By: Nicko Cajes; Northern Bukidnon State College, Philippines
Abstract
The utilization of botnets has been widely noticed together with the rising problem of DDoS attack. This became a threat in the emergence of automated systems and made traditional defense mechanisms incapable of detecting them. The use of SYN, UDP, and HTTP flood are among the most common methods of how attackers commence their attack, making a huge damage to businesses which causes damage generally. Incidents related to this attack have already been revealed by security companies highlighting the sophisticated method attackers used, giving the spot to AI as one of the solutions in this ever-evolving cyber problem.
Introduction
Numerous scattered devices, often known as bots, orchestrate and carry out DDoS assaults by flooding the target with traffic intended for attack, this is done by the attacker by interfering with the target server’s operations and flooding the server that was targeted with web traffic through geographically separated devices, rendering the computer or network inaccessible to authorized users [1, 2]. The rapid growth of automated systems raised the risk of DDoS incidents. Due to the incredible number of devices that are connected, the ever-changing network conditions, and the requirement for immediate response, traditional DDoS detection techniques are no longer sufficient [3]. This article will dive into the deep understanding of DDoS attacks, aiming to comprehensively explain how it can lead to cyber disruptions.
How DDoS Attack Work
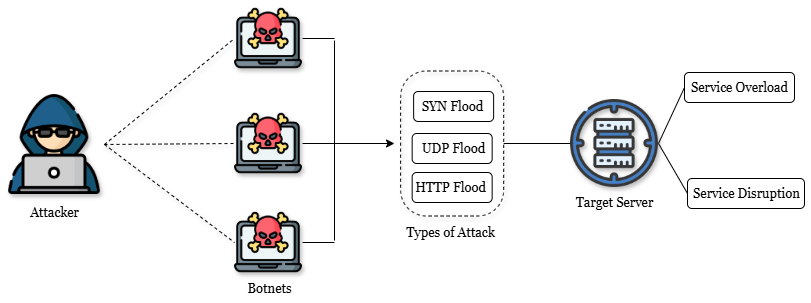
Together with the introduction of technological advances, hackers now have access to a far wider variety of assets, enabling them to launch digital attacks that do more harm with a lesser amount of work. Nowadays, structured, remotely managed networks of bots are used to carry out a variety of DDoS attacks. Botnets like these are made up of countless malware-infected computer systems that continually transmit massive amounts of data towards the targeted system, slowing it considerably and ultimately causing it to go down. By removing the possibility of an originating IP address being traced back, using a bot army to carry out a successful attack safeguards the hacker’s identity. Additionally, it significantly increases the intensity of DDoS attacks [4]. Different ways to attack can be done by the attackers, however there are most common methods used such as the SYN Flood, UDP Flood, and HTTP Flood.
SYN Flood: DDoS attack known as SYN flooding, attempt to overload the target’s host machine using a significant amount of UDP packet traffic, SYN/SYN fragments, or ICMP traffic. Such incidents specifically arise whenever one or more servers are overloaded with TCP SYN segments that initiate unsuccessful TCP connection attempts, making them unavailable to reply to valid connections being made [5].
UDP Flood: A DDoS assault known as “UDP Flooding” overloads the targeted server or network component with a large number of UDP packets. UDP (User Datagram technology) is a form of data transfer technology which doesn’t verify transmitted packets or create an affiliation prior to delivering data. Attackers use UDP flooding when they transmit a large number of UDP packets to randomized ports onto the targeted server. The server’s regular functioning may be severely slowed or completely stopped as a result of network traffic and CPU resource overloading [6].
HTTP Flood: During a form of HTTP flooding attack, the attacker targets an internet server or a software program using what appear to be legitimate HTTP POST or GET requests. Compared to distinct kinds of attacks, HTTP flood uses a lesser amount of bandwidth to knock down a target’s computer because it doesn’t use reflection techniques, deceiving, or faulty packets. The attack is likely to succeed whenever a system or program is pushed to allocate as many resources as possible in response to each request [7].
Impact of DDoS Attack
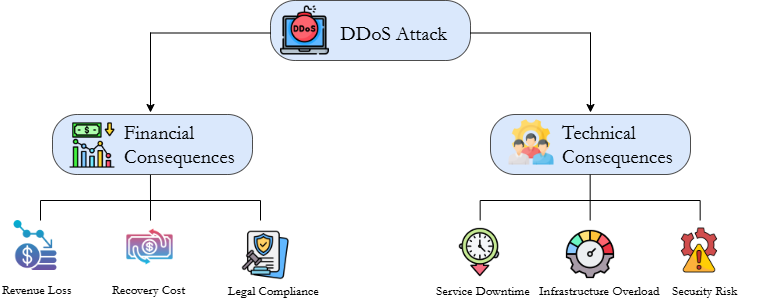
The huge threat of DDoS attacks cannot be neglected, as it can cause huge damage to individuals, especially to businesses. The interruption of operations is the primary direct consequence of a DDoS attack. Unplanned downtime immediately results in lost income for companies that depend on online sales, like retail outlets and services with subscriptions. Long-term or frequent service outages can harm a business’s reputation. After a DDoS assault, recovery can be costly. Expenses might involve paying for response to incidents by cybercrime specialists, purchasing extra safety precautions, and possibly repaying impacted clients. Businesses who neglect to safeguard client data throughout a breach could be subject to legal and legislative implications, varying according to their sector of business. The competitive advantage of a business can be undermined by a persistent attack that interferes with its activities [8].
Cloudflare revealed a real-life DDoS attack that hits well-known betting and gaming businesses. Cloudflare stopped thousands of hyper-volumetric HTTP DDoS assaults in the month of August 2023, including 89 that cost more than one hundred million RPS. During its highest point, the greatest attack reached 201 million RPS, surpassing the prior record of 71 million RPS, that had been set around February 2023 [9].
Defensive Measurement Against DDoS
Due to the huge threat which DDoS attack poses, proactive and sophisticated measures have been implemented aiming to somehow mitigate the rising problem of its sophistication, this includes the use of AI and automated threat detection as it has a lot of unique characteristics [10]. AI can mimic the way humans think and the intellect of humans. Although AI is capable of reasoning more creatively compared to humans, it cannot be considered identical as intelligence among humans [11]. AI is becoming more and more popular among cybersecurity experts as a means of protecting systems from online attacks. For example, the IoT security which uses AI in examining traffic movements to find activity suggestive for a possible attack [12].
Conclusion
Attacks made through DDoS are constantly evolving, giving a vital threat to businesses and individuals. Its ability to interrupt services have caused major damages highlighting the necessity to develop a robust defense mechanism against it. Implementation of AI has been on the sight for a lot of researchers, considering its sophisticated ability it becomes the bright spot to effectively mitigate the problem of DDoS.
Reference
- Snehi, M., & Bhandari, A. (2021). Vulnerability retrospection of security solutions for software-defined Cyber–Physical System against DDoS and IoT-DDoS attacks. Computer Science Review, 40, 100371. https://doi.org/10.1016/j.cosrev.2021.100371
- Rahaman, M., Bakkireddygari, S. S., Chattopadhyay, S., Gomez, A. L., Arya, V., & Bansal, S. (2024). Infrastructure and Network Security. In Metaverse Security Paradigms (pp. 108-144). IGI Global.
- Cirillo, M., Di Mauro, M., Matta, V., & Tambasco, M. (2021). Botnet identification in DDOS attacks with multiple emulation dictionaries. IEEE Transactions on Information Forensics and Security, 16, 3554–3569. https://doi.org/10.1109/tifs.2021.3082290
- Wang, Y., Su, Z., Zhang, N., Xing, R., Liu, D., Luan, T. H., & Shen, X. (2022). A survey on metaverse: fundamentals, security, and privacy. IEEE Communications Surveys & Tutorials, 25(1), 319–352. https://doi.org/10.1109/comst.2022.3202047
- Kumar, P., et al.: Safety: Early detection and mitigation of TCP SYN flood utilising entropy in SDN. Trans. Netw. Service Manag. 15, 1545–1559 (2018)
- Tymoshchuk, D., Yasniy, O., Mytnyk, M., Zagorodna, N., & Tymoshchuk, V. (2024). Detection and classification of DDoS flooding attacks by machine learning method. arXiv preprint arXiv:2412.18990.
- Sadiq A., Anwar M., Butt R. A., Masud F., Shahzad M. K., Naseem S., and Younas M., A review of phishing attacks and countermeasures for internet of things-based smart business applications in industry 4.0, Human Behavior and Emerging Technologies. (2021) 3, no. 5, 854–864, https://doi.org/10.1002/hbe2.301.
- SafeAeon Inc. (2024, November 18). The Impact of DDOS attacks on Businesses: A Comprehensive analysis. Medium. https://medium.com/@safeaeon-inc/the-impact-of-ddos-attacks-on-businesses-a-comprehensive-analysis-72c56eb4db8e
- Famous DDoS attacks: The largest DDoS attacks of all time. (n.d.). cloudflare. Retrieved February 2, 2025, from https://www.cloudflare.com/learning/ddos/famous-ddos-attacks/
- Rahaman, M., Pappachan, P., Orozco, S. M., Bansal, S., & Arya, V. (2024). AI Safety and Security. In Challenges in Large Language Model Development and AI Ethics (pp. 354-383). IGI Global.
- Xin Y., Kong L., Liu Z., Chen Y., Li Y., Zhu H., Gao M., Hou H., Wang C. Machine learning and deep learning methods for cybersecurity IEEE Access, 6 (2018), pp. 35365-35381
- Kuzlu M., Fair C., Guler O. Role of artificial intelligence in the Internet of Things (IoT) cybersecurity Discov. Internet Things, 1 (2021), pp. 1-14
- Jain, A. K., & Gupta, B. B. (2022). A survey of phishing attack techniques, defence mechanisms and open research challenges. Enterprise Information Systems, 16(4), 527-565.
- Arya V. (2023) Navigating the Threat Landscape DDoS Attacks in the Era of AI and ML, Insights2Techinfo, pp. 1
- Deveci, M., Pamucar, D., Gokasar, I., Köppen, M., & Gupta, B. B. (2022). Personal mobility in metaverse with autonomous vehicles using Q-rung orthopair fuzzy sets based OPA-RAFSI model. IEEE Transactions on Intelligent Transportation Systems, 24(12), 15642-15651.
Cite As
Cajes N. (2025) DDoS Explained: A Deep Dive into Cyber Disruptions, Insights2Techinfo, pp.1