By: Syed Raiyan Ali – syedraiyanali@gmail.com, Department of computer science and Engineering( Data Science ), Student of computer science and Engineering( Data Science ), Madanapalle Institute Of Technology and Science, 517325, Angallu , Andhra Pradesh.
ABSTRACT
Over past few years, the conventional approach to cybersecurity has become a hard nut to crack due to the rising complexity and occurrence of cyber threats over the years. However, with the advent of AI technologies, there is hope for improving defenses against changing dangers. This article talks about how AI can be used in cyber security for threat detection; it explains its process, advantages and possible challenges. By applying machine learning techniques like neural networks along with sophisticated algorithms, it can detect potential dangers immediately enabling risk evaluation and resolution. In terms of architecture data processing and ethics, this paper examines ways in which this technology can be advantageous over conventional ones in protecting information systems from attacks.
Keywords: Artificial Intelligence, Cyber security, Threat Detection, Machine Learning, Neural Network
INTRODUCTION
Since cyber threats are getting complicated and frequent, then cybersecurity is a very important matter. Traditional methods of securing information, although somewhat effective, cannot easily adapt to the rapidly changing threat landscape[1]. This has given room for artificial intelligence (AI) to redefine how we protect our systems from such occurrences. For instance, by employing machine learning techniques, neural networks, and sophisticated algorithms, AI-based threat detection offers robust and resilient cyber defense solutions.
THE GROWTH OF CYBER THREATS
The main reason of the cyber threats have transformed drastically from simple viruses, worms to complex ransomware or even advanced persistent threats (APTs)[2]. The conventional cybersecurity approaches mainly depend on signature based detection hence they are often incapable of identifying novel and sophisticated attacks. This is why it calls for AI powered methods which can adjust and react to emerging dangers at a moment’s notice.
AI-POWERED THREAT DETECTION MECHANISIMS
- Machine Learning and Neural Networks
AI-assisted hazard identification systems use Machine Learning (ML) algorithms along with neural networks to analyze vast amounts of data, identify trends and detect anomalies[3]. In these systems, historical data can be used for learning in order to differentiate normal patterns from unusual ones that could indicate possible danger.
- Anomaly Detection:
Anomaly detection held a very important position in the formation of AI based threat detection. Massive surveillance of network operations will alert artificial intelligence systems when someone behaves in an abnormal way[4]. This makes it possible for the detection of zero-day attacks along with new forms of malicious programs.
- Behavioral Analysis:
AI systems have been trained to analyze human behavior so they can better understand how users and devices typically behave in a network. Using this behavioral baseline, AI can uncover anomalies that might suggest intrusion or malice.
- Contextual Understanding:
Aspects-Gathering contextual information is vital in improving precision of threat recognition by AI systems. In order to differentiate good from poor actions done by certain entities, for instance, the time they act upon them, where they come from and what devices they are using.
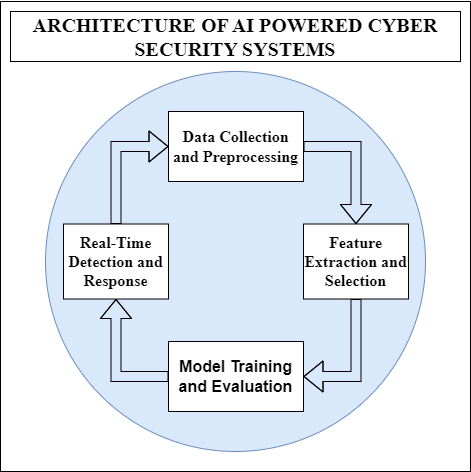
ARCHITECTURE OF AI POWERED CYBER SECURITY SYSTEMS
The architecture of AI driven Cyber Security system basically have several layers, each contributing to the overall threat detection and response capabilities:
- Data Collection and Preprocessing
The data that is collected is gathered from different sources such as network traffic systems, logs and user activities. After gathering this data it undergoes preprocessing so as to remove any noise or irrelevant information thus guaranteeing that only pertinent details would be utilized in analysis.
- Feature Extraction and Selection
From the data that has been processed, relevant characteristics are extracted in order to create a suitable dataset for machine learning. On top of that, feature selection techniques are usually employed in order to determine critical factors that help in accurate threat detection.
- Model Training and Evaluation
In order to make accurate predictions, machine learning models learn from labeled datasets which contain specific features that have been picked out from the underlying whole. To ensure that they can detect dangers effectively, these models undergo assessment of their precision, recall and accuracy.
- Real Time Detection and Response
Once the models are trained, they are deployed for real-time detection of threats. The AI system keeps an eye on the network and user activity, sending alerts and reacting automatically when it detects any possible threat.
The below shown diagram shows the Architecture of AI driven Cyber Security Systems
BENEFITS OF AI DRIVEN THREAT DETECTION
- Enhanced Detection Accuracy
When it comes to identifying dangers, systems powered by artificial intelligence have better precision than traditional means[5]. This is because they are always learning and adapting to novel threats, hence enabling them to detect and neutralize attacks with the help of great precision.
- Proactive Threat Prevention
Before an AI system fully comprehends an event associated with potential danger, its ability to upbringing that incident becomes the most precious tool for any organization interested in making provision against attacks. Hence, it focuses more on zero-day exploits and fresh challenges facing the cybersecurity industry.
- Scalability and Efficiency
AI-driven solutions for cybersecurity allow them to expand towards accommodating enormous quantities of information and traffic on the network thereby making them appropriate for organizations of every size[6]. It improves efficiency within operations as well as minimizes the amount of work done by internet security teams through automation as well as real time analysis.
CONCLUSION
The AI influenced threat detection is a major development in the domain of cybersecurity. The use of machine learning, neural networks and advanced algorithms enables AI to improve the capability of identifying, analyzing and alleviating online threats in real time. The advantages provided by AI powered systems such as increased detection accuracy, preemptive threat prevention and scalability make them an essential part of modern day cyber security. Nevertheless, there are several data privacy issues that must be settled for us to harness fully the power that lies within this technology when it comes to protecting our information systems against attacks. With increasing complexities in cyber crime today; thus would require constant updating even with respect to business models plus equipment so as not to lose any more money or information that can never be recovered again.
REFERENCES
- V. Tzavara and S. Vassiliadis, “Tracing the evolution of cyber resilience: a historical and conceptual review,” Int. J. Inf. Secur., vol. 23, no. 3, pp. 1695–1719, Jun. 2024, doi: 10.1007/s10207-023-00811-x.
- M. Alenezi, H. Alabdulrazzaq, A. Alshaher, and M. Alkharang, “Evolution of Malware Threats and Techniques: A Review,” Int. J. Commun. Netw. Inf. Secur., vol. 12, p. 326, Dec. 2020, doi: 10.17762/ijcnis.v12i3.4723.
- N. Taherifard, “AI-assisted Anomalous Event Detection for Connected Vehicles,” Université d’Ottawa / University of Ottawa, 2021. Accessed: Aug. 14, 2024. [Online]. Available: http://hdl.handle.net/10393/42273
- A. Bécue, I. Praça, and J. Gama, “Artificial intelligence, cyber-threats and Industry 4.0: challenges and opportunities,” Artif. Intell. Rev., vol. 54, no. 5, pp. 3849–3886, Jun. 2021, doi: 10.1007/s10462-020-09942-2.
- M. Rahaman, S. Chattopadhyay, A. Haque, S. N. Mandal, N. Anwar, and N. S. Adi, “Quantum Cryptography Enhances Business Communication Security,” vol. 01, no. 02, 2023.
- P. Pappachan, Sreerakuvandana, and M. Rahaman, “Conceptualising the Role of Intellectual Property and Ethical Behaviour in Artificial Intelligence,” in Handbook of Research on AI and ML for Intelligent Machines and Systems, IGI Global, 2024, pp. 1–26. doi: 10.4018/978-1-6684-9999-3.ch001.
- Sharma, A., Gupta, B. B., Singh, A. K., & Saraswat, V. K. (2023). A novel approach for detection of APT malware using multi-dimensional hybrid Bayesian belief network. International Journal of Information Security, 22(1), 119-135.
- Gupta, G. P., Tripathi, R., Gupta, B. B., & Chui, K. T. (Eds.). (2023). Big data analytics in fog-enabled IoT networks: Towards a privacy and security perspective. CRC Press.
Cite As
Ali S.R. (2024) AI-POWERED THREAT DETECTION IN CYBERSECURITY, Insights2Techinfo, pp.1