By: Soo Nee Kee1,2
1Universiti Malaya, Kuala Lumpur, Malaysia.
2International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan Email: nee.kee2001.nks@gmail.com
Abstract
IoT-based healthcare system provides efficient solutions to store medical records. All IoT devices such as wearable devices, connected inhalers and pulse oximeters connected to internet to gather patient health information in real-time, providing effective way to track patient health conditions. Nonetheless, it also brings security vulnerabilities due to the increasing number of devices and massive medical records. The main security threats are phishing, Denial of Service (DoS) attacks, and data theft. Therefore, a blockchain-based distributed application is proposed to mitigate phishing attacks.
Keywords: Healthcare, Phishing, IoT, Blockchain, AES-256
Introduction
Blockchain technology is a decentralized ledger that stores data in a distributed manner, eliminating the need for centralized storage and third-party authorities and prevent single point failures. Data is stored in blocks and each block is connected to previous blocks via cryptographic chain, preventing the tampering of data and malicious changes. The immutability nature of blockchain ensures that once the data is recorded, it cannot be deleted or modified, which enhances the security of the system and fosters user trust. [1] Blockchain provides transparency and traceability to smart healthcare systems. Thus, patients or health centers can track the transactions and prevent phishing.
Techniques
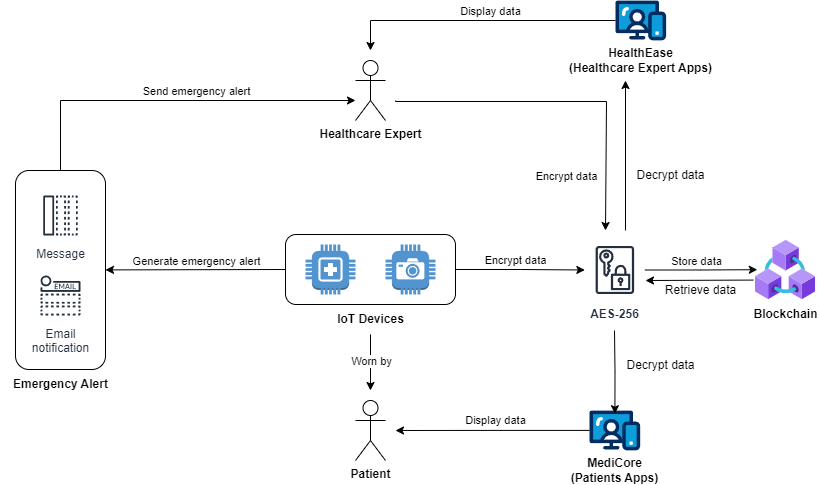
The paper proposed an integration of blockchain-based storage with IoT-based smart healthcare system to prevent phishing. There are five main entities in this system: patients, healthcare experts, blockchain, applications or websites, and IoT devices. All medical records, patient’s privacy data and healthcare experts’ data are stored in the blockchain to prevent tampering of data and improve the security of healthcare systems. Data will be encrypted using AES-256 before being stored in the blockchain to strengthen the security of the system. IoT devices detect and gather patients’ health data. For example, wearable devices like smartwatches can be used to detect patients’ health conditions like blood oxygen levels and heartbeat rate. All data gathered will be transferred to the application for analysis and stored in the blockchain. Besides, wearable devices also can give reminders to the patients like medication time and sleep time. When an emergency occurs, the smartwatches also will send alerts to the patients, their emergency contacts and healthcare experts. Applications or websites are used to do analysis and display medical records. It provides user-friendly interface that allows patients and healthcare experts to interact with it and access the blockchain. There are two types of application interfaces: one is for patient use (HealthEase), and another is for internal use (MediCore). Healthcare experts and patients must register accounts before using this blockchain-based healthcare system and their data during registration will be stored in the blockchain. Once the identities of healthcare experts are verified, they are able to view and manage patient data through MediCore. If a patient requests medical reports, he can send request through HealthEase and wait for approval from healthcare experts. Once get approval, medical reports will be retrieved from the blockchain. [2]
Conclusion
In conclusion, the integration of blockchain and IoT-based healthcare systems can effectively prevent phishing as the blockchain provides traceable and transparent platforms to store data. The encryption method AES-256 further strengthens the system security and protects the privacy data leakage. In addition, the use of IoT devices can help to track the patients’ conditions in real-time, reducing the need of visiting hospitals frequently and providing an effective way to monitor their health and respond promptly to any emergency. The two types of application interfaces provide a user-friendly experience and avoid data leakage by assigning role-based access. For example, patients cannot access healthcare experts’ data, protecting the sensitive data and ensuring only authorized users can access it.
Reference
- “Exploring the integration of edge computing and blockchain IoT: Principles, architectures, security, and applications – ScienceDirect.” Accessed: Oct. 04, 2024. [Online]. Available: https://www.sciencedirect.com/science/article/pii/S1084804524000614
- P. Sharma, S. Namasudra, N. Chilamkurti, B.-G. Kim, and R. Gonzalez Crespo, “Blockchain-Based Privacy Preservation for IoT-Enabled Healthcare System,” ACM Trans Sen Netw, vol. 19, no. 3, p. 56:1-56:17, Mar. 2023, doi: 10.1145/3577926.
- A. Gaurav, B. B. Gupta, K. T. Chui and V. Arya, “Enhancing Email Security in Consumer Electronics with a Hybrid Deep Learning Approach,” 2024 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 2024, pp. 1-5, doi: 10.1109/ICCE59016.2024.10444468.
- T. Zhang, J. Shen, H. Yang, P. Vijayakumar, B. B. Gupta and V. Arya, “Sustainable Authentication and Key Agreement Protocol Using Chaotic Maps for Industry 5.0,” in IEEE Transactions on Consumer Electronics, vol. 70, no. 1, pp. 1580-1589, Feb. 2024, doi: 10.1109/TCE.2023.3339818.
- Tian, Y., Tan, H., Shen, J., Pandi, V., Gupta, B. B., & Arya, V. (2023). Efficient identity-based multi-copy data sharing auditing scheme with decentralized trust management. Information Sciences, 644, 119255.
Cite As
Kee S.N. (2024) Detecting and Preventing Phishing Attacks in IoT-Based Smart Healthcare Systems, Insights2Techinfo, pp.1