By: Vanna karthik; Vel Tech University, Chennai, India
Abstract
One of the most common threats in the digital world today is distributed denial of service (DDoS) assaults, which seriously interrupt internet services. In order to protect networks from these severe attacks, this paper examines many DDoS defense techniques. Proactive steps, mitigation strategies, and the incorporation of AI in DDoS defense are all included in the paper. By analyzing both conventional and contemporary methods, this study offers a thorough grasp of how to strengthen networks against these kinds of attacks. The economic consequences of DDoS attacks and the need for ongoing defense strategy modification are also covered in the paper.
Introduction
DDoS assaults have advanced in sophistication due to the quick evolution of cyberthreats, and they now target networks with high traffic volumes in an effort to interrupt services. Strong protection solutions must be developed and put into place because traditional DDoS mitigation approaches frequently fail to prevent these sophisticated attacks. This study examines the state of DDoS attacks today and presents cutting-edge techniques to improve network resilience. Organizations can better prepare and protect their infrastructure against possible distractions by understanding the fundamental mechanisms of these attacks.
How DDoS attack works
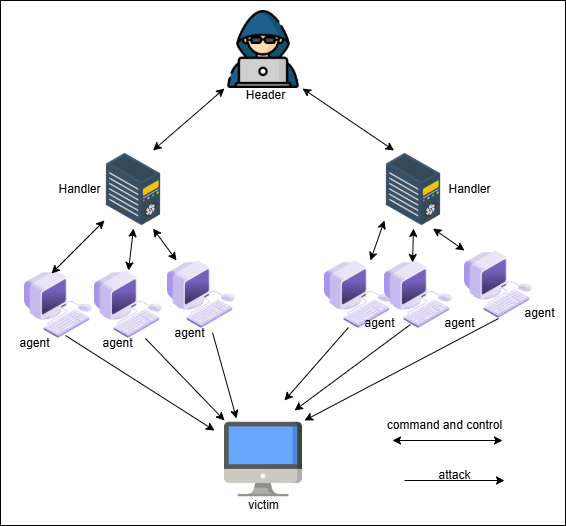
A distributed denial-of-service (DDoS) assault overloads a server or network with unacceptable Internet traffic, causing it to malfunction. In their most severe form, these attacks have the ability to take down a network or a website for extended periods of time.
DDoS attacks function by sending malicious traffic through numerous computers or machines to a target. A botnet is a collection of compromised devices that may be managed by a single attacker. These computers frequently constitute a botnet[1].
The most advanced type of DoS attack is the DDoS attack. Its capacity to use its weapons in a “distributed” manner throughout the Internet and to combine these forces to produce deadly traffic sets it apart from previous attacks[2].
To DDoS their targets, attackers may employ one or more of the following tactics:
By flooding the target’s server and network resources with what appear to be authentic HTTP requests, application-layer attacks—also referred to as layer 7 DDoS attacks—cause a denial of service.
Protocol assaults, also known as state-exhaustion attacks, use layer 3 or 4 protocols (like ICMP) to send a deluge of unwanted traffic to their target, overwhelming network infrastructure and equipment[1].
DDoS prevention tools
Web application firewall (WAF): By filtering, inspecting, and blocking dangerous HTTP traffic between web applications and the Internet using customizable policies, a WAF assists in the prevention of attacks. Organizations can use a WAF to limit inbound traffic from particular IP addresses and regions by enforcing a positive and negative security approach[1].
Always on DDoS mitigation : Through constant network traffic analysis, policy modifications in reaction to new attack trends, and the provision of a wide and dependable network of data centers, a DDoS mitigation service may help in the prevention of DDoS attacks. Search for a cloud-based DDoS mitigation service provider that provides scalable, adaptive, and always-on threat defense against complex and frequent attacks[1].
DDoS prevention methods[1]
Attack surface reduction: The impact of a DDoS assault can be reduced by limiting the exposure of the attack surface. Limiting traffic to designated areas, putting in place a load balancer, and preventing communication from out-of-date or unused ports, protocols, and apps are some ways to reduce this risk.
Anycast network diffusion: By distributing traffic over several dispersed servers, an Anycast network reduces outages and increases the surface area of a company’s network, making it easier to handle huge traffic spikes.
Real-time, adaptive threat monitoring: By examining network traffic patterns, keeping an eye out for traffic spikes or other odd activity, and adjusting to protect against malicious or unusual requests, protocols, and IP blocks, log monitoring can assist in identifying possible risks.
Caching: To reduce the number of requests that original servers must handle, copies of requested material are kept in a cache. Caching resources with a content delivery network (CDN) can reduce the burden on a company’s servers and make it harder for fraudulent and legal queries to overload them.
Conclusion
DDoS attacks unquestionably pose a significant threat to the Internet’s growth and widespread adoption by the public, skeptics in the government, and corporations.I attempted to provide a comprehensive understanding of the DDoS assault issue and the many protection strategies that have been put out in this paper. With a clearer understanding of the issue, we can think more clearly and come up with better ways to deal with DDoS attacks. The creation of DDoS attack and defensive categories has several benefits, one of which allows researchers to collaborate and communicate effectively, identifying more flaws in the DDoS area.
References
- “How to prevent DDoS attacks | Methods and tools.” Accessed: Jan. 09, 2025. [Online]. Available: https://www.cloudflare.com/learning/ddos/how-to-prevent-ddos-attacks/
- C. Douligeris and A. Mitrokotsa, “DDoS attacks and defense mechanisms: classification and state-of-the-art,” Comput. Netw., vol. 44, no. 5, pp. 643–666, Apr. 2004, doi: 10.1016/j.comnet.2003.10.003.
- “DDoS attack architecture. | Download Scientific Diagram.” Accessed: Jan. 09, 2025. [Online]. Available: https://www.researchgate.net/figure/DDoS-attack-architecture_fig1_283339435
- Gupta, P., Yadav, K., Gupta, B. B., Alazab, M., & Gadekallu, T. R. (2023). A novel data poisoning attack in federated learning based on inverted loss function. Computers & Security, 130, 103270.
- Gaurav, A., Gupta, B. B., & Panigrahi, P. K. (2023). A comprehensive survey on machine learning approaches for malware detection in IoT-based enterprise information system. Enterprise Information Systems, 17(3), 2023764.
- Almomani, A., Alauthman, M., Shatnawi, M. T., Alweshah, M., Alrosan, A., Alomoush, W., & Gupta, B. B. (2022). Phishing website detection with semantic features based on machine learning classifiers: a comparative study. International Journal on Semantic Web and Information Systems (IJSWIS), 18(1), 1-24.
- Spoorthi K.S. (2024) The Cost of Implementing Generative AI Solutions, Insights2Techinfo, pp.1
Cite As
Karthik V. (2025) DDoS Protection Strategies : How to Safeguard Your Network against Massive Attacks, Insights2techinfo pp.1