By: Vanna karthik; Vel Tech University, Chennai, India
Abstract
The fear and concern for DDoS attacks is growing greatly in organizations and among individuals with the continuous evolution of cyber threats. Because of the rise in sophistication, the conventional measurement for security appears to be proving inadequate against these DDoS attacks. This paper will present the study of integrating Machine Learning/Deep Learning techniques for enhanced DDoS detection and protection in complex networks. It aims to bring some improvement in accuracy, reduction of false positives, and realization of real-time response mechanisms by leveraging ML for pattern recognition and DL for deep feature extraction. The paper will present an overview of the existing techniques and discuss their limitations.
Introduction
Therefore, the fast growth of digital infrastructures has involved a partial increase in the frequency of cyber threats. Rather common is heavy disruption through DDoS attacks, for instance. Most of these DDoS attacks overwhelm network capacity and disrupt services, thus often inflicting substantial financial losses[1]. Conventional defense, which is based on rule-based systems and signature detection, has proved to be very slow to keep up with new and ever-changing attack patterns. One of the potential strategies is the application of ML and DL algorithms; these will lead to intelligent detection and reaction mechanisms. It reviews how the integration of ML and DL can ensure enhanced DDoS defense in complex network scenarios with increased security and resilience.
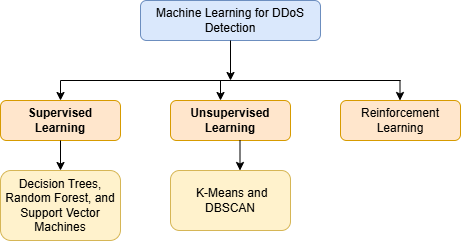
Machine Learning for DDoS Detection
Machine learning algorithms enhance DDoS detection by analyzing network traffic for anomalies in patterns. The major techniques based on ML include:
Supervised Learning: Algorithms such as Support Vector Machines, Random Forest, and Decision Trees classify malicious and legitimate traffic by using labeled datasets[2], [3].
Unsupervised Learning: Clustering techniques such as K-Means and DBSCAN identify outliers without any prior knowledge of attack patterns[2], [3].
Reinforcement Learning: By interacting with network environments, adaptive learning models dynamically enhance security rules[2], [3].
Deep Learning for Advanced Threat Protection[4]
By identifying even, the smallest attack signs and learning complex traffic patterns, deep learning algorithms offer an enhanced layer of security. Notable DL strategies consist of:
Convolutional Neural Networks (CNNs): Increase classification accuracy by extracting spatial characteristics from network data.
Long Short-Term Memory (LSTM) and Recurrent Neural Networks (RNNs): Record changes in traffic flow and detect recurring attack patterns.
Autoencoders: Recreate typical traffic patterns and highlight variations to identify irregularities.

Integration of ML and DL for Robust Security[5]
A hybrid approach that merges ML and DL further improves the DDoS defense mechanism as follows:
Multi-Layer Detection: ML provides the first layer of anomaly detection, refined by DL.
Feature Engineering: Features from ML are derived where the performance of the DL model can be optimized.
Adaptive Defense Strategy: Continuous learning in threat intelligence minimizes false positives.
Challenges and Future Directions
Despite these advantages, the ML and DL-based DDoS detection systems also suffer from a number of challenges, including but not limited to the following:
Adversarial Attacks: Attackers may craft adversarial inputs to deceive AI models.
Data Imbalance: Real-world attack datasets often have class imbalances, affecting model performance.
Future research should focus on improving model efficiency, developing adversarial-resistant techniques, and integrating AI-driven security solutions with cloud computing for scalable DDoS protection.
Conclusion
With DDoS attacks becoming a severe threat to network security, detection and mitigation need to be sophisticated. One of the feasible ways to enhance the DDoS prevention in complex networks is to combine ML and DL approaches. This approach will enhance the detection accuracy, reduce false positives, and allow for real-time response mechanisms by fusing the advantages of ML in feature selection with that of DL in deep pattern analysis. While the hybrid paradigm indeed has several advantages, the direction of future research should focus on further improvement in computing efficiency and responsiveness against changing cyber threats. The employment of AI-driven security frameworks is thus very important in ensuring effective network protection against an environment that has increasingly complex DDoS attacks.
References
- A. Aljuhani, “Machine Learning Approaches for Combating Distributed Denial of Service Attacks in Modern Networking Environments,” IEEE Access, vol. 9, pp. 42236–42264, 2021, doi: 10.1109/ACCESS.2021.3062909.
- A. H. Salem, S. M. Azzam, O. E. Emam, and A. A. Abohany, “Advancing cybersecurity: a comprehensive review of AI-driven detection techniques,” J. Big Data, vol. 11, no. 1, p. 105, Aug. 2024, doi: 10.1186/s40537-024-00957-y.
- J. Peng, E. C. Jury, P. Dönnes, and C. Ciurtin, “Machine Learning Techniques for Personalised Medicine Approaches in Immune-Mediated Chronic Inflammatory Diseases: Applications and Challenges,” Front. Pharmacol., vol. 12, Sep. 2021, doi: 10.3389/fphar.2021.720694.
- K. Yu et al., “Securing Critical Infrastructures: Deep-Learning-Based Threat Detection in IIoT,” IEEE Commun. Mag., vol. 59, no. 10, pp. 76–82, Oct. 2021, doi: 10.1109/MCOM.101.2001126.
- Joseph Nnaemeka Chukwunweike, Moshood Yussuf, Oluwatobiloba Okusi, Temitope Oluwatobi Bakare, and Ayokunle J. Abisola, “The role of deep learning in ensuring privacy integrity and security: Applications in AI-driven cybersecurity solutions,” World J. Adv. Res. Rev., vol. 23, no. 2, pp. 1778–1790, Aug. 2024, doi: 10.30574/wjarr.2024.23.2.2550.
- Sedik, A., Hammad, M., Abd El-Samie, F. E., Gupta, B. B., & Abd El-Latif, A. A. (2022). Efficient deep learning approach for augmented detection of Coronavirus disease. Neural Computing and Applications, 1-18.
- Kumar, N., Poonia, V., Gupta, B. B., & Goyal, M. K. (2021). A novel framework for risk assessment and resilience of critical infrastructure towards climate change. Technological Forecasting and Social Change, 165, 120532.
- Gupta, B. B., & Quamara, M. (2020). An overview of Internet of Things (IoT): Architectural aspects, challenges, and protocols. Concurrency and Computation: Practice and Experience, 32(21), e4946.
- Chokkappagari R (2024) Cyber security risks associated with computer software, Insights2Techinfo, pp.1
Cite As
Karthik V. (2025) Integrating Machine Learning and Deep Learning Techniques for Enhanced DDoS Detection and Protection in Complex Network, Insights2techinfo pp.1