By: Arya Brijith, International Center for AI and Cyber Security Research and Innovations (CCRI), Asia University, Taiwan,sia University, Taiwan, arya.brijithk@gmail.com
Introduction
Information and communication technology, or ICT, is becoming more and more common with the arrival of smartphones, tablets, and laptop computers, according to a technical series on primary health care issued by the World Health Organization (WHO). Digital health technologies are changing the way health services are provided and run. These technologies range from those that help people manage their health more effectively to those that provide better means of detecting illnesses and tracking the effects of policies on population health. Cybercrime is a major obstacle to the implementation of digital transformation plans because it takes advantage of system vulnerabilities and human weaknesses. Let us discuss the importance of cybersecurity in the healthcare industry.
Importance of Cybersecurity in Healthcare
Here are a few points that illustrate the significance of cybersecurity in the healthcare industry:
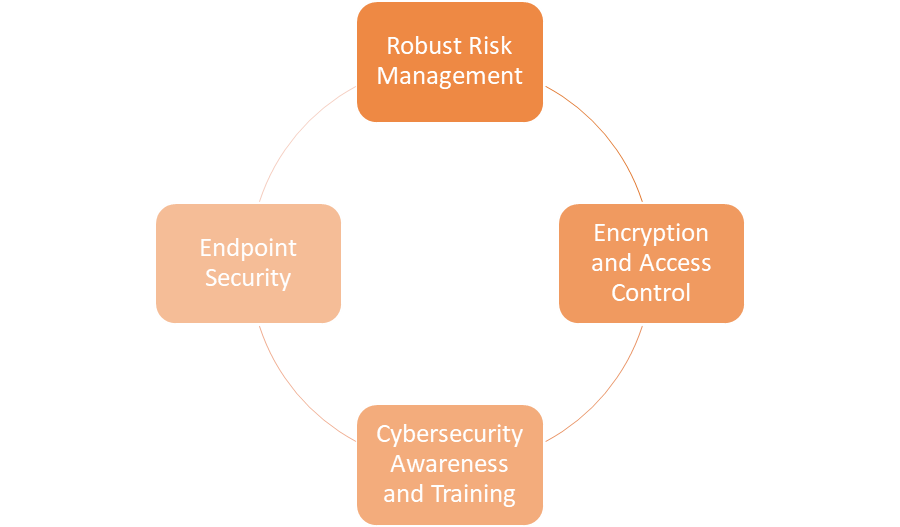
- Robust risk management: The escalation of cybersecurity events poses an increasing risk to the healthcare sector overall, and to hospitals specifically. Comprehensive risk management strategies designed for the healthcare industry are required, as are regular risk assessments.
- Encryption and Access Control: Employ robust access controls to stop unwanted access to patient data and to safeguard data while it’s in transit or at rest. The shift from conventional to digital information systems, such as Electronic Health Records (EHRs), has an impact on how these systems are secured and defended. Information security is no longer sufficient to fight off new and significant cyberattacks and threats.
- Cybersecurity awareness and training: The acceptance of addressing the dangers posed by cyber threats by healthcare professionals is a prerequisite for the effective implementation of digital transformation plans in the healthcare business. It’s critical to teach healthcare workers about cybersecurity best practices, recognize and report security issues, and cultivate a culture of security awareness.
- Endpoint security: Make sure that all systems and devices—including medical devices—are shielded by strong endpoint security solutions and that they are routinely updated with the most recent security patches.
Conclusion
Cybersecurity plays a vital role even in the field of healthcare and it is necessary to monitor the devices regularly to prevent cyber attacks. There is plenty of ongoing research being conducted in this field.
References
- Nifakos, S., Chandramouli, K., Nikolaou, C. K., Papachristou, P., Koch, S., Panaousis, E., & Bonacina, S. (2021). Influence of human factors on cyber security within healthcare organisations: A systematic review. Sensors, 21(15), 5119.
- Ali, K. A., & Alyounis, S. (2021, July). Cybersecurity in healthcare industry. In 2021 International Conference on Information Technology (ICIT) (pp. 695-701). IEEE.
- Buzdugan, A. (2020). Integration of cyber security in healthcare equipment. In 4th International Conference on Nanotechnologies and Biomedical Engineering: Proceedings of ICNBME-2019, September 18-21, 2019, Chisinau, Moldova (pp. 681-684). Springer International Publishing.
- Alsmirat, M. A., Jararweh, Y., Al-Ayyoub, M., Shehab, M. A., & Gupta, B. B. (2017). Accelerating compute intensive medical imaging segmentation algorithms using hybrid CPU-GPU implementations. Multimedia Tools and Applications, 76, 3537-3555.
- Tripathi, S., Gupta, B., Almomani, A., Mishra, A., & Veluru, S. (2013). Hadoop based defense solution to handle distributed denial of service (ddos) attacks.
- Almomani, A., Gupta, B. B., Wan, T. C., Altaher, A., & Manickam, S. (2013). Phishing dynamic evolving neural fuzzy framework for online detection zero-day phishing email. arXiv preprint arXiv:1302.0629.
- Gupta, B. B., Joshi, R. C., & Misra, M. (2012). ANN based scheme to predict number of zombies in a DDoS attack. Int. J. Netw. Secur., 14(2), 61-70.
- Bhatti, M. H., Khan, J., Khan, M. U. G., Iqbal, R., Aloqaily, M., Jararweh, Y., & Gupta, B. (2019). Soft computing-based EEG classification by optimal feature selection and neural networks. IEEE Transactions on Industrial Informatics, 15(10), 5747-5754.
Cite As
Brijith A. (2023) Cyber Security in Healthcare, Insights2Techinfo, pp.1