By: Soo Nee Kee1,2
1Universiti Malaya, Kuala Lumpur, Malaysia.
2International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, Email: nee.kee2001.nks@gmail.com
Abstract
Cloud computing is an on-demand IT resource over Internet such as data storage and virtual machines. Some well-known cloud service providers such as Amazon, Azure and Alibaba provide various services on pay-as-you-go basis, ensuring costs are are aligned with actual usage while providing elasticity to scale resources as needed. Many enterprises transform to cloud services to save costs and time, eliminating the need to build and maintain own IT infrastructure. However, security issues are still the main concerns of cloud environments, especially phishing. Therefore, a phishing detection mechanism is proposed using machine learning.
Keywords: Machine Learning, Bidirectional Long-Short Term Memory, BiLSTM, Fully Convolutional Network, FCN, Backpropagation, BP, Phishing Detection, Cloud
Introduction
Phishing is one of the common cybersecurity that tricks individuals into providing private information such as bank accounts and passwords by using fake URLs, emails or messages. Attackers can utilise the stolen information to gain unauthorized access to individuals’ accounts, making malicious financial transactions or even selling those data on the dark web. [1] In cloud environments, phishing is a serious issue as attackers will use homograph URLs, making it difficult to detect using traditional security mechanisms. Thus, machine learning is brought to the table to identify phishing emails, URLs or messages effectively. In this paper, a phishing detection method is proposed using Bidirectional Long-Short Term Memory (BiLSTM), Backpropagation (BP) and Fully Convolutional Network (FCN). [2]
Techniques
The proposed system utilises BiLSTM, FCN and BP to develop phishing detection. BiLSTM is an enhanced version of recurrent neural network (RNN) that is used for analysing sequential data. It reads input in both directions and retains data for a longer period, which can help in understanding patterns of email contents and URLs and detect any suspicious or phishing contents effectively. In addition, BiLSTM can detect the new phishing method called Browser in the Browser Attack (BiTB). [3] The use of FCN can conduct local feature extraction. It helps detect irregular structures in URLs by applying convolutional layers on the input and extracting feature maps directly, ensuring the spatial relationship is preserved. Besides, BP is optimization technique that is used for final classification. It helps reduce classification errors by adjusting weights in both BiLSTM and FCN during training.
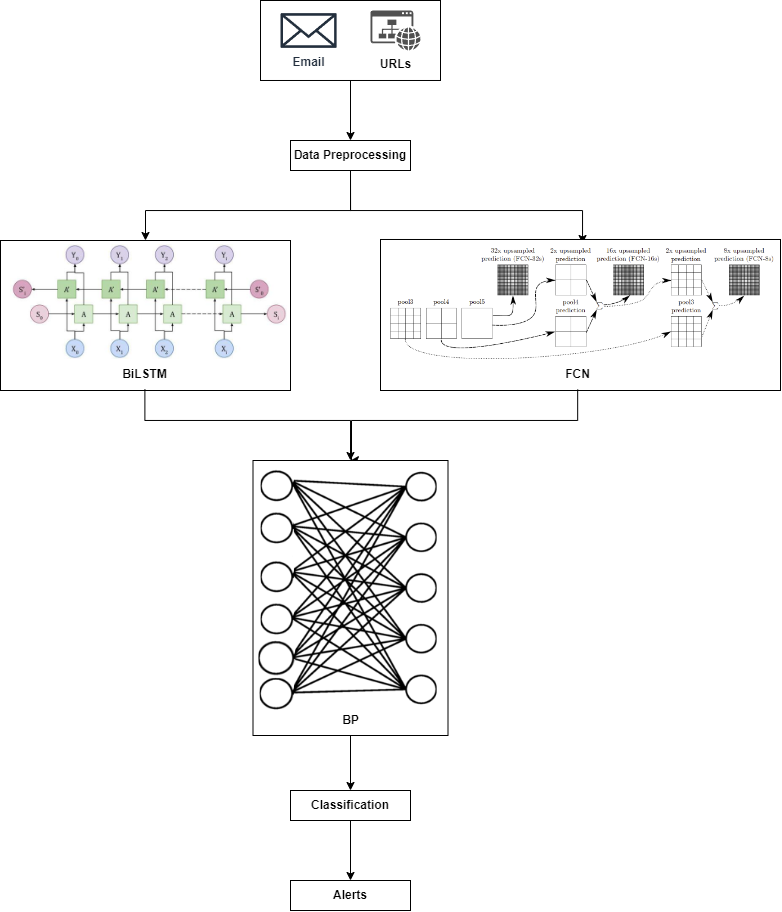
Conclusion
In conclusion, the combination of BiLSTM, FCN and BP provides a robust solution to detect phishing in cloud environment effectively. BiLSTM analyses sequential patterns of emails and URLs in order to identify suspicious phishing contents while FCN provides local feature extraction to detect anomalies in phishing attempts. BP helps optimize the classification model and improves phishing detection accuracy. This machine learning approach can mitigate phishing attempts and enhance overall security in cloud environment.
Reference
- K. L. Chiew, K. S. C. Yong, and C. L. Tan, “A survey of phishing attacks: Their types, vectors and technical approaches,” Expert Syst. Appl., vol. 106, pp. 1–20, Sep. 2018, doi: 10.1016/j.eswa.2018.03.050.
- T. Wen, Y. Xiao, A. Wang, and H. Wang, “A novel hybrid feature fusion model for detecting phishing scam on Ethereum using deep neural network,” Expert Syst. Appl., vol. 211, p. 118463, Jan. 2023, doi: 10.1016/j.eswa.2022.118463.
- “PhishingRTDS: A real-time detection system for phishing attacks using a Deep Learning model – ScienceDirect.” Accessed: Oct. 05, 2024. [Online]. Available: https://www.sciencedirect.com/science/article/pii/S0167404824001445
- Gupta, B. B. (Ed.). (2021). Advances in Malware and Data-driven Network Security. IGI Global.
- Sharma, P. C., Mahmood, M. R., Raja, H., Yadav, N. S., Gupta, B. B., & Arya, V. (2023). Secure authentication and privacy-preserving blockchain for industrial internet of things. Computers and Electrical Engineering, 108, 108703.
- Tan, H., Gu, Z., Wang, L., Zhang, H., Gupta, B. B., & Tian, Z. (2022). Improving adversarial transferability by temporal and spatial momentum in urban speaker recognition systems. Computers and Electrical Engineering, 104, 108446.
Cite As
KEE S.N. (2024) Cloud-Based Phishing Attack Detection Using Machine Learning, Insights2Techinfo, pp.1