By: Soo Nee Kee1,2
1Universiti Malaya, Kuala Lumpur, Malaysia.
2International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, Email: nee.kee2001.nks@gmail.com
Abstract
Smart home technology has brought a lot of benefits to us by automating of daily repeating tasks, eliminating the need of human intervention. For example, it helps controlling the temperature of rooms, intensity of lights and appliances. Smart security system provides real-time monitoring and anomaly detection, allowing users to remote control, effectively improving the efficiency and quality of life. Nonetheless, it also brings security issues as there are many interconnected devices and attackers can exploit vulnerabilities in these devices to gain unauthorized access. Therefore, a robust security mechanism is needed to protect smart home systems from security threats and privacy data leakage. In this paper, a blockchain based IoT-enabled smart home system is proposed to detect and prevent phishing effectively.
Keywords: Smart Home, IoT, Blockchain, Smart Contracts, Phishing
Introduction
Phishing attacks is the most common cybersecurity threats in IoT ecosystem, especially smart homes. Attackers steals victims’ privacy data by using fake emails or messages to trick them. Those fake emails look like legitimate emails and victims face difficulty to differentiate it normally. Once the users open the phishing contents, attackers can gain unauthorized access to victims’ data. Moreover, phishing can be used to distribute malicious software, which leads to malware attack and disrupt operations. This causes serious problem in a smart home as there are many interconnected devices and actuators together, including smart electricity and water bills, smart locks or smart security system, smart healthcare systems, smart thermostat and others. Once a system in smart home has been exploited, it will lead to security vulnerabilities of other systems as well. Thus, the phishing threats should be addressed immediately to avoid more serious problems come.
To mitigate phishing attacks, blockchain, a decentralized ledger which store transaction in distributed manner is proposed. Blockchain enhances the security, traceability and transparency of smart home system, preventing malicious changes and deletion of the data. Once data is added on blockchain, it will be stored in a block and each block connected via cryptographic chain. [1] Thus, it is impossible for a blockchain user to change or delete the data without consensus. Blockchain can be classified into three categories: public chain, private chain and federated chain. The main different between three chains is the access permission. Public blockchains are permissionless which mean all users can use blockchains while both private blockchains and federated blockchains are permissioned blockchain. The different is private chains are managed by one entity while federated chains are managed by a group of authorized organizations. [2] In this paper, federated chain is used to build a smart home as it connects multiple trusted entities like utility or house automation companies.
Technique
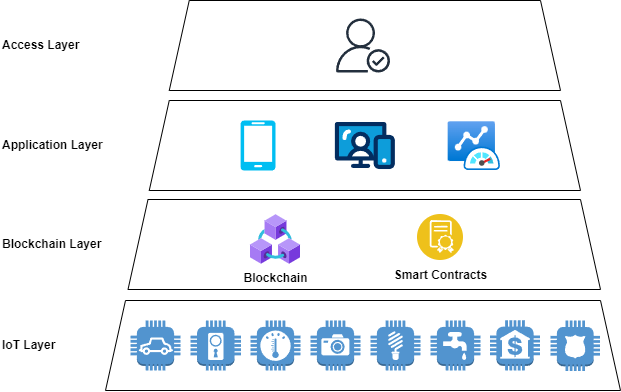
The integration of federated blockchain with IoT-enabled smart home can mitigate phishing effectively. This is because federated blockchain only allows authorized entities to access blockchain. In addition, blockchain can prevent modification or deletion of stored data, fostering users’ trust. The paper proposes a four-layer architecture to detect and prevent phishing attacks: IoT layer, blockchain layer, application layer and access layer. [3] IoT layer, also known as blockchain nodes, consists of a lot IoT devices, such as smart TV, smart locks, Closed-circuit television (CCTV) and wearable devices. Those devices collect data for data analysis and anomalies detection. Once there is an abnormal occurs, IoT devices will respond to the abnormality by triggering predefined actions. For example, IoT devices will send alerts to users, shut down the devices and change devices setting to mitigate any potential losses and damage. The collected data will then be stored in blockchain. Blockchain is built on top of IoT ecosystem. There are two main components in this layer: blockchain technology and smart contracts. Smart contract is a set of rules followed by different entities to manage the relationship for exchanging values. Smart contract helps to automate the storing processes, eliminating the need of intervention.
Entities such as house owners and service providers can access and view the data through application layer. Application layer provides user-friendly interfaces for users to interact with the data. It will display the data dashboard based on access policies for users to view data and anomalies happed. For example, healthcare providers can access house owners’ health records, but not other records like CCTV. Application layer also provides services like utilities payment automation, healthcare interoperability and others to bring a lot of convenience to users. Access layer means the entities involved in the smart home system, such as house owners and his families, healthcare experts, utilities providers, and authorized service technicians. This layer ensures that each entity has appropriate access permissions based on their roles. It also manages user authentication and security protocols, ensuring data privacy and secure communication between IoT devices and users.
Conclusion
In conclusion, the proposed blockchain-based IoT-enabled smart home system offers a secure solution to mitigate phishing attacks. Federated blockchain architecture ensures only authorized entities have the access right to certain data, preventing unauthorized modification on the data and promoting trust and accountability. The four-layer architecture integrates IoT devices, blockchain and application interface, providing real-time data analysis, anomaly detection and automated responses to any security vulnerabilities. It not only enhances the efficiency and security of the smart home systems, but also provides the seamless interaction among service providers and users, improving the quality of life ultimately.
Reference
- “Exploring the integration of edge computing and blockchain IoT: Principles, architectures, security, and applications – ScienceDirect.” Accessed: Oct. 04, 2024. [Online]. Available: https://www.sciencedirect.com/science/article/pii/S1084804524000614
- “Blockchain-based cloud-fog collaborative smart home authentication scheme – ScienceDirect.” Accessed: Oct. 08, 2024. [Online]. Available: https://www.sciencedirect.com/science/article/pii/S1389128624000720
- Md. Moniruzzaman, S. Khezr, A. Yassine, and R. Benlamri, “Blockchain for smart homes: Review of current trends and research challenges,” Comput. Electr. Eng., vol. 83, p. 106585, May 2020, doi: 10.1016/j.compeleceng.2020.106585.
- A. Gaurav, B. B. Gupta, K. T. Chui and V. Arya, “Enhancing Email Security in Consumer Electronics with a Hybrid Deep Learning Approach,” 2024 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 2024, pp. 1-5, doi: 10.1109/ICCE59016.2024.10444468.
- T. Zhang, J. Shen, H. Yang, P. Vijayakumar, B. B. Gupta and V. Arya, “Sustainable Authentication and Key Agreement Protocol Using Chaotic Maps for Industry 5.0,” in IEEE Transactions on Consumer Electronics, vol. 70, no. 1, pp. 1580-1589, Feb. 2024, doi: 10.1109/TCE.2023.3339818.
- Tian, Y., Tan, H., Shen, J., Pandi, V., Gupta, B. B., & Arya, V. (2023). Efficient identity-based multi-copy data sharing auditing scheme with decentralized trust management. Information Sciences, 644, 119255.
Cite As
Kee S.N. (2024) Detection and Prevention of Phishing Attacks in IoT-Enabled Smart Homes Using Blockchain, Insights2Techinfo, pp.1