By: Rishitha Chokkappagari, Department of Computer Science &Engineering, student of Computer Science & Engineering, Madanapalle Institute of Technology & Science, Angallu (517325), Andhra Pradesh. chokkappagaririshitha@gmail.com
Abstract
End to End Encryption is a line of communication or connection where the message and the information conveyed in between two or more departments is secured. In E2EE, the data will be encrypted at the sender’s side and decryption is only probable at the receiver end leaving the middlemen with no access to content that is being shared. Here, the keys are appointed by the users, and they are specific to the both the sender and the receiver of the message or the data to be protected. Since EE2 aids in reducing risks of interception, leakage and spying in secure messaging applications, monetary transactions and any form of information exchange, it is very important. The increase in end-to-end encryption assists in boosting the assurance of the users, and accreditation to the protection laws of the data making end-to-end encryption an essential factor in the protection of messages in cases of improved link connectivity.
Keywords: security, server, client, protection, end-to-end encryption
Introduction
Because almost all the businesses operate on an international market, it is very crucial to ensure privacy and security of such information as communicated using electronic means. Thus, end-to-end encryption (E2EE) appears necessary in the given context as it transforms into an adequate tool in protecting the data from unauthorized users. E2EE means that data originating from a particular sender is encrypted, and this encryption remains till the data reaches the intended recipient. This makes it possible to keep intermediaries ranging from the Internet service providers, hackers or even the actual communication service providers from having access to the content of the massages. E2EE is not limited to apps involved in messaging only but is now being implemented in calls, business communications and even financial transactions. It is an assured way of data protection since cryptographic procedures used to protect E2EE data are secure enough to protect users’ sensitive information especially in the current time when several countries are implementing data protection laws. First, this introduction will briefly explain what exactly end-to-end encryption is, how applying it works, and that it is such a vital method in the contemporary world.
- How End-to End Encryption works
Specifically, confidentiality of information is one of the biggest issues personally as well as in organizations at the present time. This means that as the threats in the virtual area fail or increase or the nature of the threats change then so do the ways of protection of the information. End to end encryption (E2EE) is one of the most efficient and used solutions in mobile communication. This article dwells on what E2EE means, how it works to safeguard information, the key concepts of E2EE, and why it remains crucial today[1].
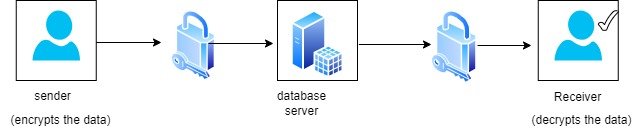
Understanding End-to-End Encryption
End to end encryption is a system of security that provides architectonics in which all the data that is passed in between two affined parties is to be secure from data intruders. While other paradigms of encryption involve the capability of data being encrypted and decrypted at several places right from the point where it still resides with the sender to the point where it is received by the recipient, E2EE assures that data is encrypted on the sender’s device and can only be decrypted the recipient’s device. This implies that if hackers gain access to the data being transmitted, they will not be able to understand it.

The process of end-to-end encryption involves several key steps:
- Key Generation: Two parties begin a conversation, in which each of them independently creates two keys, the public one and the private one. The public key is transmitted to the other person, whereas the private key is kept a secret.
- Data Encryption: Encrypted data is first encrypted with the recipient’s public key before sending data. This makes it possible for only the recipient to be able to read the data since he/she has the corresponding private key.
- Data Transmission: The encrypted data is over the network. In case the information trafficked is intercepted through the internet, it is safe since only the recipient has the decryption key.
- Data Decryption: Once the data has been encrypted, it is then sent to the end-user who then uses his/her secret key to decrypt the data and gain access to the information.
- Benefits of End-to-End Encryption
End-to-end encryption offers several key benefits that make it a preferred choice for securing digital communications. End-to-end encryption has multiple advantages which make it the most suitable means of protecting the commutations as listed below:
- Data Confidentiality: E2EE makes it a requirement that even the person in the middle like Internet service provider and big communication platforms cannot have any look at the data.
- Data Integrity: Regarding the safeguarding of the content of the exchanged messages, E2EE is beneficial since it reduces the probability of changing the messages.
- Enhanced Privacy: E2EE minimizes end users from traffic interception from other parties and service providers and, therefore, increases users’ privacy.
- Compliance with Regulations: Some of the most popular data protection legislation such as the general data protection regulation do insist on the use of good encryption algorithms for data protection. These regulations assist organizations and E2EE backs them[2].
- Applications of End-to-End Encryption
End-to-end encryption is widely used across various applications and industries. We have to improve the understanding of non-sectors[3]. End-to-end encryption has become quite popular and is used in different applications in day-to-day life and almost all industrial sectors.
- Messaging Apps: Celebrities and politicians often use WhatsApp, Signal, and Telegram to encrypt their messages and conversations from user to user to remain confidential.
- Email Services: From the list of mail services some can today incorporate the technology to ensure that the content of the emails is protected from the third parties[4].
- Financial Transactions: In online banking and systems of payment E2EE is used to protect the particulars of the finance and fight against fraudulence.
- Healthcare: In the healthcare, by definition, E2EE is used in the protection of the patients’ information within their communication and documents[5].
Conclusion
End to end encryption is among the most effective solutions in the sphere of data protection and is scarcely susceptible to attacks in the field of communication. Feasibility of illegitimate data interception is well dealt by E2EE due to data encryption ranging from the sender’s device up to the intended recipient. This very strong security technique involves keys that are created and maintained purposely on the two communicating devices and that after the service providers of the message, intruders or any other individuals violating the message they have no means of deciphering the contents of the message. Concerning E2EE, relevance is not only to personal privacy but also to the protection of business information, completion of business processes, and the message content confidentiality. This is especially the case as digitization of interactions is on the rise hence the need to have the use of E2EE in ensuring protection from modern day threats and fulfilling the stringent obligations in the present world.
Hence, the end-to-end encryption not only enhances the aspects of safety and privacy of the electronic communication but is also beneficial to the creation of confident environment in the digital platform. So E2EE minimizes the exposure of data to unauthorized persons as one is comfortable to transact or converse knowing that their information cannot be accessed by a third party. Toward the progression of technologic in the future, on E2EE’s shall remain one of the fundamental foundations to assist in protecting the world of cyberspace.
References
- M. Nabeel, “The Many Faces of End-to-End Encryption and Their Security Analysis,” in 2017 IEEE International Conference on Edge Computing (EDGE), Jun. 2017, pp. 252–259. doi: 10.1109/IEEE.EDGE.2017.47.
- P. Pappachan, Sreerakuvandana, and M. Rahaman, “Conceptualising the Role of Intellectual Property and Ethical Behaviour in Artificial Intelligence,” in Handbook of Research on AI and ML for Intelligent Machines and Systems, IGI Global, 2024, pp. 1–26. doi: 10.4018/978-1-6684-9999-3.ch001.
- W. Bai, M. Pearson, P. G. Kelley, and M. L. Mazurek, “Improving Non-Experts’ Understanding of End-to-End Encryption: An Exploratory Study,” in 2020 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Sep. 2020, pp. 210–219. doi: 10.1109/EuroSPW51379.2020.00036.
- M. Rahaman, B. Chappu, N. Anwar, and P. K. Hadi, “Analysis of Attacks on Private Cloud Computing Services that Implicate Denial of Services (DoS),” vol. 4, 2022.
- Rahaman M (2024) Foundations of Phishing Detection Using Deep Learning: A Review of Current Techniques Available: https://insights2techinfo.com/foundations-of-phishing-detection-using-deep-learning-a-review-of-current-techniques/
- Gupta, B. B., Gaurav, A., Arya, V., Alhalabi, W., Alsalman, D., & Vijayakumar, P. (2024). Enhancing user prompt confidentiality in Large Language Models through advanced differential encryption. Computers and Electrical Engineering, 116, 109215.
- Raj, B., Gupta, B. B., Yamaguchi, S., & Gill, S. S. (Eds.). (2023). AI for big data-based engineering applications from security perspectives. CRC Press.
- Gupta, G. P., Tripathi, R., Gupta, B. B., & Chui, K. T. (Eds.). (2023). Big data analytics in fog-enabled IoT networks: Towards a privacy and security perspective. CRC Press.
Cite As
Chokkappagari R. (2024) How End-to-End Encryption protects data, Insights2Techinfo, pp.1