By: Rishitha Chokkappagari, Department of Computer Science &Engineering, student of Computer Science & Engineering, Madanapalle Institute of Technology & Science, Angallu (517325), Andhra Pradesh. chokkappagaririshitha@gmail.com
Abstract
Spam has always been a major problem for the individuals living in the digital world. Email spam is not only the spam that occurs, but spam also has different forms one among them is the Email spam detection. It is very crucial for maintaining privacy and security of emails or other social media platforms. To detect these spam messages, we need a spam detector. Alone spam detector is not enough to detect, it should be AI driven detector that automatically detects the spam messages, spam Emails, Links, websites. AI has changed many aspects of our lives in the digital world including how we detect, handle and filter the spam. AI has many developed tools that are increasingly popular to detect spams. The primary goal of this article is to provide a strong and comparative study on detecting spam using AI tools.
Keywords: AI tools, Spam Detection, Machine Learning
Introduction
In the digital world, spam is affecting individuals and organizations in a critical way. Spam encompasses unrequested and often poisonous content such as fraudulent emails, misleading advertisements and phishing attacks which lead to data breaches, financial loss, loss of trust on communication systems. This can be prevented by AI powered tools. The key approaches include supervised learning for training data, unsupervised learning for clustering (grouping of similar data) and anomaly detection, Deep learning methods such as neural networks for high-dimensional data processing. AI detects with high accuracy and high efficiency.
Here are some AI powered tools for spam detection: GPTZero, ContentDetector.AI, ZeroGPT, Spam Spy, Mail Meteor, Spam Arrest, Spam Titan, Mail Cleaner, Spam Bully. It is more important to detect using AI because many of the spam messages have viruses in them that can harm the system even if the messages are just opened once[1].
1. AI methods for Spam Detection
A. Machine Learning-Based Approaches
Supervised Learning Methods (SLM):
The models used for training in SLM are NB, SVM, DTs, RFs, and KNN by utilizing the labelled data. Possible methods of text classification that have been identified include decision trees, rule-based method and the neural networks and researchers have concluded that the later has high accuracy in identifying between SMS spam and email spam.
Unsupervised Learning Methods (ULM):
Clustering Techniques: A structural type of clustering algorithms suitable when a considerable number of labelled data is not available is ULMs like K-Means and Hierarchical Clustering. It clusters similar spam messages and recognizes different patterns and abnormalities in the messages which helps in the discovery of new types of spam.
Advanced Methods: Such approaches like the Long Short-Term Memory auto encoding helps in distinguishing between spam and genuine message, with lots of precision[2].
B. Techniques of deep learning
DL methods such as CNNs, RNNs, and LSTM is very efficient in detecting spam. They can deal with intricate data patterns and are employed in areas such as devices for the Internet of Things to the text categorisation. It outperforms classical methods and decreases the misdiagnosis price[3].
C. Image-Based Spam Detection
The spam detection problem in images is solved by DL models such as CNNs with desirable accuracy. For instance, the Image Spam Hunter Dataset recorded a success rate of more than ninety-nine percent and similar results have been realised in other practices, as evidenced by other research, to affirm the efficiency of DL in the processing of image datasets that are new[4].
D. Text Based Spam detection using NLP
Text content data mining is significant in the detection of spam, and this can only be achieved through the application of NLP techniques. The discussed techniques include, sentiments, content factors, and rating standard deviations for the identification of spam reviews. Furthermore, there are adversarial attacks in NLP applications and hybrid methods that increase the efficiency and stability of applications and have a high success rate in spam detection[5]. Here fig.1 depicts the detection of spam emails and separated the spam mails and authorized mails.
2. Contemporary Social Engineering Attacks
As the digital landscape evolves, so do social engineering tactics that exploit human psychology. These attacks have become more sophisticated, posing significant challenges to cybersecurity defences.
A. Evolution and Adaptation
Social engineering began with simple deceptions like phone-based pretexting or basic phishing emails. As technology advanced, so did these methods, evolving into complex schemes such as spear phishing, which targets individuals with tailored messages using personal data. The rise of mobile technology introduced smishing, where fraudulent text messages seek sensitive information. Additionally, high-profile targets like executives are increasingly targeted in “whaling” attacks, which aim for significant data or financial gains. This evolution reflects attackers’ adaptation to technological advancements, highlighting the need for proactive cybersecurity measures.
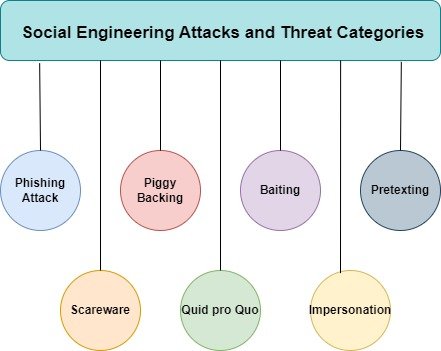
B. Threat Categories and Methods
Phishing: Phishing has evolved from broad, generic attacks to more targeted forms like spear phishing, which focuses on specific individuals using detailed information to appear legitimate. Whaling targets high-ranking officials to access critical data or financial resources[6].
Impersonation Techniques and Pretexting: Impersonation involves attackers pretending to be trusted individuals or entities, such as coworkers or banks. Pretexting creates a plausible scenario to trick victims into providing information, like posing as tech support needing details to “resolve an issue.”
New-Age Vectors: Exploits Through social media and Mobile Platforms, social media and mobile apps have become new vectors for attacks. Platforms like Facebook and LinkedIn are used to gather information for crafting sophisticated attacks. Malicious mobile apps can access sensitive data, record conversations, or track movements[7]. Fig.2 shows the types of social engineering attacks and threat categories.
3. Role of AI across Detection, Prevention and Response:
AI is becoming the main trend in cybersecurity as it improves the abilities in detection, prevention, and response.
A. Detection
AI enhances threat detection beyond the systems that are based on signature and pattern identification. Cognitive models perform mathematical analysis on a massive number of records, finding slight deviations or trends, including the emergence of new risks. This predictiveness leads to use of precautionary measures based on past and current data as opposed to just being on the receiving end of an attack.
B. Prevention
AI improves the pre-emption level by constantly upgrading the shield strategies according to the identified threats. It can modify the firewall rules and filters in real time, and it can modify and set up ‘mock’ attacks to look for and remediate potential threats that may occur and be used. This makes passes to be minimized or eradicated thus reducing the risk of successful attacks[8].
C. Response
In the event of a breach AI enhances the speed of determining the damage caused by the intrusion, the source and the AI can also recommend or carry out measures to contain the intrusion. Forensics applications developed with the help of Artificial Intelligence allows for delineating the specifics of the attack and its delivery, hence contributing to the enhancement of strategies that can be used for protection against future attacks[7].
Conclusion:
Implementing spam detection with the help of AI tools has become possible due to the usage of such methods as machine and deep learning and natural language processing. These tools are defined to have best performances in spam handling, new threat detection, and improvement of identification within text and image-based data. Thus, through AI’s constant learning and adaptation, internet spam and security threats are effectively filtered for the safety of digital contents and individual’s private information. Hence, as new and deeper threats appear in cyberspace, AI’s application will only grow, providing reliable and versatile protection against spam.
References:
- G. Zhang, S. Davoodi, S. S. Band, H. Ghorbani, A. Mosavi, and M. Moslehpour, “A robust approach to pore pressure prediction applying petrophysical log data aided by machine learning techniques,” Energy Rep., vol. 8, pp. 2233–2247, Nov. 2022, doi: 10.1016/j.egyr.2022.01.012.
- M. Rahaman, C.-Y. Lin, P. Pappachan, B. B. Gupta, and C.-H. Hsu, “Privacy-Centric AI and IoT Solutions for Smart Rural Farm Monitoring and Control,” Sensors, vol. 24, no. 13, Art. no. 13, Jan. 2024, doi: 10.3390/s24134157.
- F. Hossain, M. N. Uddin, and R. K. Halder, “Analysis of Optimized Machine Learning and Deep Learning Techniques for Spam Detection,” in 2021 IEEE International IOT, Electronics and Mechatronics Conference (IEMTRONICS), Apr. 2021, pp. 1–7. doi: 10.1109/IEMTRONICS52119.2021.9422508.
- H. B. Aradhye, G. K. Myers, and J. A. Herson, “Image analysis for efficient categorization of image-based spam e-mail,” in Eighth International Conference on Document Analysis and Recognition (ICDAR’05), Aug. 2005, pp. 914-918 Vol. 2. doi: 10.1109/ICDAR.2005.135.
- A. H. Odeh and M. A. Hattab, “AI Methods Used for Spam Detection in Social Systems – An Overview,” in 2023 Tenth International Conference on Social Networks Analysis, Management and Security (SNAMS), Nov. 2023, pp. 1–8. doi: 10.1109/SNAMS60348.2023.10375397.
- L. Burita, P. Matoulek, K. Halouzka, P. Kozak, and Department of Informatics and Cyber Operations, University of Defence, 65 Kounicova Street, 66210 Brno, Czech Republic, “Analysis of phishing emails,” AIMS Electron. Electr. Eng., vol. 5, no. 1, pp. 93–116, 2021, doi: 10.3934/electreng.2021006.
- H. N. Fakhouri, B. Alhadidi, K. Omar, S. N. Makhadmeh, F. Hamad, and N. Z. Halalsheh, “AI-Driven Solutions for Social Engineering Attacks: Detection, Prevention, and Response,” in 2024 2nd International Conference on Cyber Resilience (ICCR), Feb. 2024, pp. 1–8. doi: 10.1109/ICCR61006.2024.10533010
- Rahaman M (2024) Foundations of Phishing Detection Using Deep Learning: A Review of Current Techniques Available: https://insights2techinfo.com/foundations-of-phishing-detection-using-deep-learning-a-review-of-current-techniques/
- Sahoo, S. R., Gupta, B. B., Choi, C., Hsu, C. H., & Chui, K. T. (2020). Behavioral analysis to detect social spammer in online social networks (OSNs). In Computational Data and Social Networks: 9th International Conference, CSoNet 2020, Dallas, TX, USA, December 11–13, 2020, Proceedings 9 (pp. 321-332). Springer International Publishing.
- Sahoo, S. R., Gupta, B. B., Peraković, D., Peñalvo, F. J. G., & Cvitić, I. (2022). Spammer detection approaches in online social network (OSNs): a survey. In Sustainable Management of Manufacturing Systems in Industry 4.0 (pp. 159-180). Cham: Springer International Publishing.
Cite As
Chokkappagari R. (2024) AI-Powered Tools for Spam Detection, Insights2Techinfo, pp.1