By: Gonipalli Bharath Vel Tech University, Chennai, India International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, Gmail: gonipallibharath@gmail.com
Abstract:
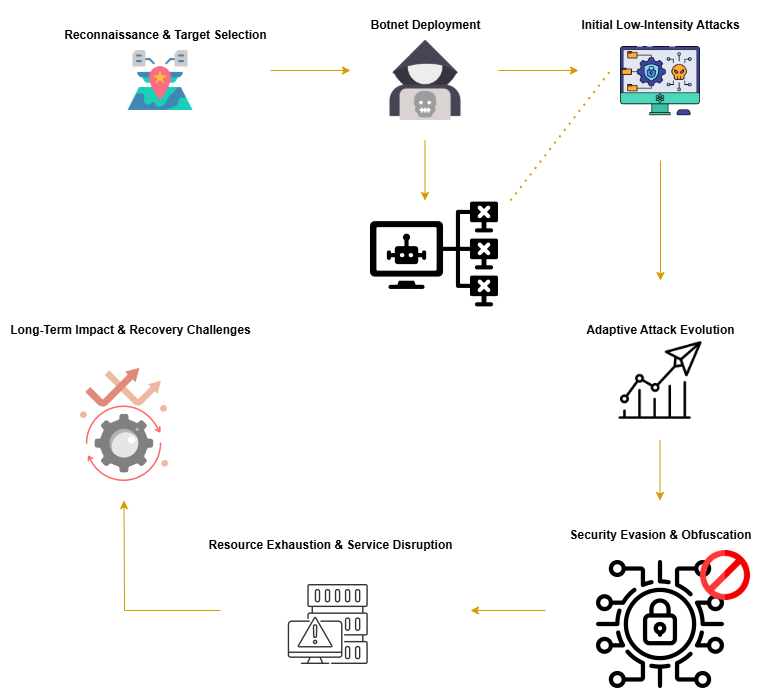
Modern cyber warfare has experienced significant changes that brought Distributed Denial of Service (DDoS) attacks into the hands of hostile parties. Organizations and governments together with critical infrastructure face new threats because AP-DDoS has transformed into a sophisticated and extended cyber threat. AP-DDoS stands apart from normal DDoS attacks through its extended conduction of adaptable and elusive attack approaches while posing high challenges to defense initiatives. The paper examines AP-DDoS features along with the effects it has on cybersecurity protection as well as prevention strategies. This paper presents an attack process diagram through a flowchart.
Introduction:
Organizations become more exposed to cyberattacks through their expanding digital infrastructure dependence while DDoS attacks represent one of the main vulnerabilities. The conventional approach of DDoS attacks sends too much traffic to target servers which results in disrupted services. AP-DDoS attacks have transformed DDoS into a sophisticated manner of cyber assault that produces widespread harm. AP-DDoS attacks maintain their status due to continued duration combined with evasive capabilities and strategic objectives which are usually executed by nation-sponsored cybercriminals alongside organized crime operations[1]. AP-DDoS campaigns operate at a much longer timescale than DDoS attacks because they keep adapting and evolving during extended periods reaching weeks and months.
Characteristics of AP-DDoS Attacks:
The characteristics that set AP-DDoS attacks apart from standard DDoS attacks include their following features:
- Persistence: AP-DDoS attacks continue indefinitely which makes protection extremely difficult to achieve while stripping organizations of their available resources.
- Adaptive Techniques: The attackers utilize adjustable traffic pattern modifications to escape detection while making standard defensive methods useless to protect against their attacks.
- Multi-Vector Approach: The Target Supporting Multi-Vector Approach allows AP-DDoS attackers to launch volumetric in combination with protocol and application-layer attacks for overwhelming effects.
- Botnet Utilization: A large population of compromised devices powered by botnets send constant attack traffic which automatically responds to security adjustments throughout the attack.
- Stealth Mechanisms: Attackers implement stealth attack methods which start with modest attack forces that slowly rise to avoid detection from current security equipment.
Impact of AP-DDoS on Cybersecurity:
AP-DDoS attacks create significant damage to multiple sectors because of their serious consequences.
- Economic Disruption: The running durations of such attacks create significant economic damage which affects both business operations and their provider networks. The disruption of online transactions by prolonged outages affects the revenues of companies that depend on electronic business platforms[2]. The finance sector and healthcare industry and other sectors face operational interruptions which require extensive remedy projects.
- Infrastructure Damage: Attacks which extend beyond normal times force hardware to break down while simultaneously degrading performance levels of infrastructure systems. Under continuous pressure from attacks routers along with firewalls and network load balancers experience premature wear that leads to increased costs for maintenance. Long-standing weaknesses emerge from these attacks which provide sufficient entry points for later exploitation by attackers[3].
- Data Breaches: Certain AP-DDoS attacks function as decoys which provide hackers the opportunity to launch sophisticated cyber intrusions against the same network. Newly formed security vulnerabilities during attack mitigation efforts provide hackers the opportunity to insert malware, carry out data theft and ascend security permissions throughout the network[4].
- National Security Threats: State-sponsored AP-DDoS activities specifically target government departments along with military facilities and utility infrastructure operating at the national level. The strikes interrupt essential public operations while damaging economic equilibrium to support the operational goals of modern cyber warfare operations against nations[5].
- Operational Fatigue: Manufacturing wear and tear among cybersecurity teams develops through nonstop attacks which leads them to experience exhaustion while making their systems progressively more insecure. Security professionals monitor continuous threats twenty-four hours per day while their effectiveness declines due to extended hours which raises the possibility of defense errors[6].
Defensive Strategies Against AP-DDoS:
AP-DDoS attack mitigation needs both defensive steps before and after attacks begin.
- AI-Powered Threat Detection: For the purpose of to avoid various dangers from occurring, algorithms with artificial intelligence analyze circulation patterns and discover novel hazards. The AI-driven systems create capabilities to differentiate between normal traffic and attacks while delivering better response outcomes with decreased numbers of false alarms.
- Traffic Scrubbing & Load Balancing: Load balancing techniques combined with traffic scrubbing make it possible to distribute Internet traffic between multiple servers in order to avoid performance bottlenecks. Scrubbing services run checks on incoming data packets during real-time operation to eliminate destructive requests from reaching crucial infrastructure.
- Behavioral Analysis & Anomaly Detection: System detection of irregular behaviors enables security personnel to identify threats before their inception. Security systems need to use dynamic baselining methods which detect unusual traffic behavior patterns so they can expedite the handling of suspicious data.
- Zero Trust Security Framework: Through Zero Trust Security Framework organizations can achieve strict access controls which decreases their potential attack vulnerabilities. Facts must be enforced along with multiple authentication factors and network partitions and authorization by roles to defend against cyber intrusion risks.
- Collaboration with ISPs & Security Firms: Security companies and Internet service providers unite their efforts to share threat intelligence through collaboration which leads to becoming more effective at real time threat detection. Internet service providers together with cybersecurity vendors effectively share attack signatures for network-level traffic analysis to speed up malicious traffic detection followed by blocking.
Conclusion:
AP-DDoS stands as an advanced version of double-digit denial-of-service cyber threats that exceeds standard security protocols. AP-DDoS differentiates from traditional attacks because it creates an extended danger that continues perpetually demanding permanent associated security precautions. Organizations alongside governments should create predictive security systems based on artificial intelligence threat analysis to work with other entities for combatting these threats effectively.
To combat evolving adversaries effectively it is critical to buy security solutions which lead the market and provide ongoing training to employees and multilateral cooperation. A contingency approach that integrates information technology, safety models, as well as exchange of information toward advanced intrusions is crucial to safeguarding electronic records along with services.
References:
- “Mitigation strategies for distributed denial of service (DDoS) in SDN: A survey and taxonomy: Information Security Journal: A Global Perspective: Vol 32, No 6.” Accessed: Mar. 03, 2025. [Online]. Available: https://www.tandfonline.com/doi/abs/10.1080/19393555.2022.2111004
- “Mitigation strategies for distributed denial of service (DDoS) in SDN: A survey and taxonomy: Information Security Journal: A Global Perspective: Vol 32, No 6.” Accessed: Mar. 03, 2025. [Online]. Available: https://www.tandfonline.com/doi/abs/10.1080/19393555.2022.2111004
- “Cyberphysical Security of Grid Battery Energy Storage Systems | IEEE Journals & Magazine | IEEE Xplore.” Accessed: Mar. 03, 2025. [Online]. Available: https://ieeexplore.ieee.org/abstract/document/9787060
- “Cyber Threat Analysis and Mitigation in Emerging Information Technology (IT) Trends | SpringerLink.” Accessed: Mar. 03, 2025. [Online]. Available: https://link.springer.com/chapter/10.1007/978-3-031-56728-5_47
- D. Moore, Offensive Cyber Operations: Understanding Intangible Warfare. Oxford University Press, 2022.
- “Beyond Defense: Proactive Approaches to Disaster Recovery and Threat Intelligence in Modern Enterprises.” Accessed: Mar. 03, 2025. [Online]. Available: https://www.scirp.org/journal/paperinformation?paperid=131680
- Zou, L., Sun, J., Gao, M., Wan, W., & Gupta, B. B. (2019). A novel coverless information hiding method based on the average pixel value of the sub-images. Multimedia tools and applications, 78, 7965-7980.
- Stergiou, C. L., Psannis, K. E., & Gupta, B. B. (2021). InFeMo: Flexible big data management through a federated cloud system. ACM Transactions on Internet Technology (TOIT), 22(2), 1-22.
- Bhatti, M. H., Khan, J., Khan, M. U. G., Iqbal, R., Aloqaily, M., Jararweh, Y., & Gupta, B. (2019). Soft computing-based EEG classification by optimal feature selection and neural networks. IEEE Transactions on Industrial Informatics, 15(10), 5747-5754.
- Navaneeth J. (2024) Real-World Applications of Deep Learning in Phishing Detection, Insights2Techinfo, pp.1
Cite As
Bharath G. (2025) Advanced Persistent DDoS (AP-DDoS): A New Breed of Cyber Warfare, Insights2Techinfo, pp.1