By: Vanna karthik; Vel Tech University, Chennai, India
Abstract
Phishing scams have changed considerably over time, moving from straightforward email-based attacks to increasingly complex plots that target social media, text messaging, and other channels of communication. The article explores the development of phishing techniques, highlighting the strategies used by cybercriminals to take advantage of both human weaknesses and technology advances. . This paper pinpoints some relevant tactics being used in current phishing and discusses practical defenses by reviewing case studies and current trends. The findings have brought into focus the importance of sustained awareness, flexible defenses, and technological improvement in fighting the ever-changing phishing menace.
Introduction
It has long been a key element in cybercrime, as it merges technology and confidence to divulge private data. What once originated on the email platforms has now spread through social media platforms, text messages, and even phone calls-smishing and vishing, respectively [1]. With such variation, hackers are able to reach an even bigger audience and tailor their attacks to capitalize on particular weaknesses. With the increased use of mobile devices, digital interactions have dramatically risen, thereby making phishing schemes a threat as never before. This article looks into the challenges proposed by these innovative methods and how methods of phishing have time and again shifted..
Literature review
A lot of research has been done on the evolution of phishing, with academics examining how attackers’ techniques and technologies have changed. Early research on email phishing, such that done by[2], highlighted how social engineering is a key component of this tactic. The emergence of smishing and its particular difficulties, such sending customized messages to mobile users, have been brought to light by recent studies[3]. Another new type that takes advantage of voice-over-IP (VoIP) technology is called vishing[4].
Phishing schemes have evolved significantly from traditional email-based approaches to include new digital channels such as social media platforms, text messaging (smishing) , and voice calls (vishing). While early phishing attempts used generic emails sent to huge audiences, spear phishing and other highly targeted and customized attacks are common nowadays[5]. Nowadays, cybercriminals distribute malicious links that look like genuine notifications by taking advantage of mobile devices and the popular usage of instant messaging programs. Vishing attacks, in which criminals appear as legitimate organizations over the phone, have also been made easier by the development of VoIP technology. This development highlights how phishing tactics can change, becoming more dangerous and difficult to identify than in the past.
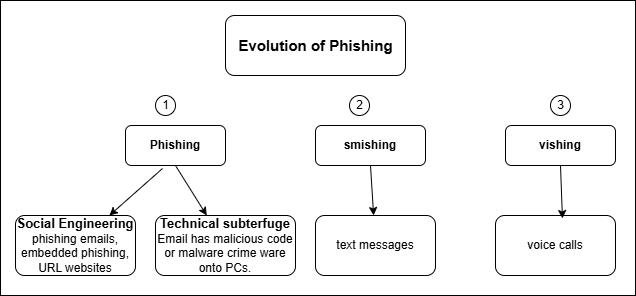
These phishing schemes have become more specialized with the advancement of technology, exploiting the peculiar weaknesses of each platform. Nowadays, attackers use artificial intelligence and machine learning to construct very plausible phishing communications that implement the logo and tone of trusted companies. Social media has become a new battleground where scammers target users with dangerous links by compromising existing accounts or creating false identities[6]. Smishing, also known as mobile phishing, uses the sense of urgency that text messages, such phony bank alerts or package arrival notifications, frequently convey. Cross-platform phishing methods include a variety of techniques wherein the victim is texted to the fake email or website. Due to the growth of digital platforms, which has complicated identification and protection, the attackers have been able to expand their methods. Because of the constant growth of methods, much more awareness and advanced detection technologies are needed to effectively tackle phishing. On the other hand, developments in machine learning and artificial intelligence indicate potential ways of limiting such risks.
Methodology
In the present study, a sequential mixed-methods approach was undertaken to find how phishing scams evolve. Quantitative data collection regarding incident reports on cybersecurity incidents has been done with a view to finding out the frequency and types of phishing attacks in recent years. Case studies regarding significant phishing were also studied to look for trends or new emerging variants. This holistic approach presents a wide view of how phishing strategies have evolved and how they have been affecting different groups.
Conclusion
This growth has passed from simple email attacks to highly complicated machinery that could use every channel of contact. Technological development and cybercriminal flexibility, taken together, nurture this very process. For effective protection from such risks, one needs to build a multidimensional strategy that covers strong protection with technology, current research of new patterns, and education of the general public. It will be necessary to mitigate the risks posed by these scams through a culture of cybersecurity awareness and by leveraging the latest solutions, as phishing tactics continue to evolve.
Reference
- J. Rastenis, S. Ramanauskaitė, J. Janulevičius, A. Čenys, A. Slotkienė, and K. Pakrijauskas, “E-mail-Based Phishing Attack Taxonomy,” Appl. Sci., vol. 10, no. 7, Art. no. 7, Jan. 2020, doi: 10.3390/app10072363.
- M. Schmitt and I. Flechais, “Digital deception: generative artificial intelligence in social engineering and phishing,” Artif. Intell. Rev., vol. 57, no. 12, p. 324, Oct. 2024, doi: 10.1007/s10462-024-10973-2.
- M. N. B. Haizam and N. H. binti N. Zulkipli, “Analysing The Impact of Smishing Attack in Public Announcement System on Mobile Phone,” Procedia Comput. Sci., vol. 245, pp. 1165–1174, Jan. 2024, doi: 10.1016/j.procs.2024.10.346.
- F. Toapanta, B. Rivadeneira, C. Tipantuña, and D. Guamán, “AI-Driven Vishing Attacks: A Practical Approach,” Eng. Proc., vol. 77, no. 1, Art. no. 1, 2024, doi: 10.3390/engproc2024077015.
- Y. Al-Hamar, H. Kolivand, M. Tajdini, T. Saba, and V. Ramachandran, “Enterprise Credential Spear-phishing attack detection,” Comput. Electr. Eng., vol. 94, p. 107363, Sep. 2021, doi: 10.1016/j.compeleceng.2021.107363.
- A. Basit, M. Zafar, X. Liu, A. R. Javed, Z. Jalil, and K. Kifayat, “A comprehensive survey of AI-enabled phishing attacks detection techniques,” Telecommun. Syst., vol. 76, no. 1, pp. 139–154, Jan. 2021, doi: 10.1007/s11235-020-00733-2.
- Sedik, A., Hammad, M., Abd El-Samie, F. E., Gupta, B. B., & Abd El-Latif, A. A. (2022). Efficient deep learning approach for augmented detection of Coronavirus disease. Neural Computing and Applications, 1-18.
- Deveci, M., Pamucar, D., Gokasar, I., Köppen, M., & Gupta, B. B. (2022). Personal mobility in metaverse with autonomous vehicles using Q-rung orthopair fuzzy sets based OPA-RAFSI model. IEEE Transactions on Intelligent Transportation Systems, 24(12), 15642-15651.
- Navaneeth J. (2024) Machine Learning Models that Excel in Detecting Phishing Attacks, Insights2Techinfo, pp.1
Cite As
Karthik V. (2025) From Email to Text and Voice : how Phishing scams are Evolving, Insights2techinfo pp.1