By: Gonipalli Bharath Vel Tech University, Chennai, India International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, Gmail: gonipallibharath@gmail.com
Abstract:
Among all the threats facing IoT networks nowadays, DDoS attacks appear to be the most striking ones; therefore, the development of effective mechanisms of their detection is an urgent challenge. In the framework of the given review, two new approaches will be compared: the Conditional Entropy-Based Hybrid DDoS Detection Model and FlowGuard-an Intelligent Edge Defense Mechanism. Both performed very well to mitigate DDoS attacks, but the model based on conditional entropy significantly outperformed, since its nature of the framework was hybrid by incorporating both statistical and machine learning methods analytically. This article work deals with the detection performance, computing efficiency, & real-time applicability of both mechanisms.
Introduction:
Due to the rapid proliferation in IoT devices, currently, communication and automation have taken a shift in the following nature, It also extends the scope of DDoS attacks further in this growth and this can take advantages of computation capabilities of IoT devices while crippling the traditional systems used for detection. An increasing need in this area requires intelligent, adaptive, and high-accuracy models for detection. The paper threw light on two such state-of-the-art mechanisms and defined one most feasible in consideration to security in IoT networks.
Literature Review:
A lot of research is in progress for reducing the possibilities of DDoS threats. Early models, which were signature-based detection-based, were quite inefficient against the evolution of attack patterns. Conditional entropy-based approaches analyze network traffic for deviations in entropy and are really effective in picking out abnormal behavior. Edge-based defense mechanisms like FlowGuard integrate real-time traffic analysis with machine learning to facilitate immediate and localized responses. While both approaches are an advance over traditional methods, applicability to real situations and efficiency can only be determined by a comparative study[[1]].
Flow chart representation:
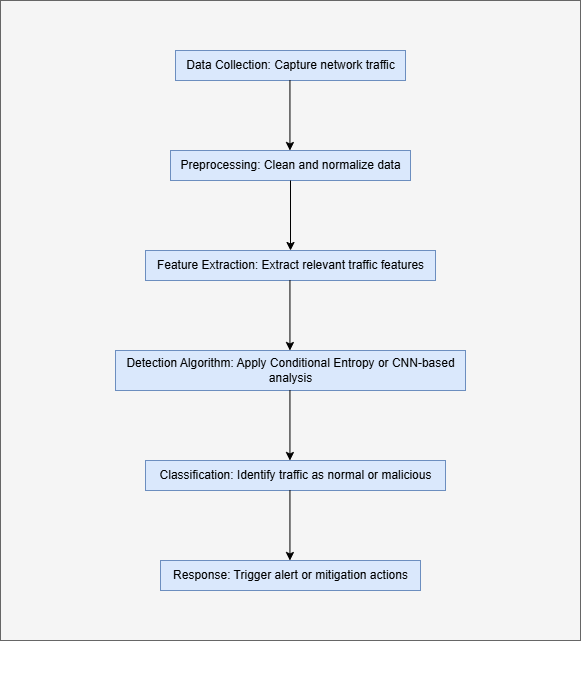
Methodology:
Conditional Entropy-Based Hybrid Model:
The hybrid mechanism is based on statistical entropy analysis in tandem with machine learning classifiers. The steps of the methodology followed can then be grouped into the following processes: DATA COLLECTION Network traffic data would be continuously acquired and stored by IoT devices and gateways, respectively. Including but not limited to packet headers, flow statistics, and timestamps[[2]].
Entropy Analysis:
Model compute conditional entropy for different traffic features such as source IPs, destination IPs, and packet sizes. Feature Conditional entropy in quantifying the randomness of data for identifying deviation in data flow as a probability for DDoS attacks[[3]]. Only the most relevant features enabling deviations from respective entropy distributions undergo further analysis using statistical techniques. This reduces computational resources in avoiding the redundancy of processing unnecessary data. The filtered features are used as input for the machine learning algorithms, which may be a random forest, SVM, or gradient boosting. These algorithms classify the traffic as normal or malicious based on their training and real-time analysis. A hybrid use of entropy metrics and machine learning enhances the detection precision.
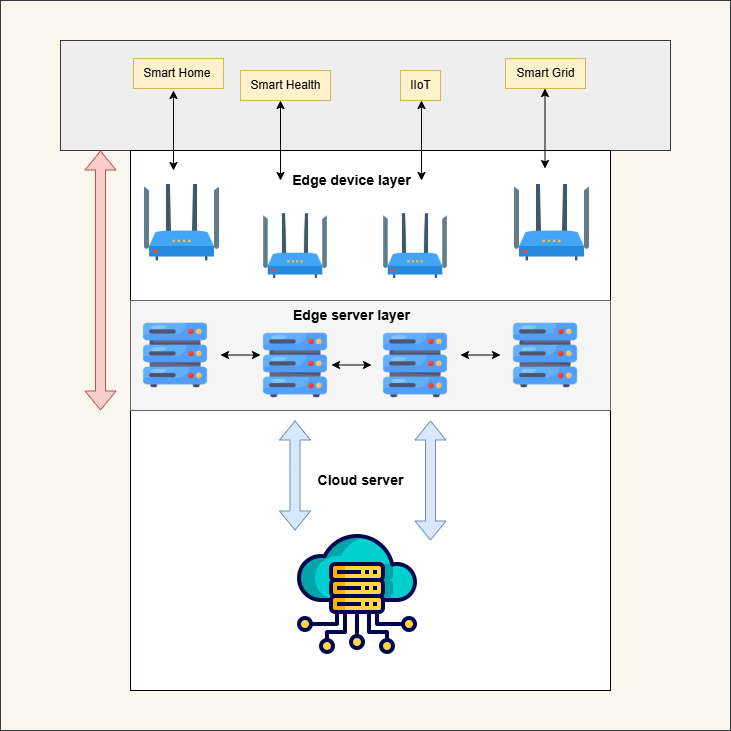
Fig[[4]]
FlowGuard:
It is an Edge IoT network-based detection that deploys deep learning for real-time DDoS detection. The methodology followed has been: Deploy at Edge Node: FlowGuard is deployed at the edge nodes, observing streams of incoming and outgoing traffic. Because it is decentralized, there will be low latency, hence faster detection.
Data Preprocessing:
Preprocessing of raw traffic data: It filters out the noise to present standardized inputs to the deep learning models, including packet size normalization, aligning the timestamps, and protocol tagging.
Deep Learning Analysis:
FlowGuard extracts high-dimensional features from the traffic data using CNN. The use of CNN is justified because it proves quite efficient in DDoS pattern identification due to hierarchical feature extraction. Dynamic Rule Updates:
FlowGuard dynamically updates the detection rules from the anomalies identified. In these ways, the system would remain effective-whether currently trending or otherwise evolutive vectors of an attack.
Mitigation Actions:
This would detect the attack, upon which FlowGuard will apply the preprogrammed mitigation measures, which include traffic rate limiting, IP blacklisting, and the redirection of suspect traffic for further security.
Conclusion:
The Conditional Entropy-Based Hybrid Model and FlowGuard are both powerful frameworks for the detection of DDoS attacks in IoT environments. However, the conditional entropy-based model outperforms FlowGuard in view of the fact that its detection accuracy ranges above 98% for different attack scenarios. Besides, this hybrid model had a good balance between computational efficiency and detection precision, hence better within IoT networks. The architecture of FlowGuard is edge-centric and thus remains very suitable for use cases requiring low latency and scalability. Probably, future work will be able to combine the best features of both mechanisms for an even stronger defense.
References:
- Jia, Yizhen, Fangtian Zhong, Arwa Alrawais, Bei Gong, and Xiuzhen Cheng. “FlowGuard: An Intelligent Edge Defense Mechanism Against IoT DDoS Attacks.” IEEE Internet of Things Journal 7, no. 10 (October 2020): 9552–62. https://doi.org/10.1109/JIOT.2020.2993782.
- Pandey, Nimisha, and Pramod Kumar Mishra. “Conditional Entropy-Based Hybrid DDoS Detection Model for IoT Networks.” Computers & Security 150 (March 1, 2025): 104199. https://doi.org/10.1016/j.cose.2024.104199.
- Tian, Qiwen, and Sumiko Miyata. “A DDoS Attack Detection Method Using Conditional Entropy Based on SDN Traffic.” IoT 4, no. 2 (June 2023): 95–111. https://doi.org/10.3390/iot4020006.
Yizhen Jia et al., “FlowGuard: An Intelligent Edge Defense Mechanism Against IoT DDoS Attacks,” IEEE Internet of Things Journal 7, no. 10 (October 2020): 9552–62, https://doi.org/10.1109/JIOT.2020.2993782. ↑
Nimisha Pandey and Pramod Kumar Mishra, “Conditional Entropy-Based Hybrid DDoS Detection Model for IoT Networks,” Computers & Security 150 (March 1, 2025): 104199, https://doi.org/10.1016/j.cose.2024.104199. ↑
Qiwen Tian and Sumiko Miyata, “A DDoS Attack Detection Method Using Conditional Entropy Based on SDN Traffic,” IoT 4, no. 2 (June 2023): 95–111, https://doi.org/10.3390/iot4020006. ↑
- Sedik, A., Hammad, M., Abd El-Samie, F. E., Gupta, B. B., & Abd El-Latif, A. A. (2022). Efficient deep learning approach for augmented detection of Coronavirus disease. Neural Computing and Applications, 1-18.
- Deveci, M., Pamucar, D., Gokasar, I., Köppen, M., & Gupta, B. B. (2022). Personal mobility in metaverse with autonomous vehicles using Q-rung orthopair fuzzy sets based OPA-RAFSI model. IEEE Transactions on Intelligent Transportation Systems, 24(12), 15642-15651.
- Katiyar A. (2024) Social Engineering Phishing Detection, Insights2Techinfo, pp.1
Cite As
Bharath G. (2025) Simplified DDoS Detection Models for IoT Networks: A Comparison of Conditional Entropy and FlowGuard, Insights2Techinfo, pp.1