By: Achit Katiyar1,2
1South Asian University, New Delhi, India.
2International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan. Email: achitktr@gmail.com
Abstract
Cloud computing is most important for today’s IT system. It gives us flexible & scalable resources. But it also brings up some big security concerns. However, there are some big threats to security. There is another concept by using quantum-inspired evolutionary algorithms (QIEAs). QIEAs use ideas from quantum computing and evolutionary algorithms to make security systems better and more efficient. In this article, we will explore that how QIEAs can be helpful for the security of cloud computing. This article presents their uses and benefits, as well as the challenges they might face.
Introduction
These days many organizations are using cloud computing for their work. So, the safety of these cloud computing systems is very important [1]. Traditional security measures often find it challenging to keep pace with the increasing volume of threats. This can be easily achieved with the help of the QIEAs to enhance cloud security pattern [2]. Cloud computing is also appealing in that it can offer an elastic and utilitarian environment on which and where one can develop and deploy. Real-time accessibility and the setup’s accountability is another reason why organizations are drawn towards this cloud model [3]. Cloud computing platforms may be classified into three types based on their access policies: the public cloud, private cloud and the community cloud [4]. In this article, the details regarding the principles of QIEAs will be revealed, the integration of QIEAs in cloud security, and some of the challenges that are related to integration of QIEAs in cloud security will also be described in detail [5].
Quantum-inspired Evolutionary Algorithms
The QIEAs is an evolutionary algorithms including quantum computing attributes such as superposition and entanglement [2]. These algorithms utilize quantum bits or qubits to represent the multiple states and thus make the search and the optimization algorithms faster [6].
- Quantum Genetic Algorithms (QGA):
QGAs increase classical genetic algorithms through the application of quantum mechanics [2]. The new proposed GA incorporates the quantum effect which entails the superposition and the interferences with the basic genetic algorithm. It allows for better exploration of a larger solution space [6].
Application in Cloud Security-
They can be also incorporated in cloud systems to describe the security level of the system and prescriptions for the same. They help one to be proactive particularly where risks are involved that may not be easily predictable, or are latent [2]. Secondly, these algorithm also constantly alter the condition for marking the malware and that further increases the possibility of the detection of system [6]. The working process of the genetic algorithm is shown is figure 1.
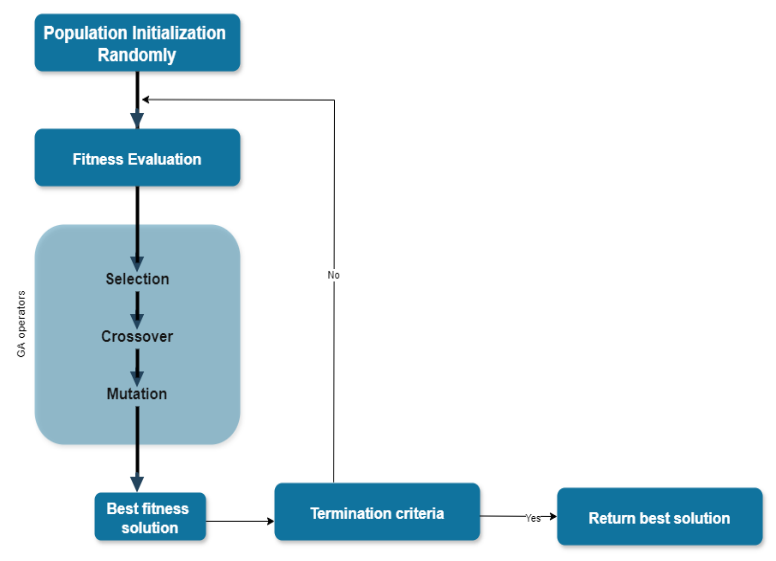
- Quantum-inspired Particle Swarm Optimization (QPSO):
QPSO is method that is derived from the PSO under the concepts of the quantum mechanics. This means that the particles are able to scan the solution space in order to arrive at the best real solution [7]. Faster convergence and improved optimization performance.
Application in Cloud Security-
In cloud data organizations, QPSO can optimize how virtual machines are deployed and how resources are allocated. This approach boosts security while minimizing potential attack surfaces significantly [7].
Challenges of Implementing QIEAs
- Computational complexity:
QIEAs are indeed effective, but they can be tough regarding computation [2]. This is because of complicated nature of quantum methods. Flexibility, along with performance in large-scale cloud systems, remains a major problem [6].
- Quantum-Specific Knowledge:
To implement QIEAs, having specialized knowledge in both quantum computing & evolutionary algorithms is a must. This requirement can create challenges for many purposes [7]. To effectively implement these algorithms, the trainings and skills that have been outlined were needed.
- Integration of Existing Systems
Implementing QIEAs with these current clouds and security infrastructures can be rather challenges. Compatibility has to be established [1]. These system’s optimality indeed depends on efficiency; in other words, a smooth running to maximize the benefit derived from the systems.
Emerging trends and future directions
- Hybrid Quantum–Classical Approaches:
There is evidence that shows when one uses traditional algorithms in combination with quantum-inspired ones, the overall performance of the used algorithms is enhanced and can lead to computing problem solving [2]. The two paradigms are combined in hybrid techniques that have favourable qualities of both of them and offer good solutions for security purposes.
- Quantum Machine Learning:
The combination of traditional quantum-inspired evolutionary bio-inspired approaches with machine learning can improve threat identification and management [2]. Application of machine learning in the quantum realm can be useful in transcending classical methods of evaluating security threats.
Conclusion
It is possible that this type of evolutionary algorithms serves as further development in cloud computing security leveraging quantum solutions. These algorithms which incorporated with quantum computation procedures provide improvements in versatility, productivity & adaptability in managing security aspects. Despite serious challenges in implementation, the opportunities given by QIEAs justify the integration of the system within cloud security. It is believed that future research to improve their efficiency are expected to be conducted on hybrid techniques & quantum machine learning.
References
- M. Zhou, R. Zhang, W. Xie, W. Qian, and A. Zhou, “Security and Privacy in Cloud Computing: A Survey,” presented at the Semantics Knowledge and Grid (SKG), 2010 Sixth International Conference On, Dec. 2010, pp. 105–112. doi: 10.1109/SKG.2010.19.
- K.-H. Han and J.-H. Kim, “Quantum-inspired evolutionary algorithm for a class of combinatorial optimization,” IEEE Trans. Evol. Comput., vol. 6, no. 6, pp. 580–593, Dec. 2002, doi: 10.1109/TEVC.2002.804320.
- T. Haksoro, A. S. Aisjah, Sreerakuvandana, M. Rahaman, and T. R. Biyanto, “Enhancing Techno Economic Efficiency of FTC Distillation Using Cloud-Based Stochastic Algorithm,” Int. J. Cloud Appl. Comput. IJCAC, vol. 13, no. 1, pp. 1–16, Jan. 2023, doi: 10.4018/IJCAC.332408.
- B. B. Gupta, A. Gaurav, and D. Peraković, “A Big Data and Deep Learning based Approach for DDoS Detection in Cloud Computing Environment,” in 2021 IEEE 10th Global Conference on Consumer Electronics (GCCE), Oct. 2021, pp. 287–290. doi: 10.1109/GCCE53005.2021.9622091.
- A. M. Widodo et al., “Quantum-Resistant Cryptography,” in Innovations in Modern Cryptography, IGI Global, 2024, pp. 100–130. doi: 10.4018/979-8-3693-5330-1.ch005.
- A. Narayanan and M. Moore, “Quantum-inspired genetic algorithms,” in Proceedings of IEEE International Conference on Evolutionary Computation, May 1996, pp. 61–66. doi: 10.1109/ICEC.1996.542334.
- J. Sun, B. Feng, and W. Xu, “Particle swarm optimization with particles having quantum behavior,” in Proceedings of the 2004 Congress on Evolutionary Computation (IEEE Cat. No.04TH8753), Jun. 2004, pp. 325-331 Vol.1. doi: 10.1109/CEC.2004.1330875.
- T. Zhang, J. Shen, H. Yang, P. Vijayakumar, B. B. Gupta and V. Arya, “Sustainable Authentication and Key Agreement Protocol Using Chaotic Maps for Industry 5.0,” in IEEE Transactions on Consumer Electronics, vol. 70, no. 1, pp. 1580-1589, Feb. 2024, doi: 10.1109/TCE.2023.3339818.
- Tian, Y., Tan, H., Shen, J., Pandi, V., Gupta, B. B., & Arya, V. (2023). Efficient identity-based multi-copy data sharing auditing scheme with decentralized trust management. Information Sciences, 644, 119255.
Cite As
Katiyar A. (2024) Enhancing Cloud Computing Security Through Quantum-Inspired Evolutionary Approaches, Insights2Techinfo, pp.1