By: Arya Brijith, International Center for AI and Cyber Security Research and Innovations (CCRI), Asia University, Taiwan,sia University, Taiwan, arya.brijithk@gmail.com
Abstract
Man-in-the-Middle (MitM) assaults are a stealthy hazard that can lie in seemingly secure connections inside the complexity of digital networks. This article aims to provide light on the severity of the MitM assault and the prevention methods against it.
Keywords MitM, prevention, cybersecurity, attacks, network security.
Introduction
Man-in-the-Middle (MitM) attack is one of the oldest type of cyberattack, in which the attacker pretends to be one of the end points or passively listens in on a discussion between the two end points[1]. Let us discuss about the prevention methods of the MitM attack.
What is MitM Attack?
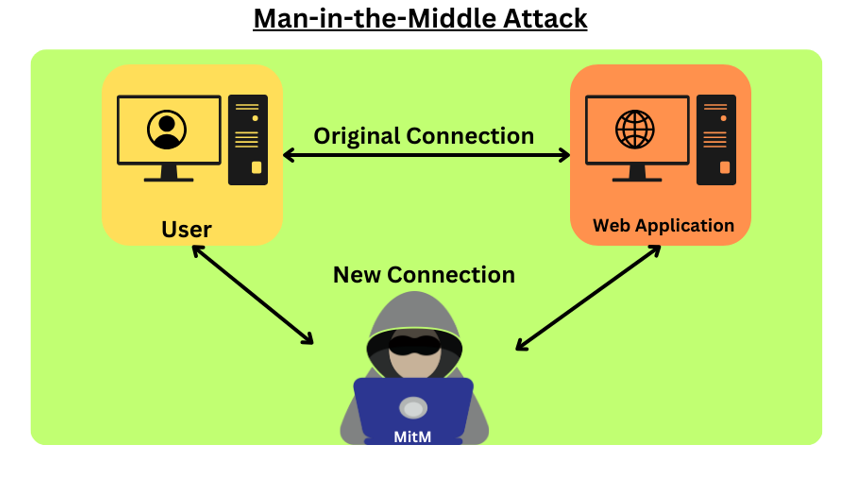
A Man-in-the-Middle (MitM) assault involves an attacker infiltrating a discussion between two devices to either eavesdrop or pretend to be one of the devices, giving the impression that regular communication is taking place. It is similar to listening in on a private discussion via the internet. To gain the cooperation of the indestructible, a competition places itself between the two sides of the thieves in this kind of attack, allowing them to change or modify the data without knowing the code.
MitM attacks leverage weaknesses in networks, from weak encryption methods to unprotected networks, to execute their clandestine activities. Attacker-used devices Session hijacking, in which user sessions are intercepted, and DNS spoofing, in which traffic is redirected to malicious sites to steal connections from attackers, alter data, or even pose as legitimate organizations, highlight the urgent need for strong security measures to counter these hidden threats in our networked digital environment.
Prevention methods
It is crucial to recognize these attacks and take protective action. A few of the preventative techniques are listed below.
- Certificate pinning[3]: A security measure called certificate pinning is used to enforce the authentication procedure in SSL/TLS connections between a server and an application. Certificate pinning links a program directly to a server-specific SSL/TLS certificate, as opposed to depending just on the system’s trust store. In order for subsequent connections to validate the server’s certificate against the pinned certificate, the server’s certificate must be stored in the application, a procedure known as “pinning.” This ensures excellent connection channel security overall.
- Secure Wi-Fi and networks: Use only safe Wi-Fi networks and those with strong passwords, encryption, and the most recent security updates. Sensitive information should not be sent over public or unsecured Wi-Fi networks as they are frequently the main targets of MitM attacks.
- Mutual Authentication[3]: Mutual authentication, also known as two-way authentication, is a security protocol that means two parties involved in a communication session, such as a client and a server Unlike traditional one-way authentication, where only the server uses its identity identifies the client Emphasis on legitimacy, reduces the risk of impersonation or man-in-the-middle (MitM) attacks, and ensures a high level of trust and security in communications through secure communications and the acknowledgment is established between the client and the server.
- Continuous Monitoring: Maintain a regular eye out for any unusual or suspect activity that could point to a potential MitM attack by monitoring network traffic and communication channels. In order to lessen the damage of such attacks, optimism and early recognition are crucial.
Conclusion
Man-in-the-middle (MitM) assaults remain a hidden menace in seemingly safe digital networks in the constantly evolving field of cybersecurity. By employing the prevention strategies, the communication channels can be protected, the authentication process can be reinforced, and early detection can be prioritized. These methods continue to serve as a guardian against the threat posed by MitM assaults in our globalized society as the digital sphere develops.
References
- Wlazlo, P., Sahu, A., Mao, Z., Huang, H., Goulart, A., Davis, K., & Zonouz, S. (2021). Man‐in‐the‐middle attacks and defence in a power system cyber‐physical testbed. IET Cyber‐Physical Systems: Theory & Applications, 6(3), 164-177.
- Javeed, D., MohammedBadamasi, U., Ndubuisi, C. O., Soomro, F., & Asif, M. (2020). Man in the middle attacks: Analysis, motivation and prevention. International Journal of Computer Networks and Communications Security, 8(7), 52-58.
- Badhwar, R. (2021). Man-in-the-Middle Attack prevention. In The CISO’s Next Frontier: AI, Post-Quantum Cryptography and Advanced Security Paradigms (pp. 223-229). Cham: Springer International Publishing.
- Wang, L., Li, L., Li, J., Li, J., Gupta, B. B., & Liu, X. (2018). Compressive sensing of medical images with confidentially homomorphic aggregations. IEEE Internet of Things Journal, 6(2), 1402-1409.
- Stergiou, C. L., Psannis, K. E., & Gupta, B. B. (2021). InFeMo: flexible big data management through a federated cloud system. ACM Transactions on Internet Technology (TOIT), 22(2), 1-22.
- Gupta, B. B., Perez, G. M., Agrawal, D. P., & Gupta, D. (2020). Handbook of computer networks and cyber security. Springer, 10, 978-3.
- Bhushan, K., & Gupta, B. B. (2017). Security challenges in cloud computing: state-of-art. International Journal of Big Data Intelligence, 4(2), 81-107.
Cite As
Brijith A. (2024) Man-in-the-Middle Attack, Insights2Techinfo, pp.1