By: Praneetha Neelapareddigari, Department of Computer Science & Engineering, Madanapalle Institute of Technology and Science, Angallu (517325), Andhra Pradesh. praneetha867reddy@gmail.com
Abstract
Artificial intelligence is the practical concept used to enhance and advance cyber defence procedures. Traditional methods of controlling cyber security threats, which involve the use of automated tools and identification of threats based on matching against pre-known signatures, are gradually proving insufficient due to growth of cyber threats complexity and the frequency of their occurrence. Conventional Methods of security are now facing new types of cyber threats that pose risk to the digital world. At the same time, along with the possible position of AI in the sphere of cybersecurity, it is essential to note that there is no information about how AI should be applied and how the corresponding challenges should be addressed. More work must be done in this field to understand how AI really supports cybersecurity in consideration of the appropriate ethic and risk-related factors to address. Based on a broad review of existing deployment of the AI-based cyber defence solutions and future trends, this work offers a clear insight of how AI is shaping the next generation cyber security and how it is going to impact the individuals and company. This paper describes the changes in role of AI that helps in the development of security systems that can learn new threats and change its protection methods.
Keywords: Artificial Intelligence, Deep learning, Machine Learning, cyber defence, cyberattacks.
1. Introduction
The safety of online sectors in this digital world is too less as the cyberattacks is more frequent nowadays. The traditional methods that are used in cybersecurity finds to be difficult to keep up all these changing threats as they frequently rely on manual analysis and signature-based techniques the most. The data that is increasing as a huge amount and the sophistication of cyberattacks, where there is involvement of ransomware, advanced persistent threats (APTs), and zero-day exploits are mostly the reason for this insufficiency. Artificial intelligence (AI) has become a potent weapon for strengthening cyber defence capabilities in this environment. To further improve defences against cyber threats, cybersecurity frameworks that incorporate AI algorithms, machine learning, and deep learning approaches are a significant advancement[1].
2. Cyberattacks
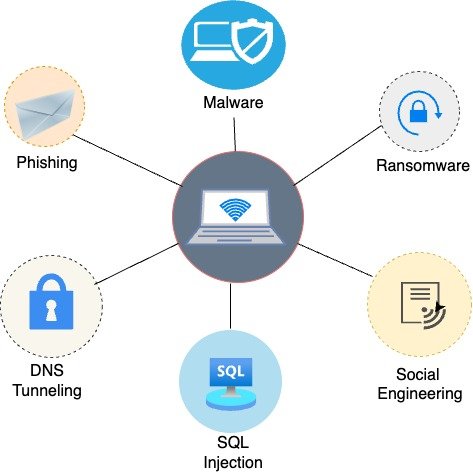
Cyberattack are the collection of tactics and methods that hackers employ to breach computer networks, systems, or data. Here are a few typical cyberattack strategies:
- Phishing
- Malware
- Denial of Service (DoS)
- SQL injection
- Brute Force Attacks
- Ransomware
- Credential Stuffing
Cyberattacks are actions that use harmful software (malware) to attack computer networks or systems via the internet [2]. Malware can be dangerous software or viruses that are installed on devices or applications. It also can be the hardware that allows illegal access. The damage that occur in security
services may be damaged by an inability to detect intrusions, putting data availability, and integrity at risk[3].
2.1 Definitions of attack components
Phishing is one of the component name of cyberattacks which is a method that is used for acquiring the sensitive data like any information about bank details through a fake emails. It is a criminal act and the main aim of this phishing attack is that to get personal information such as credit card numbers, bank passwords , usernames , phone numbers , addresses or bank passwords[4].
Malicious software, which is also called as malware is the process of destroying the system or to damage the data that is personal. Malicious refers as the intrusive software developed by criminal or even called as hackers. There are few types of malware practice’s such as viruses, worm’s, trojan, spyware, adware, ransomware[4]. This type of attack can occur if you download the information from any illegal sites.
Vulnerabilities refers that , it is an opportunity in an information system that cyber criminals can exploit and gain the unauthorized access to computer system. Vulnerabilities are the flaw in either software or hardware process as the cyber criminals take a chance to enter systems or networks without authorizations.
3. Proactive Defence Strategies Powered by AI
AI technology and techniques are almost used in every sector in the world as AI solves any problems in a smart way. Similarly the technologies of AI are used in the defence industry for cyber defence. These technologies are used in cyber defence in order to stop the threats and attacks that are actually occurred in the past. There are various concepts involved in AI such as machine learning that is used to implement the algorithms that can recognize odd patterns or behaviours, response systems, predictive analytics and many other tasks. This is more useful for organizations to improve their cybersecurity defences, speed up response times by using AI. The main advantage of using AI in the concept of cybersecurity is to have good analyse of real time data allowing threat detections. Artificial intelligence (AI)-driven systems can have the capacity to mark out the abnormalities and patterns suggestive by monitoring network activity. This would be more easy and possible to step in quick and reduce hazards.
It is even more possible if ethical standards are used to reduce the risks by using an ethical approach to AI that places high standards on accountability, transparency and equity. In this digital world , AI is transforming the cyber sector and helping in various ways as possible in order to find the solutions to many different problems. The essential thing for creating intelligent services due to its computational capacity for automation and decision making[6]. Creating strong frameworks for the deployment of AI requires understanding between industry, academia. The efficiency and ethical deployment of AI- driven cybersecurity solutions is ensured by the establishment of standards and best practices. By using the proactive defence strategies that are powered by AI is more helpful to the sector of cybersecurity so it could be better to know the new attacks before they occur and it is really required rather than getting to know the information after the attack. In order to complete such tasks it is essential to implement AI in cybersecurity to be more responsible.
3.1 Concepts used for Cyber Defence by AI
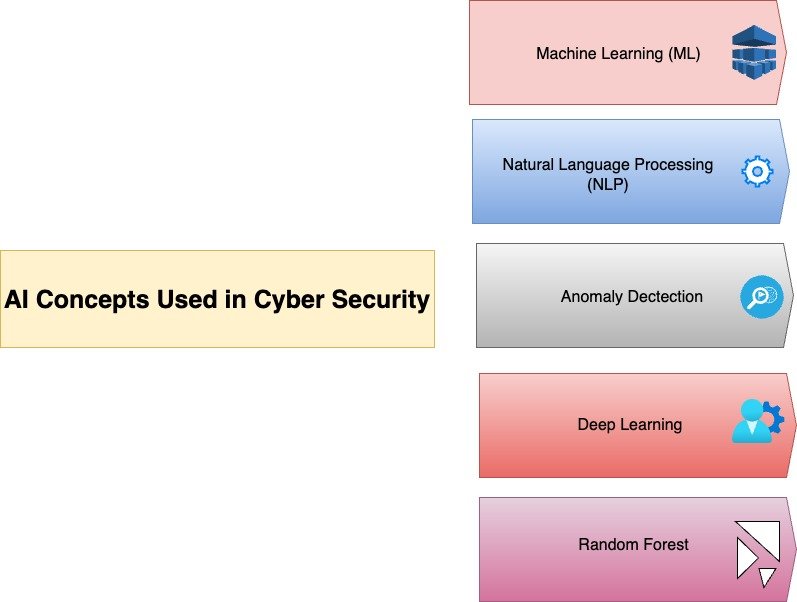
There are few methods to detect, analyse and respond to the threats. Few of the concepts that plays a major role in cyber defence are like machine learning(ML),natural Language processing (NLP),Anomaly detection, behavioural analysis, predictive analytics, deep learning, cyber threat hunting.
Machine learning :
In machine learning concept the supervised learning ,which train models on labelled datasets to know threats like phishing patterns. Similarly the unsupervised learning is used to detect anomalies to identify the unusual patterns in data[7]. Reinforcement learning is applied to have the strong and adaptive security systems. AI and machine learning usage has increased in the industry in response to cybersecurity problems. The concept of machine learning in cybersecurity is done by using analytical and predictive powers to be identified , mitigate and to resolve security problems[8].
Natural Language Processing (NLP) :
This concept is used to understand the human language in various formats such as chat messages, emails and posts. This is applied to detect the phishing attempts, social engineering attacks. Tokenization, sentence splitting, part-of-speech tagging, named entity recognition, and sentiment analysis are just a few of the language analysis features available in Stanford Core NLP, a natural language processing toolbox[9].
Anomaly detection:
Anomaly detection is also called as outlier detection, which is used for identification of observations, events or datapoints that usually deviate. In the concept of cyber security anomaly detection is a monitoring feature of data observability tools that borrows the machine learning concepts to identify unexpected changes in dataset.
Behavioural analysis:
Artificial intelligence (AI) systems are able to track changes in user and object behaviour over time, potentially indicating compromised accounts or insider threats.
Deep learning:
For more difficult tasks like picture recognition and speech recognition (e.g., detecting voice-based phishing assaults), deep learning approaches, such as neural networks, are employed.
Cyber threat hunting:
By evaluating data to find hidden hazards that might not set off conventional security warnings, AI helps with proactive threat hunting.
4. AI-Driven Cyber Defence
Certainly, artificial intelligence cyber defence is defined as the use of machine learning or artificial intelligence technology as a technique to enhance the effectiveness of safety systems in cybersecurity. These technologies assist in enhancing an organization’s capability in being able to detect, prevent, and manage cyber threats.[10].
Real-Time Threat Detection –
Here, AI programs observes and examine user behaviour and network traffic to spot departures from the usual. Then after ,by identifying established attack patterns and signatures, machine learning algorithms enhance the detection of malware and other harmful activity.
Phishing Detection –
By analysing linguistic patterns and context, artificial intelligence(AI) employs natural language processing (NLP) to analyse email content and identify phishing attempts.AI scans emails for URLs and links that lead to harmful websites in order to block users from visiting them.
Data Privacy and Protection –
AI recognizes and tags sensitive data in accordance with organizational policy and privacy regulations, assisting in its classification and protection. By keeping an eye on usage and access trends, AI makes sure that data protection laws are followed.
5.Challenges associated with implementation of AI in cyber defence
5.1 Troubles that occur while using AI
Even though there are many advantages of the concept AI ,but it also have challenges associated and may create a trouble .Here are few challenges that occur due to AI:
- False Positives and False Negatives
The case of false positives is when the behaviours that are not that much harm are even considered without knowing and tagged as threats, in this case AI produces as false positives. This may lead to many problems.
The case of false negatives on the other hand , here in this case AI could fail of predicting the correct statements, especially if it is the new threat evade to detect.
2. Privacy and Security Concerns of data
This issues arises due to frequently accessing the huge amounts of private information. So here the privacy and security issues are brought up. It is necessary to make sure if the data is handled properly and assembles with legal requirements. AI systems themselves may be the subject of cyberattacks if they are not adequately guarded, which could reveal private data. One of the hardest issues with implementing AI, according to Petit and Shladover (2014), is security. The confidentiality, availability, authenticity, and privacy of data and systems are all at risk from a variety of cyberattacks that target advanced artificial intelligence (AI) systems (Cerrudo and Apa, 2017). (Dash, Karimibiuki, and Pattabiraman, 2021)[11-13].
5.2 Overcoming the challenges
There are few addressing solutions to the challenges when the AI is in the picture. For AI-based cybersecurity systems to be reliable and successful, these problems must be resolved. Organizations should adopt a multifaceted strategy to address the drawbacks of utilizing AI in cyber protection. This entails improving AI algorithms to lower false positives and alert fatigue while adding human review to improve precision. The difficulty of developing threats can be addressed by putting into practice a hybrid approach that combines AI with conventional cybersecurity measures and continuing team training. So, strong systems are required to have the high security and to follow the data privacy laws.
Conclusion
The prevention from attacks are the results of using AI technology and techniques. This technology is based on using various concepts like detections, prevention, and reaction capabilities. By integrating AI with cybersecurity led organizations to manage the attacks , adjust the strategies or even to create the new strategies to protect their digital data . The AI alone is not possible to overcome all this complicated tasks so the concepts of machine learning, deep learning, NLP and more are used according to the problem occurred. So this implementations makes many impossible task to be possible. Artificial intelligence(AI) technologies improves and help to detect and respond to threats more faster when compared to traditional methods. All this development that are made have the great improvement to undertake certain challenges even though complicated. AI model is required to manage the data and make sure that every data taken is secure . So this concludes furthermore, in order for AI systems to continue to be effective, they must constantly adapt to the changing nature of cyber threats.
References:
- D. V. V. Vegesna, “Comprehensive Analysis of AI-Enhanced Defense Systems in Cyberspace,” Int. Numer. J. Mach. Learn. Robots, vol. 7, no. 7, Art. no. 7, Dec. 2023, Accessed: Jul. 27, 2024. [Online]. Available: https://injmr.com/index.php/fewfewf/article/view/21
- M. Rahaman, F. Tabassum, V. Arya, and R. Bansal, “Secure and sustainable food processing supply chain framework based on Hyperledger Fabric technology,” Cyber Secur. Appl., vol. 2, p. 100045, Jan. 2024, doi: 10.1016/j.csa.2024.100045.
- N. N. M. Yusof and N. S. Sulaiman, “Cyber Attack Detection Dataset: A Review,” J. Phys. Conf. Ser., vol. 2319, no. 1, p. 012029, Aug. 2022, doi: 10.1088/1742-6596/2319/1/012029.
- R. Derbyshire, B. Green, D. Prince, A. Mauthe, and D. Hutchison, “An Analysis of Cyber Security Attack Taxonomies,” in 2018 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Apr. 2018, pp. 153–161. doi: 10.1109/EuroSPW.2018.00028.
- A. Qamar, A. Karim, and V. Chang, “Mobile malware attacks: Review, taxonomy & future directions,” Future Gener. Comput. Syst., vol. 97, pp. 887–909, Aug. 2019, doi: 10.1016/j.future.2019.03.007.
- I. H. Sarker, “Introduction to AI-Driven Cybersecurity and Threat Intelligence,” in AI-Driven Cybersecurity and Threat Intelligence: Cyber Automation, Intelligent Decision-Making and Explainability, I. H. Sarker, Ed., Cham: Springer Nature Switzerland, 2024, pp. 3–19. doi: 10.1007/978-3-031-54497-2_1.
- L. Triyono, R. Gernowo, P. Prayitno, M. Rahaman, and T. R. Yudantoro, “Fake News Detection in Indonesian Popular News Portal Using Machine Learning For Visual Impairment,” JOIV Int. J. Inform. Vis., vol. 7, no. 3, pp. 726–732, Sep. 2023, doi: 10.30630/joiv.7.3.1243.
- V. Shah, “Machine Learning Algorithms for Cybersecurity: Detecting and Preventing Threats,” Rev. Espanola Doc. Cient., vol. 15, no. 4, Art. no. 4, 2021.
- S. Shao, C. Tunc, P. Satam, and S. Hariri, “Real-Time IRC Threat Detection Framework,” in 2017 IEEE 2nd International Workshops on Foundations and Applications of Self* Systems (FAS*W), Sep. 2017, pp. 318–323. doi: 10.1109/FAS-W.2017.166.
- G. Blessing, A. Azeta, S. Misra, V. Osamor, L. Fernandez-Sanz, and V. Pospelova, “The Emerging Threat of Ai-driven Cyber Attacks: A Review,” Appl. Artif. Intell., vol. 36, pp. 1–34, Mar. 2022, doi: 10.1080/08839514.2022.2037254.
- K. AL-Dosari, N. Fetais, and M. Kucukvar, “Artificial Intelligence and Cyber Defense System for Banking Industry: A Qualitative Study of AI Applications and Challenges,” Cybern. Syst., vol. 55, no. 2, pp. 302–330, Feb. 2024, doi: 10.1080/01969722.2022.2112539.
- Yang, H., et al. (2024). A Flexible and Verifiable Keyword PIR Scheme for Cloud-Edge-Terminal Collaboration in AIoT. IEEE Internet of Things Journal.
- Kumar, S., et. al. (2024). Metaversal 6G: Deciphering Complex Requirements and Multivariate KPIs in High-Performance Computing. Procedia Computer Science, 238, 914-919.
Cite As
Neelapareddigari P. (2024) AI-Driven Cyber Defense, Insights2Techinfo, pp.1