By: KV Sai Mounish, Department of computer science and technology, Student of computer science and technology, Madanapalle Institute Of Technology and Science, 517325, Angallu, Andhra Pradesh.
ABSTRACT –
With the aid of Online Voting, there is hope towards improvement of issues that may affect the process of elections through complication hence; the improved voters turnout. Nevertheless, the authenticity of such systems is questionable as the records belonging to the voters and their registration, votes as well as their card details can be faked, edited or vulnerable to hacking among others electoral issues. As for the specificity of successful trends in the given problem, the issue of authenticity is also addressed in this article as a powerful successful trend in relation to solving the problem in connection with the sphere of online voting. Another highly secure form of confirming the voter’s details is the biometric authentication because it employs such parameters, as a finger print, facial recognition system, Iris scan, and so on, which qualify as the physiological and behavioral attributes. In addition to this, the article takes the above analysis a notch higher in describing the technicality of biometric security and assessing biometric security concerning normal risks and the defects such as the violation of privacy and data as well as its vulnerability to abuse. Besides, it overemphasizes the usage of examples based on the application of the biometric system to the voting process and depicts the measures to avoid frauds in the sphere of online voting. Last of all, this Endeavour seeks to establish that perhaps the biometric authentication could be the solution to the current poor and doubtful online voting systems to boost the degrees of democracy.
KEYWORDS –
Authenticity, Specificity, Fingerprint, Biometric Security, Vulnerability, Privacy, Fraud.
INTRODUCTION –
While the use of digital technology in almost all spheres of human activity has become evident over the years, online voting remains one of the contested yet promising ways to develop the democracy. There are several advantages that can be derived from engaging in online voting such as; high voter turn up, ease in the process, and low expenses as compared to other methods of paper based voting. Nevertheless, the transfer to on line voting systems brings a lot of security issues which must be solved in order to maintain the offering of confident and authoritative elections. Another crucial issue of major concern when it comes to the use of online voting is how the identity of the voter can best be accredited. The methods of simple texts, PINs, or passwords are quite vulnerable to almost all the cyber threats; it includes phishing, hacking, and stolen passwords[1]. Such weaknesses make it easy for the election processes to be fixed through impersonation of voters, multiple voting, among other vices that distort the true outcome of elections.
In order to overcome these challenges, there is a solution which has been commonly adopted and it is known as Biometric authentication. Compared to more traditional access control mechanisms, biometrics depends on one’s physical or behavioral attributes, among them fingerprints, facial or iris recognition patterns, which are extremely hard to imitate or forge. When the biometric technology is incorporated into the online voting systems, it becomes possible to develop a more secure method of voter identification hence improving on the security that is accorded to the general elections. In this article the authors raise awareness on the application of biometric authentication in the protection of online voting systems. This looks into the technological aspects of biometric security, its efficiency in handling the known threats, and the ethical and privacy issues revolving around biometric data. Thus, using actual cases and key recommendations, the article is designed to shed light on how biometric authentication can help to establish reliable, open, and democratic electronic voting systems[2].
Feasibility of Biometric Authentication in Voting Systems
To ensure that on-line voting system is secure other than the traditional method of voting some of the technique that has being adopted to solve the security issues include the biometric authentication. The innovation of spots such as finger prints, face identifies as well as iris recognition played a big role in enhancing the peace and security of the online voting system. Below, we explore these aspects in detail: In the following sections, the above aspects will be examined as follows:
1. Can Biometrics be used for Authentication in Online Voting
Technological Maturity:
This paper brings out the current status of the biometric technologies and concludes that it is safe to embark on the large scale use of the technologies[3]. Seeing that the mobile digital devices of today are generally provided with the inbuilt biometric devices, and that there are prospects for creating the cloud-based biometric devices, one can include them in the online voting systems.
Infrastructure Requirements: These are such things as secure servers for preserve the information, encrypted databases and Interfaces that can be half users to use for the voting . It is therefore expected that regions with more developed IT systems will be most likely to apply biometric elements in the administration of their votes. Moreover, cooperation with the biometric service providers and the IT security specialists is very crucial since, in a large-scale and highly loaded process, such as the election, certain issues can appear that require immediate solution.
Accessibility Considerations:
One is to make sure that biometric systems are affordable to all the concerned voters and that the disabled or else those who do not have appropriate apparatus are not left out[4]. This must be done in a way that defines other vote authentication processes or help schemes that would sufficiently reach to the voters while at the same time satisfying the issue of security.
2. Security Enhancement of Biometric Authentication
Enhanced Identity Verification:
Biometric authentication gives a lot of confidence that the person casting the vote is the right voter. Biometric is unique and hard to imitate; therefore, instances of voter impersonation and that are associated with fraud are eliminated. This is quite unparallel to other security solutions such as the password or PIN which can be easily hacked.
Protection against Multiple Voting:
Biometric systems can also be integrated to suppress voting by a single person so that a voter is only allowed to vote once. This is especially the case when undertaking online voting because it is easier to vote more than once in a single voting session when adequate measures have not been taken.
Mitigation of Cyber Threats:
It means, no system can completely protect data from cyber threats, but the integration of biometric authentication is more difficult to penetrate. For example, even if an attacker compromises the credential files of a voter, then he will still require the voters biometric information to fully verify the voter. Moreover, biometric data, if encrypted and saved, is relatively more secure as compared to credential attack such as phishing or brute force.
Auditability and Transparency:
Biometric authentication useful in increasing the auditability of the voting process. The direct link between biometric record and each vote is that every vote can be accountable for and therefore no case of rigging can be done in the dark.
3. Challenges and Considerations
Privacy Concerns:
This has been seen one of the major drawbacks that come with the use of biometric authentication which is privacy infringement. Biometric data is very sensitive, this means that in the wrong hand or through theft this data can produce disastrous results.
False Rejection and Acceptance Rates: False Rejection and Acceptance Rates: Despite their efficiency, biometric systems are bound to reject some of the legal voters or let in some illegitimate voters into the voting room.
Regulatory and Legal Compliance:
The implementation of biometric data is prohibited by law in many parts of the world due to the high grade of sensitive information[5]. Adhering to these regulations for instance, the need to gain voters’ consent and having commendable and easily understood data protection policy is crucial for proper and lawful use of biometric systems in the case of elections.
The process of biometric authentication in Online voting systems is shown in F igure 1.
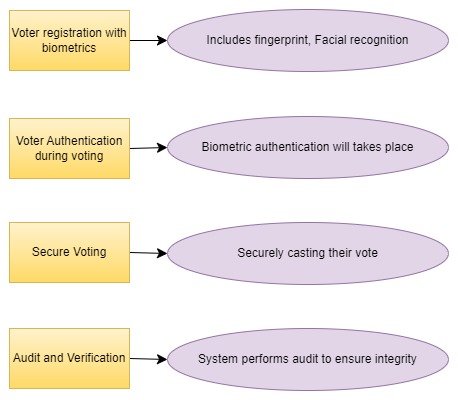
CONCLUSION –
Biometrics authentication can therefore be considered as a rather potential solution stream to the security threats still in existence on the online voting system. Identification methods using physiological and behavioral characteristics of the voters are better alternatives for voters’ identification and therefore reduce chances of fraudulent activities, unlawful access and multiple voting. Application of some of these technologies makes the elections more secure, accurate and popularizes the related democracy practices. Thus, one can state that it can be discussed that despite the technological advancement and theoretical underpinnings, there are some issues in the sphere of biometric authentication in the sphere of online voting, namely, that the issues related to personal data protection, infrastructural possibility of applying the biometric systems in the sphere of voting, and legislation necessity. Specifically, the protection of biometrical data as well as its use only within the framework of the elections is one of the pillars that would ensure the privacy of the electorate and effectiveness of the provided system. That is why biometric authentication is considered as the perspective approach for the online voting system, given the fact that the digital democracy is becoming more universal all across the world. Based on the ethical, legal, and technological analysis of the corresponding issues, the policymakers and election officials are capable of rallying the advantages of using biometric authentication for sustaining and enhancing the electoral integrity and the voters’ experience.
REFERENCES –
- Ö. Aslan, S. S. Aktuğ, M. Ozkan-Okay, A. A. Yilmaz, and E. Akin, “A Comprehensive Review of Cyber Security Vulnerabilities, Threats, Attacks, and Solutions,” Electronics, vol. 12, no. 6, Art. no. 6, Jan. 2023, doi: 10.3390/electronics12061333.
- A. H. Mohsin et al., “Finger Vein Biometrics: Taxonomy Analysis, Open Challenges, Future Directions, and Recommended Solution for Decentralised Network Architectures,” IEEE Access, vol. 8, pp. 9821–9845, 2020, doi: 10.1109/ACCESS.2020.2964788.
- A. E. Omolara et al., “The internet of things security: A survey encompassing unexplored areas and new insights,” Comput. Secur., vol. 112, p. 102494, Jan. 2022, doi: 10.1016/j.cose.2021.102494.
- K. T. Putra, A. Z. Arrayyan, R. Z. Syahputra, Y. A. Pamungkas, and M. Rahaman, “Design a Two-Axis Sensorless Solar Tracker Based on Real Time Clock Using MicroPython,” Emerg. Inf. Sci. Technol., vol. 4, no. 1, Art. no. 1, May 2023, doi: 10.18196/eist.v4i1.18697.
- S. Manikandan, M. Rahaman, and Y.-L. Song, “Active Authentication Protocol for IoV Environment with Distributed Servers,” Comput. Mater. Contin., vol. 73, no. 3, pp. 5789–5808, 2022, doi: 10.32604/cmc.2022.031490.
- Abd El-Latif, A. A., Hammad, M. A., Maleh, Y., Gupta, B. B., & Mazurczyk, W. (Eds.). (2023). Artificial Intelligence for Biometrics and Cybersecurity: Technology and Applications. IET.
- Peng, J., Yang, B., Gupta, B. B., & Abd El-Latif, A. A. (2021). A biometric cryptosystem scheme based on random projection and neural network. Soft Computing, 25, 7657-7670.
Cite As
Mounish K.V.S. (2024) Biometric Authentication in Voting Systems, Insights2Techinfo, pp.1