By: Syed Raiyan Ali – syedraiyanali@gmail.com, Department of computer science and Engineering( Data Science ), Student of computer science and Engineering( Data Science ), Madanapalle Institute Of Technology and Science, 517325, Angallu , Andhra Pradesh.
ABSTRACT
IT especially in the current society has become a thorny issue with the kind and rates of cyber attack that are current and these have an impact on organizations and individuals. Traditional security strategies are still relevant but insufficient to address contemporary dangers; woman in her context is insecure. One of the greatest approaches is Artificial Intelligence (AI), that can enforce exact defense measures prior to cyber attacks. This paper seeks at explaining how artificial intelligence is used in the field of cybersecurity and some of the features it holds are; threat intelligence, anomaly detection, and automation. It also talk about limitation and advancement of using AI in the futures of cybersecurity.
Keywords: Artificial Intelligence, Cyber Security, Threat Detection, Anomaly Detection, Machine learning, Predictive Analytics, Cyber Attacks
INTRODUCTION
Today cybersecurity is identified as a main issue that organizations face around the world. The hackers, cybercriminals are getting smarter and hence, using mere firewall and antivirus are not enough like before. The application of AI in the cybersecurity environment has become one of the effective methods to improve the efforts for threat identification, the ability to forecast the attacks, and the use of AI to control the actions taken to minimize threats[1].
THE ROLE OF AI IN CYBERSECURITY
Al is quite useful in cyber security to its capability in processing large volumes of information and identifying tendency[2]. They therefore differ from traditional system that depend on mathematical or logical set algorithms that are followed in arriving at the final output; they can be trained and therefore have the capability to identify new risks that are not known to the system. The below figure explains the AI driven Cybersecurity Framework.
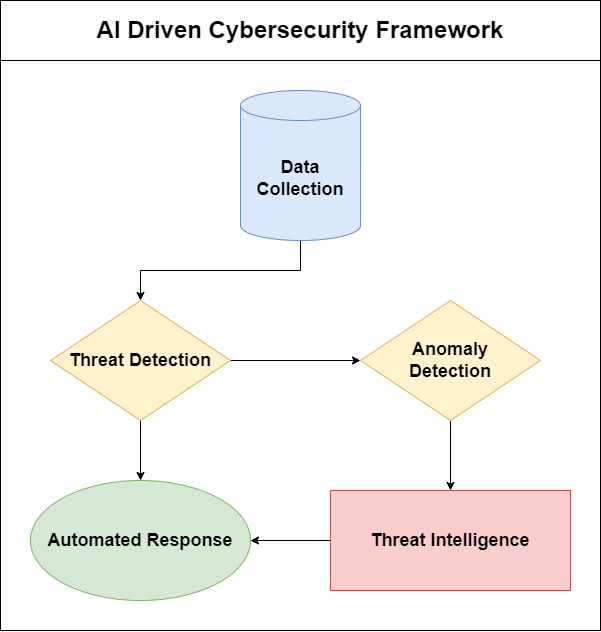
- Threat Detection
The employment of artificial intelligence assists the systems to monitor the traffic in the network real-time therefore wrong doings can be prevented. Neural networks as well as decision trees are used as a basis for pattern recognition that is relevant to known threats, as well as definition of new threats[3].
Example: Intrusion Detection Systems (IDS): IDS based on AI can identify the traffic anomalies because of its capability to compare the traffic patterns with the one credited to an assailant.
- Anomaly Detection
Information leakage is defined by the sometimes subtle identification of that portion of a system or process that is not consistent with the existing culture. Activities such as intrusion attempts or accumulation of data by a third party can be also learned by AI algorithms for a quick response.
Example: User Behavior Analytics (UBA): Insights: UBA is an AI-assisted tool that records user behavior in search of such things as potentially malicious accounts, or insider threats.
- Automated Response
Since AI is capable of automatically reacting to the threats that the system has identified, it means that lesser time would have been taken by the AI to counter those threats. Dynamic analysis also has the ability to resize infected routes, block pc attacks, and in some cases it also has the ability to counterattack the attacks[4].
Example: Security Orchestration, Automation, and Response (SOAR): SOAR turn to the use of artificial intelligence to coordinate the responses to various tools in the threat detection and mitigation process making the process of incident management more efficient.
Table 1: Comparison of Traditional vs AI driven Cybersecurity Systems
Feature | Traditional Systems | AI-Driven Systems |
Threat Detection | Rule-based | Data-driven, Predictive |
Response Time | Manual, Delayed | Automated, Real-time |
Adaptability | Limited to known threats | Learns and adapts to new threats |
Cost of Implementation | Lower | Higher, due to AI complexity |
Scalability | Limited | Highly scalable |
CHALLENGES IN AI DRIVEN CYBERSECURITY
here are important advantages of Artificial Intelligence, but its implementation in Cybersecurity has risks as well:
Data Privacy and Security
In order to use AI for Cybersecurity, we must have large volumes of data, leading to concerns about privacy and data security. It is essential that AI systems do not unintentionally reveal confidential information.
Adversarial Attacks
Cyber criminals can abuse AI systems by giving them harmful data so as to change their results. One of the foremost challenges is creating strong AI models that will withstand such an assault even with changing circumstances[5].
Complexity and Cost
Adoption of AI-powered cybersecurity solutions can be complicated and expensive. Organizations must employ qualified personnel, establish infrastructure, and regularly update their models if they want to provide adequate protection against cyber threats.
FUTURE TRENDS IN AI CYBERSECURITY
The evolution of artificial intelligence within the field of information security is certainly encouraging, with anticipated improvements in some cornerstones:
Quantum Computing with Artificial Intelligence
Linking artificial intelligence with quantum computing may totally transform how we guard our personal data through extremely fast processing power needed when it comes about finding hacks or encryption[6].
Behavioral Biometric Systems
Biometric systems based on user’s mobile phone actions will make access controls much more secure via computer-based analysis for behaviors like velocity of writing or navigation mode that are somehow unusual.
AI Cooperation Platforms
There are other possibilities such as AI integration platforms which various models help each other as against diverse institutional settings so that they can create a common protection bureau against universal internet challenges.
CONCLUSION
Cybersecurity can be revolutionized by artificial intelligence; it is capable of anticipating and averting cyber assaults prior to their occurrence. There are still challenges to face like making certain of maintaining data privacy and protecting oneself from enemy attacks but it cannot be denied that AI plays a crucial role in making security better. With time, AI will become more important in protecting electronic spaces because of the constant rise in digital crimes.
This essay focuses on how much AI will impact on Cyber Security encouraging various companies worldwide to take heed and invest in AI powered solutions which could help them remain ahead in their continuous fight against threats posed by hackers.
REFERENCES
- K. Meduri, H. Gonaygunta, and G. Nadella, “Evaluating the Effectiveness of AI-Driven Frameworks in Predicting and Preventing Cyber Attacks,” Int. J. Res. Publ. Rev., vol. 5, pp. 6591–6595, Mar. 2024, doi: 10.55248/gengpi.5.0324.0875.
- A. Anandita Iyer and K. S. Umadevi, “Role of AI and Its Impact on the Development of Cyber Security Applications,” in Artificial Intelligence and Cyber Security in Industry 4.0, V. Sarveshwaran, J. I.-Z. Chen, and D. Pelusi, Eds., Singapore: Springer Nature, 2023, pp. 23–46. doi: 10.1007/978-981-99-2115-7_2.
- J. Li, “Cyber security meets artificial intelligence: a survey,” Front. Inf. Technol. Electron. Eng., vol. 19, no. 12, pp. 1462–1474, Dec. 2018, doi: 10.1631/FITEE.1800573.
- M. M. Nair, A. Deshmukh, and A. K. Tyagi, “Artificial Intelligence for Cyber Security,” in Automated Secure Computing for Next-Generation Systems, John Wiley & Sons, Ltd, 2024, pp. 83–114. doi: 10.1002/9781394213948.ch5.
- Rahaman M (2024)” Foundations of Phishing Detection Using Deep Learning: A Review of Current Techniques, Insights2Techinfo [Online]. Available: https://insights2techinfo.com/foundations-of-phishing-detection-using-deep-learning-a-review-of-current-techniques/
- M. Rahaman, C.-Y. Lin, and M. Moslehpour, “SAPD: Secure Authentication Protocol Development for Smart Healthcare Management Using IoT,” in 2023 IEEE 12th Global Conference on Consumer Electronics (GCCE), Oct. 2023, pp. 1014–1018. doi: 10.1109/GCCE59613.2023.10315475.
- P. Chaudhary, B. B. Gupta, K. T. Chui and S. Yamaguchi, “Shielding Smart Home IoT Devices against Adverse Effects of XSS using AI model,” 2021 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 2021, pp. 1-5, doi: 10.1109/ICCE50685.2021.9427591.
- Li, K. C., Gupta, B. B., & Agrawal, D. P. (Eds.). (2020). Recent advances in security, privacy, and trust for internet of things (IoT) and cyber-physical systems (CPS).
- Chaudhary, P., Gupta, B. B., Choi, C., & Chui, K. T. (2020). Xsspro: Xss attack detection proxy to defend social networking platforms. In Computational Data and Social Networks: 9th International Conference, CSoNet 2020, Dallas, TX, USA, December 11–13, 2020, Proceedings 9 (pp. 411-422). Springer International Publishing.
Cite As
Ali S.R. (2024) USING AI TO PREDICT AND PREVENT CYBER ATTACKS, Insights2Techinfo, pp.1