By: Mosiur Rahaman, International Center for AI and Cyber Security Research and Innovation, Asia University, Taiwan
Abstract:
A rapidly expanding cyberthreat, smishing, also known as SMS phishing, uses text message to trick people into exposing confidential data. Considering how dependent people are on mobile devices, fraudsters use social engineering tactics to create attractive notifications that seem authentic. The article explores the steps of a smishing attack, including monitoring, implementation, and the technical and psychological methods deployed to manage targets. The unique methods used by intruders, including customization, taking advantage of recent developments are also covered. The study concludes by outlining solutions, such as technical security features, authentication procedures, and public awareness instruction highlighting the significance of a multifaceted strategy to prevent smishing risks.
Introduction:
Various interfaces are frequently used in smishing strategies, such as posing as a reliable organization and employing social engineering to deceive the target into divulging private information. Six smishing attacks are launched against only ten US and UK banks per second, stated Proofpoint [1]. A new phishing comes to light every week, a new company goes under, and another individual loses their life savings or modest fortune to sophisticated smishing [2].
Distributed denial of service (DDoS) attacks is intended to interfere with or prevent registered users from accessing a web server [3].Important IT systems including banks, credit card payment gateways, and even domain name servers are frequently the targets of these attacks. The goal of such attacks is to overload the server’s capacity such that authorized users can’t access it or it becomes unresponsive [4]. Attacks may also be defined as any illegal network penetration that leads to the unauthorized extraction of data; this is commonly known as an attack on security.
Anatomy of a Smishing Attack:
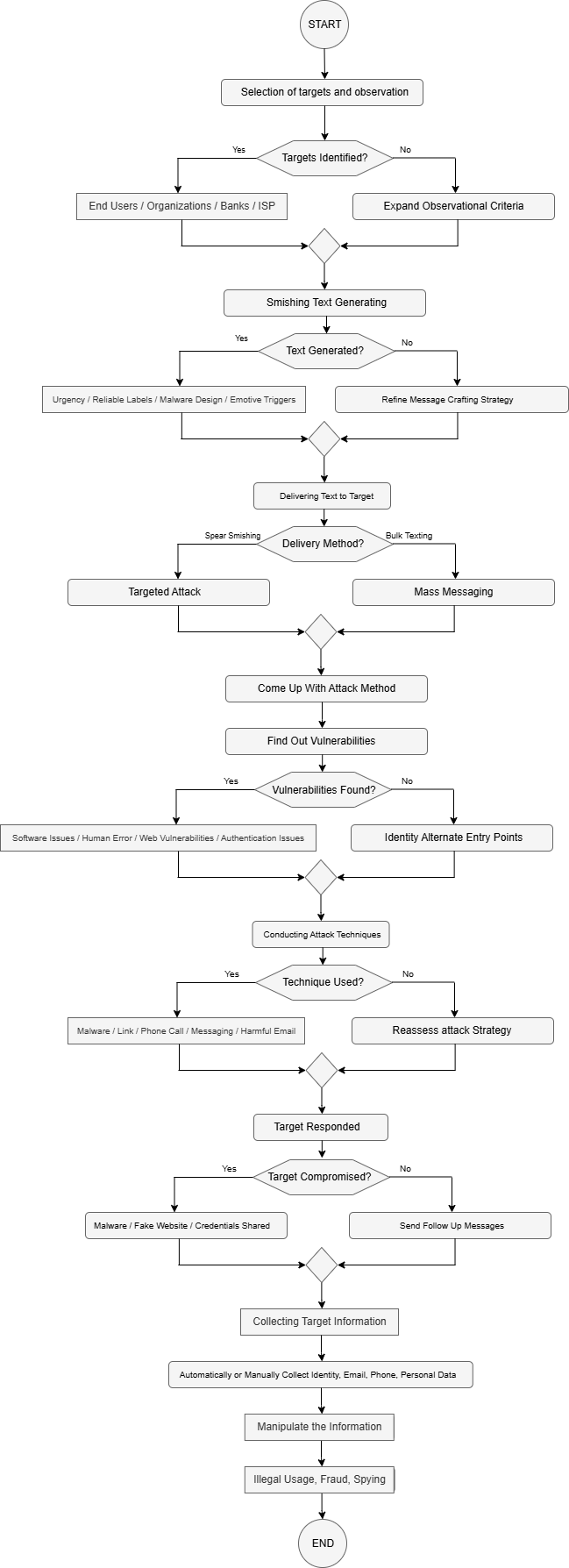
By showing the steps attackers use to carry out an effective attack, the flowchart illustrates the anatomy of a smishing threat. Attackers first choose targets and observe possible victims, such as end users, businesses, banks, or internet service providers. Next is Smishing Text Generating, which is the process of creating harmful messages that induce trust, urgency, or emotional emotions. Malware is frequently included in these messages [5]. Using strategies like mass texting and spear-smishing, the texts are disseminated via Sending Text to Target. Next, attackers create targeted techniques in Design an attack strategy and determine weaknesses, such as software defects, human mistake, online problems, or inadequate authentication [6]. By using strategies like distributing malware URLs, faked emails; or telemarketing calls, the Conducting Attack Technique is used to take advantage of these weaknesses. Attackers gather important details, such as identities, login passwords, or personal data, in the Collection of Target Information if the target responds. To complete the attack cycle, the method ends with Manipulate the Information, in which the stolen data is utilized for illicit purposes including fraud, eavesdropping, or unauthorized financial transactions. Anatomy of a Smishing attacks shown in Fig 1 and all the steps are mentioned below in Table 1,
Table 1: Smishing attacks Operations and Method
1 | Selection of Targets and Observation | End Users Organisation Bank/Financial Service ISP (Internet Service Providers) |
2 | Smishing Text Generating | •Urgency like Account deactivation •Offering as Reliable Labels •Malware Designing •Event triggers for Emotive feelings |
3 | Delivering Text to Target | •Spear-smishing •Bulk texting •Counterfeiting Method |
Come up with Attack Method | ||
5 | Find out Vulnerability | •Software Vulnerabilities •Human Error •Web Vulnerabilities •Inheritance System •Authentication and Endorsement issues |
6 | Conducting Attack Technique | •Malware Link •Calling via Phone •Messaging •Harmful email |
7 | Target Responded | •Effected by Malware link •Click on any link •Login in fake website •Sharing Login Credentials |
8 | Collection Target Information | •Automatically or manually collecting the information •Identity •Email Address/Phone details •Personal Data |
9 | Manipulate the Information | •Illegally use Personal Data •Purchasing •Perform Fraud •Spying |
Smishing Countermeasures:
- Awareness of Data Security:
By improving knowledge of both anti-smishing and smishing attack strategies, smishing crimes can be reduced.
- Scientific Procedure:
Many scholars have put out a few technological strategies to reduce smishing attacks.
- To identify smishing communications, Sonowal et al. suggested the “SmiDCA” machine learning model. A correlation methodology inside the model is used to extract the 39 most important components from messages from smishing.
- The model’s performance is evaluated using four machine learning classifiers.
Four classifiers were employed: Random Forest, Decision Tree, Support Vector Machine, and AdaBoost for recognizing smishing attempts.
- S-Detector consists of an SMS monitor, an SMS analyser, an SMS determinant, and a database. It checks the content and URL of the text message. In their approach, they utilized a Nave Bayesian Classifier to search for terms that were more commonly used in smishing messages to distinguish them from legitimate ones [7].
- Smishing detection in a mobile environment using a content-based method, where text messages are categorized according to their content and URL behaviour. To find out whether SMS messages include URLs, phone numbers, email addresses, and dangerous keywords, text pre-processing and analysis techniques are employed. Malicious keywords found in the communication are utilized to categorize it using a machine learning technique [8].
- Developed a mobile spam filtering application called “SMS Assassin,” which makes advantage of the sender’s being blacklisted protocol and Bayesian computing. The Bayesian classifier and Support Vector Machine are combined to get higher accuracy.
Conclusion:
Because of how much we rely on mobile interactions, smishing attacks pose a serious and dynamic cyberthreat. People and companies may create strong defences by comprehending the structure of these attacks, including the methods and strategies employed by fraudsters. To reduce the dangers of smishing and create a more secure online environment, comprehensive training, innovative technological protections, and strict legal frameworks are required.
Reference:
- A. Papathanasiou, G. Liontos, V. Liagkou, and E. Glavas, “Business Email Compromise (BEC) Attacks: Threats, Vulnerabilities and Countermeasures—A Perspective on the Greek Landscape,” Journal of Cybersecurity and Privacy, vol. 3, no. 3, Art. no. 3, Sep. 2023, doi: 10.3390/jcp3030029.
- B. B. Gupta, N. Arachchilage, and K. Psannis, “Defending against Phishing Attacks: Taxonomy of Methods, Current Issues and Future Directions,” Telecommunication Systems, vol. 67, Feb. 2018, doi: 10.1007/s11235-017-0334-z.
- A. Singh and B. B. Gupta, “Distributed Denial-of-Service (DDoS) Attacks and Defense Mechanisms in Various Web-Enabled Computing Platforms: Issues, Challenges, and Future Research Directions,” IJSWIS, vol. 18, no. 1, pp. 1–43, Jan. 2022, doi: 10.4018/IJSWIS.297143.
- D. Y. Perwej, S. Q. Abbas, J. P. Dixit, D. N. Akhtar, and A. K. Jaiswal, “A Systematic Literature Review on the Cyber Security,” International Journal of Scientific Research and Management (IJSRM), vol. 9, no. 12, Art. no. 12, Dec. 2021, doi: 10.18535/ijsrm/v9i12.ec04.
- M. Rahaman, V. Arya, S. M. Orozco, and P. Pappachan, “Secure Multi-Party Computation (SMPC) Protocols and Privacy,” in Innovations in Modern Cryptography, IGI Global, 2024, pp. 190–214. doi: 10.4018/979-8-3693-5330-1.ch008.
- Z. Alkhalil, C. Hewage, L. Nawaf, and I. Khan, “Phishing Attacks: A Recent Comprehensive Study and a New Anatomy,” Front. Comput. Sci., vol. 3, Mar. 2021, doi: 10.3389/fcomp.2021.563060.
- M. K. Mehmood, H. Arshad, M. Alawida, and A. Mehmood, “Enhancing Smishing Detection: A Deep Learning Approach for Improved Accuracy and Reduced False Positives,” IEEE Access, vol. 12, pp. 137176–137193, 2024, doi: 10.1109/ACCESS.2024.3463871.
- S. Mishra and D. Soni, “Smishing Detector: A security model to detect smishing through SMS content analysis and URL behavior analysis,” Future Generation Computer Systems, vol. 108, pp. 803–815, Jul. 2020, doi: 10.1016/j.future.2020.03.021.
- Bharath G. (2025) Detecting and Preventing Phishing Attacks in IoT Applications Through Threat Modeling, Insights2Techinfo, pp. 1
Cite As
Rahaman M. (2025) The Anatomy of a Smishing Attack: Common Techniques and Tactics Used by Cybercriminals, Insights2Techinfo, pp.1