By: Soo Nee Kee1,2
1Universiti Malaya, Kuala Lumpur, Malaysia.
2International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan Email: nee.kee2001.nks@gmail.com
Abstract
Cloud computing is widely used by many organizations and corporates in recent year due to its scalability, flexibility and cost-effectiveness. Cloud computing offers a range of services, including storage, servers and software, enabling organizations to use the resources on demand. It allows businesses to scale their IT infrastructure horizontally and vertically without the significant need of hardware investment. It brings a lot of convenient to human life by offering ease to use solutions. However, the security issues still the main concern of cloud computing, especially phishing attacks since the traditional security measurement is difficult to prevent phishing. Thus, a decentralized phishing blacklist approach is proposed to mitigate phishing attacks in cloud computing.
Keywords: Blockchain, Smart Contracts, Cloud Computing, Phishing
Introduction
Phishing is one of the common cybersecurity attacks, in which attackers persuade victims to open a fake URLs found in emails, messages or websites. The fake URLs can be worn to victims, as attacks can steal privacy information for unauthorized use, which lead to sensitive data leakage or financial loss. Thus, blockchain is implemented in the virtual environment to prevent phishing in cloud computing. Blockchain is a decentralized ledger that stores transaction records in a distributed manner, which means data is distributed across each node within a network. Therefore, stored data is difficult to modify, edit or delete, providing temper-resistant to the system and ensuring transparency and traceability. [1]
Proposed Framework
In this paper, a decentralized phishing blacklist approach is proposed by using blockchain, eliminating centralized storage and preventing single point failure. Blockchain is used to store all potential phishing URLs. Its temper-proof nature enhances the security since nobody can modify or delete the stored records on blockchain. In the cloud environment, there are several nodes spread across the network to perform analysis in order to detect phishing URLs. Once URLs are classified malicious, smart contracts will be triggered, logging the phishing URLs and its domain information on blockchain. The stored information consists phishing URL’s metadata such as timestamp, domain and URL. Those metadata will be stored in block and each block connects previous blocks via cryptographic chain, making it impossible to edit and any malicious changes on blockchain can be traced. [2] When new phishing URL is added, the system will propagate across the network to give alerts to all nodes, protecting them from phishing vulnerabilities. This phishing blacklist approach integrates with cloud to detect and prevent phishing attacks effectively, providing a safe place for all cloud users.
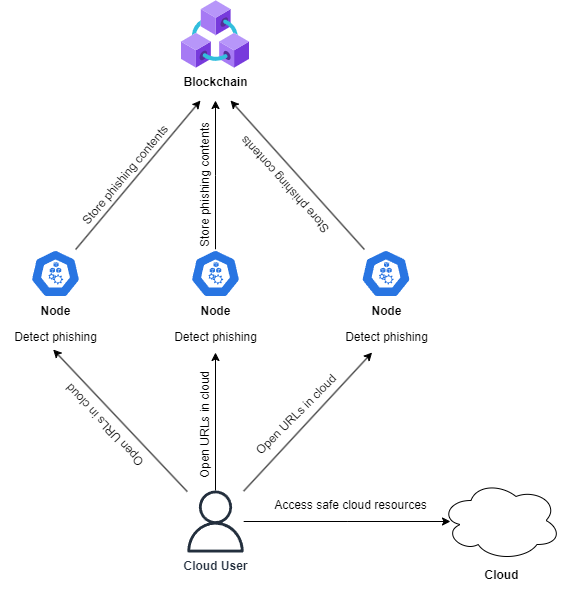
Conclusion
In conclusion, building a decentralized phishing blacklist using blockchain can effectively prevent phishing attacks and enhance the security of cloud environment. All cloud users are able to view the entire blacklist in the blockchain, receiving real-time alerts about the phishing contents. The use of smart contracts helps automate the process of storing phishing contents on blockchain, providing a seamless and efficient way for updating and distributing the blacklist across the network. Furthermore, the tamper-resistant characteristic of blockchain not only strengthen the security of cloud computing, but also enhances the transparency and accountability of the cloud environment.
Reference
- “Exploring the integration of edge computing and blockchain IoT: Principles, architectures, security, and applications – ScienceDirect.” Accessed: Oct. 04, 2024. [Online]. Available: https://www.sciencedirect.com/science/article/pii/S1084804524000614
- R. Karthika, C. Valliyammai, and M. Naveena, “Phish Block: A Blockchain Framework for Phish Detection in Cloud,” Jun. 2022, doi: 10.32604/csse.2023.024086.
- Vajrobol, V., Gupta, B. B., & Gaurav, A. (2024). Mutual information based logistic regression for phishing URL detection. Cyber Security and Applications, 2, 100044.
- Gupta, B. B., Gaurav, A., Panigrahi, P. K., & Arya, V. (2023). Analysis of cutting-edge technologies for enterprise information system and management. Enterprise Information Systems, 17(11), 2197406.
- Gupta, B. B., Gaurav, A., & Panigrahi, P. K. (2023). Analysis of retail sector research evolution and trends during COVID-19. Technological Forecasting and Social Change, 194, 122671.
Cite As
Kee S.N. (2024) Cloud Computing Security Frameworks: Mitigating Phishing Attacks in Virtual Environments, Insights2Techinfo, pp.1