By: Saksham Arora, CSE Department, Chandigarh College of Engineering and Technology, Chandigarh, India
Abstract: This article delves into the significance of WebSockets in forging vibrant and prompt web applications. It expounds upon the essential principles, strategies for implementation, and thoughtful factors to consider when enabling bidirectional communication between client and server. Moreover, it delves into the seamless integration of WebSockets with other cutting-edge technologies, showcases vital security measures, and offers practical wisdom for crafting real-time applications. By exploring case studies and examples, developers are presented with a succinct handbook on leveraging WebSockets to enhance user engagement and contentment within dynamic web development frameworks.
Keywords: WebSockets, Real-Time Communication, High Performance Computing.
1. Introduction
The rapid progressive developments of technology and the progressively complicated needs from users have inherited developers in searching for solutions beyond static web pages. This has led to a high trend of using web applications that are more responsive in real time as users now want much captivating and dynamic interactions. As mobile devices become widely available, high-speed Internet becomes widespread availability and powerful web browsers get introduced in the market there is a rising demand for innovative web applications that are not only quick in sharing information but also provide an interactive encounter. Today, users expect seamless navigation and live updates as well as the level of engagement expected from native applications. This change has prompted developers to find cutting-edge technologies that can eliminate gaps between the request – response model and immediacy of real time communication.
Given these facts, WebSockets have become a core technology that assists in fulfilling the rapidly evolving demands of modern users. This revolutionary departure from the established request response architecture allows developers to design applications able to provide real-time updates for users, thus enabling a more immersive and engaging user experience.
2. WebSockets: Underlying Principles
2.1 Bidirectional Communication:
WebSockets bring about a fundamental shift in the way client/server communication works. They completely transform the traditional model by introducing two-way communication capabilities [1]-[3]. This newfound interoperability enables real-time exchange of data and is particularly well-suited for applications that demand instant updates, like messaging platforms, collaborative tools, and online gaming environments. Once you grasp the essence of two-way communication [4], you gain the ability to employ WebSockets in order to fashion web applications that are both lively and adaptable. These remarkable tools offer a continuous and mutually interactive avenue for communication, enabling the seamless exchange of data in real-time between Internet of Things devices and servers[5]-[7].
2.2 WebSocket Handshake Process:
The WebSocket protocol employs a distinctive process of introduction to create a link between a user and a server. This initial exchange encompasses an HTTP request and response, where the user conveys its desire to enhance the connection to a WebSocket link. Following successful confirmation and validation by the server, the connection transitions from HTTP to WebSocket, allowing subsequent communication through the WebSocket protocol. This handshake sequence forms a crucial component of WebSocket functionality, guaranteeing harmony with pre-existing web infrastructure while facilitating real-time peer-to-peer interactions.
2.3 Establishing and Maintaining a Persistent Connection:
Unlike conventional HTTP connections, which lack any lasting attachments and necessitate repeated establishment for every request, WebSockets initially set up a permanent connection, eliminating the need for constant re-establishment. This permanence facilitates immediate data transfer [8], minimizing delays and enabling swift response to alterations from either side. The mechanism responsible for sustaining an open pathway for communication plays a vital role in the instantaneous responsiveness that WebSockets offer, rendering it a potent instrument for crafting engaging and vibrant web encounters.
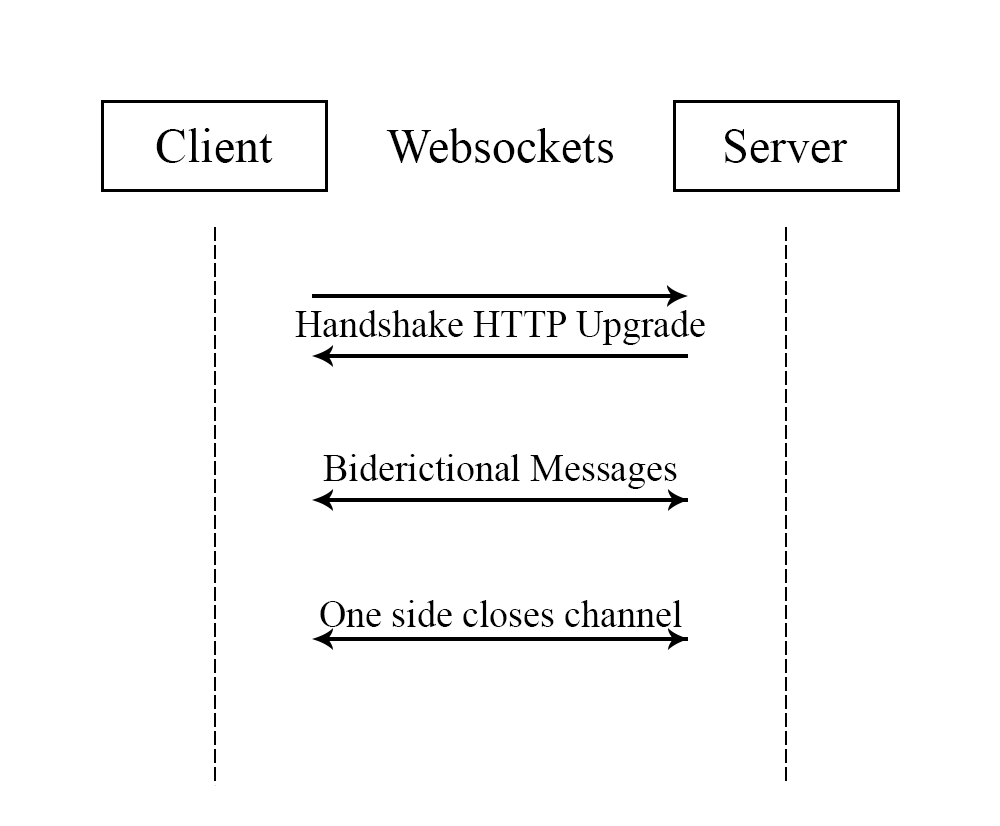
Figure 1. Client Server interactions in Websockets
Developers who grasp the fundamental principles of WebSockets are equipped with the groundwork needed to efficiently implement and enhance their functionality. By delving into bidirectional communication, the process of handshaking, and establishing persistent connections, they lay the foundation for further exploration into architectural considerations, integration strategies, and crucial security measures. These elements are essential for designing web experiences that are interactive and responsive.
3. Security in Real-Time Communication
Nowadays, the field of web development is developing at breakneck speed, and due to that privacy protection [9] and security measures for real-time communications have become more important than ever. Applications now relying on cutting-edge technologies such as WebSockets to ease for data exchange, it is just as important to make sure that these communication channels are protected against any potential threats or weaknesses [10]. In this age of interconnectedness where interactive communication becomes important for creating appealing user experiences, a proper understanding about how to secure the systems from security [11] threats in real-time communications is mandatory for developers and system architects.
3.1 Threats and Challenges in WebSocket Security:
While we get into the world of WebSockets, it is crucial to remember that security also has to be maintained. These channels offer fast and easy real-time communication; however, they need protection from possible threats. Scary predators lay in wait, ready to capitalize on weaknesses like man-in-the middle attacks or unauthorized access and data interception. The complexity of WebSockets, the bidirectional flow adds another level. Thus, it is important to consider vulnerabilities during the establishment of connection as well as while transferring data [12]. In order to bolster our WebSocket-based applications and make sure they stand up against attacks that would affect security, we should start by acquainting ourselves with these threats and challenges.
Table 1: Threats and Challenges faced in Websocket Security
Threats and Challenges | Description | Solution |
Cross-Site WebSocket Hijacking (CSWSH) | Malicious websites attempt to hijack WebSocket connections for unauthorized access. This can lead to potential security breaches and unauthorized access to sensitive data exchanged over WebSocket connections. | Implement proper Cross-Origin Resource Sharing (CORS) policies, use secure authentication mechanisms (OAuth, JWT), and enforce strict authorization controls. |
Denial-of-Service (DoS) Attacks | Attackers flood the WebSocket server with connection requests or messages, impacting availability. This can lead to service disruptions, making the WebSocket infrastructure unavailable for legitimate users. | Implement rate limiting, connection throttling, and use a Web Application Firewall (WAF) to filter and block malicious traffic. Ensure server capacity and scalability to handle high loads [13]. |
Session Hijacking | Attackers attempt to hijack WebSocket sessions by stealing session identifiers or tokens, gaining unauthorized access to active sessions. | Implement secure session management practices, including the use of unique session identifiers, token validation, and regular session audits. Use secure, HTTP-only cookies for session storage [14]. |
Protocol Downgrade Attacks | Attackers attempt to force WebSocket connections to downgrade to less secure protocols. | Use strong cryptographic handshake mechanisms and protocols. Implement server-side checks to ensure that connections adhere to secure protocols (wss://) and reject insecure connections. |
3.2 Best Practices for Securing WebSocket Connections:
To minimize WebSocket security risks, developers should follow well-known and time-tested methods. Secure WebSocket connections through the standard ws protocol are an absolute priority. In addition, the integration of secure login mechanisms like tokens and API keys makes it even more protected against unauthorized access. By frequently updating software and applying patches, developers are able to address any potential vulnerabilities that may occur in WebSocket libraries or the server infrastructure. Using these best practices, they will be able to set up a robust privacy framework [15] for the WebSocket connections so that real-time data being exchanged can remain protected regarding its integrity and confidentiality.
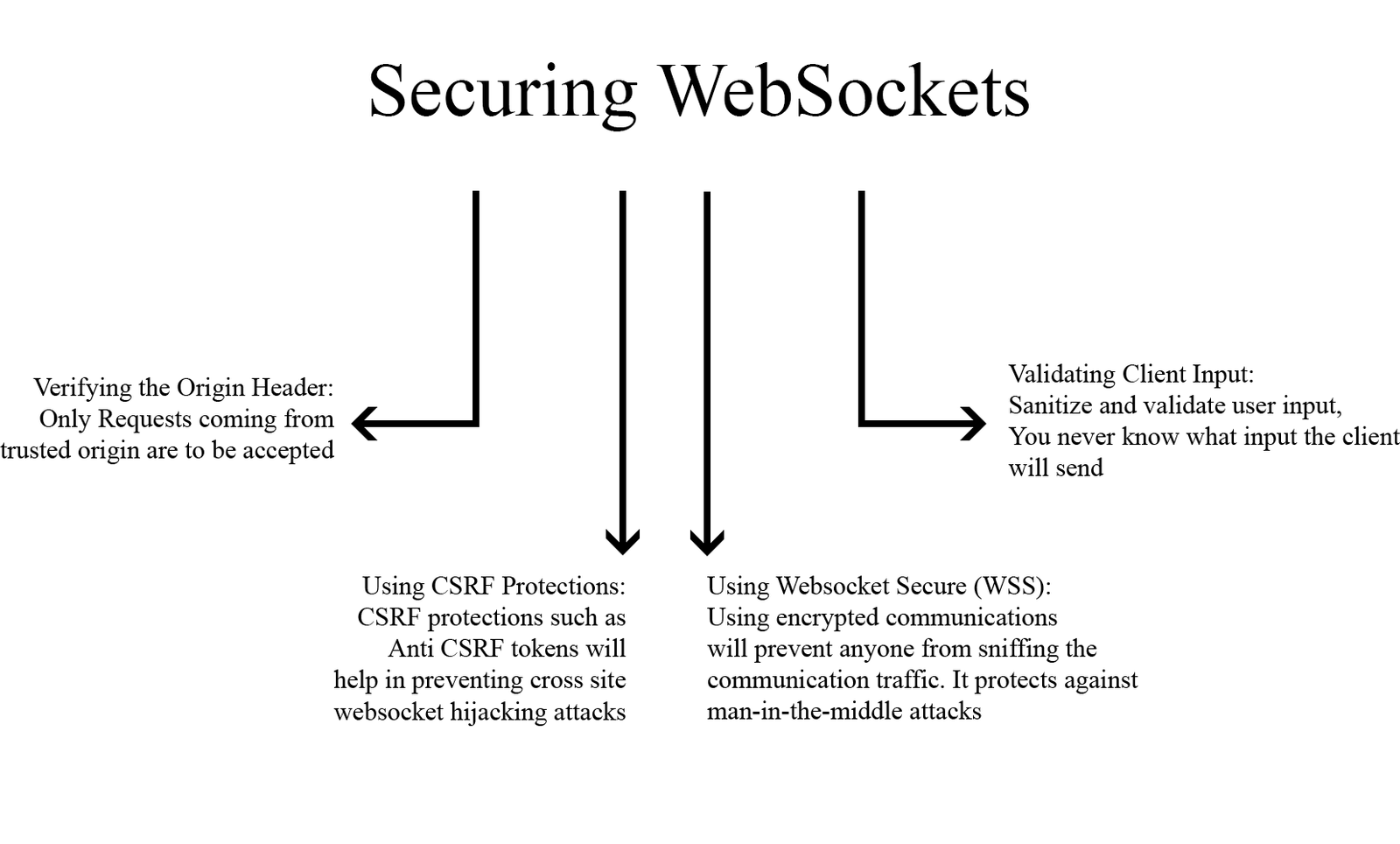
Figure 2. Practices to secure Websockets
3.3 Ensuring Confidentiality and Integrity of Real-Time Data:
These mechanisms do not only protect the data to be transmitted but ensure that it has neither been altered by using message authentication codes and digital signatures. Secure key management ensures further increases the confidentiality level of data in WebSockets. All these measures together help create a secure atmosphere where users can believe in the fact that their real-time interactions are private and no one intervenes without authorization.
4. Optimizing Real-Time Communication with Parallel Computing in Websockets
When using the term parallel computing in relation to websockets and real-time communication, we are really talking about doing more than one computation or managing multiple tasks simultaneously. This can have a positive impact on the effectiveness and speed[16]-[17] of real-time applications. So, let’s explore the implementation of parallel computing ideas in web-sockets and real-time communication.
4.1 Concurrency and Asynchronous Programming:
When it comes to real-time communication, the combination of concurrency and asynchronous programming is crucial for improving the efficiency of websockets. Websockets are specifically designed for two-way communication and require a quick and simultaneous approach to handle multiple connections at once. Asynchronous programming is essential in achieving this concurrency as it allows the application to effectively manage different tasks while waiting for input/output operations, like sending or receiving messages through websockets.
4.2 Multi-threading and Multi-Processing:
To achieve parallelism, one can opt for either multi-threading or multi-processing with the help of multicore chips [18-19]. By assigning each connection or client to its own thread or process, they can operate simultaneously, ensuring smooth management of multiple concurrent communications. This approach prevents the entire application from being blocked, thus enhancing efficiency and performance.

4.3 Parallel Message Processing:
When you have a lot of messages or data in real-time communication, parallel message processing can be useful. For example, the messages from different clients do not depend on each other; thus, they can be processed in parallel which increases their efficiency and speed [20-21].

4.4 Caching and Optimization
When we aim to improve the performance of applications that require real-time action, the realm of parallel computing broadens beyond just dealing with multiple tasks at once. It includes implementing methods like caching and optimizing strategies to make things faster and more efficient. By storing commonly used data and fine-tuning algorithms, we can greatly enhance overall effectiveness. Moreover, the idea of loop unrolling [22] adds another layer of efficiency to these strategies by reducing unnecessary calculations.
It is noteworthy to understand that not every task can be effectively divided into parallel tasks, and there might be obstacles like synchronization and maintaining data integrity. Moreover, the selection of parallelization methods relies on the unique demands and attributes of your real-time application. It is crucial to always weigh the pros and cons as well as the intricate aspects associated with parallel computing when making design choices.
5. Performance Optimization Techniques
5.1 Addressing Latency Issues:
Latency reduction plays a pivotal role in enhancing the responsiveness of real-time communication. To delve into the impact, let’s consider a mathematical perspective. Let RTT_original indicate the original round-trip time and optimized be the abbreviation for rounded trip time after optimization. The latency reduction (Latency_Reduction) can be expressed as:
Latency_Reduction = RTT_original – RTT_optimized
This reduction directly influences the responsiveness of the application, illustrating the time saved in the communication cycle. For instance, if the Original RTT measure is 100 milliseconds – and this optimization reduces it to 75 ^ q, Latency_Reduction would be measured at any number less than those values. This is an example of the immediate reward for tackling latency issues in real time communication where users receive faster responses.
5.2 Strategies for Efficient Data Transmission:
Efficient data transmission, often achieved through compression algorithms like gzip, can be quantified by examining the compression ratio. Let Original_Size be the size of original data, and Compressed_Size denote after compression. The compression ratio (Compression_Ratio) is given by:
Compression Ratio = Original Size/Compressed Size
A higher compression ratio indicates more efficient data transmission, reducing bandwidth usage and accelerating transmission speed. If the original data size is 1000 KB, and compression decreases it to 5% MB then Compression_Ratio would be 2. This mathematical representation underscores the significance of efficient data transmission strategies in optimizing the performance of real-time communication [23].
5.3 Ensuring High Performance in Real-Time Applications:
The efficiency gained in managing concurrent connections, a crucial aspect of high-performance real-time applications, can be mathematically explored through the impact of connection pooling. Let Time_original denote the time spent on setting up a connection without connection pooling, and Time_optimized represent the time with connection pooling. The time reduction (Time_Reduction) can be expressed as:
Time_Reduction = Time_original – Time_optimized
This reduction signifies the efficiency gained in handling multiple simultaneous connections, leading to improved application performance. For example, if the original connection setup time is 50 milliseconds, and connection pooling reduces it to 30 milliseconds, the Time_Reduction would be 20 milliseconds. This mathematical perspective emphasizes the tangible time savings achieved through connection pooling, contributing to the overall high performance of real-time applications. While these mathematical expressions provide a theoretical framework [24], it is crucial to supplement them with empirical testing and performance monitoring to validate their effectiveness in specific application contexts. Practical implementation considerations, network conditions, and evolving application requirements are integral aspects of evaluating the real-world impact of these optimization strategies [23].
6. Conclusion:
In summary, this investigation of WebSockets and how they contribute to real-time communication shows just what an effect interactive communication have played as the modern web has evolved. WebSockets have fundamentally changed the original client/server structure and allowed web applications to become more dynamic, responsive thus meeting user’s growing needs. In this article, we explore the realm of optimization methods. These methods address the problems related to latency, data transfer efficiency and overall performance in real-time applications. By doing this, developers are equipped with a full set of tools. Moreover, we acquire an understanding of how these techniques provide benefits through a mathematical perspective. This gives an insight into their capability to reduce latency, enhance data transfer efficiency and consequently improve the performance of applications. Moreover, when you look at WebSocket architecture considerations as well as integration strategies, security concerns and real-life applications – it becomes apparent that the diversity of use cases is just limitless starting from messaging platforms to live collaboration tools up to online gaming environments.
References
- Hanson, Leah. (2016). Inside Websockets. 110. 10.1145/2959689.2960084.
- Mengi, G., Singh, S.K., Kumar, S., Mahto, D., Sharma, A. (2023). Automated Machine Learning (AutoML): The Future of Computational Intelligence. In: Nedjah, N., Martínez Pérez, G., Gupta, B.B. (eds) International Conference on Cyber Security, Privacy and Networking (ICSPN 2022). ICSPN 2021. Lecture Notes in Networks and Systems, vol 599. Springer, Cham. https://doi.org/10.1007/978-3-031-22018-0_28 .
- Q. Liu and X. Sun, “Research of Web Real-Time Communication Based on Web Socket,” International Journal of Communications, Network and System Sciences, Vol. 5 No. 12, 2012, pp. 797-801. doi: 10.4236/ijcns.2012.512083.
- Aggarwal, K., Singh, S.K., Chopra, M., Kumar, S., Colace, F. (2022). Deep Learning in Robotics for Strengthening Industry 4.0.: Opportunities, Challenges and Future Directions. In: Nedjah, N., Abd El-Latif, A.A., Gupta, B.B., Mourelle, L.M. (eds) Robotics and AI for Cybersecurity and Critical Infrastructure in Smart Cities. Studies in Computational Intelligence, vol 1030. Springer, Cham. https://doi.org/10.1007/978-3-030-96737-6_1 .
- Singh, M., Singh, S.K., Kumar, S., Madan, U., Maan, T. (2023). Sustainable Framework for Metaverse Security and Privacy: Opportunities and Challenges. In: Nedjah, N., Martínez Pérez, G., Gupta, B.B. (eds) International Conference on Cyber Security, Privacy and Networking (ICSPN 2022). ICSPN 2021. Lecture Notes in Networks and Systems, vol 599. Springer, Cham. https://doi.org/10.1007/978-3-031-22018-0_30 .
- Kumar, R., Singh, S. K., & Lobiyal, D. K. (2023). UPSRVNet: Ultralightweight, Privacy preserved, and Secure RFID-based authentication protocol for VIoT Networks. The Journal of Supercomputing, 1-28.
- Vats, T., Singh, S.K., Kumar, S. et al. Explainable context-aware IoT framework using human digital twin for healthcare. Multimed Tools Appl (2023). https://doi.org/10.1007/s11042-023-16922-5 .
- Dubey, H. A. R. S. H. I. T., Kumar, S. U. D. H. A. K. A. R., & Chhabra, A. N. U. R. E. E. T. (2022). Cyber Security Model to Secure Data Transmission using Cloud Cryptography. Cyber Secur. Insights Mag, 2, 9-12.
- Sharma, A., Singh, S. K., Chhabra, A., Kumar, S., Arya, V., & Moslehpour, M. (2023). A Novel Deep Federated Learning-Based Model to Enhance Privacy in Critical Infrastructure Systems. International Journal of Software Science and Computational Intelligence (IJSSCI), 15(1), 1-23. http://doi.org/10.4018/IJSSCI.334711.
- Kumar, R., Singh, S. K., & Lobiyal, D. K. (2023). Communication structure for Vehicular Internet of Things (VIoTs) and review for vehicular networks. In Automation and Computation (pp. 300-310). CRC Press.
- Choudhary, S. & Singh, N. (2022). Analysis of Security-Based Access Control Models for Cloud Computing. International Journal of Cloud Applications and Computing (IJCAC), 12(1), 1-19. http://doi.org/10.4018/IJCAC.2022010104.
- Sharma, A., Singh, S.K., Kumar, S., Chhabra, A., Gupta, S. (2023). Security of Android Banking Mobile Apps: Challenges and Opportunities. In: Nedjah, N., Martínez Pérez, G., Gupta, B.B. (eds) International Conference on Cyber Security, Privacy and Networking (ICSPN 2022). ICSPN 2021. Lecture Notes in Networks and Systems, vol 599. Springer, Cham. https://doi.org/10.1007/978-3-031-22018-0_39 .
- Z. Chao-yang, “DOS Attack Analysis and Study of New Measures to Prevent,” 2011 International Conference on Intelligence Science and Information Engineering, Wuhan, China, 2011, pp. 426-429, doi: 10.1109/ISIE.2011.66.
- Baitha, Anuj & Vinod, Smitha. (2018). Session Hijacking and Prevention Technique. International Journal of Engineering & Technology. 7. 193. 10.14419/ijet.v7i2.6.10566.
- Joshi, B., Joshi, B., Mishra, A., Arya, V., Gupta, A. K., & Peraković, D. (2022). A Comparative Study of Privacy-Preserving Homomorphic Encryption Techniques in Cloud Computing. International Journal of Cloud Applications and Computing (IJCAC), 12(1), 1-11. http://doi.org/10.4018/IJCAC.309936.
- S. Kumar, S. K. Singh and N. Aggarwal, “Sustainable Data Dependency Resolution Architectural Framework to Achieve Energy Efficiency Using Speculative Parallelization,” 2023 3rd International Conference on Innovative Sustainable Computational Technologies (CISCT), Dehradun, India, 2023, pp. 1-6, doi: 10.1109/CISCT57197.2023.10351343.
- Sudhakar Kumar, Sunil Kr. Singh, Naveen Aggarwal & Kriti Aggarwal (2021) Evaluation of automatic parallelization algorithms to minimize speculative parallelism overheads: An experiment, Journal of Discrete Mathematical Sciences and Cryptography, 24:5, 1517-1528, DOI: 10.1080/09720529.2021.1951435.
- Kumar, S., Singh, S. K., & Aggarwal, N. (2023). Speculative parallelism on multicore chip architecture strengthen green computing concept: A survey. In Advanced Computer Science Applications (pp. 3-16). Apple Academic Press.
- Kumar S, Singh SK, Aggarwal N, Gupta BB, Alhalabi W, Band SS. An efficient hardware supported and parallelization architecture for intelligent systems to overcome speculative overheads. Int J Intell Syst. 2022; 37: 11764-11790. doi:10.1002/int.23062
- Kumar, S., Singh, S. K., Aggarwal, N., Gupta, B. B., Alhalabi, W., & Band, S. S. (2022). An efficient hardware supported and parallelization architecture for intelligent systems to overcome speculative overheads. International Journal of Intelligent Systems, 37(12), 11764-11790.
- Kumar, S. S., Singh, S. K., Aggarwal, N., & Aggarwal, K. (2021). Efficient speculative parallelization architecture for overcoming speculation overheads. In International Conference on Smart Systems and Advanced Computing (Syscom-2021) (Vol. 3080, pp. 132-138).
- Singh, I., Singh, S. K., Singh, R., & Kumar, S. (2022, May). Efficient loop unrolling factor prediction algorithm using machine learning models. In 2022 3rd International Conference for Emerging Technology (INCET) (pp. 1-8). IEEE.
- Peñalvo, F. J., Sharma, A., Chhabra, A., Singh, S. K., Kumar, S., Arya, V., & Gaurav, A. (2022). Mobile Cloud Computing and Sustainable Development: Opportunities, Challenges, and Future Directions. International Journal of Cloud Applications and Computing (IJCAC), 12(1), 1-20. http://doi.org/10.4018/IJCAC.312583 .
- Peñalvo, F. J., Maan, T., Singh, S. K., Kumar, S., Arya, V., Chui, K. T., & Singh, G. P. (2022). Sustainable Stock Market Prediction Framework Using Machine Learning Models. International Journal of Software Science and Computational Intelligence (IJSSCI), 14(1), 1-15. http://doi.org/10.4018/IJSSCI.313593 .
Cite As:
Arora S (2024) WebSockets and Real-Time Communication, Insights2Techinfo, pp.1