By : Achit Katiyar1,2
1South Asian University, New Delhi, India.
2International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan. Email: achitktr@gmail.com
Abstract
Biometric security solutions are growing popular due to their ability to deliver dependable and user-friendly authentication. However, typical biometric systems come across difficulties, such as high incorrect acceptance and rejection rates. Quantum-inspired evolutionary algorithm is a potential strategy for improving the accuracy and strength of biometric security systems. The methodology involving quantum computing and referred as QIEAs under the umbrella of Evolutionary Algorithm can enhance large number of biometric matching and feature extractions operations significantly. The present article aims at deliberating on the use of QIEA in biometric security systems, more so in benefit, challenge, and prospect.
Introduction
Biometric security systems use biometric attributes of a user, involving logical and or physical attributes such as fingerprints, face and voice. These solutions are more efficient, and convenient in comparison to the password’s security measures methodology [1]. However, it is important to notice that they cannot prevent from such problems as wrong acceptances and rejections of connections that threaten security and user experience [2]. The conventional security systems are most of the time inadequate in providing sufficient protection against the more sophisticated attacks; there is therefore need to enhance the current security systems [3]. Because of these obstacles, there emerges the need to have an effective approach called quantum-inspired evolutionary algorithms (QIEAs): a set of methods that integrates the quantum computing idea in the course of creating the evolutionary algorithms to support the functionality of the biometric systems.
Quantum-Inspired Evolutionary Optimization
Quantum-inspired evolutionary algorithms (QIEAs) make use of quantum computing notions such as superposition and entanglement in order to enhance the search and optimization functions of evolutionary algorithms [4]. These algorithms work with a quantum version of the Boolean bit referred to as the qubit; this enables them to explore many states of the solution space at a time [5].
- Quantum Genetic Algorithms (QGA):
Quantum Genetic Algorithms (QGAs) combine the concept of quantum computing with simple genetic algorithms thus providing the users with the ability of encompassing a more widened search for the most appropriate solutions [4]. QGAs can utilize quantum super-position to analyze simultaneously all the possible answers, which drastically improves the efficiency of search [4].
Application in Biometric Systems-
There may be several advantages of using QGAs with regard to enhancing diverse characteristics associated with biometric systems such as the feature extraction algorithms, decision-making points where the matching score thresholds are set, and mechanisms of updating biometric templates [5]. The dynamic optimization capability allows the biometric systems adapt to the evolution of the user situations and other parameters within the environment, thereby leading to high level of reliability and efficiency [4].
- Quantum Inspired Particle Swarm Optimization (QPSO):
Quantum-Inspired Particle Swarm Optimization (QPSO) combines the classical particle swarm optimization with the principles of quantum computing. This enables the particles to explore the solution space, resulting in faster convergence and better optimization performance [6].
Application in Biometric Systems-
Thus, the applicability of QPSO could be in the altering of some of the aspects of the biometric system this includes testing of the sensors, updating the templates and in the detection of anomalies. Therefore, by gradually adjusting these functions, QPSO increases the capacity of such a system for authenticating the users with higher security level
Robust Biometric Security Systems
Mainstream biometric security strategies and Reliable identity recognition are also not similar because while the former is flexible and maybe changed depending on the users, the environment in which they are used is flexible because the processes that goes through to identify the individual is also being adjusted [2]. This flexibility is critical for maintaining high security and reducing mistakes. Figure 1 shows Robust Biometric Security Systems.
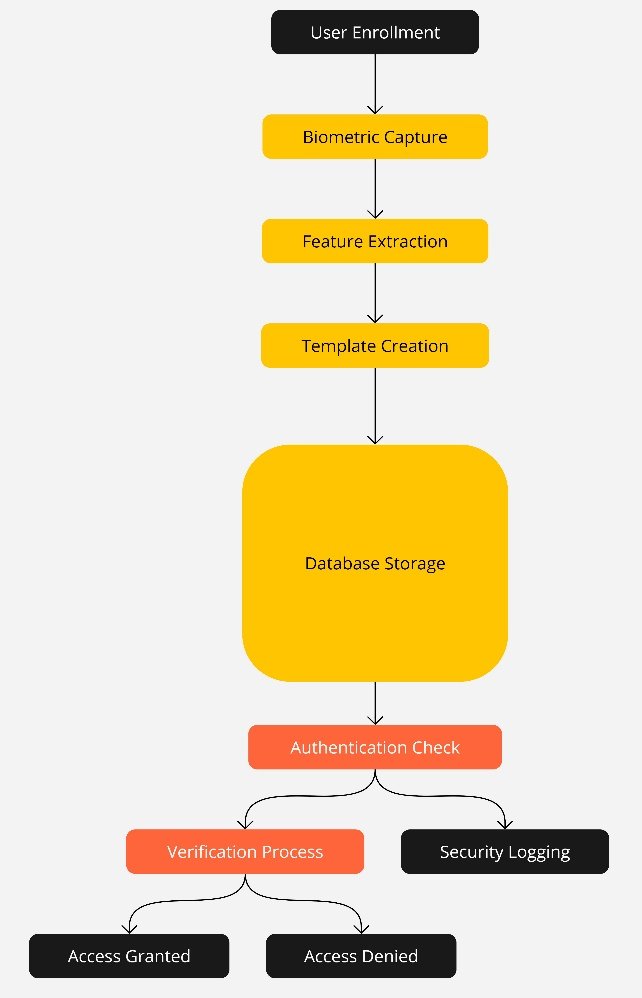
- Benefits of QIEO in Biometric Systems:
- Enhanced Adaptability:
QIEO improves biometric system’s accuracy and reliability by allowing them to adapt to changing user situations and surrounding elements [4].
- Improved Efficiency:
By utilizing quantum computing concepts, QIEO improves search and optimization operations while lowering computational overhead [5].
- Scalability:
QIEO may be used on large-scale biometric systems to provide scalable solutions to difficult security concerns [6].
Challenges in Implementing QIEO
- Computational Complexity:
QIEO, while efficient, can be computationally demanding due to the complexity of quantum processes [4]. Balancing computational costs with security advantages is a major difficulty in real-time biometric systems [5].
- Quantum-Specific Knowledge:
The strategies that are associated with the execution of QIEO require specific comprehension of the quantum computing and also the ideas of evolutionary algorithms. This can be a barrier for many organizations, a careful training and experience is required for the right implementation [6].
- Integration with Existing Systems:
Integrating QIEO into current biometric infrastructure can be difficult. Ensure compatibility and easy operation to maximize their benefits [1].
Emerging trends and future directions
- Hybrid Quantum–Classical Approaches:
Combining quantum-inspired algorithms with conventional approaches can improve their efficiency and help solve computing problems. Hybrid techniques use the qualities of both frameworks to deliver strong security solutions [6].
- Quantum Machine Learning:
Combining quantum-inspired evolutionary techniques with machine learning can enhance biometric feature extraction and matching capabilities [4]. Quantum machine learning models can outperform traditional methods for user identification and authentication [4].
- Quantum Resistant Cryptography:
Use of QIEO in the production of quantum resistance cryptographic algorithms improves the security of the whole biometric system. These algorithms can also afford significant defense against the quantum computing-based attacks and provide the biometric data precise and confidential [7], [8].
Case Studies & Practical Applications
- Case Study #1: Financial Sector:
In the given specifically financial sphere complex systems based on the result of the advanced work within the frames of QIEO have been searching to protect the cyber banking and other financial operations. QIEO’s dynamic optimization capabilities have considerably enhanced biometric system safety and user experience, minimizing the danger of unauthorized access and financial fraud [6].
- Case Study #2: Healthcare Industry:
In the healthcare business, sophisticated biometric systems based on QIEO have been used to protect sensitive patient data and enable secure access to medical records. Therefore, applying the adaptability aspects in QIEO has contributed to the improvement of security and reliability of the healthcare biometric system giving a better solution to the protection of clients’ information confidentiality and integrity [2].
Conclusion
The integration of ideas based on quantum mechanics in the development of the evolutionary optimization is one of the important steps in the development of the highly secure biometric systems. Such algorithms based on the principles of quantum computing offer better versatility, productivity, and responsiveness when it comes to security issues. The main drawbacks were observed in implementation issues; however, the advantages indicate that QIEO is a valuable technique for enhancing capabilities of biometric systems. It is anticipated that advances in future related research and development of the hybrid techniques and quantum machine learning should enhance their efficiency.
References
- U. Uludag, S. Pankanti, S. Prabhakar, and A. K. Jain, “Biometric cryptosystems: issues and challenges,” Proc. IEEE, vol. 92, no. 6, pp. 948–960, Jun. 2004, doi: 10.1109/JPROC.2004.827372.
- A. K. Jain, A. Ross, and S. Prabhakar, “An introduction to biometric recognition,” IEEE Trans. Circuits Syst. Video Technol., vol. 14, no. 1, pp. 4–20, Jan. 2004, doi: 10.1109/TCSVT.2003.818349.
- “An Enhanced Multi-Factor Authentication and Key Agreement Protocol in Industrial Internet of Things,” Insights2Techinfo. Accessed: Aug. 05, 2024. [Online]. Available: https://insights2techinfo.com/an-enhanced-multi-factor-authentication-and-key-agreement-protocol-in-industrial-internet-of-things/
- K.-H. Han and J.-H. Kim, “Quantum-inspired evolutionary algorithm for a class of combinatorial optimization,” IEEE Trans. Evol. Comput., vol. 6, no. 6, pp. 580–593, Dec. 2002, doi: 10.1109/TEVC.2002.804320.
- A. Narayanan and M. Moore, “Quantum-inspired genetic algorithms,” in Proceedings of IEEE International Conference on Evolutionary Computation, May 1996, pp. 61–66. doi: 10.1109/ICEC.1996.542334.
- J. Sun, B. Feng, and W. Xu, “Particle swarm optimization with particles having quantum behavior,” in Proceedings of the 2004 Congress on Evolutionary Computation (IEEE Cat. No.04TH8753), Jun. 2004, pp. 325-331 Vol.1. doi: 10.1109/CEC.2004.1330875.
- D. J. Bernstein and T. Lange, “Post-quantum cryptography,” Nature, vol. 549, no. 7671, pp. 188–194, Sep. 2017, doi: 10.1038/nature23461.
- A. M. Widodo et al., “Quantum-Resistant Cryptography,” in Innovations in Modern Cryptography, IGI Global, 2024, pp. 100–130. doi: 10.4018/979-8-3693-5330-1.ch005.
- Raj, B., Gupta, B. B., Yamaguchi, S., & Gill, S. S. (Eds.). (2023). AI for big data-based engineering applications from security perspectives. CRC Press.
- Gupta, G. P., Tripathi, R., Gupta, B. B., & Chui, K. T. (Eds.). (2023). Big data analytics in fog-enabled IoT networks: Towards a privacy and security perspective. CRC Press.
Cite As
Katiyar A. (2024) Quantum-Inspired Evolutionary Optimization for Biometric Security Systems, Insights2Techinfo, pp.1