By: Gonipalli Bharath Vel Tech University, Chennai, India International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, Gmail: gonipallibharath@gmail.com
Abstract:
Phishing has become a vastly different scam since its humble beginnings in deceitful emails, reaching its current heights with advanced deepfake scams. Cyberthieves leverage the rapid advancement of technology to amplify their fake activities, and this article follows the chronological history of how phishing evolved into its latest iteration. An extensive flowchart visually displays how the method transformed from traditional email phishing to artificial intelligence-created deepfake scams, as well as highlighting the immediate necessity for top-level security solutions.
Introduction:
Phishing attacks have undergone major transformations throughout several years by embracing both technological advancements and human predictabilities. exploiting human vulnerabilities. This short article examines the noticeable development of phishing attacks since their original email-based method during the 1990s, their early forms in emails to the sophisticated deepfake scams prevalent today.
Early Days: Email Phishing:
The main method of phishing during the late 1990s and early 2000s consisted of deceptive emails. Legitimate source platforms such as banks received their digital protection from malicious cybercriminals who developed fraudulent messages with misleading appearances, popular online services. When users received these emails, they found messages with vital information that directed them to dangerous links[1]. The content focuses on directing victims toward dangerous links or extracting sensitive details. Potential victims faced two basic approaches through which cybercriminals tried to manipulate them. Users fell victim through fake suspension warnings and unreasonably desirable offers that looked suspicious[2]. Early phishing tactics relied heavily, social engineering strategies took advantage of user trust combined with their lack of awareness. These attacks succeeded due to their basic design that tricked unsuspecting users without their knowledge of potential hazards. Various risks emerge from webpage clicks and user data submission activities[3]. As a result, early phishing campaigns brought notable accomplishments which forced numerous users and institutions to face major financial setbacks.
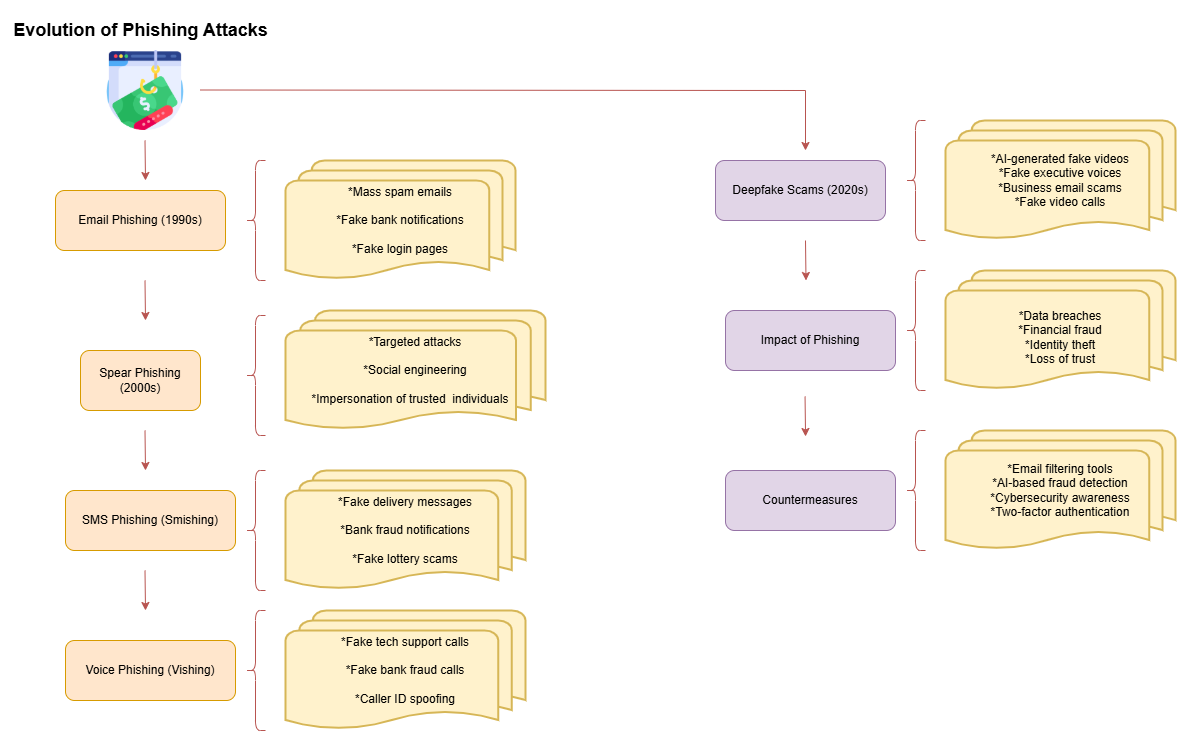
The Rise of Spear Phishing:
Security understanding regarding generic phishing emails pushed attackers to dedicate their efforts toward personalized attack methods known as spear phishing. Extensive research about victims allows cybercriminals to execute these attacks. Insider information allowed such attackers to compose personal messages which appeared authentic. Social media networks serve as well as publicly available information together allow attackers to execute their schemes effectively[4]. Cyber attackers leveraged available information to develop the dangerous spear phishing attacks which proved more successful and significant data breaches and financial losses. The attacks of spear phishing focus on individual organizations and specific people to generate plausible messages. A hacker would pretend to be the company CEO to send fraudulent messages appearing as if from the top executive toward an individual employee, requesting sensitive financial information. The attack goals of spear phishing exploitation focus specifically on individuals. The existing organizational trust and familiarity create a strong environment for this particularly evil form of attack[5].
Advent of SMS Phishing (Smishing):
Most people acquiring mobile devices caused phishing techniques to transform further. Cybercriminals adopted SMS messaging as their weapon to send deceptive messages which introduced the technique known as smishing. These messages often contained both harmful links which led users to dangerous websites along with phone number connections that routed victims to scammers. Mobile communication provided ease of use which made smishing attacks highly effective among phishers[6].
Method for phishing:
Thieves who do smishing attacks usually use breaking news events together with prominent service offerings as bait for potential victims. For instance, Attackers will dispatch a phony delivery-related text message that requests the recipient to access a given link. The victim needs to check their address by clicking on the link provided. The rapid growth of mobile communication and the immediacy of Smishing attacks became more effective through the increases in user text message. Users tend to answer quickly without performing proper evaluation of the provided content[7].
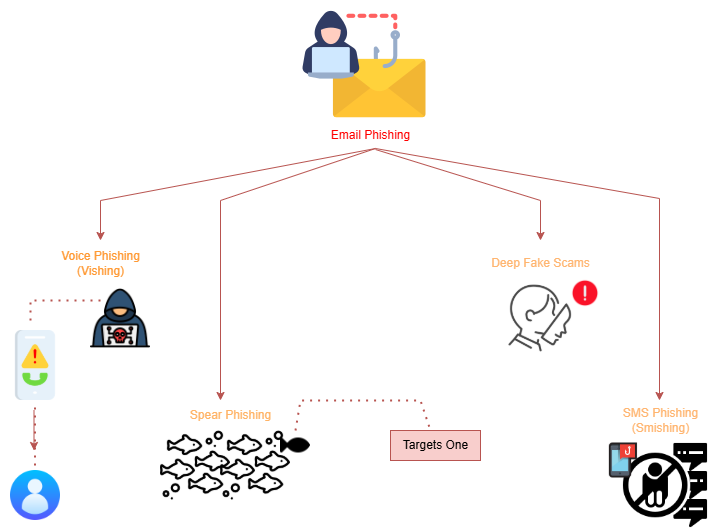
Voice Phishing (Vishing):
Voice phishing also known as vishing started appearing as a new technique which involved phone attacks. They make themselves impersonate legitimate organizations and callers impersonated bank agents along with representatives from service organizations so victims trusted their identities and may requesting personal information. An attacker will generate artificial pressure to foolishly prompt victims into action. Scammers use intimidation tactics against users to force them into taking prompt action before their accounts get suspended or to perform unspecified urgent actions. New caller ID spoofing technology enables vishing attacks to become more difficult to detect since scammers can display fake identification numbers. Cybercriminals succeed in disguising their genuine phone numbers through fake numbers which seem trustworthy. This may increase a victim’s trust in the call tends to increase due to this tactic which enhances their susceptibility to give sensitive information[8].
Era of Deepfake Scams:
Deepfake technology which emerged in recent years has created an innovative path in phishing attack developments of phishing attacks. Artificial intelligence in deepfakes generates authentic audio and video items which appear realistic to people and this technology permits scammers to duplicate voices which make their fraud attempts appear authentic. Forged video calling systems are used in these scam campaigns, Audio messages and seemingly genuine communication from trusted sources have increased the challenge for victims to verify authenticity. And victims are struggling to identify real information from fabricated information in such circumstances[9].
Example: An example of such an attack involves cyber attackers using deepfake technology to produce fraudulent audio-visual content where the company executive appears to order bank transfers to particular accounts. The employee must direct funds from the company account into a designated banking location. A high degree of authenticity distinguishes deepfake technologies in their creations. The emotional manipulation and quick response manipulation by attackers causes major financial damages to victims and data breaches. Deepfakes have established a new advanced level in deceptive technology. This deepfakes have emerged as an advanced form of phishing attacks which creates severe obstacles for cybersecurity operations.
Impact of Phishing Attacks:
Phishing attacks generate extensive damage that targets both personal citizens and corporate entities as well as national institutions security. Financial losses represent only part of successful phishing attacks because they can also cause victims to become victims of identity theft while simultaneously experiencing data breaches.
Data breaches together with customer trust loss and additional security-related consequences result from these incidents. The victim organizations that experience a successful attack face multiple- consequences like regulatory fines, legal repercussions, and reputational damage. Successful and continuous education programs become essential because phishing tactics continue to evolve awareness efforts. Organizations must provide cyber security training to their staff members alongside maintenance of current phishing threat knowledge. Organizations must focus on security measures development and trend analysis to adequately fight against these threats.
Conclusion:
The evolution of phishing scams from simple email scams to advanced deepfake scams demonstrates the adaptability of cybercrime attackers. The methods of the attackers improve with advancing technology. It is crucial that individuals and organizations are attentive and become aware of the new threats so that they would not be victims of phishing scams.
References:
- Z. Alkhalil, C. Hewage, L. Nawaf, and I. Khan, “Phishing Attacks: A Recent Comprehensive Study and a New Anatomy,” Front. Comput. Sci., vol. 3, Mar. 2021, doi: 10.3389/fcomp.2021.563060
- S. Rathore, P. K. Sharma, V. Loia, Y.-S. Jeong, and J. H. Park, “Social network security: Issues, challenges, threats, and solutions,” Inf. Sci., vol. 421, pp. 43–69, Dec. 2017, doi: 10.1016/j.ins.2017.08.063.
- Z. Wang, H. Zhu, and L. Sun, “Social Engineering in Cybersecurity: Effect Mechanisms, Human Vulnerabilities and Attack Methods,” IEEE Access, vol. 9, pp. 11895–11910, 2021, doi: 10.1109/ACCESS.2021.3051633.
- M. S. Baig, F. Ahmed, and A. M. Memon, “Spear-Phishing campaigns: Link Vulnerability leads to phishing attacks, Spear-Phishing electronic/UAV communication-scam targeted,” in 2021 4th International Conference on Computing & Information Sciences (ICCIS), Nov. 2021, pp. 1–6. doi: 10.1109/ICCIS54243.2021.9676394.
- A. Yasin, R. Fatima, Z. JiangBin, W. Afzal, and S. Raza, “Can serious gaming tactics bolster spear-phishing and phishing resilience? : Securing the human hacking in Information Security,” Inf. Softw. Technol., vol. 170, p. 107426, Jun. 2024, doi: 10.1016/j.infsof.2024.107426.
- S. Mishra and D. Soni, “DSmishSMS-A System to Detect Smishing SMS,” Neural Comput. Appl., vol. 35, no. 7, pp. 4975–4992, Mar. 2023, doi: 10.1007/s00521-021-06305-y.
- J. Lee, Y. Lee, D. Lee, H. Kwon, and D. Shin, “Classification of Attack Types and Analysis of Attack Methods for Profiling Phishing Mail Attack Groups,” IEEE Access, vol. 9, pp. 80866–80872, 2021, doi: 10.1109/ACCESS.2021.3084897.
- Z. H. Phang, W. M. Tan, J. S. Xiong Choo, Z. K. Ong, W. H. Isaac Tan, and H. Guo, “VishGuard: Defending Against Vishing,” in 2024 8th Cyber Security in Networking Conference (CSNet), Dec. 2024, pp. 108–115. doi: 10.1109/CSNet64211.2024.10851764.
- F.-A. Croitoru et al., “Deepfake Media Generation and Detection in the Generative AI Era: A Survey and Outlook,” Nov. 29, 2024, arXiv: arXiv:2411.19537. doi: 10.48550/arXiv.2411.19537.
- Lv, L., Wu, Z., Zhang, L., Gupta, B. B., & Tian, Z. (2022). An edge-AI based forecasting approach for improving smart microgrid efficiency. IEEE Transactions on Industrial Informatics, 18(11), 7946-7954.
- Mirsadeghi, F., Rafsanjani, M. K., & Gupta, B. B. (2021). A trust infrastructure based authentication method for clustered vehicular ad hoc networks. Peer-to-Peer Networking and Applications, 14, 2537-2553.
- Chokkappagari R. (2024) How AI Detects Phishing Scams, Insights2Techinfo, pp.1
Cite As
Bharath G. (2025) The Evolution of Phishing Attacks: From Emails to Deepfake Scams, Insights2Techinfo, pp.1