By: Soo Nee Kee1,2
1Universiti Malaya, Kuala Lumpur, Malaysia.
2International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan Email: nee.kee2001.nks@gmail.com
Abstract
Phishing attacks occur frequently in IoT-based systems due to their various interconnectivity, each IoT device can be an entry point of phishing attempts. Attackers always exploit vulnerabilities in IoT ecosystems by sending fake URLs or emails to IoT users and persuading them to give sensitive information. This can lead to data breaches, identity theft or financial losses. Thus, this paper introduces an innovative phishing detection approach that integrating blockchain and machine learning. The proposed model not only mitigate phishing attacks, but also enables s decentralized and scalable verification.
Keywords: Phishing Detection, IoT, Machine Learning, Federated Learning, Blockchain, AI
Introduction
Internet of Things (IoT) is a distributed network of physical devices or software that connect with internet and can communicate with each other, including sensors, computers and mobile devices. IoT is widely used in many areas, from smart home to smart cities or even to smart industries like agriculture, healthcare, and transportation. Due to a huge number of connected devices and a large amount of data on IoT, it poses a variety of security challenges, including phishing. [1] Traditional security mechanisms are difficult to detect phishing attempts as attackers are executing phishing in creative ways such as using homograph URLs or Browser in the Browser Attack (BiTB). Thus, phishing attempts must be mitigated before any data leakage, identity theft or financial losses occur.
Techniques
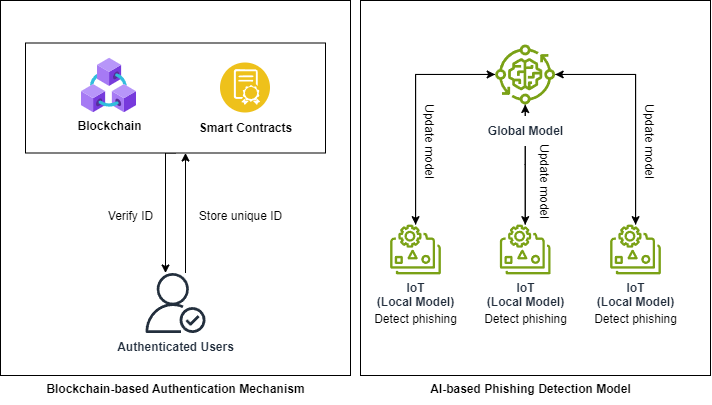
In this paper, a combination of AI-based phishing detection and blockchain-based authentication mechanism is proposed to enhance security of IoT-based systems. Federated learning, which is a type of ai is used to identify phishing content. It trains data on each IoT device locally, eliminating the need to transfer data over the network. Since there are various connected devices in IoT ecosystem, federated learning proves particularly suitable, and phishing can be detected at the entry point of IoT ecosystem. [2] This approach not only improves detection efficiency, but also reduces network bandwidth usage. Besides, blockchain acts as authentication mechanism in IoT-based systems due to its immutability, transparency and traceability. [3] All devices have own unique digital identity and all identities are stored in blockchain to prevent any malicious changes. Smart contract is programmed to automate the storing and verification processes of data on blockchain. It will compare the data on blockchain with device identity based on predefined rules in order to verify it. If matched successfully, the device is considered safe and can access the IoT resources, avoiding any unauthorized access. The security and reliability of system can be approved by using blockchain.
Conclusion
In conclusion, the integration of machine learning and blockchain in phishing detection mechanism provides a reliable solution to improve overall security of IoT-based systems. The use of federated learning allows IoT devices to identify phishing attempts locally, reducing the risks of phishing attacks at the entry points while protecting data privacy. In addition, blockchain-based authentication mechanism can protect IoT-based systems from unauthorized access, data leakage and identity theft, further strengthening the security of the systems.
Reference
- F. Mehdipour, “A Review of IoT Security Challenges and Solutions,” in 2020 8th International Japan-Africa Conference on Electronics, Communications, and Computations (JAC-ECC), Dec. 2020, pp. 1–6. doi: 10.1109/JAC-ECC51597.2020.9355854.
- I. Priyadarshini, “Anomaly Detection of IoT Cyberattacks in Smart Cities Using Federated Learning and Split Learning,” Big Data Cogn. Comput., vol. 8, no. 3, Art. no. 3, Feb. 2024, doi: 10.3390/bdcc8030021.
- M. S. Almadani, S. Alotaibi, H. Alsobhi, O. K. Hussain, and F. K. Hussain, “Blockchain-based multi-factor authentication: A systematic literature review,” Internet Things, vol. 23, p. 100844, Oct. 2023, doi: 10.1016/j.iot.2023.100844.
- Zhou, Z., Wang, M., Ni, Z., Xia, Z., & Gupta, B. B. (2021). Reliable and sustainable product evaluation management system based on blockchain. IEEE Transactions on engineering management.
- Chui, K. T., Gupta, B. B., Liu, J., Arya, V., Nedjah, N., Almomani, A., & Chaurasia, P. (2023). A survey of internet of things and cyber-physical systems: standards, algorithms, applications, security, challenges, and future directions. Information, 14(7), 388.
- Li, D., Lai, J., Wang, R., Li, X., Vijayakumar, P., Gupta, B. B., & Alhalabi, W. (2023). Ubiquitous intelligent federated learning privacy-preserving scheme under edge computing. Future Generation Computer Systems, 144, 205-218.
Cite As
KEE S.N. (2024) Phishing Threats in IoT-Based Systems: Detection and Mitigation Techniques, Insights2Techinfo, pp. 1