By: Soo Nee Kee1,2
1Universiti Malaya, Kuala Lumpur, Malaysia.
2International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan Email: nee.kee2001.nks@gmail.com
Abstract
In recent years, cloud has growth rapidly and transformed enormously, becoming a cornerstone of modern IT infrastructure. With the assistance of top cloud providers such as Amazon and Google, most of the corporates started adopting cloud services to streamline their operations enhance efficiency and reduce operational costs. The pay-as-you go payment method is attractive which can help reduce the waste of unnecessary costs and eliminate the need of building own IT infrastructure. Clients just have to purchase and use the IT resources once they have a well planning without worrying about the maintenance of those resources as cloud vendors are taking care of it, effectively saving costs and time. Firms can utilise time and cost to focus on their core business activities and innovation, as well as expand their business. It is undeniable cloud has brought a lot of benefits to us. Nonetheless, the security issues are still the main concerns of cloud-based systems, especially phishing attacks. This is because the traditional security measurements and encryption methods are not sufficient to fully protect cloud environment from increasingly sophisticated phishing attacks. Therefore, blockchain-based mitigation is proposed to detect and prevent this vulnerability.
Keywords: Phishing, Cloud-based system, Blockchain
Introduction
Phishing occurs when attackers trick users into revealing privacy information such as personal data and account number. Normally, attackers will send fake URLs, message or email that look similar with the legitimate one in order to persuade users to open it. Once users interact with the fake websites or messages, attackers can gain unauthorized access to users’ sensitive information. Phishing is one of the most common cybersecurity attacks occurs in cloud environment as most of the attackers uses social engineering techniques and deceptive email tactics to conduct phishing and systems are difficult to track phishing attacks. It can cause serious financial losses or privacy data leakage. For example, once attackers gain unauthorized access to sensitive data, they can exploit it for identity theft, unauthorized financial transactions or even sell those data to dark web. Besides, attackers can alter data or disrupt business operations of an organizations. [1]
Thus, organizations should enhance their security measures, including advanced phishing detection tools and employee awareness programs. Blockchain is implemented and integrated with cloud environment to reinforce cloud-based systems and reduce the chances of falling victims to phishing attacks. Blockchain is a decentralized ledger that stores transactions in a distributed manner, eliminating the need of centralized server and prevent single point failure. It widely used in many areas like supply chain management, healthcare, agriculture and finance sectors. Every transaction will be stored in blocks and each block connected via cryptographic chain, making it immutable and ensuring all data remains secure without unauthorized access. In addition, blockchain allows organizations to monitor the tractions in real-time, making it easier to track any anomalies and suspicious activities. The transparency of blockchain technology allows all cloud users to view and manage the entire view of the system and prevent unauthorized access and malicious changes, effectively mitigating phishing attacks. [2]
Framework
The proposed framework addresses the impact of phishing on cloud-based system by integrating blockchain with cloud environments. The inadequate detection mechanism of existing cloud-based systems, making them prone to phishing. By utilising blockchain technology, systems can enhance security and accountability, as the stored data cannot be tempered or modify by attackers once it is added on the blockchain. Cloud users also can monitor transactions continuously in real-time. In addition, smart contract is implemented to enforce security protocols by blocking suspicious URLs and verifying legitimate transactions automatically. A URL scanning mechanism using deep learning that cooperate with smart contracts to differentiate between the phishing and legitimate URLs, provides a seamless operation to detect and prevent phishing attacks.
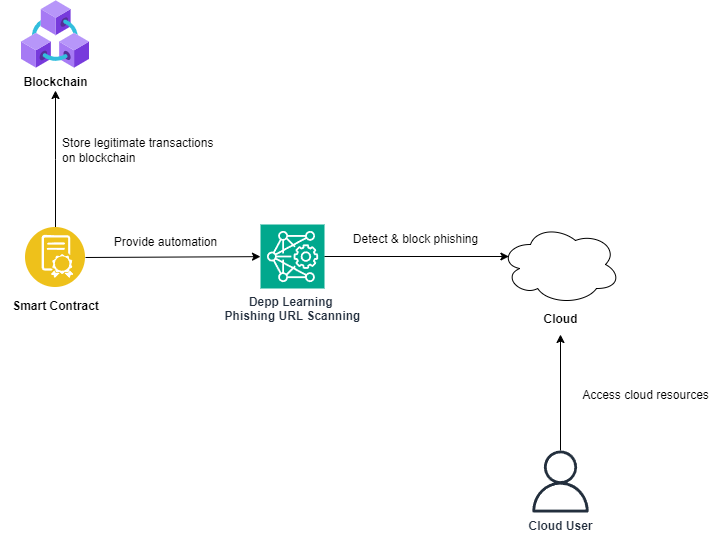
Conclusion
In conclusion, this paper proposes a robust framework to address phishing vulnerabilities. The use of blockchain enhances the overall security of cloud-based system through its decentralized nature and ensures data immutability and system transparency. Smart contracts provides automated phishing detection mechanism, blocking phishing URLs in real-time effectively. The leverage of deep learning further strengthens the phishing detection, allowing seamless identification of phishing while minimizing false positive. It enables organizations to store and protect sensitive data from any phishing attacks.
Reference
- “PhishingRTDS: A real-time detection system for phishing attacks using a Deep Learning model – ScienceDirect.” Accessed: Oct. 05, 2024. [Online]. Available: https://www.sciencedirect.com/science/article/pii/S0167404824001445
- “Exploring the integration of edge computing and blockchain IoT: Principles, architectures, security, and applications – ScienceDirect.” Accessed: Oct. 04, 2024. [Online]. Available: https://www.sciencedirect.com/science/article/pii/S1084804524000614
- Aldweesh, A., Alauthman, M., Al Khaldy, M., Ishtaiwi, A., Al-Qerem, A., Almoman, A., & Gupta, B. B. (2023). The meta-fusion: A cloud-integrated study on blockchain technology enabling secure and efficient virtual worlds. International Journal of Cloud Applications and Computing (IJCAC), 13(1), 1-24.
- M. Casillo, F. Colace, B. B. Gupta, A. Lorusso, F. Marongiu and D. Santaniello, “Blockchain and NFT: a novel approach to support BIM and Architectural Design,” 2022 International Conference on Innovation and Intelligence for Informatics, Computing, and Technologies (3ICT), Sakheer, Bahrain, 2022, pp. 616-620, doi: 10.1109/3ICT56508.2022.9990815.
Cite As
Kee S.N. (2024) The Impact of Phishing on Cloud-Based Systems and Blockchain-Based Mitigations, Insights2Techinfo, pp.1