By: Praneeth
Internet of Things (IoT) incorporates several resources into systems that deliver complex and smart services. It is expected that about 20 billion machines would be linked together at the end of 2020. In the field of IoT, development, and accomplishment have increased dramatically. So, data security and communication threats such as eavesdropping, denial of service (DoS) attacks, jamming, and spoofing attacks in this area must be secured by progress.
The Internet of Things tends to introduce an increased accessibility period, with over an estimated 50 billion devices to be connected over the web by 2020 [1, 2]. At its essence, the IoT attempts to link previously disconnected devices to the internet, thereby allowing smart machines to fit for data processing, storage, and distribution without the need for physical communication. For customers who consider the minimum effort and operational flexibility over security [3], many of these IoT devices are gone. These market forces have led IoT manufacturers, excluding standard protection, to provide and build a range of insecure Internet-associated products, such as IP cameras, Recorder (DVR) boxes, and Digital Video. The intrinsic technical limits, the usage of default passwords, and unclear norms frequently evaluate and exemplify certain shortcomings and endeavors.
For example, activity trackers that collect and transfer data upon their user’s corresponding smartphone prevent data security leakage. It is typically restricted to IoT devices because of its minimal computing power, the capacity of energy supplies, and network bandwidth to carries out intense processing, and high resistance of sensitive security commitments, especially in the context of significant data flow [4, 5]. Deep computing and communications burdens for IoT devices are created in most of the current security mechanisms. Figure. 1 demonstrates the threat structure for IoT frameworks.
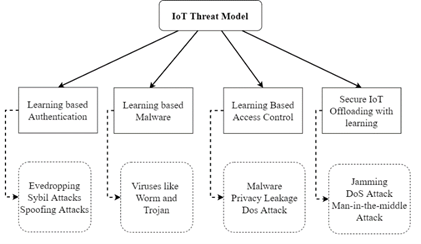
With all the IoT implementations these days, there are many complexities, complications, and limits. This paper’s goal is to resolve IoT devices’ safety issues and risks. So, it consists of many aspects, services, and interlinked systems. IoT devices, thus, are most often very exposed to threats, especially network attacks, data breaches, software threats, and physical attacks. As follows:
- Privacy leakage: Tracking devices that collect close-to-home consumer data, such as health data and location, see an elevated risk of personal privacy leakage.
- Man-in-the-middle attack: To furtively test, listen into the network then modifying the personal data transfer between IoT devices, an intruder will transmit spoofing and jamming signals.
- Software attacks: A malicious computer such as worms, viruses, Trojans and will result in company failure, IoT device value depletion, and resource loss, and privacy spillage.
- Spoofing: These threats are centered on RFID tags and MAC addresses to reach illegitimate access in the IoT network and enable attacks such as man-in-middle and denial-of-service attacks.
- Jamming: Attackers send fake signals to attack IoT devices’ which transmits persistent radio signals and thereby wastes communication speed, IoT device storage, energy, and Central Processing Unit (CPUs).
- Denial-of-service attacks: DoS and DDoS cyber-attacks are among the most critical IoT threats. By utilizing hundreds of compromised computers to destroy targeted IoT systems, an intruder starts sending a massive request. Most IoT architectures are primarily powerless against DDoS attacks by providing just minimal security measures.
IoT threat systems and learning-based IoT security mechanisms include access control, IoT authorization, intrusion identification, and safe offloading, which provide exciting safety for IoT. Many such issues need to be discussed in the application of learning-based security methods in functional IoT systems.
- Computing and interaction overhead: Most current ML-based protection systems have an intense expense of computing and interaction and involve a vast range of learning details and often a complicated feature-extraction procedure [6]. New ML strategies with lower computing and latency interaction, such as dFW, need to be explored to boost protection for IoT devices, especially for environments that lack cloud-based servers and edge processing.
- Partial State examination: Modern RL-based protection strategies presume that each training agent recognizes the exact status and determines the imminent benefit to every event in the period. In turn, the operator has to consider the wrong schemes — particularly at the start of the training phase. Even so, IoT machines typically have trouble calculating the system and threat status correctly and must prevent a safety catastrophe due to inadequate policy at the outset of the training procedure. A possible approach is transfer learning [7], which utilizes current data mining security expertise to minimize irregular exploring, speeds up training pace, and reduces the dangers of selecting inadequate defense rules during the training phase. In turn, safety recovery measures must be established to secure IoT devices from the discovery phase of the training phase.
- Backup Safety Explications: To reach a practical approach, RL-based security approaches must investigate the “poor” defense policies which can often trigger a system catastrophe for IoT devices at a first training level. Intrusion detection mechanisms focused on unsupervised training methods that often have misrecognition rates that are not qualified for IoT programs. Unsupervised and Supervised training often fails to identify threats due to oversampling, inadequate learning data, and insufficient functionality processing. Backup protection systems must also be planned and implemented with ML-based authentication mechanisms to offer stable and stable IoT facilities.
References:
- Aazam, M., St-Hilaire, M., Lung, C. H., Lambadaris, I., & Huh, E. N. (2018). IoT resource estimation challenges and modeling in fog. In Fog Computing in the Internet of Things (pp. 17-31). Springer, Cham.
- McDermott, C. D., & Petrovski, A. (2017). Investigation of computational intelligence techniques for intrusion detection in wireless sensor networks. International journal of computer networks and communications, 9(4).
- Atzori, L., Iera, A., & Morabito, G. (2010). The internet of things: A survey. Computer networks, 54(15), 2787-2805.
- Moganedi, S., & Mtsweni, J. (2017, May). Beyond the convenience of the internet of things: Security and privacy concerns. In 2017 IST-Africa Week Conference (IST-Africa) (pp. 1-10). IEEE.
- V. (2017, December 7). Q3 2017 DDoS Trends Report: 29 Percent of Attacks Employed Five or More Attack Types. Verisign Blog.
- Alsheikh, M. A., Lin, S., Niyato, D., & Tan, H. P. (2014). Machine learning in wireless sensor networks: Algorithms, strategies, and applications. IEEE Communications Surveys & Tutorials, 16(4), 1996-2018.
- Pan, S. J., & Yang, Q. (2009). A survey on transfer learning. IEEE Transactions on knowledge and data engineering, 22(10), 1345-1359.
Cite this article as
Praneeth (2021) CONSUMER DATA PROTECTION IN CLOUD AND IOT NETWORKS, Insights2Techinfo, pp.1