By: Soo Nee Kee1,2
1Universiti Malaya, Kuala Lumpur, Malaysia.
2International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan Email: nee.kee2001.nks@gmail.com
Abstract
With the rapid growth of IoT ecosystems, many industries have used IoT in their operations in order to automate monitoring and enhance resources management. IoT devices provide real-time monitoring, data collection and remote control, enhancing the efficiency of operation process. Industries such as healthcare, logistics, agriculture and supply chain beneficial from IoT to collect data and analyse collected data in real-time, improving yields and providing predictions for their business. The interconnected IoT supports better decision making, reduce human intervention and reduce mundane and repetitive workload, which lead to significant cost savings in term of operational costs and recourse allocation. Despite IoT has brought a lot of benefits to us, its security risks are still the main concern due to its weak security protocols, vast amounts of IoT devices and network traffics, making IoT ecosystems attractive targets for attackers. Cybersecurity issues like data leakage, unauthorized access and phishing attacks might occur. Every connected device can become an entry point for attackers to break into IoT networks to explore sensitive data and manipulate device functionality. To address phishing vulnerabilities, blockchain and federated learning are integrated in IoT ecosystem.
Keywords: Blockchain, federated learning, five-layer architecture, IoT, phishing, security
Introduction
Federated learning is a deep learning that train data on each IoT devices, eliminating the need of transferring data across the network, ensuring security of the privacy of data while reducing network bandwidth usage. Each local model will share updates with others after training completed to enhance overall model accuracy and phishing detection capabilities. The updated global model is deployed on IoT devices to perform real-time phishing detection. [1]
Blockchain is a decentralized ledger that provides distributed storage for all users. It is utilized in many sectors nowadays to store transactions in a secure manner to enhance data security and accountability due to its transparency, immutability and traceability nature. Data is stored in block and all blocks are linked together via cryptographic chain, making it impossible to be altered as all malicious changes can be tracked. Users can observer the entire view of the blockchain which foster users’ trust. There are three main types of blockchain: permissioned, permissionless and consortium blockchain. Permissioned blockchain means a blockchain-based system that only accessible by identified participants while permissionless blockchain can be accessed by anyone, which means participants can join and leave the blockchain services freely. Consortium blockchain is a hybrid model that combines both permissioned and permissionless blockchain. Consortium blockchain is controlled by a group of selected organizations. It is only accessible by authorized entities, but the system data is shared publicly. Consortium blockchain is widely used in industries that have collaboration between trust parties as it provides high level of security compared to permissionless blockchain, while maintaining decentralized and transparency. [2] The use of blockchain depends on the specific requirements such as level of control, privacy, and transparency needed of the systems.
Techniques
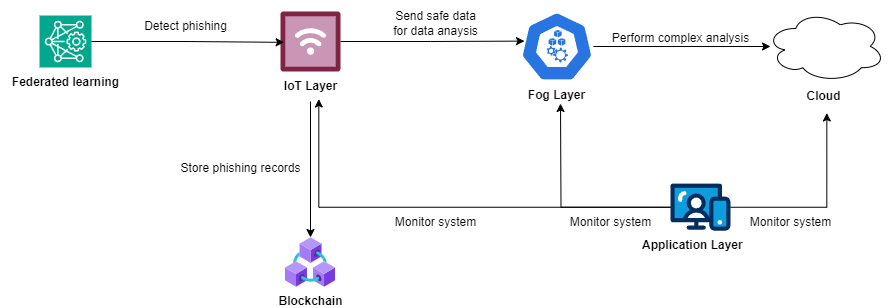
In this paper, a five-layer decentralized phishing detection mechanism using blockchain and federated learning is proposed. The five main layers are: IoT layer, fog layer, cloud layer, blockchain layer, and application layer. In blockchain layer, blockchain acts as a storage that stores phishing contents. Since it is immutable, attackers cannot alter or delete the stored data on blockchain ensuring trustworthy and transparent of phishing records. The use of smart contracts automates storing process based on predefined rules, eliminating human intervention and improving system efficiency. IoT layer consists of all IoT devices that gather data and perform federated learning to identify phishing attempts. Once phishing is detected, IoT devices will send the records to blockchain to be stored. This can prevent phishing attacks from the bottom up. The safe data will then be sent to fog layer to further process.
Fog layer serves as an intermediary between IoT layer and cloud. It processes data locally to reduce network latency and offload of cloud. It detects anomalies and supports faster decision making, making the system more responsive. Let’s us look at an example of smart agriculture, if the surrounding temperature is higher than normal, fog devices will analyse and response to the abnormal temperature by sending instructions to IoT devices to lower down temperature. Cloud layer provides advanced computational capabilities to perform more complex tasks that require higher processing power and storage such as running large-scale data analysis. Application layer is the layer that provides interaction of the system to users by using user-friendly interface such as mobile apps, dashboards or websites. Thus, users are able to view, manage and control the entire system in real-time. [3]
Conclusion
In conclusion, the integration of blockchain and federated learning in IoT ecosystems provides robust phishing detection mechanism, enhancing the system security and accountability. The five-layer architecture demonstrates the cooperation and communication between each layer, providing seamless operations for data transmission, data storage and data analysis in secure and decentralized manner. Federated learning ensures that systems can response to any anomalies immediately while protecting the privacy data without transferring to other layers. Blockchain provides immutable, traceable and transparent storage to store all phishing records, where all phishing records are visible and can be alert for all IoT users
Reference
- I. Priyadarshini, “Anomaly Detection of IoT Cyberattacks in Smart Cities Using Federated Learning and Split Learning,” Big Data Cogn. Comput., vol. 8, no. 3, Art. no. 3, Feb. 2024, doi: 10.3390/bdcc8030021.
- “Exploring the integration of edge computing and blockchain IoT: Principles, architectures, security, and applications – ScienceDirect.” Accessed: Oct. 04, 2024. [Online]. Available: https://www.sciencedirect.com/science/article/pii/S1084804524000614
- Md. Moniruzzaman, S. Khezr, A. Yassine, and R. Benlamri, “Blockchain for smart homes: Review of current trends and research challenges,” Comput. Electr. Eng., vol. 83, p. 106585, May 2020, doi: 10.1016/j.compeleceng.2020.106585.
- Gupta, B. B., & Panigrahi, P. K. (2022). Analysis of the Role of Global Information Management in Advanced Decision Support Systems (DSS) for Sustainable Development. Journal of Global Information Management (JGIM), 31(2), 1-13.
- Gupta, B. B., & Narayan, S. (2021). A key-based mutual authentication framework for mobile contactless payment system using authentication server. Journal of Organizational and End User Computing (JOEUC), 33(2), 1-16.
- Gupta, B. B., & Narayan, S. (2021). A key-based mutual authentication framework for mobile contactless payment system using authentication server. Journal of Organizational and End User Computing (JOEUC), 33(2), 1-16.
Cite As
Kee S.N. (2024) IoT and Blockchain Convergence: Addressing Phishing Threats in Industrial IoT, Insights2Techinfo, pp.1