By: KUKUTLA TEJONATH REDDY, International Center for AI and Cyber Security Research and Innovations (CCRI), Asia University, Taiwan, tejonath45@gmail.com
Abstract:
This article explores the use of CatBoost in phishing detection, a powerful gradient enhancing algorithm that focuses on the use of categorical data. As phishing attacks have become a major cybersecurity threat, the need for machine learning solutions improved will become more important. CatBoost’s unique features, including its proficiency in handling categorical features, robustness to overfitting, and model translation capabilities, position it as a formidable tool in the fight against phishing. The article explores how CatBoost enables feature engineering, model training and real-time processing is facilitated detection of objects. Highlights adaptability to threats Providing insights into CatBoost practices in the context of phishing detection, this article highlights its role in strengthening cybersecurity systems against the dynamic online threat environment emphasize.
Introduction:
Combating phishing attacks is a constant challenge in the ever-changing cybersecurity landscape. Phishing, a fraudulent technique in which attackers masquerade as a trusted company to manipulate individuals into revealing sensitive information, poses a significant threat to individuals and organizations [1]. Advanced machine learning plays a key role in strengthening security against such threats. One such powerful tool is CatBoost, a booster library known for its performance and accuracy. This article explores how CatBoost performs in phishing detection, providing robust solutions to protect against malicious online activity.
Understanding CatBoost:
CatBoost, short for Categorical Boosting, is a machine learning algorithm specifically designed to support categorical features [2]. Developed by Yandex, CatBoost excels at processing categorical data, making it particularly suitable for applications such as fraud detection, and in our case phishing detection [3].
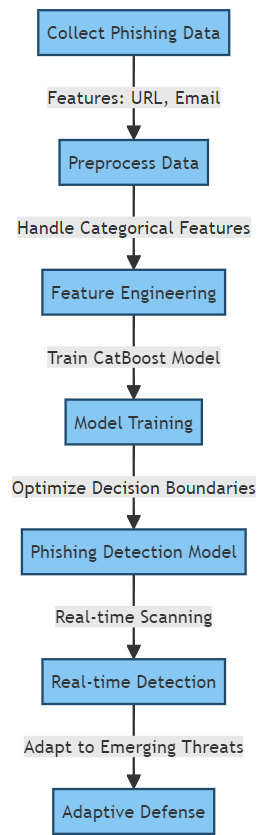
Key Features of CatBoost:
Categorical Feature Support:
CatBoost is adept at handling hierarchical features without requiring extensive preprocessing. In phishing detection, where URLs and email addresses are often critical elements, CatBoost’s ability to seamlessly add categorical data will prove invaluable.
Robustness to overfitting:
CatBoost incorporates a technique called ordered boosting, which naturally prevents overloading. This is important in phishing detection models, as they must be designed properly to detect previously unnoticed malicious patterns.
Effective handling of missing data:
Real-world data sets are often full of missing values. CatBoost provides an efficient way to handle missing data, ensuring that model performance does not deteriorate in the face of incomplete information.
Model Interpretability:
In cybersecurity, definability is paramount. CatBoost provides a feature importance score, allowing analysts to understand which features contribute most to the model’s decision-making process. This transparency is essential to identify and mitigate potential vulnerabilities.
Application of CatBoost in Phishing Detection:
Feature Engineering:
Phishing detection patterns depend on a variety of factors, such as URL structure, domain name, and email content. CatBoost’s ability to handle categorical features makes it easy to incorporate these important features into the model.
Training the model:
During the training phase, CatBoost optimizes decision boundaries based on the given features. Its hierarchical boosting approach ensures that it accurately catches subtle phishing schemes, making it more effective at differentiating between legitimate and malicious activity
Real-time detection:
CatBoost’s fast predictive capabilities make it suitable for real-time phishing detection. As new phishing techniques emerge, the paradigm can evolve rapidly, continually increasing an organization’s level of cybersecurity.
Adaptability to Evolving Threats:
Phishing attacks are dynamic and persistent to circumvent traditional security measures. CatBoost’s adaptability allows it to stay ahead of emerging threats by learning from new data and adjusting its decision boundaries accordingly.
Conclusion:
CatBoost stands as a formidable ally in the ongoing fight against phishing attacks. His prowess in essays with serious aspects, stability of fitness, skilled Modder talk and acquisition options for the construction of a better option for ideal option for ideal options of the cybers and religions continues as advanced employee of the evolaris like catboost. and Fishing- efforts to protect against the ever-present danger of attack.
References:
- Fang, L. C., Ayop, Z., Anawar, S., Othman, N. F., Harum, N., & Abdullah, R. S. (2021). Url phishing detection system utilizing catboost machine learning approach. International Journal of Computer Science & Network Security, 21(9), 297-302.
- Deekshitha, B., Aswitha, C., Sundar, C. S., & Deepthi, A. K. (2022). URL Based Phishing Website Detection by Using Gradient and Catboost Algorithms. Int. J. Res. Appl. Sci. Eng. Technol., 10(6), 3717-3722.
- Nguyen, N., Duong, T., Chau, T., Nguyen, V. H., Trinh, T., Tran, D., & Ho, T. (2022). A proposed model for card fraud detection based on Catboost and deep neural network. IEEE Access, 10, 96852-96861.
- Hancock, J., & Khoshgoftaar, T. M. (2020, December). Performance of catboost and xgboost in medicare fraud detection. In 2020 19th IEEE international conference on machine learning and applications (ICMLA) (pp. 572-579). IEEE.
- Chen, Y., & Han, X. (2021, January). CatBoost for fraud detection in financial transactions. In 2021 IEEE International Conference on Consumer Electronics and Computer Engineering (ICCECE) (pp. 176-179). IEEE.
- Li, Y., Mai, Y., Lin, Z., & Liang, S. (2020, July). Online transaction detection method using catboost model. In 2020 International Conference on Communications, Information System and Computer Engineering (CISCE) (pp. 236-240). IEEE.
- Cvitić, I., Perakovic, D., Gupta, B. B., & Choo, K. K. R. (2021). Boosting-based DDoS detection in internet of things systems. IEEE Internet of Things Journal, 9(3), 2109-2123.
- Alieyan, K., Almomani, A., Anbar, M., Alauthman, M., Abdullah, R., & Gupta, B. B. (2021). DNS rule-based schema to botnet detection. Enterprise Information Systems, 15(4), 545-564.
- Deveci, M., Pamucar, D., Gokasar, I., Köppen, M., & Gupta, B. B. (2022). Personal mobility in metaverse with autonomous vehicles using Q-rung orthopair fuzzy sets based OPA-RAFSI model. IEEE Transactions on Intelligent Transportation Systems.
- Chopra, M., Singh, S. K., Gupta, A., Aggarwal, K., Gupta, B. B., & Colace, F. (2022). Analysis & prognosis of sustainable development goals using big data-based approach during COVID-19 pandemic. Sustainable Technology and Entrepreneurship, 1(2), 100012.
Cite As
REDDY K.T (2023) CatBoost’s Role in Advanced Phishing Detection, Insights2Techinfo, pp.1