By: Nicko Cajes; Northern Bukidnon State College, Philippines
Abstract
The continuous evolution of Distributed Denial of Service (DDoS) attacks has highlighted the importance of developing a sophisticated cyber defense against it. The use of AI-powered detection utilizing the methods of machine Learning and Deep Learning have shown good potential against this attack, providing an automated detection mechanism, predictive analysis, and real-time prevention. Unique characteristics of these systems such as its ability to quickly adapt to threats, learn continuously, and improve the response time have aided its effectiveness against the sophisticated DDoS attack.
Introduction
Due to shifting hackers’ intentions and the characteristics of the methods being employed, DDoS attacks are always developing. Even now, those responsible for distributed denial of service attacks which utilize botnets to inflict thousands of dollars in damages on targets are apprehended and imprisoned [1]. According to Cisco, there will be twice as many DDoS attacks worldwide annually in 2023 from 7.9 million in 2018 to 15.4 million, the reason for that relies on historical data regarding on annual attacks until 2020 and forecasts spanning three more years [2]. Within this regard, the combination of digital security and artificial intelligence (AI) offers an aspect of promise by offering creative ways to strengthen countermeasures to combat the ever-changing threat environment [3, 4]. This article will discuss how AI-Powered detection mechanism can be effective as a guardian of modern technology against the growing problem of sophisticated attacks, highlighting its huge impact in effectively mitigating this cyber-threat.
AI-Powered DDoS Attack Detection
AI has offered a lot of opportunities in detecting cyber-attack in the modern age. This put them into the spotlight of being one of the countermeasures against it. Its powerful ability to make automated threat detection, advanced threat detection, continuous learning, and continuous learning, are just a few of its well-known strengths which other approaches cannot achieve.
Automated Threat Detection: In present time, AI-powered systems are capable of immediately recognizing and classifying risks, both recognized and unidentified. Through the analysis of extensive data coming from various sources, which includes logs, desktop and laptop computers, and traffic on the network, artificially intelligent systems are able to identify patterns and unusual behaviors that could be signs of an attack [5].
Advanced Threat Detection: Predictive analytics could be used by systems equipped with AI to spot possible dangers before they actually materialize. Artificial intelligence (AI) systems are able to detect possible safety risks and initiate preventative actions to minimize them by examining past data and finding trends [6].
Continuous Learning: Systems with AI capabilities are able to continually acquire knowledge from fresh data and adjust to changing risks. AI systems may alter their computer programs and gradually increase their preciseness and efficacy by examining emerging risks and spotting trends [6].
Common Machine Learning and Deep Learning Techniques for DDoS
Their shown effectiveness has motivated numerous researchers in developing AI-based security systems, which effectively mitigate and detect DDoS attacks. Popular AI techniques used specifically in Machine Learning which is the Support Vector Machine (SVM) and Decision Tree (DT), and for Deep Learning are Convolutional Neural Network (CNN) and Recurrent Neural Network (RNN) which will be discussed as follows [7].
SVM: SVM utilized the kernel algorithms to handle the latter, it can be easily applied for nonlinear as well as linear problems. An optimum maximal margin hyperplane that functions like a decision boundary is created utilizing the support vectors after a low-dimensional input vector has been translated towards a feature space with high dimension utilizing the kernel function. Through accurate classification of the harmless and hazardous groups, the SVM approach may more accurately and efficiently detect DDoS attacks [8].
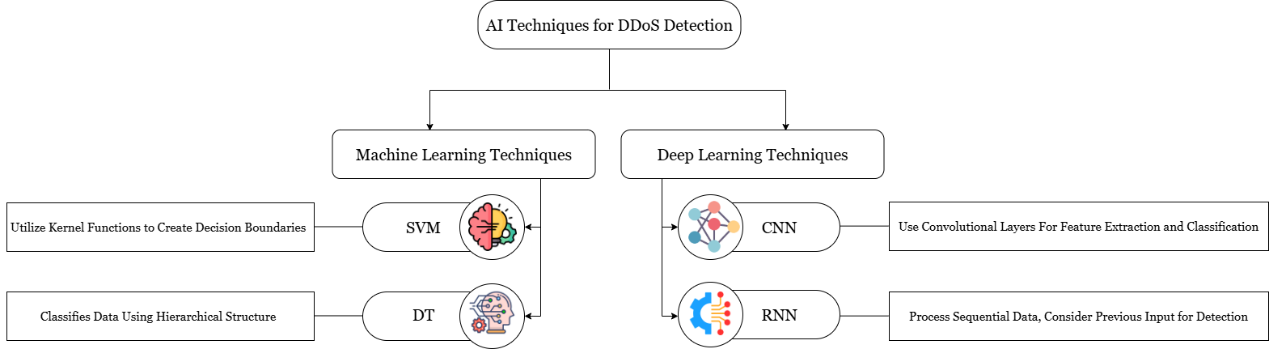
DT: A basic supervised machine learning technique that uses regression to categorize and forecast data by utilizing a collection of parameters [9]. A feature or attribute is represented by each node in the framework, which is organized into a tree comprising nodes, branches, and leaves. The branch itself represents a choice or a regulation, whereas each leaf on the branch represents a potential result or a class description. When building a tree, the DT algorithm decisively selects the best characteristics and prunes the tree to remove extra branches and avoid overfitting [10].
CNN: CNN has emerged as a type of DL framework that works effectively with signal and image data. Input layer, fully connected layer, pooling and convolutional layers are all components of a CNN. CNNs are capable of carrying out supervised feature extraction as well as classification operations for identifying DDoS activities, and they have made significant strides in the field of image processing [11].
RNN: RNNs have been designed to enhance the qualities of model sequence data and conventional feed-forward neural networks, it is composed of input, hidden, and output units, the units that are hidden serve as memories for the components. Every RNN unit takes into account the outcomes of previous inputs as well as the current input when making its choice. Semantic comprehension, handwriting prediction, audio processing, and human behavior recognition are just a few of the many domains where RNNs are frequently employed [12].
Real-Time Attack Prevention
Security professionals can identify, evaluate, and respond to security risks far more quickly and accurately when AI is used in network surveillance and retaliation. By continuously monitoring network usage, logs, and behavior-related information, artificial intelligence (AI) will swiftly spot possible dangers and unusual activity. It can also instantly recognize unusual activities by proactively evaluating the data and sending out the proper notifications. In order to aid security personnel concentrate on those most urgent dangers for immediate action, AI may additionally categorize recorded risks and rank them according to their seriousness and risk evaluation. AI is able to immediately carry out pre-established reaction actions, including patch deployment, quarantining compromised devices, and restricting fraudulent activity. This automatic reaction increases response effectiveness and decreases the duration needed for intervention by humans [13].
Conclusion
AI-powered defense mechanisms can effectively detect DDoS attacks by real-time prevention, automation, and predictive analysis. Its subsets which are Machine learning and Deep Learning have provided a useful technique providing an innovative enhancement to the cybersecurity field. Considering that the cyber-threats are constantly evolving, solutions that are AI-driven have become vital in securing the digital infrastructure, helping in preventing financial losses, and keeping the service running throughout the threat of DDoS attack, making it an important component to utilize in modern cyber-security.
Reference
- Ur Rehman, S., Khaliq, M., Imtiaz, S. I., Rasool, A., Shafiq, M., Javed, A. R., … & Bashir, A. K. (2021). DIDDOS: An approach for detection and identification of Distributed Denial of Service (DDoS) cyberattacks using Gated Recurrent Units (GRU). Future Generation Computer Systems, 118, 453-466.
- Smith, G. (2024, December 11). Top +35 DDOS Statistics (2025). StationX. https://www.stationx.net/ddos-statistics/
- Vegesna, V. V. (2023). Enhancing cyber resilience by integrating AI-Driven threat detection and mitigation strategies. Transactions on Latest Trends in Artificial Intelligence, 4(4).
- Rahaman, M., Pappachan, P., Orozco, S. M., Bansal, S., & Arya, V. (2024). AI Safety and Security. In Challenges in Large Language Model Development and AI Ethics (pp. 354-383). IGI Global.
- Kumar, R. S. AN OVERVIEW OF THE EXPECTED INFLUENCE OF WEB 3.0 ON e-COMMERCE AND ALLIED DOMAINS.
- Bharadiya, J. P. (2023). AI-driven security: how machine learning will shape the future of cybersecurity and web 3.0. American Journal of Neural Networks and Applications, 9(1), 1-7.
- Aslam, N., Srivastava, S., & Gore, M. M. (2024). A comprehensive analysis of machine learning-and deep learning-based solutions for DDoS attack detection in SDN. Arabian Journal for Science and Engineering, 49(3), 3533-3573.
- Yılmaz, A.; Küçüker, A.; Bayrak, G.; Ertekin, D.; Shafie-Khah, M.; Guerrero, J.M. An improved automated PQD classification method for distributed generators with hybrid SVM-based approach using un-decimated wavelet transform. Int. J. Electr. Power Energy Syst. 2022, 136, 107763.
- Vajrobol, V., Saxena, G. J., Pundir, A., Singh, S., B. Gupta, B., Gaurav, A., & Rahaman, M. (2024). Identify spoofing attacks in Internet of Things (IoT) environments using machine learning algorithms. Journal of High Speed Networks, 09266801241295886.
- Costa, V.G.; Pedreira, C.E. Recent advances in decision trees: An updated survey. Artif. Intell. Rev. 2022, 1–36.
- Santos, C.F.G.D.; Papa, J.P. Avoiding overfitting: A survey on regularization methods for convolutional neural networks. ACM Comput. Surv. CSUR 2022, 54, 213.
- Yadav, S.P.; Zaidi, S.; Mishra, A.; Yadav, V. Survey on machine learning in speech emotion recognition and vision systems using a recurrent neural network (RNN). Arch. Comput. Methods Eng. 2022, 29, 1753–1770.
- Gao, Y. (2024). Cyber Attacks and Defense: AI-Driven Approaches and Techniques. Academic Journal of Computing & Information Science, 7(7), 41-46.
- Hammad, M., Abd El-Latif, A. A., Hussain, A., Abd El-Samie, F. E., Gupta, B. B., Ugail, H., & Sedik, A. (2022). Deep learning models for arrhythmia detection in IoT healthcare applications. Computers and Electrical Engineering, 100, 108011.
- Chui, Kwok Tai, Brij B. Gupta, and Pandian Vasant. “A genetic algorithm optimized RNN-LSTM model for remaining useful life prediction of turbofan engine.” Electronics 10, no. 3 (2021): 285.
- Tiwari H. (2023) Defending Against DDoS Attacks: A Comprehensive Guide to vDDoS Protection tool, Insights2Techinfo, pp.1
Cite As
Cajes N. (2025) Guardians of the Web: AI-Powered DDoS Attack Detection, Insights2Techinfo, pp.1