By: Megha Quamara
The most important application of quantum computing in the future is likely to be a computer simulation of quantum systems, because that’s an application where we know for sure that quantum systems in general cannot be efficiently simulated on a classical computer
David Deutsch
Knowing that there are no ideal digital communication pathways and not all users on the Internet are the legitimate ones, and in addition to everything else, recognizing the importance of the information we exchange as an asset, cryptography came to the rescue. The notion of cryptography originally points towards the study of hidden secrets, and involves practicing means to allow secure communication in the presence of adversaries [1]. Since its appearance, cryptography is in continuous use being the cornerstone of a secure information ecosystem. Conventional means, for example, substitution, transposition, steganography, emphasized on securing the information via obscurity; however, were restricted in terms of their wide-scale realization. Modern cryptography, on the other hand, adds a secure layer of defense to the vast network of devices and users, addressing millions of transactions per second. It is an amalgamation of fields like computer science, mathematics, and informatics, and finds its working basis in the idea of security via computational complexity, where unidirectional mathematical operations take part in protecting the information from security threats. These operations constitute two fundamental types of cryptographic algorithms, viz. symmetric- and asymmetric-key algorithms, in modern cryptography.
Symmetric-key cryptographic algorithms involve the use of a common key by the communicating parties (i.e., sender and receiver) for both encryption and decryption of the messages [1]. These algorithms are also referred as secret-key cryptographic algorithms, as the cryptographic key or the parameters used to derive the key are representative of a shared secret that must be known in advance or distributed to both parties for establishing a private communication link. Consequently, the security of the information exchange relying on these algorithms lies in the secrecy of the underlying key. Some of the popular symmetric-key cryptographic algorithms include, but are not limited to Data Encryption Standard (DES) [2], International Data Encryption Algorithm (IDEA) [3], and Advanced Encryption Standard (AES) [4]. To address the issue of key distribution in symmetric-key cryptographic algorithms, asymmetric or public-key cryptographic algorithms came into picture. These algorithms work with the idea of using a pair of different keys, viz. public (known by anyone in the network) and private (known by only its owner) for the purpose of encryption and decryption, respectively [1]. In such a case, anyone in the network can encrypt the message using the public key of the intended receiver, and upon receiving the encrypted message, the receiver can decrypt it using its private key. A wide range of asymmetric-key cryptographic algorithms can be found in literature and practice, with Rivest-Shamir-Adleman (RSA) [5] being the popular one. Moreover, key distribution methods like Diffie-Hellman [6] facilitate both the communicating parties to agree on the shared secret over a public channel. Figure 1 provides a taxonomy of some of the widely known classical and modern cryptographic algorithms in the literature.
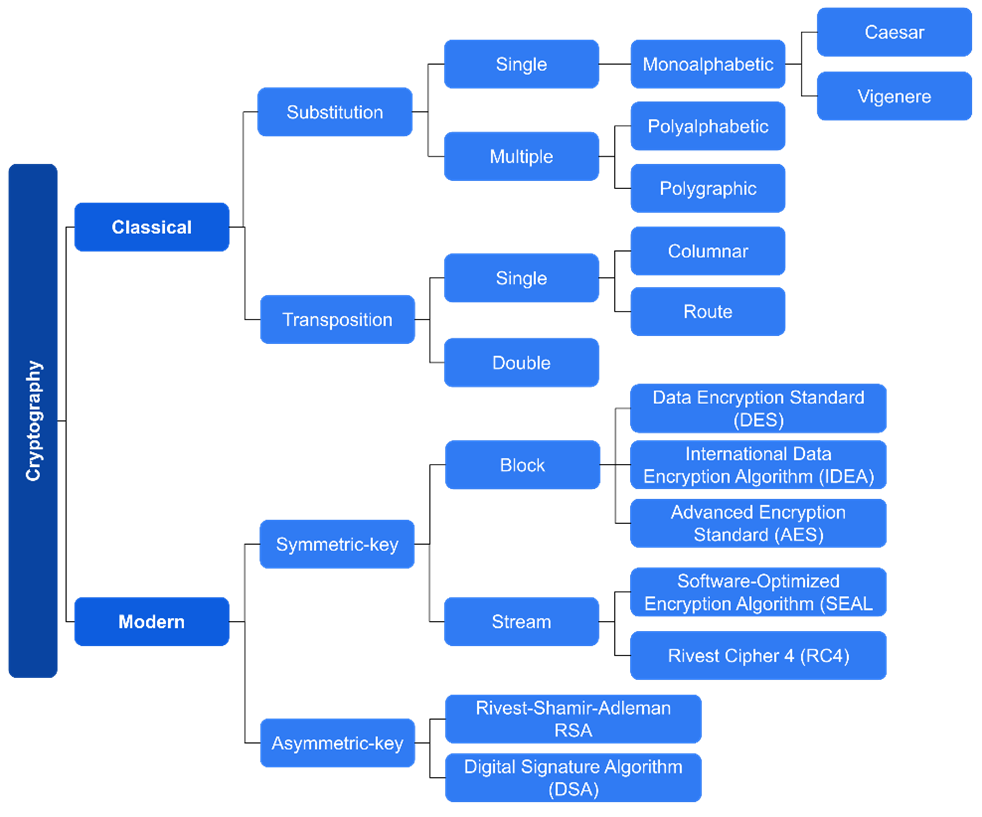
Perhaps not surprisingly, many of us may not be aware about where concretely we can find the use of the above-mentioned categories of algorithms. Unbelievably, but they exist in every essence of our information ecosystem, spanning applications including financial, social networking, E-Health, E-Commerce, etc. For instance, message applications like WhatsApp [7] and Signal [8] make use of end-to-end encryption for authenticating us and ensuring the confidentiality of the messages we exchange with our loved ones. To prevent malicious entities from knowing the content of our conversation, the interaction between Instagram [9] and us is an encrypted one. For identifying machines over the Internet, Hypertext Transfer Protocol Secure (HTTPS) [10] is in use, which relies on asymmetric-key algorithms for connection establishment, and then, symmetric-key algorithms for encryption and decryption of information exchanges during the session. The idea of digital currency that uses cryptography for securing our financial transactions is prevailing these days, as another dimension of the applicability of asymmetric-key algorithms. As a matter-of-fact, the story does not end here!
Although the assurance of confidentiality and privacy of transmission, authenticity of source, controlled accessibility of resources, etc. have remained the chief aspects of information security so far; however, the field of cryptography is not limited to merely these goals due to an ever-increasing sophistication of the applicability of information systems in today’s world. With the advent of the notion of Quantum cryptography, we as developers or end users need to rethink about our reliance on the present-day security assurance techniques. We can observe that there are potential reasons to believe that a new wave of transformation is coming, and the future of Quantum cryptography is significantly as powerful as of the classical cryptography. The intuition of simulating physics in computers [11] has proven to be right and Shor’s breakthrough exemplifies that there may be a need of another paradigm-shift. It is anticipated that Quantum computing may offer advantages far beyond the reach of classical computing; allowing simultaneous execution of the computational paths in single hardware unit in alignment with the superposition principle, unlike classical computing where among all the possible paths, only one makes the difference in an instance. Nevertheless, computational security being an area yet to be explored in context of Quantum cryptography [12-14], unexpected challenges may also threaten classical computing to a significant extent. My future post in this series would address these threats in detail.
Stay tuned to Insights2Techinfo for my next post!
References:
- Stinson, D. R. (1995). Classical cryptography. Cryptography, Theory and Practice, 2nd Edition, Chapman & Hall/CRC, Kenneth H. Rosen (Ed.), 1-20.
- Coppersmith, D. (1994). The Data Encryption Standard (DES) and its strength against attacks. IBM journal of research and development, 38(3), 243-250.
- Lai, X., & Massey, J. L. (1990, May). A proposal for a new block encryption standard. In Workshop on the Theory and Application of Cryptographic Techniques (pp. 389-404). Springer, Berlin, Heidelberg.
- Daemen, J., & Rijmen, V. (2001). Reijndael: The Advanced Encryption Standard. Dr. Dobb’s Journal: Software Tools for the Professional Programmer, 26(3), 137-139.
- Rivest, R. L., Shamir, A., & Adleman, L. (1978). A method for obtaining digital signatures and public-key cryptosystems. Communications of the ACM, 21(2), 120-126.
- Diffie, W., & Hellman, M. (1976). New directions in cryptography. IEEE transactions on Information Theory, 22(6), 644-654.
- WhatsApp. WhatsApp Encryption Overview (2016). Technical White Paper. Accessed: October 2021.
- Signal. https://signal.org/docs/. Accessed: October 2021.
- Landsverk, K. H. (2014). The Instagram Handbook: 2014 Edition. PrimeHead Limited.
- Bhimani, A. (1996). Securing the commercial Internet. Communications of the ACM, 39(6), 29-35.
- Brassard, G. (1994). Quantum computing: the end of classical cryptography?. ACM SIGACT News, 25(4), 15-21.
- Megha Quamara (2021), Quantum Computing: A Threat for Information Security or Boon to Classical Computing? Insights2Techinfo, pp. 1
- Abd El-Latif, A. A., Abd-El-Atty, B., Hossain, et al. (2018). Efficient quantum information hiding for remote medical image sharing. IEEE Access, 6, 21075-21083.
- Pljonkin, A. P., et al. (2017, September). Features of detection of a single-photon pulse at synchronisation in quantum key distribution systems. In 2017 6th International Conference on Informatics, Electronics and Vision & 2017 7th International Symposium in Computational Medical and Health Technology (ICIEV-ISCMHT) (pp. 1-5). IEEE.
Cite this article:
Megha Quamara (2021), Beyond Classical Cryptography: A Technical View Cultivating Quantum Cryptography, Insights2Techinfo, pp. 1