Everyone has heard about DDoS attacks [1-4] and how they can be disruptive to service and networks, but do you know what a DDoS attack actually entails? And how much more complicated is it than first glance might make it seem? Read on to find out, and to learn first-hand account of the technicalities and details in this article; you might think twice before clicking on that link with the pretty animation!
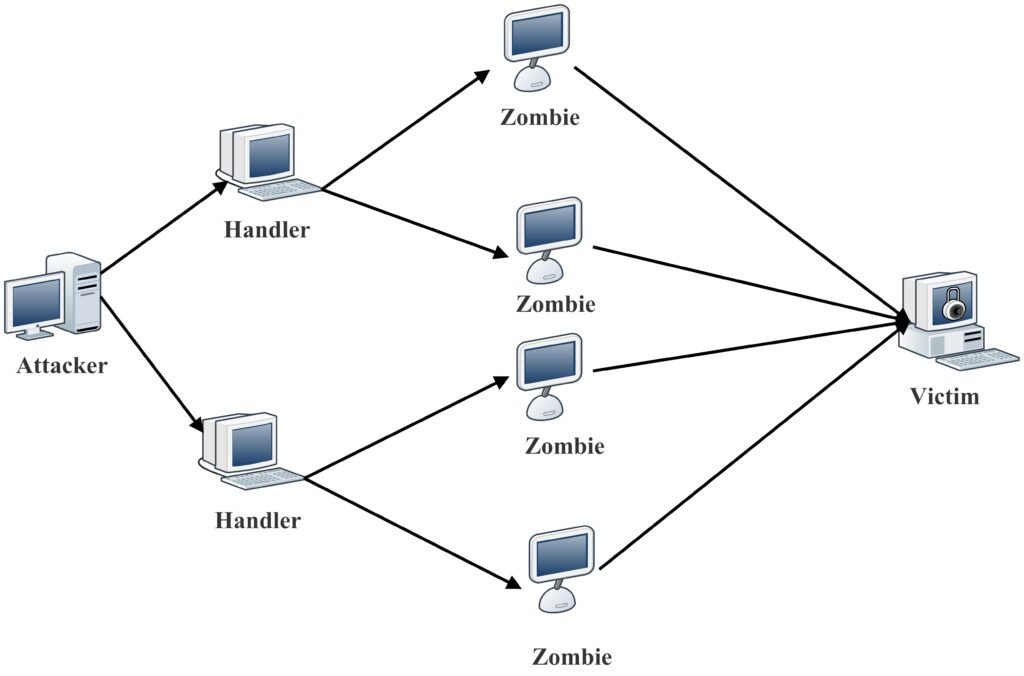
What is a DDoS attack?
A distributed denial-of-service attack (DDoS) is an attack that floods a system with requests from numerous sources. These requests overload the system and thereby delay or potentially prevent access from legitimate users [5-6].
What are the different types of DDoS attacks?
A DDoS attack can be classified as a volumetric, protocol overload, or application-level attack. Volumetric attacks consist of sending as much as possible to the target’s computer network or “sending packets that saturates” the connection bandwidth and storage space on the server. Protocol overload an application-level attack is one that includes malicious commands and requests that may not always consume a lot of bandwidth and storage, but it forces the computing resources to use an enormous amount of system memory and CPU time.
Why would someone want to do a DDoS attack?
Generally, the reasons why people would want to cause a DDoS attack are for fame, fun, or revenge. These individuals may also use them for serious matters like cybersecurity breaches. Whoever has access to the resources necessary to cause these attacks will inevitably be able to distinguish themselves in some way given enough time and devote resources [7-8].
Prevention techniques
One of the best defenses ⸺ around-the-clock security staffing on your infrastructure, which includes security technologies such as intrusion captcha service, prevention system (IPS & IDS), firewalls, and web application firewalls (WAF) ̶ is to limit server access. That goes for both the perimeter and the internal network. It’s important that employees follow company guidelines when connecting to any network over a public connection so they don’t inadvertently expose a sensitive company resource [9-10].
Conclusion
These types of cyber attacks are very difficult to fend off because the perpetrator’s location remains unknown. The best solution is to maintain your network security, make sure you have a backup plan in case of an attack, and research who your cyber protection company is before engaging in business with them—preferably one that comes recommended by people you know.
References
- Zargar, S. T., Joshi, J., & Tipper, D. (2013). A survey of defense mechanisms against distributed denial of service (DDoS) flooding attacks. IEEE communications surveys & tutorials, 15(4), 2046-2069.
- Mishra, A., et al. (2011, September). A comparative study of distributed denial of service attacks, intrusion tolerance and mitigation techniques. In 2011 European Intelligence and Security Informatics Conference (pp. 286-289). IEEE.
- Gupta, B. B., Misra, M., & Joshi, R. C. (2012). An ISP level solution to combat DDoS attacks using combined statistical based approach. arXiv preprint arXiv:1203.2400.
- Peng, T., Leckie, C., & Ramamohanarao, K. (2007). Survey of network-based defense mechanisms countering the DoS and DDoS problems. ACM Computing Surveys (CSUR), 39(1), 3-es.
- Mishra, A., Gupta, N., et al. (2021). Defense mechanisms against DDoS attack based on entropy in SDN-cloud using POX controller. Telecommunication systems, 77(1), 47-62.
- Dahiya, A., et al. (2021). A reputation score policy and Bayesian game theory based incentivized mechanism for DDoS attacks mitigation and cyber defense. Future Generation Computer Systems, 117, 193-204.
- Dahiya, A., et al. (2019). A PBNM and economic incentive-based defensive mechanism against DDoS attacks. Enterprise Information Systems, 1-21.
- Gupta, B. B., Agrawal, P. K., Joshi, R. C., & Misra, M. (2011, January). Estimating strength of a ddos attack using multiple regression analysis. In International Conference on Computer Science and Information Technology (pp. 280-289). Springer, Berlin, Heidelberg.
- Gaurav, A., et al. (2021, June). Filtering of distributed denial of services (ddos) attacks in cloud computing environment. In 2021 IEEE International Conference on Communications Workshops (ICC Workshops) (pp. 1-6). IEEE.
- Gupta, B. B., Dahiya, A., et al. (2020). A comprehensive survey on DDoS attacks and recent defense mechanisms. Handbook of Research on Intrusion Detection Systems, 186-218.
FAQ on DDoS attack
Cloudflare will not mitigate all attacks, because some large scale attackers can overwhelm their capacity. Cloudflare is best for “run-of-the-mill” DDoS attacks that are NOT specifically targeted at you, or trivial to block (like in the case of DNS reflection). If you are being directly targeted, or if your attack is very sophisticated – it may be necessary to utilize more expensive services like scrubbing centers.
DDoS Protection for Azure is the service for preventing, detecting and responding to DDoS attacks against your web applications. The protection is provided by Microsoft through a shared IP address space that covers all customers who subscribe to this service. This shared IP address space allows the traffic from different customers to be routed via the same route, hence if some customer originates malicious traffic, this traffic will be received by all other customers in the same network, which reduces the impact on each customer individually.