb, P. Poornachandran, A. K. Madasamy, and S. Kp, DeepAnti-PhishNet: Applying Deep Neural Networks for Phishing Email Detection CEN-AISecurity@IWSPA-2018. 2018.
- B. D. Alfia, A. Asroni, S. Riyadi, and M. Rahaman, “Development of Desktop-Based Employee Payroll: A Case Study on PT. Bio Pilar Utama,” Emerging Information Science and Technology, vol. 4, no. 2, Art. no. 2, Dec. 2023, doi: 10.18196/eist.v4i2.20732.
- M. Rahaman, B. Chappu, N. Anwar, and P. K. Hadi, “Analysis of Attacks on Private Cloud Computing Services that Implicate Denial of Services (DoS),” vol. 4, 2022.
- Vajrobol, V., Gupta, B. B., & Gaurav, A. (2024). Mutual information based logistic regression for phishing URL detection. Cyber Security and Applications, 2, 100044.
- Gupta, B. B., Gaurav, A., Panigrahi, P. K., & Arya, V. (2023). Analysis of cutting-edge technologies for enterprise information system and management. Enterprise Information Systems, 17(11), 2197406.
- Gupta, B. B., Gaurav, A., & Panigrahi, P. K. (2023). Analysis of retail sector research evolution and trends during COVID-19. Technological Forecasting and Social Change, 194, 122671.
Cite As
Navaneeth J. (2024) The Role of Neural Networks in Identifying Phishing Emails, Insights2Techinfo, pp.1