By: Nicko Cajes; Northern Bukidnon State College, Philippines
ABSTRACT
The network of hacker’s compromised devices called botnets presented a great threat especially in DDoS attacks. The target systems will be flooded with fake traffic in this type of attack, which will cause a lot of damage to resources and infrastructure. Vulnerable devices that were compromised can become botnets that can be used by attackers in large-scale DDoS attacks. The method of botnet-driven attack, difficulty in detecting it, and the current mitigation techniques are discussed in this article. The famous botnet attacks like Mirai and Zeus are included in this article along with the development of this attack and their advancement. Despite the enhancements, defending against botnet-driven DDoS attacks is still difficult, especially with IoT vulnerabilities.
INTRODUCTION
A botnet is a group consisting of multiple malware-infected computers, often known as zombies, that are summoned by evil actors known as botmasters. These zombies are remotely controlled by a botmaster who gives them commands to carry out malicious tasks. Internet crimes including Distributed Denial of Service (DDoS) attacks, identity theft, email spamming, and click fraud usually involve botnets. Given that they may eat up the victim network’s bandwidth and the victim machine’s resources, botnet-based DDoS attacks are disastrous for the victim network [1]. This paper aims to discuss the role of botnets in DDoS attacks, which includes the emerging trends, operational insights, and key challenges which researchers can use to understand the nature of the botnets properly.
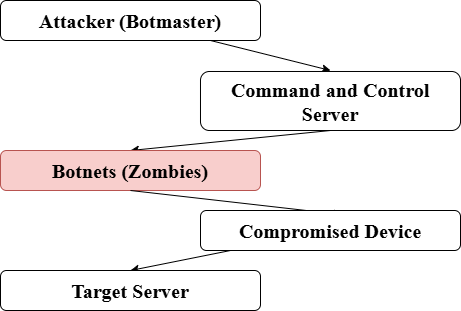
UNDERSTANDING DDOS ATTACKS
The term “DDoS” refers to a coordinated attack that is created using hacked hosts. For access and control, an attacker first identifies the network’s weaknesses and installs malicious software on several computers. Without the victim’s awareness, the attacker then sends attack packets to them through the compromised host as shown in figure 2. Damage to the victim’s network is equivalent to the intensity of the attack packet and the number of hosts employed in the attack. In a short amount of time, a network or web server may be affected if there are a lot of infected hosts [2].

The first step in a successful DDoS assault requires the attacker to build a botnet. In some cases, botnets are constructed using an already established methodology such as a campaigner, a single person, or a team of programmers working with a criminal organization that can program the code to poison the device. Any device that can run code can host this virus. With the goal of creating a botnet with these compromised devices, the attacker uses the malicious malware he developed to corrupt as many devices as possible [3].
BOTNET OPERATION IN DDOS ATTACKS
From the moment when the attacker starts a DDoS assault, the botnets take on the position of the attacker, this typically happens by managing them through a command-and-control server. A peer-to-peer network controlled by a single botmaster can be quickly created by botnet servers collaborating and communicating with one another. Therefore, any botnet DDoS attack might have numerous origins or be carried out by multiple people, sometimes acting in coordination and other times acting individually [5]. A visualization of the role of botnet in DDoS attack is shown in figure 3.
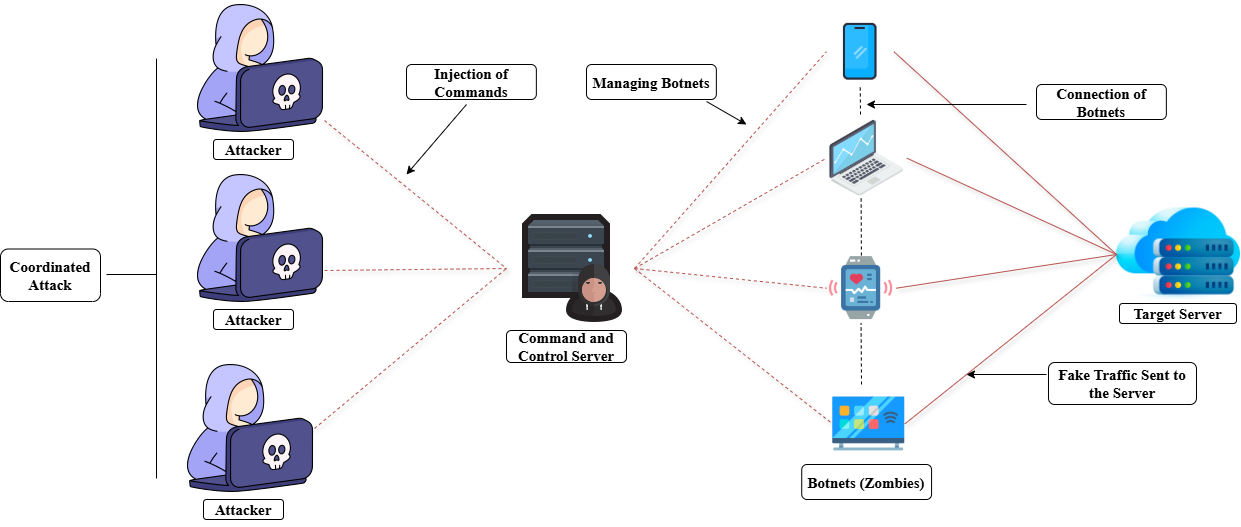
As a cybersecurity threat which utilizes the networks of compromised devices to carry out broad and separate attacks, botnets are not new in the field of cyber security that made the phrase well-known. The following are some of the previous incidents that have been attributed to this attack [6]:
Storm botnet (2007): In the year 2007, an example of the botnets has appeared. Storm botnet attack recorded 57 emails sent per day, this cyber monster is making an email onslaught that is not the same as before. This high growth of spam emails shows the dangerous impact of internet technology along with exposing the vastness of the botnet’s reach.
Conficker (2008): The next year saw a rise in the prevalence of the Conficker botnet, another significant cyberthreat. This assault has created a zombie army by assembling nine to ten million compromised Devices. Conficker used vulnerabilities in Microsoft Windows to infect machines and link them to a huge hidden network. The ability of botnets to take over millions of computers around the world is not only alarming to people and businesses, but it also shows an alarming increase in the advancement and scope of cybercrime.
Zeus (2009): Targeting online banking institutions, the Zeus botnet was renowned for its disturbingly effective evasion of security challenges, which resulted in massive data and financial breaches. Over 74,000 FTP accounts were hacked in this attack, and it did not include just any random collection of websites, famous websites such as Cisco, Amazon, and BusinessWeek were among the victims. This incident only shows the advance of the botnet’s ability to penetrate and obtain private data from many different victims.
Cutwail (2009): Another type of botnet that is well-known for its enormous spamming capabilities is Cutwail. It can transmit an incredible 74 billion spam messages per day and was thought to have breached between 1.5 and 2 million individual PCs. If we total these numbers, more than 51 million spam emails are sent per minute, which at that time accounted for 46.5% of the spam volume in the whole world. In addition to the flood of inboxes worldwide, the Cutwail spamming spree has become the beginning of the spread of malware and phishing schemes.
Mirai Botnet (2016): About 500,000 IoT devices have been infected globally by the Mirai botnet, which primarily targets IoT devices. This was an alarming and groundbreaking occurrence. Infecting gadgets like digital cameras and transforming them into powerful army bots was the intention. Through taking advantage of IoT device vulnerabilities that were frequently ignored in terms of security, this botnet demonstrated a terrifying new stage in cyber threats.
Emotet (2014-2020): Another troubling phase in the history of cybercrime is represented by Emotet. In addition to being disruptive, this assault infection also extremely expensive to maintain as it hits your system with state, municipal, tribal, and territorial governments having to pay up to $1 million for maintenance for each instance.
According to security analysts, botnet activity increased significantly worldwide from December 2023 to the first week of January 2024, with peaks topping one million devices [6].
CHALLENGES IN DEFENDING AGAINST BOTNET DDOS ATTACKS
Even with a lot of solutions proposed, there are still challenges related to detecting DDoS attack, the following are the common challenges in detecting it [7].
Large Traffic Classification: It needs to collect all domain traffic and extract every feature to identify DDoS attacks with the maximum detection accuracy. Yet in real-world situations, the number of flows often exceeds the highest possible processing capacity of any monitoring device, which made it a challenge for researchers to develop solutions to this problem.
Application of Machine Learning for Higher Detection Accuracy: Most machine learning techniques now in use have common issues, such as covering a limited number of attack types, deploying only one node, and consuming a lot of resources.
Feature Selection Problem in AI-based Solution: The network’s programmable features have limited computation and storage capacities. The detection model can only handle actions on a small number of features, even after it is deployed.
Collaborative Detection: Although machine learning is increasingly being used in detection, distributed DDoS assaults are typically too strong for model deployment on a single node, this necessitates collaborative nodes to effectively detect sophisticated DDoS attacks.
Incapability of Application Layer Attack Detection: Since attacks at the application layer differ from those in the network and transport layers, they are currently one of the most challenging problems to resolve in the field of defense against DDoS.
MITIGATION TECHNIQUES
Some strategies are used to neutralize this problem. Researchers have introduced mitigation techniques that are helpful in this case. The mitigation strategies that were commonly used are categorized into four main groups which are filtering, rate restriction, access control, and resource movement [8].
Filtering: This technique recognizes the attack source and blocks all flows from that harmful source by filtering network traffic and removing any suspicious connections.
Dynamic Filtering: By altering resource allocation, such as bandwidth, server capacity, or load balancing, this technique limits the effect of the attack while ensuring that legitimate traffic receives enough resources. It performs this by dynamically providing network resources based on recognized attack patterns.
Rate Limiting: This method tries to restrict the quantity of packets sent from a suspicious source at a specific moment by controlling the transmission rate.
Access Control: This technique includes establishing a blacklist and whitelist of network hosts to restrict network users’ ability to communicate and access resources.
Migration: This involves sending dangerous network traffic to a secure state for further analysis, this sends suspicious network traffic to a secure middlebox for a more thorough examination.
CONCLUSION
Botnets are a useful tool for cybercriminals who run DDoS attacks. While detecting these attacks and mitigating them such as filtering and rate limiting have been developed, the threats are still there because of the sophistication of the attack and the weaknesses in IoT. Machine learning techniques have shown great potential in solving this problem, but their limitations such as resources that must be used and application layer attacks remain. The effective defense against this attack requires a multi-layered approach, continuing to adapt to the evolving botnet tactics and threats.
REFERENCES
- Hoque, N., Bhattacharyya, D. K., & Kalita, J. K. (2015). Botnet in DDoS attacks: trends and challenges. IEEE Communications Surveys & Tutorials, 17(4), 2242-2270.
- Li, Q., Huang, H., Li, R., Lv, J., Yuan, Z., Ma, L., … & Jiang, Y. (2023). A comprehensive survey on DDoS defense systems: New trends and challenges. Computer Networks, 109895.
- Kumari, P., & Jain, A. K. (2023). A comprehensive study of DDoS attacks over IoT network and their countermeasures. Computers & Security, 127, 103096.
- Al-Hadhrami, Y., & Hussain, F. K. (2021). DDoS attacks in IoT networks: a comprehensive systematic literature review. World Wide Web, 24(3), 971–1001. https://doi.org/10.1007/s11280-020-00855-2
- Hasson, E. (2023, December 20). What is a DDoS Botnet | Common Botnets and Botnet Tools | Imperva. Learning Center. https://www.imperva.com/learn/ddos/botnet-ddos/
- Mascellino, A. . (2024, December 17). Researchers Uncover Major Surge in Global Botnet Activity. Infosecurity Magazine. https://www.infosecurity-magazine.com/news/hundredfold-surge-global-botnet/
- Li, Q., Huang, H., Li, R., Lv, J., Yuan, Z., Ma, L., … & Jiang, Y. (2023). A comprehensive survey on DDoS defense systems: New trends and challenges. Computer Networks, 109895.
- Singh, C., & Jain, A. K. (2024). A Comprehensive Survey on DDoS Attacks Detection & Mitigation in SDN-IoT Network. e-Prime-Advances in Electrical Engineering, Electronics and Energy, 100543.
- Stergiou, C. L., Plageras, A. P., Psannis, K. E., & Gupta, B. B. (2020). Secure machine learning scenario from big data in cloud computing via internet of things network. Handbook of Computer Networks and Cyber Security: Principles and Paradigms, 525-554.
- AlZu’bi, S., Shehab, M., Al-Ayyoub, M., Jararweh, Y., & Gupta, B. (2020). Parallel implementation for 3d medical volume fuzzy segmentation. Pattern Recognition Letters, 130, 312-318.
- Kee S.N. (2024) Blockchain as a Solution for Secure Data Transmission in IoT Networks, Insights2Techinfo, pp.1; https://insights2techinfo.com/blockchain-as-a-solution-for-secure-data-transmission-in-iot-networks/
Cite As
Cajes N. (2025) Botnets in DDoS Attacks: Emerging Trends, Operational Insights, and Key Challenges, Insights2techinfo, pp.1