By: Farhin Tabassum1 and Mosiur Rahaman2
1Indian Institute of Technology, Kharagpur, India
2International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan
Email: tabassumfarhin390@kgpian.iitkgp.ac.in, mosiurahaman@gmail.com
Abstract
The article presents an enhanced Multi-Factor Authentication (MFA) and Key Agreement protocol for the Industrial Internet of Things (IIoT). It addresses the security challenges in IIoT due to increased connectivity and automation. The protocol combines various authentication methods and a lightweight, resilient key agreement process. It introduces dynamic authentication adapting to risk levels and uses advanced cryptographic techniques for secure key exchanges. The protocol balances security with efficiency, is scalable, and adaptable, significantly enhancing IIoT security against sophisticated cyber threats.
Introduction
In recent years, the Industrial Internet of Things (IIoT) has been transforming the industrial landscape, allowing for unprecedented connectivity and automation. However, this growing interconnectivity also introduces significant security challenges, particularly in the area of authentication and key agreement [1]. Addressing these concerns, researchers have developed an enhanced Multi-Factor Authentication (MFA) and Key Agreement protocol specifically designed for IIoT environments.
The Need for Enhanced Security in IIoT
The IIoT connects a vast array of industrial devices, from sensors and actuators to control systems, over the internet. While this connectivity enables remote monitoring, predictive maintenance, and improved efficiency, it also exposes industrial systems to cyber threats. Traditional security measures often fall short in protecting against sophisticated attacks, making enhanced security protocols essential [2].
Multi-Factor Authentication in IIoT
MFA, a security system that requires more than one method of authentication from independent categories of credentials, is crucial in IIoT. It ensures that the process of verifying the identity of a user or device is robust and resistant to unauthorized access. The enhanced MFA protocol in IIoT combines something the user knows (like a password), something the user has (like a security token), and something the user is (like a fingerprint) [3].
Key Agreement Protocols in IIoT
Key agreement protocols are essential for secure communication in IIoT. They enable devices to agree on a secret key that can be used for encrypting and decrypting messages [4]. The enhanced protocol proposed for IIoT is designed to be lightweight, considering the limited computational resources of many industrial devices, while also being resilient against various cyber threats including man-in-the-middle attacks [5].
The Enhanced MFA and Key Agreement Protocol
This new protocol integrates MFA with a robust key agreement process. Firstly, it involves a dynamic authentication method that adapts based on the perceived risk level of the communication. Secondly, the key agreement component utilizes advanced cryptographic techniques to ensure that the keys exchanged between devices remain confidential and are not compromised [6].
The enhanced protocol offers several benefits:
Increased Security: By integrating MFA, the protocol significantly reduces the risk of unauthorized access.
Scalability: It is designed to be scalable, accommodating the growing number of devices in IIoT networks.
Flexibility: The protocol can adapt to different levels of risk, providing appropriate security measures as needed.
Efficiency: Despite its robust security features, the protocol is efficient and suitable for devices with limited processing capabilities.
The “Use-Case Diagram for IIoT Security Challenges,” we can define functions that represent the interactions between actors and use cases. Let’s consider each use case as a function of the actors involved.
: This function represents the interaction of the User with the basic MFA process.
This function denotes the User engaging with biometric authentication methods.
- Key Agreement Protocol
This function illustrates the Network Administrator implementing the Key Agreement Protocol within the System .
- Dynamic Risk-Adaptive Security :
This function shows the Network Administrator applying dynamic, risk-adaptive security measures in the System.
- Security with Efficiency :
This function represents the Maintenance Personnel (M) and Security Auditor (S) working to balance security and efficiency in the System (Σ).
- Scalability and Flexibility :
This function indicates the Security Auditor (S) enhancing the scalability and flexibility of the System (Σ).
In this mathematical model, each function encapsulates a specific use case, with the actors as input variables. The interactions between the actors and the use cases are thus formalized, providing a clear and quantifiable representation of the roles and responsibilities within the IIoT security system in Figure 1.
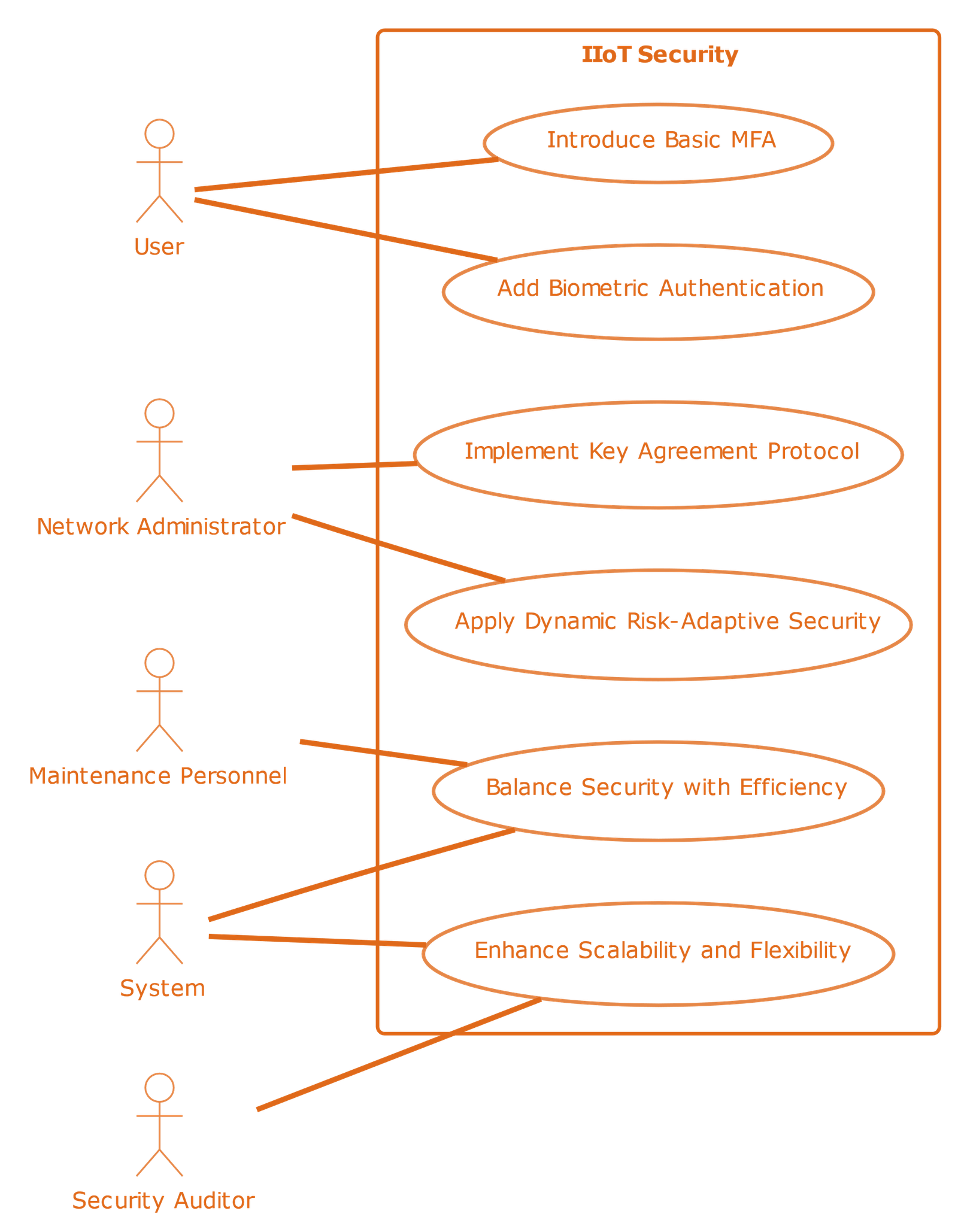
The “Use-Case Diagram for IIoT Security Challenges” in Figure 1 serves as a comprehensive visual representation of the various roles and functionalities within the Industrial Internet of Things (IIoT) aimed at addressing its unique security challenges. It features a range of actors, each with a distinct role in the IIoT ecosystem: the User, who directly utilizes the IIoT system; the Network Administrator, tasked with managing the network aspects; Maintenance Personnel, responsible for the upkeep of devices and infrastructure; the Security Auditor, specializing in security assessment; and the System itself, symbolizing the automated and interconnected components of IIoT. These actors are linked to specific use cases that address different facets of IIoT security. These include introducing basic Multi-Factor Authentication (MFA) to enhance security, adding Biometric Authentication for more robust access control, implementing a Key Agreement Protocol for secure communication, applying Dynamic Risk-Adaptive Security measures, balancing high security with system efficiency, and enhancing the system’s scalability and flexibility to accommodate a growing network of devices.
Evolution of Multi Factor Authentication methods in IIoT.
Multi-factor authentication (MFA) has been pivotal in enhancing security measures, particularly in the realm of the Industrial Internet of Things (IIoT). The evolution of MFA methods has been driven by the need to combat the escalating threats and vulnerabilities in IIoT systems. Initially, MFA schemes integrated two or more authentication factors [7]. These factors typically encompassed elements such as knowledge, biometrics, possession, one-time passwords (OTP), timestamps, challenges, and passwords [8][9]. The utilization of multiple authentication factors has been acknowledged as a more robust approach to identity verification [10].
A notable advancement in MFA for IIoT security is the introduction of two-factor device DNA-based fuzzy vaults. This method involves creating a specific two-factor device DNA by amalgamating intrinsic factors of IIoT devices with their surrounding environments. The objective is to establish a vault set to obscure secret keys based on the two-factor device DNA, thereby bolstering security in IIoT environments [11].
Furthermore, the integration of MFA protocols in IIoT applications has been underscored as a critical element in ensuring secure authentication and key agreement. These protocols have been crafted to offer rapid, privacy-preserving, and zero-round-trip-time authentication, integrating components such as physically unclonable functions (PUFs), proximity estimation, and secret key generation[12].
Moreover, the evolution of MFA in IIoT has witnessed the implementation of blockchain-based authentication mechanisms to surmount the constraints of single-factor authentication. Blockchain technology has been harnessed to heighten data security and privacy in IIoT systems, guaranteeing secure authentication processes .
In recent years, there has been a transition towards more sophisticated MFA frameworks, such as the multi-factor multi-level and interaction-based (M2I) authentication framework for IoT applications. This framework aims to streamline multi-level authentication by integrating various factors and interactions to fortify security measures in IoT environments.
Conclusion
The introduction of the enhanced MFA and Key Agreement protocol marks a significant step forward in securing IIoT environments. By addressing the unique challenges posed by the IIoT, this protocol ensures that industrial systems can reap the benefits of connectivity without compromising on security. As the IIoT continues to evolve, such innovative security solutions will be crucial in safeguarding the industrial sector against an ever-changing landscape of cyber threats.
Reference:
- S. Munirathinam, “Chapter Six – Industry 4.0: Industrial Internet of Things (IIOT),” in Advances in Computers, vol. 117, 1 vols., P. Raj and P. Evangeline, Eds., in The Digital Twin Paradigm for Smarter Systems and Environments: The Industry Use Cases, vol. 117. , Elsevier, 2020, pp. 129–164. doi: 10.1016/bs.adcom.2019.10.010.
- D. sharma, A. kumar, N. Tyagi, S. S. Chavan, and S. M. P. Gangadharan, “Towards intelligent industrial systems: A comprehensive survey of sensor fusion techniques in IIoT,” Measurement: Sensors, vol. 32, p. 100944, Apr. 2024, doi: 10.1016/j.measen.2023.100944.
- M. Rahaman, C.-Y. Lin, and M. Moslehpour, “SAPD: Secure Authentication Protocol Development for Smart Healthcare Management Using IoT,” in 2023 IEEE 12th Global Conference on Consumer Electronics (GCCE), Oct. 2023, pp. 1014–1018. doi: 10.1109/GCCE59613.2023.10315475.
- Z. Hu, J. Li, and C. Wilson, “Resilient Intermediary-Based Key Exchange Protocol for IoT,” ACM Trans. Internet Things, vol. 5, no. 1, p. 7:1-7:31, Jan. 2024, doi: 10.1145/3632408.
- S. Cherbal and R. Benchetioui, “ScPUAK: Smart card-based secure Protocol for remote User Authentication and Key agreement,” Computers and Electrical Engineering, vol. 109, p. 108759, Aug. 2023, doi: 10.1016/j.compeleceng.2023.108759.
- T. Suleski, M. Ahmed, W. Yang, and E. Wang, “A review of multi-factor authentication in the Internet of Healthcare Things,” Digit Health, vol. 9, p. 20552076231177144, May 2023, doi: 10.1177/20552076231177144.
- Alizai, Z., Tahir, H., Murtaza, M., Tahir, S., & McDonald-Maier, K. (2019). Key-based cookie-less session management framework for application layer security. Ieee Access, 7, 128544-128554. https://doi.org/10.1109/access.2019.2940331
- Khan, A., Javed, Y., Saqib, R., Ahmad, Z., Abdullah, J., Zen, K., … & Khan, N. (2022). Lightweight multifactor authentication scheme for nextgen cellular networks. Ieee Access, 10, 31273-31288. https://doi.org/10.1109/access.2022.3159686
- Olanrewaju, R., Khan, B., Morshidi, M., Anwar, F., & Kiah, M. (2021). A frictionless and secure user authentication in web-based premium applications. Ieee Access, 9, 129240-129255. https://doi.org/10.1109/access.2021.3110310
- Hong, E., Lee, S., Oh, M., & Seo, S. (2021). Two-factor device dna-based fuzzy vault for industrial iot device security. Ieee Access, 9, 99009-99023. https://doi.org/10.1109/access.2021.3095348
- Gupta, B. B., & Prajapati, V. (2020). An Efficient SIP Authentication Scheme for Multiserver Infrastructure. In Futuristic Trends in Networks and Computing Technologies: Second International Conference, FTNCT 2019, Chandigarh, India, November 22–23, 2019, Revised Selected Papers 2 (pp. 64-74). Springer Singapore.
- Gupta, B. B., & Prajapati, V. (2019, July). Secure and efficient session initiation protocol authentication scheme for VoIP communications. In 2019 International Conference on Communication and Electronics Systems (ICCES) (pp. 866-871). IEEE.
Cite As
Tabassum F, Rahaman M (2024) An Enhanced Multi-Factor Authentication and Key Agreement Protocol in Industrial Internet of Things, Insights2Techinfo, pp.1