By: 1Tanish Aggarwal, 1Department of CSE, Chandigarh College of Engineering & Technology, Chandigarh, India.
Abstract
Lockheed Martin’s Cyber-Kill Chain methodology, comprising seven phases, offers a structured defensive strategy against cyber-attacks, emphasizing proactive measures like threat intelligence, security training, and incident response plans. Concurrently, the article introduces the Zero Trust model, challenging traditional trust assumptions in cybersecurity by advocating for continuous verification and dynamic access controls, thereby minimizing the potential impact of breaches. Together, these approaches underscore the importance of understanding attack lifecycles and implementing proactive defence strategies in today’s evolving digital landscape, providing organizations with effective tools to safeguard their digital assets against cyber threats.
Keywords: Cyber Kill Chain, Threat Intelligence, Zero Trust Model, Network Segmentation, Behavioural Analysis, Incident Response Plan.
Introduction:
Nowadays cyber threats constantly evolving in today’s interconnected digital environment, organizations must adopt proactive and effective cybersecurity strategies. One popular scheme in cybersecurity is this cyber methodology. This is a comprehensive tool that helps organizations understand and protect themselves against sophisticated cyber-attacks. Cyber Kill Chain is a concept that explains cyber-attacks from the initial investigation to the attacker’s final goal The plan consists of seven steps, each representing an important step in the attacker’s activity.
The seven-step cyber-murder chain begins with “probing,” where attackers gather information about a potential target. Subsequently, the stages progress through “Weaponization,” “Delivery,” “Exploitation,” “Installation,” “Command and Control,” culminate in “Actions on Objectives.” This framework acts` as a strategic guide, enabling organizations to identify and disrupt cyber [9] threats at various points in the attack lifecycle.
This emphasizes proactive cybersecurity measures, including the integration of threat intelligence [2], security training, and incident response plans. Threat intelligence keeps organizations informed about evolving cyber threats, while comprehensive security [3] training ensures that employees are equipped to recognize and mitigate potential risks.
In addition to the Cyber Kill Chain, the discussion introduces the Zero Trust model [6] as a modern and adaptive cybersecurity approach. Challenging traditional notions of trust, the Zero Trust [14] model advocates for continuous verification and dynamic access controls. Organizations can strengthen their security measures against growing cyber threats by assuming that no entity, inside or outside the network [10] is inherently trustworthy.
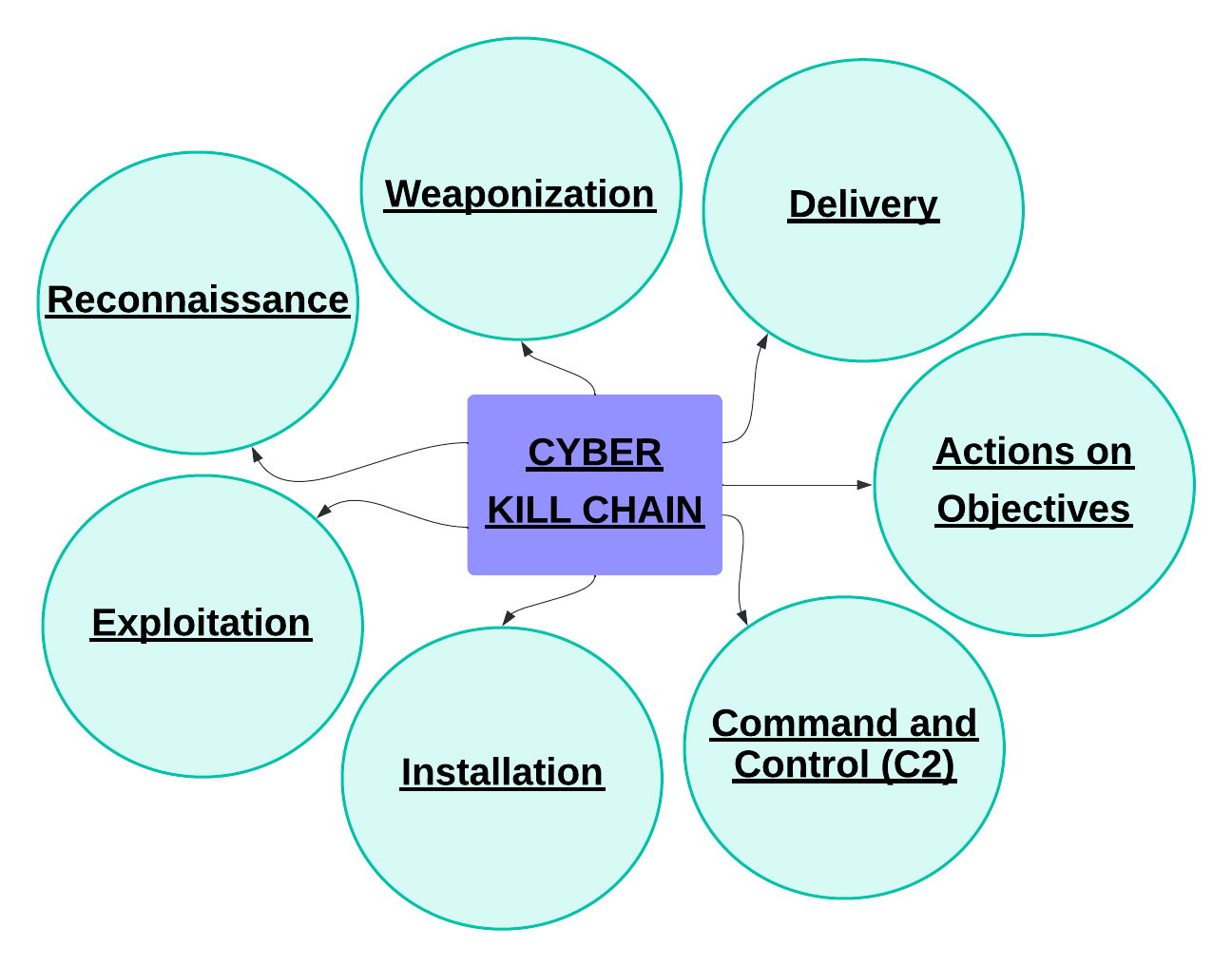
1. Reconnaissance
During the “Reconnaissance” phase of the Cyber Kill Chain, attackers gather information about their target, pinpointing potential vulnerabilities. This involves techniques like open-source intelligence (OSINT) gathering or scanning publicly available data [13]. By scrutinizing websites and social media, attackers compile valuable data for subsequent stages of the attack. This phase sets the foundation for informed decisions on weaponing and delivering malicious payloads. Organizations can enhance their defences by focusing on identified vulnerabilities during this initial stage of Cyber Kill Chain.
2. Weaponization
In the “Weapons” phase of the Cyber Kill Chain, attackers develop and develop the tools, malware, or exploits needed to thwart their targets. This may entail crafting malicious code or exploiting existing vulnerabilities. The goal is to prepare and weaponized the chosen method of attack, setting the stage for the subsequent delivery of the malicious payload. Organizations need to be vigilant in fortifying their defences against potential Weaponization by staying updated on emerging threats and vulnerabilities.
3. Delivery
In the “Delivery” phase of the Cyber Kill Chain, attackers deliver the payload to the target system. This can be performed by multiple manner, including phishing mails, infected websites, or any software updates. The objective is to successfully introduce the malicious elements into the target environment, establishing the groundwork for the subsequent stages of the attack. Organizations must implement robust security measures, such as email filtering and software patching, to thwart delivery mechanisms and prevent successful exploitation.
4. Exploitation
Upon successful delivery of the payload, the Cyber Kill Chain progresses to the “Exploitation” phase, where attackers exploit vulnerabilities in the target system to attain unauthorized access. This may entail capitalizing on software vulnerabilities, misconfigurations, or weak authentication mechanisms. By identifying and exploiting these weaknesses, attackers aim to establish a foothold within the compromised system, paving the way for further malicious activities. Organizations should prioritize regular system patching, robust configurations, and strong authentication protocols to mitigate the risk of exploitation during this critical [4] phase of the attack.
5. Installation
In the “establishment” phase of the cyber assassination chain, attackers strengthen their presence in a compromised system by actively establishing it. This could include deploying malware, creating a backdoor, or changing system settings to ensure continued compliance. The goal is to maintain a foothold within the compromised environment, enabling the attackers to execute subsequent stages of their malicious objectives. Organizations need to focus on continuous monitoring, advanced threat detection, and timely response to identify and eradicate any persistent elements introduced by attackers during this critical stage.
6. Command and Control (C2)
In the “Command and Control” of Cyber Kill Chain, attackers establish communication [2] channels to remotely control the compromised system. This enables them to issue commands, exfiltration data, or conduct various malicious activities without requiring direct physical access. By creating these remote control points, attackers maintain a covert and dynamic connection to the compromised environment, facilitating ongoing manipulation and exploitation. Organizations must implement robust network controls, intrusion detection systems and firewalls to identify and prevent unauthorized command and control activities during this critical stage of cyberattacks.
7. Goal-Oriented Actions
The concluding part of the cyber murder chain is the achievement of the attacker’s primary objectives. These objectives may encompass data theft, service disruption, or other malicious actions. This final stage signifies the culmination of the cyber-attack, where attackers execute their predetermined mission within the compromised system. Organizations must focus on comprehensive incident response plans, timely detection, and mitigation strategies to minimize the impact of malicious activities during this critical stage and swiftly recover from the aftermath of the cyber-attack.
Defending Against Cyber Kill Chain:
Understanding Cyber Kill Chain is crucial for developing effective cybersecurity strategies. Organizations can enhance their defences by implementing the following measures:
1. Threat Intelligence
Stay updated on emerging threats and vulnerabilities through threat notifications. This helps organizations anticipate potential attacks during the reconnaissance and weaponization stages.
2. Safety awareness training
Educate personnel on cybersecurity high-quality practices to reduce the chance of successful delivery and exploitation degrees. Training can help individuals recognize phishing attempts and other common attack vectors.
3. Vulnerability Management
Regularly assess and patch software vulnerabilities to mitigate the risk of exploitation. This includes maintaining an up-to-date inventory of assets and using automated tools to identify weaknesses.
4. Network Segmentation
Use grid segmentation to prevent segmentation of the infrastructure [1]. This makes it more difficult for attackers to traverse through the network even if they successfully exploit one segment.
5. Behavioural Analysis
Deploy advanced security solutions that utilize behavioural analysis to detect anomalous activities, such as unusual patterns of data access or communication, indicative of a compromised system.
6. Incident Response Planning
Develop and frequently test an incident response plan to ensure a spark off and accurate reaction to a safety incident. This consists of techniques for keeping apart affected applications [8], forensic investigations, and stakeholder engagement. Develop and frequently take a look at an incident response plan to make certain a set off and correct reaction to a security incident. This consists of techniques for separating affected packages, forensic investigations, and stakeholder engagement. Develop and regularly check an incident reaction plan to make sure a set off and correct response to a security incident. This includes techniques for keeping apart affected packages, forensic investigations, and stakeholder engagement.
Conclusion:
The Cyber-Kill Series, developed by Lockheed Martin, provides organizations with a systematic approach to understanding and mitigating cyber-attacks. By breaking down attacks into specific areas, such as reconnaissance, weapons supply, supply, operations, installation, command and control, objectives and operations, the plan provides we gain valuable insight into threat anatomy. This comprehension enables organizations to strategically bolster their defences by deploying targeted countermeasures at each stage of the attack lifecycle. Through proactive threat intelligence, robust security controls, and comprehensive incident response plans, organizations can disrupt adversaries tactics and significantly enhance their cybersecurity posture. In today’s dynamic threat landscape, where cyber adversaries continuously evolve their techniques, a proactive and multi-layered defence approach, informed by the Cyber Kill Chain, is imperative for safeguarding sensitive assets and maintaining operational resilience.
References:
- Sharma, A., Singh, S. K., Chhabra, A., Kumar, S., Arya, V., & Moslehpour, M. (2023). A Novel Deep Federated Learning-Based Model to Enhance Privacy in Critical Infrastructure Systems. International Journal of Software Science and Computational Intelligence (IJSSCI), 15(1), 1-23. http://doi.org/10.4018/IJSSCI.334711.
- Kumar, R., Singh, S. K., & Lobiyal, D. K. (2023, April). Routing of Vehicular IoT Networks based on various routing Metrics, Characteristics, and Properties. In 2023 International Conference on Computational Intelligence, Communication Technology and Networking (CICTN) (pp. 656-662). IEEE.
- Sharma, A., Singh, S.K., Kumar, S., Chhabra, A., Gupta, S. (2023). Security of Android Banking Mobile Apps: Challenges and Opportunities. In: Nedjah, N., Martínez Pérez, G., Gupta, B.B. (eds) International Conference on Cyber Security, Privacy and Networking (ICSPN 2022). ICSPN 2021. Lecture Notes in Networks and Systems, vol 599. Springer, Cham. https://doi.org/10.1007/978-3-031-22018-0_39
- K Aggarwal, SK Singh, M Chopra, S Kumar, F Colace (2022). Robotics and AI for Cybersecurity and Critical Infrastructure in Smart Cities. Springer, Cham(pp. 1-19).
- Manraj Singh, Sunil K Singh, Sudhakar Kumar, Uday Madan, Tamanna Maan(2023). Sustainable Framework for Metaverse Security and Privacy: Opportunities and Challenges. International Conference on Cyber Security, Privacy and Networking (ICSPN 2022).(pp 329-340). Springer International Publishing.
- Harshit Dubey, Sudhakar Kumar, Anureet Chhabra (2022). Cyber Security Model to Secure Data Transmission using Cloud Cryptography. Cyber Secur. Insights Mag(pp.1-4).
- Sudhakar Kumar, Sunil K Singh.(2021). Brain Computer Interaction (BCI): A Way to Interact with Brain Waves.(pp.1-10).
- Himanshu Setia, Amit Chhabra, Sunil K Singh, Sudhakar Kumar, Sarita Sharma, Varsha Arya, Brij B Gupta, Jinsong Wu.(2024) Securing the Road Ahead: Machine Learning-Driven DDoS Attack Detection in VANET Cloud Environments. Cyber Security and Applications
- M. Singh, S.K. Singh, S. Kumar, U. Madan, T. Maan
- Sustainable framework for metaverse security and privacy: opportunities and challenges. In International Conference on Cyber Security, Privacy and Networking, Cham: Springer International Publishing (2021), (pp. 329-340).
- Akash Sharma, Sunil K Singh, Sudhakar Kumar, Anureet Chhabra, Saksham Gupta(2023).Security of Android Banking Mobile Apps: Challenges and Opportunities. Springer International Publishing. International Conference on Cyber Security, Privacy and Networking (ICSPN 2022).(pp.406-416).
- Parnit Kaur, Sunil K Singh, Inderpreet Singh, Sudhakar Kumar.(2021) Exploring advanced Neural Network in Computer Vision-based Image Classification. International Conference on Smart Systems and Advanced Computing (Syscom-2021).(pp.18).
- Muskaan Chopra, Sudhakar Kumar, Uday Madan, Soumya Sharma.(2021) Influence and Establishment of Smart Transport in Smart Cities. International Conference on Smart Systems and Advanced Computing (Syscom-2021).(pp.6)
- Sudhakar Kumar, Sunil K Singh, Naveen Aggarwal(2023). Sustainable Data Dependency Resolution Architectural Framework to Achieve Energy Efficiency Using Speculative Parallelization. 2023 3rd International Conference on Innovative Sustainable Computational Technologies (CISCT).(pp.1-6) IEEE.
- Tanish Aggarwal (2024). Zero Trust on Cybersecurity Evolution. https://insights2techinfo.com/zero-trust-on-cyber-security-evolution/. (pp6-7).
- Kapil Raina(2023).Zero trust security explained: Principle Of The Zero Trust Model. https://www.crowdstrike.com/.(pp7-10)
- Cybersecurity and Infrastructure Security Agency, America’s Cyber Defence Agency (2022). Zero Trust Maturity model. https://www.cisa.gov/ (CISA). (pp 6-10).
- Aliss Irei, Sharon Shea (2021) Zero Trust Model Zero Trust Network. https://www.techtarget.com/. (pp 14-16).
- Lockheedmartin(2020) Cyber kill chain. Lockheedmartin.com
- Michael Buckbee (2023) What is The Cyber Kill Chain and How to Use it Effectively. https://www.varonis.com (pp 16-20)
- Bart Lenaerts Bergmans (2022) What is the Cyber Kill Chain? Process & Model. https://www.crowdstrike.com (pp 20-25)
- Malik, M., Prabha, C., Soni, P., Arya, V., Alhalabi, W. A., Gupta, B. B., … & Almomani, A. (2023). Machine Learning-Based Automatic Litter Detection and Classification Using Neural Networks in Smart Cities. International Journal on Semantic Web and Information Systems (IJSWIS), 19(1), 1-20.
- Verma, V., Benjwal, A., Chhabra, A., Singh, S. K., Kumar, S., Gupta, B. B., … & Chui, K. T. (2023). A novel hybrid model integrating MFCC and acoustic parameters for voice disorder detection. Scientific Reports, 13(1), 22719.
- Chui, K. T., Gupta, B. B., Liu, J., Arya, V., Nedjah, N., Almomani, A., & Chaurasia, P. (2023). A survey of internet of things and cyber-physical systems: standards, algorithms, applications, security, challenges, and future directions. Information, 14(7), 388.
- Sharma, P. C., Mahmood, M. R., Raja, H., Yadav, N. S., Gupta, B. B., & Arya, V. (2023). Secure authentication and privacy-preserving blockchain for industrial internet of things. Computers and Electrical Engineering, 108, 108703.
Cite As
Aggarwal T (2024) Cyber Kill Chain: Enhancing Cybersecurity Strategies, Insights2Techinfo, pp.1