By Deepak Mahto, Sudhakar Kumar
A new digital robbery has appeared in the world of cybersecurity. Rumours of a new zero-day vulnerability, Log4Shell, affecting several Minecraft servers surfaced on December 9th, 2021. A zero-day vulnerability is an exploit or flaw that is new and has not yet been studied by researchers or analysts. The exploitation of the Log4Shell vulnerability in Log4j has far-reaching implications for the digital world and security systems. Log4Shell has been discovered in millions of devices, making them insecure to this vulnerability. Log4Shell’s vulnerability might be one of the most dangerous vulnerabilities ever discovered. A zero-day vulnerability is abused when attackers discover and exploit it before IT risk analysts, specialists, and researchers can study and fix it. Log4Shell is no exception and has been similarly abused. Minecraft servers were among the first to be targeted and attacked using this vulnerability, providing a warning about the dangers of the Log4Shell vulnerability. According to Cloudflare, the vulnerability remained in the wild for at least 9 days before it was publicly revealed. So far, the first indication of Log4Shell vulnerability exploitation was discovered on December 1st, 2021. Nonetheless, widespread exploitation did not occur until the vulnerability was publicized on social media [4][8][9].

Log4Shell’s Discovery
On November 24th, 2021, Alibaba’s Cloud Security Team notified the Apache Software Foundation of a severe vulnerability in Log4j. As a result, on December 6th, 2021, Apache submitted a potential fix for this vulnerability. Through the Cloud Security team at Alibaba judged the fix insufficient to resolve the issue. On December 9th, 2021, before Apache issued the required fix, a tweet was sent out noting that utilizing JNDI Lookup in Log4j might result in RCE. The security and hacking community appears to be in a state of panic as a result of this post. The next day, Apache issued Log4j 2.15.0 as an official patch to fix the vulnerability. However, around this time, attackers began sniffing for possible victims by looking for susceptible devices. As seen in the figure, more vulnerabilities in log4j were discovered. Additionally, Mirai IoT malware incorporating a Log4Shell exploit code was discovered on December 19, 2021 [1][4][7].
Logs, Log4Shell and Log4j
Log files record how events are handled in a software application. Errors and warnings, as well as significant events, may be included in this. These instances are recorded by the program and saved to a file. Context information, timestamps, and log levels are some of the most typical components seen in application log entries. Application logs are critical to applications’ overall strategy for diagnostics and audits [6].
Log4j is an open-source Java-based logging system created in 2001 by the Apache Software Foundation. The dependencies on Log4j can be two to three layers deep, making it pervasive. The Log4j framework communicates with the Java Naming and Directory Interface (JNDI), which is commonly used in logs, settings, and attributes. JNDI may communicate with external directory services such as The Lightweight Directory Access Protocol (LDAP) across a network. Log4j will effectively treat a log message as a URL, fetch it, and even execute any executable payload included inside it with full program rights [3][8].
The vulnerability’s official name is CVE-2021-44228, although it’s also known as “Log4Shell” and “LogJam”. This security flaw is easy to exploit and allows for full Remote Code Execution (RCE) on a target system. National Institute of Standards and Technology (NIST) given the vulnerability a Common Vulnerability Scoring System (CVSS) score of 10, the maximum possible score, and Redhat, an American IBM subsidiary software corporation, given a CVSS score of 9.8. SANS (officially known as Escal Institute of Advanced Technologies) raised its Infocon alert level to yellow for the first time since the WannaCry attack in 2017. The WannaCry cyber-outbreak happened in 2017 when the WannaCry ransomware crypto-worm launched a global attack on PCs running on Windows OS. Historically, Infocon has only been upgraded to a yellow level for major accidents, demonstrating the gravity of Log4Shell [1][7].
Working on Log4Shell Vulnerability
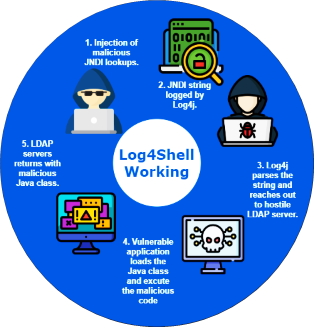
Attackers can use RCE to insert malware or potentially unwanted applications (PUA) into the system. They include the RCE starting code in a specific data request packet or payload. To effectively carry out the assault, the attacker must first select an appropriate data format that will allow them to inject Java software into the targeted machine. This method’s simplicity of usage has increased the vulnerability of Log4Shell to a critical degree. The attacks are aimed against LDAP servers, which provide access to data resources such as devices and files in the targeted network domain. When an attacker exploits the Log4j library, they have access to a “shell” that allows them to run whatever system code they want, allowing them to zero in on their target. As a result, Log4Shell exploiters may target any user who has utilized Log4j [4][2][9].
Log4Shell’s Impact
Log4Shell affects a wide variety of commercial applications and systems that use Java or Java-based software components. A critical new vulnerability identified in the Log4j framework, which is used by millions of servers, compelled the great majority of the internet-connected world to cope with it. Because many business products use Log4j, they are vulnerable to Log4Shell. Among them are Amazon, VMware, Siemens, Ruckus, Redhat, Oracle, and Splunk. This flaw affects several popular services, including Apple’s iCloud, and Twitter, and gaming applications such as Minecraft, Tencent, and Steam. Researchers found that by exploiting this important and easily exploitable weakness, hackers are installing crypto-mining malware, growing Linux botnets, and stealing sensitive data from vulnerable devices. Malware and PUAs supplied by Log4Shell vulnerability-based attacks include Khonsari ransomware, Kinsing, Mirai, SitesLoader, and XMRig [1][5].
References
- Shunichi Imano, J. S. (2021,). “Critical Apache log4j vulnerability updates: FortiGuard Labs.”. Fortinet Blog. December 21, 2021.
- “Log4Shell vulnerability response”. Splunk. (n.d.). December 15, 2021.
- Gorelik, M. (n.d.). “Protecting against the LOG4J (log4shell) vulnerability.”. December 17, 2021.
- Shantanu, K. S., K. B., Michael Vizard, Michael Vizard, R. J. “Log4Shell: The new zero-day vulnerability in LOG4J.”. Security Boulevard. December 15, 2021.
- “Which all software is affected by LOG4J shell vulnerability?”. Zyxware Technologies – Digital Services Provider – Digital Strategy Consultant. (n.d.). December 15, 2021.
- Kernel, J. (2020, May 24). “Application logs: What they are and how to use them – xpolog.”. XPLG Turn Data into Action. 2021.
- Apache. Apache Log4j security vulnerabilities. 2021, December 28..
- Berger, A., Kaar, D., Ali, A. (). “What is Log4Shell? the LOG4J vulnerability explained (and what to do about it)”. Dynatrace news. 2021, December 31.
- Allen, Z., & Tafani-Dereeper, C. “The Log4j Log4Shell vulnerability: Overview, detection, and remediation”. 2021, December 14.
Cite this article as:
Deepak Mahto, Sudhakar Kumar (2022) Log4Shell Vulnerability, Insights2Techinfo, pp.1
Very knowledgeable piece of work.
Very helpful and insightful piece of work.
Great and insightful article
Good content