By: Vanna karthik; Vel Tech University, Chennai, India
Abstract
Network infrastructure is seriously threatened by Distributed Denial of Service (DDoS) assaults, which overload targets with excessive data and prevent services from operating. This study offers a real time DDoS mitigation strategy that successfully detects and counters these attacks by utilizing FlowGuard and entropy analysis. While entropy analysis measures the randomness in traffic patterns which helps in differentiating between malicious and legitimate traffic, FlowGuard tracks network flows and detects irregularities. In order to create a strong defense mechanism and secure network service availability and stability in the event of DDoS attacks, our technique integrates these tools. The outcomes show how well this strategy works to reduce the impact of DDoS attacks in real time.
Introduction
The dependence on internet services has increased significantly in the digital era. DDoS assaults, which try to stop these services from being available, have grown more regular and effective. It is very challenging to put in place suitable security measures on IoT devices because of their limited storage and limited processing capacity[1]. Traditional defenses frequently don’t react fast enough to reduce the harm these attacks provide. Because of this, this paper examines the combination of flowguard, A network flow monitoring tool and entropy analysis to detect and mitigate DDoS attacks in real time.
Literature review
At present world DDoS attacks are rapidly evolving ,attackers are trying to bypass various traditional security measures. Current detection methods are focuses on static rule based and signature based detection, it provides imperfect against new and evolving DDoS attacks patterns. Most of the researches are suggested new deep learning or machine learning approaches to secure IoT devices[2].
A DDoS mitigation framework called FlowGuard works by keeping an eye on and evaluating network traffic patterns. FlowGuard focuses on flows, which are collections of packets between a source and a destination that share characteristics such as source IP, destination IP, source port, destination port, and protocol, in contrast to conventional packet-based inspection techniques. The scalable and effective identification of anomalous traffic patterns suggestive of DDoS attacks is made possible by this flow-based method.
FlowGuard offers a defensible approach to monitoring network traffic by analyzing flows rather than individual packets. FlowGuad contain two components they are flow filter and flow handler.in this flow filter work on the flow filtration of DDoS attacks. Like this flow handler is used to identification and classification of DDoS attacks by using machine learning models[1]. The machine learning models are Long Short-Term Memory(LSTM) and Convolution Neural Network (CNN). By this we can understand that flow-based analysis are used to identify and classify the anomaly DDoS attack patterns.
Measuring the unpredictability or randomness of data is known as entropy analysis. Entropy can be used to measure the distribution of packet properties like IP addresses, ports, or protocols in the context of network traffic. A high concentration of similar traffic, such as many packets from a single IP address, is indicated by low entropy and is frequently seen in DDoS assaults. A more random distribution is suggested by high entropy, which could happen during broad attacks or real traffic bursts. Entropy analysis provide a mathematical framework to measure the unpredictability in datasets. This can be used to identify unusual patterns in network traffic[3].
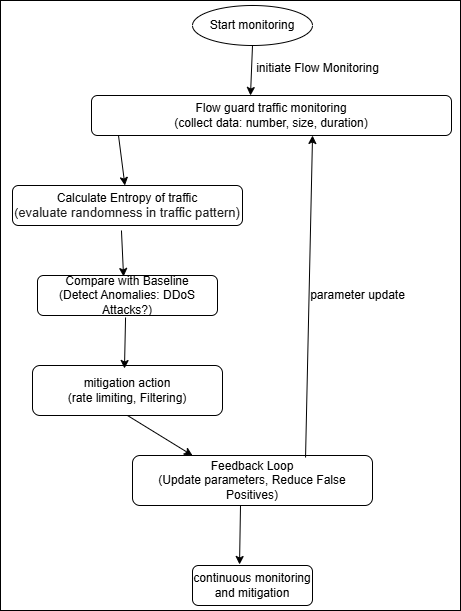
Explanation about the flow chart
Starting traffic monitoring with FlowGuard is the first step in the procedure. This initiates ongoing network traffic monitoring to gather crucial information for subsequent analysis. FlowGuard gathers information about network flows, including their quantity, size, and duration. Finding trends and irregularities in traffic patterns that can indicate a DDoS assault is made easier with the use of this data. The next step after gathering flow data is to determine the traffic’s entropy. The randomness or predictability of the distribution of traffic attributes, such as IP addresses or ports, is measured by entropy analysis. Possible DDoS assaults are indicated by notable departures from typical entropy values. The determined entropy is contrasted with a predetermined baseline, which is typical traffic patterns. This comparison helps with anomaly detection. A considerable deviation from the baseline in entropy indicates the presence of unusual traffic patterns, which could be the result of a DDoS attack. The system looks for entropy and traffic flow irregularities. The system advances to the following stage if an anomaly is found that might point to a DDoS attack. It keeps tracking traffic if no anomaly is found. FlowGuard initiates mitigation procedures in real time upon detection of a DDoS assault. To reduce the impact of the attack, these measures could involve rate limitations, removing questionable traffic, or blackholing traffic from particular sources. Following the implementation of mitigation measures, the system goes through a feedback loop in which it modifies its settings in response to the results. By lowering false positives and increasing the precision of subsequent detections, this ongoing feedback helps in refining the detection and mitigation procedure. And the last step continues the monitoring and mitigation.
Methodology
The suggested mitigation approach combines entropy analysis and FlowGuard into a real-time system. There are three stages to the methodology:
Utilizing FlowGuard for Traffic Monitoring: FlowGuard continuously tracks network flows, gathering information on their quantity, size, and time. It detects anomalous patterns or peaks that diverge from typical behavior.
Entropy Calculation: The entropy of incoming traffic is computed concurrently. A probable DDoS assault is indicated by a notable departure from the baseline entropy. While high entropy may indicate unpredictable, dispersed assault patterns, low entropy may indicate automated, repetitive attack activity.
Conclusion
The combination of entropy analysis and FlowGuard offers a complete real time DDoS mitigation solution. By utilizing the advantages of both statistical analysis and flow-based monitoring, this dual strategy outperforms conventional techniques in identifying and addressing DDoS attacks. By guaranteeing network service continuity even in the face of an assault, the suggested approach significantly enhances DDoS protection methods.
References
- Y. Jia, F. Zhong, A. Alrawais, B. Gong, and X. Cheng, “FlowGuard: An Intelligent Edge Defense Mechanism Against IoT DDoS Attacks,” IEEE Internet Things J., vol. 7, no. 10, pp. 9552–9562, Oct. 2020, doi: 10.1109/JIOT.2020.2993782.
- V. Mothukuri, P. Khare, R. M. Parizi, S. Pouriyeh, A. Dehghantanha, and G. Srivastava, “Federated-Learning-Based Anomaly Detection for IoT Security Attacks,” IEEE Internet Things J., vol. 9, no. 4, pp. 2545–2554, Feb. 2022, doi: 10.1109/JIOT.2021.3077803.
- N. Pandey and P. K. Mishra, “Conditional entropy-based hybrid DDoS detection model for IoT networks,” Comput. Secur., vol. 150, p. 104199, Mar. 2025, doi: 10.1016/j.cose.2024.104199.
- Liao, M., Tang, H., Li, X., Vijayakumar, P., Arya, V., & Gupta, B. B. (2024). A lightweight network for abdominal multi-organ segmentation based on multi-scale context fusion and dual self-attention. Information Fusion, 108, 102401.
- Gokasar, I., Pamucar, D., Deveci, M., Gupta, B. B., Martinez, L., & Castillo, O. (2023). Metaverse integration alternatives of connected autonomous vehicles with self-powered sensors using fuzzy decision making model. Information Sciences, 642, 119192.
- Zhang, S., Hu, B., Liang, W., Li, K. C., & Gupta, B. B. (2023). A caching-based dual k-anonymous location privacy-preserving scheme for edge computing. IEEE Internet of Things Journal, 10(11), 9768-9781.
- Shaik D.A. (2024) The Role of AI in Data Privacy and Protection, Insights2Techinfo, pp.1
Cite As
Karthik V. (2025) Real time DDoS Mitigation Using FlowGuard and Entropy Analysis, Insights2techinfo pp.1