By: KV Sai Mounish, Department of computer science and technology, Student of computer science and technology, Madanapalle Institute Of Technology and Science, 517325, Angallu, Andhra Pradesh.
ABSTRACT–
Over decade mobiles has became great convenient tool for the users to access their data and take on any services such as online shopping, Net banking, movies, web series, etc. At the same time the importance of security has become crucial in maintaining their private data. Now-a-days unauthorized access to user private data is common which means our data is in stake of loss like private information including credit card details, passwords, etc. This is the phase where biometric security contributes themselves to protect user’s sensitive information without permitting any access to others. This paper will explore different authentication methods involved in mobile phones. This security in mobile phones will be including passwords, patterns, facial recognition which uses biometric security. It will categorize individual based on iris, fingerprint, etc. For example you know multi factor authentication to create more secure lock. And also we explore existing authentication methods and also reveal their vulnerabilities. Here the user characteristics and biometric will be extracted from input knowledge and this article will explore different authentication metrics.
KEYWORDS –
Unauthorized, Biometric security, Authentication, Facial recognition, Fingerprint, Vulnerabilities.
INTRODUCTION –
It is true that in an old survey researchers told that the number of mobile phone users will reach 5 billion in 2021 which has crossed now, it resulted as benefit for mobile phone manufacturers and industry. But simultaneously it has increased user concern for security. And now-a-days most of the mobile applications are having access to user private information such as location, user media which will be asked to allow or not in starting of app and that’s why the apps are using different types of authentication techniques to verify user identity and avoid manipulation of data.
But now-a-days leakage of data such as credit card details, security numbers present in phone is common. So there is a need to address these problems biometric security comes into picture to safeguard data to [1].
So finally this article will be explaining about various authentication methods in mobile phones focusing on security of user’s private data by integration of biometric security and also there is another security mechanism called two factor authentication which combine different security measures.
And also identify the vulnerabilities to weakness existing in current authentication methods. But the main focus of this article is to show the importance of biometric security aligned in mobile phones and how effectively it reduces unauthorized access.
TRADITIONAL AUTHENTICATION METHODS
Traditional authentication protocols plays a crucial role in mobile security over many years in this the user has to give some input secret information to their device and has to remember that secret information whenever they will try to get access to their device[2]. Some commonly used methods are as follows:
Passwords are the secret words which are widely used for authentication process that the user has to enter in order to gain access to device. To create effective password there are certain rules and regulations such as there should be special characters, numbers, different combination[3].
It is very easy to implement and set to use and also can be changed easily if compromised.
However it will be in user’s hands to forgot or change the password that has been set and it is less effective to cyber attacks like phishing, brute force, data manipulation. And if user create weak passwords it will be easy to crack.
Patterns based authentication will be involving drawing a pattern to unlock device like includes any shape, it is some what easy to use when compared to password which is especially on touch screen devices and it is easy to remember compared to others.
But the visible print on touch screen will be used to crack that pattern and anybody can easily peek and crack the patterns.
PIN stands for Personal Identification Numbers which is sequence of numbers usually 4 to 6 digits long and is widely used in laptops, PC[4].
It is also used in banking application and will be quick to enter and requires two factor authentication to crack security but it also includes limitation such as limit to numerical digits and can be easily guessed if it is not that much strong enough, will also supports shoulder surfing which is attackers watching user entering pin.
So it is important to understand that even traditional approaches comes with vulnerabilities and rely on user reliability, to avoid these biometric authentication and multi factor authentication has to be used. The main process involved in authentication process is illustrated in Figure 1.
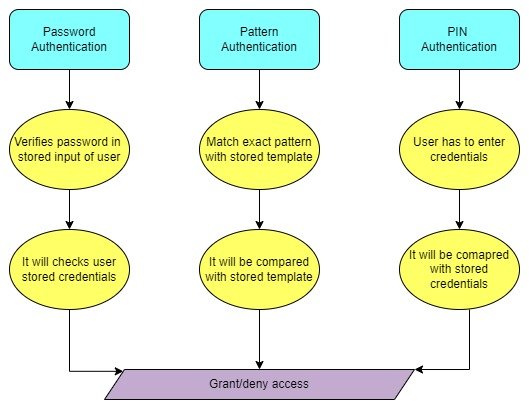
AUTHENTICATION METRICS
These are the measurements which are used to measure how much accurate the model is and how effectively it is working and also simultaneous assess performance to expected security standards.
Accuracy it means how correctly the system rejects or verifies users includes metrics like true positive rate which means percentage of legit users correctly verified and true negative rate which means percentage of legit users rejected.
False positive rate means percentage of illegal users incorrectly accepted by system and false negative rate means percentage of illegal users incorrectly rejected by systems.
Usability will be defining how user friendly and convenient the authentication process like ease of use, speed response time, satisfaction of users.
Scalability it will measure how system can handle increased number of users and requests to provide resources which is crucial.
Interoperability will be explaining how well the authentication methods will be integrated to different systems including ability to work along different environment and whether it will be aligned to industry standards[5].
POSSIBLE TRENDS IN FUTURE OF AUTHENTICATION
There will be continuous evolving of security in mobile and these might be future trends in mobile which will lead to more secure, user friendly approach.
Enhanced Biometric Authentication it will be expected to become more prevalent and advance in biometric technology[6].
3D Facial Recognition will improve sensing technology by using 3D models reducing risk of manipulating photos or media.
Emotion Recognition it will detect and analyze expression facial emotions by adding additional layer of authentication.
Iris And Retina Scanning it will improve camera technology and will increase accuracy and reliability of iris and retina scans.
Block Chain Technology will be providing access to see if anything is changed or removed for digital identities and the users will be having more control to verify identity information. And also transparency will be reducing frauds and improve trust.
CONCLUSION-
The concept of mobile authentication is changing rapidly with huge and increased demand for security due to leakage of private data even password, pin, pattern didn’t provide adequate amount of security so it became difficult to manage. In this case biometric authentication techniques including facial recognition, voice recognition are more secured and act as alternative. It will make intruders difficult to attack.
With integration of advanced technology it will be easier to increase security so we explored future trends in article like by incorporate 3D facial recognition and emotion recognition and by improving accuracy through iris and retina scanning and should be adopted widely. By enabling multi factor authentication combining different security protocols and by integrating block chain technology we will be getting more control over digital identities.
So overall it is necessary to implement robust and user understandable authentication methods and by welcoming creative technology and improve security measures and eventually can safeguard sensitive information. Finally we say that authentication plays a crucial role in security of mobile phones.
REFERENCES –
- C. Wang, Y. Wang, Y. Chen, H. Liu, and J. Liu, “User authentication on mobile devices: Approaches, threats and trends,” Comput. Netw., vol. 170, p. 107118, Apr. 2020, doi: 10.1016/j.comnet.2020.107118.
- M. Alizadeh, S. Abolfazli, M. Zamani, S. Baharun, and K. Sakurai, “Authentication in mobile cloud computing: A survey,” J. Netw. Comput. Appl., vol. 61, pp. 59–80, Feb. 2016, doi: 10.1016/j.jnca.2015.10.005.
- R. Shay et al., “Encountering Stronger Password Requirements: User Attitudes and Behaviors”.
- D. T. Akomolafe and B. O. Afeni, “Using Database Management System to Generate, Manage and Secure Personal Identification Numbers (PIN),” J. Softw. Eng. Appl., vol. 07, no. 05, Art. no. 05, May 2014, doi: 10.4236/jsea.2014.75043.
- S. Manikandan, M. Rahaman, and Y.-L. Song, “Active Authentication Protocol for IoV Environment with Distributed Servers,” Comput. Mater. Contin., vol. 73, no. 3, pp. 5789–5808, 2022, doi: 10.32604/cmc.2022.031490.
- L. Triyono, – Prayitno, M. Rahaman, – Sukamto, and A. Yobioktabera, “Smartphone-based Indoor Navigation for Guidance in Finding Location Buildings Using Measured WiFi-RSSI,” JOIV Int. J. Inform. Vis., vol. 6, no. 4, pp. 829–834, Dec. 2022, doi: 10.30630/joiv.6.4.1528.
- Gupta, B. B., & Panigrahi, P. K. (2022). Analysis of the Role of Global Information Management in Advanced Decision Support Systems (DSS) for Sustainable Development. Journal of Global Information Management (JGIM), 31(2), 1-13.
- Gupta, B. B., & Narayan, S. (2021). A key-based mutual authentication framework for mobile contactless payment system using authentication server. Journal of Organizational and End User Computing (JOEUC), 33(2), 1-16.
Cite As
Mounish K.V.S (2024) Biometric Security incorporated in Mobile Devices, Insights2Techinfo, pp.1