By: Soumya Sharma ![]() , Sunil K. Singh
, Sunil K. Singh ![]()
Technology is tremendously transforming the way we work, where we work, and how we work. Even now, many billions of gadgets are intertwined with our daily lives. They are conversing with one another. They communicate with organizational data streams. And, increasingly, they affect and alter the environment in real time to provide results that were thought to be impossible only a few years back.
Communication between the Internet of Things devices, either directly or via cloud, is maturing fast. Simultaneously, sensors are becoming smaller, more efficient and cheaper, and data streams are becoming less antidotal and have easier access [1]. These developments, along with advances in data mining, software, machine learning, and AI provide a greater understanding of the link between facility and not only individual performance, but also organizational success.
What exactly is IoT?
The internet of things, or we can simply call it IoT, is intimately linked to many technological advancements or ideas, including ubiquitous computing and AI (Artificial Intelligence). One of the most crucial aspects of the IoT is that it has the ability to turn everyday things into devices. They are traceable by an IP (Internet Protocol) address, use sensors to track the state of objects, and store data on chips[2]. Because of the built-in microcomputers, they can regulate themselves, control their surroundings, and communicate data autonomously. Machine learning enables them to recognize and learn patterns, hence generalizing them so as to draw conclusions/results in order to adapt and suit to their environment and continuously improve for better enhancement.
Mini webcams, sensors, monitors, and metres measure and report on their environment. They detect motion, climatic conditions, luminosity and decibel levels and AQI among many other things. Also, they can monitor your health, maneuverability, location, routes traveled throughout space, and stress levels.
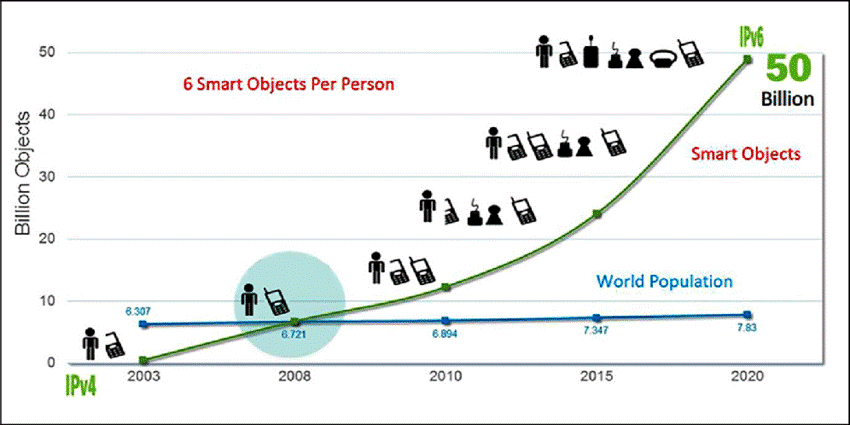
IoT has the capacity to improve and alter almost every aspect of our life. The potential of a more pleasant daily living, hence more impeccable economy and thus the administrative work. Adding on to it are safer roadways, a more environmentally friendly energy power source, a hygienic lifestyle is propelling its expansion and evolution. Mechanized coffee machines, demand-responsive industrial production and auto-pilot feature in vehicles— the possibilities and chances are endless.[5] Many tasks may be better organized using the data collected by the networked equipment.
Uses of IoT in the security world:
CCTV cameras can simply display and capture video footage; they can’t do much else. They can’t do anything about it since they don’t understand what they’re viewing. To successfully combat theft, violence, vandalism, or fire, cameras must be capable of detecting and interpreting such occurrences on their own [7]. They must also be able to communicate with different types of security systems. This is where the IoT gets some skin in the game. It transforms security monitoring into smart safety and security management by connecting cameras with devices and systems that conduct other duties.
The IoT security market is developing, and arrangements have advanced well past basic caution checking. For ventures that wish to safeguard their representatives, resources, and offices, CCTV and security capacities have helped perceivability [4]. By empowering both private and public associations to securely and remotely watch out for offices and public spots in real time with shrewd security and reconnaissance frameworks, the Internet of Things (IoT) is assisting with making urban communities, homes, and organizations more secure. You can enable building owners, organization managers, and security experts to manage and operate surveillance equipment remotely to monitor all parts of a facility by using the potential of IoT for your safety solutions[8]. Based on live security situations, one can make better judgments regarding the best course of action. It gets easier to determine whether or not there has been a false alert without having to personally investigate the place or summon law enforcement needlessly.
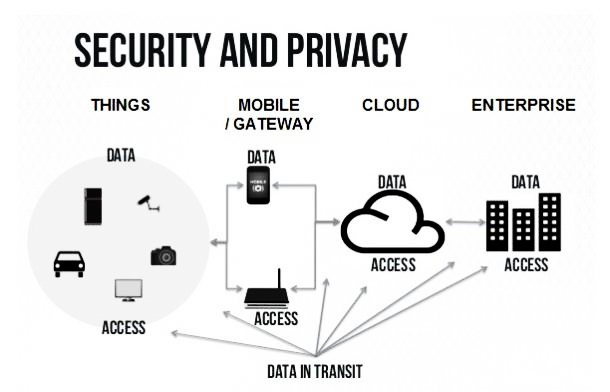
The future prospects of the IoT or as we say Internet of Things in the upcoming foreseeable future are quite promising. Increased network dexterity, combined Artificial Intelligence i.e. AI and also the ability to deploy that is to implement, automate, coordinate with other devices, and secure various use cases at big scale or hyper scale will definitely enhance advancements in the cyber industry. Like a sinusoidal wave, there is a downside to this as well. In 2016, the first IoT virus was detected which could connect all chip based devices. This resulted in a DDoS attack which flooded websites with unsolicited traffic. The assault flooded one of the world’s largest internet hosting firms, putting a number of famous websites having a high traffic rate to a standstill for many hours. This malware’s code could be edited by anyone. To paraphrase, it was “open-source”[9].
IoT is expected to hit 3.2 billion devices by the end of 2023. The paramount factor contributing to this rise in the use of this technology is the fifth-generation mobile network, popularly known as 5G. The launch of the 5G network is a colossal news for the IoT industry [8]. This is owing to the fact that 5G networks will improve performance and credibility of these linked devices many fold. Any IoT’s economic success is ultimately determined by its performance, which is determined by how rapidly it can connect with similar devices such as smartphones, apps, IoT based software or even the websites[3]. Data-transfer rates will considerably improve with 5G.
The internet of things can benefit from a variety of technologies. Despite the fact that there is no unified definition of IoT, the following qualities are usually connected with it and can be thought of to be the applications of IoT at the same time as well [10-16]:
- Collection, storage, and data processing. For example, Air conditioner changes its temperature with respect to the environment.
- Communication via clouds or directly
- Networking. For example, via Bluetooth
- Ubiquity
- Self-regulation: actions triggering a reaction automatically. For example, an electric water heater turns itself off automatically after water has reached the desired boiling point.
- Learning ability: a table lamp connected to the internet can alter its luminosity according to the surrounding environment.
References
- M. H. Miraz, M. Ali, P. S. Excell, and R. Picking, “A Review on Internet of Things (IoT), Internet of Everything (IoE) and Internet of Nano Things (IoNT)”, in 2015 Internet Technologies and Applications (ITA), pp. 219– 224, Sep. 2015, DOI: 10.1109/ITechA.2015.7317398.
- Inderpreet Singh, Sunil Kr. Singh, Sudhakar Kumar, Kriti Aggarwal (2021), “Dropout-VGG based Convolutional Neural Network for Traffic Sign Categorization”, in the proc. of 2nd Congress on Intelligent Systems (CIS 2021), Lecture Notes on Data Engineering And Communication Technologies. Springer, Berlin, Heidelberg.
- Sudhakar Kumar, Sunil Kr Singh, Naveen Aggarwal, Kriti Aggarwal, “Evaluation of automatic parallelization algorithms to minimise speculative parallelism overheads: An experiment”, pp 1517-1528, 2021 Journal of Discrete Mathematical Sciences and Cryptography, Volume 24, Issue 5 , Taylor Francis, (2021)
- P. J. Ryan and R. B. Watson, “Research Challenges for the Internet of Things: What Role Can OR Play?,” Systems, vol. 5, no. 1, pp. 1–34, 2017.
- Sudhakar Kumar, Sunil K. Singh (2021), Brain Computer Interaction (BCI): A Way to Interact with Brain Waves. Insights2Techinfo, pp. 1
- K. K. Patel, S. M. Patel, et al., “Internet of things IOT: definition, characteristics, architecture, enabling technologies, application future challenges,” International journal of engineering science and computing, vol. 6, no. 5, pp. 6122–6131, 2016.
- Z. Alansari, N. B. Anuar, A. Kamsin, M. R. Belgaum, J. Alshaer, S. Soomro, and M. H. Miraz, “Internet of Things: Infrastructure, Architecture, Security and Privacy”, in 2018 International Conference on Computing, Electronics Communications Engineering (ICCECE), pp. 150– 155, Aug 2018, DOI: 10.1109/iCCECOME.2018.8658516.
- H. U. Rehman, M. Asif, and M. Ahmad, “Future applications and research challenges of IOT,” in 2017 International Conference on Informa-tion and Communication Technologies (ICICT), pp. 68–74, Dec 2017.
- Chopra, M., Singh, S. K., Aggarwal, K., & Gupta, A. (2022). Predicting Catastrophic Events Using Machine Learning Models for Natural Language Processing. In B. Gupta, D. Peraković, A. Abd El-Latif, & D. Gupta (Ed.), Data Mining Approaches for Big Data and Sentiment Analysis in social media (pp. 223-243). IGI Global. http://doi:10.4018/978-1-7998-8413-2.ch010
- AlZu’bi, S., Hawashin, B., et al. (2019). An efficient employment of internet of multimedia things in smart and future agriculture. Multimedia Tools and Applications, 78(20), 29581-29605.
- Masud, M., Gaba, G. S., Alqahtani, S., et al. (2020). A lightweight and robust secure key establishment protocol for internet of medical things in COVID-19 patients care. IEEE Internet of Things Journal, 8(21), 15694-15703.
- Gupta, B. B., Tewari, A., Cvitić, I., Peraković, D., et al. (2022). Artificial intelligence empowered emails classifier for Internet of Things based systems in industry 4.0. Wireless networks, 28(1), 493-503.
- Yamaguchi, S., et al. (2021). Malware threat in Internet of Things and its mitigation analysis. In Research Anthology on Combating Denial-of-Service Attacks (pp. 371-387). IGI Global.
- Gupta, B. B., & Tewari, A. (2020). A Beginner’s Guide to Internet of Things Security: Attacks, Applications, Authentication, and Fundamentals. CRC Press.
- Gaurav, A., et al. (2021, January). Fog layer-based ddos attack detection approach for internet-of-things (iots) devices. In 2021 IEEE International Conference on Consumer Electronics (ICCE) (pp. 1-5). IEEE.
- Tewari, A., et al. (2018). A lightweight mutual authentication approach for RFID tags in IoT devices. International Journal of Networking and Virtual Organisations, 18(2), 97-111.
Cite this article as
Soumya Sharma, Sunil K. Singh (2022), IoT and its uses in Security surveillance, Insights2Techinfo, pp.1
Nice and Crip