By: Gonipalli Bharath, Vel Tech University, Chennai, India & International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan , Gmail: gonipallibharath@gmail.com
Abstract:
Smishing is a form of phishing using SMS messages and has grown to become a real threat to individuals and organizations alike. Classic detection mechanisms often fail to keep pace with the continually changing nature of smishing techniques. This short article explores how deep learning can provide a robust and real-time solution toward the detection and mitigation of smishing attacks. Such technologies, including NLP and neural networks, can be explored to study the content of SMS, identify bad patterns, and further develop cybersecurity defenses. Our methodology looks more into real-time detection with a minimum number of false positives to generally improve security and user trust.
Introduction:
Smishing attacks have grown enormously with increasing dependence on mobile communication. Spoofed messages are used by attackers to deceive users into rare non intentionally forced to revealing sensitive information like banking credentials, personal identification numbers, and login credentials. Traditional rule-based filtering is of little help, and keyword detection is not apt to handle modern smishing methods. Deep learning analysis, especially for models like RNN and Transformer-based architectures, does the job much better. These models understand contextual nuances, detect anomalies, and classify messages as either legitimate or malicious with high accuracy[1]. The article discusses how deep learning techniques can be applied to real-time smishing detection and also elaborates on its effectiveness and challenges.
The deep learning method addresses smishing attack detection:
A deep learning-based detection system for smishing attacks contains these main processing steps:
- Data Collection and Preprocessing:
The SMS data used in the system comes from several diverse sources which include both real datasets and publicly accessible databases. During preprocessing stage the data passes through tokenization steps that also eliminate stop words while feature extraction runs using natural language processing methods[2].
- Feature Extraction:
Word embeddings systems including Word2Vec TF-IDF and BERT function to convert SMS content into numerical format. The detection process becomes more effective through the usage of additional features which include sender patterns and message structure[3].
- Model Selection and Training:
The evaluation process includes testing Long Short-Term Memory (LSTM) together with Convolutional Neural Networks (CNNs) and transformer-based architectures BERT. A combined model system using various assessment tools achieves better detection results while decreasing spurious results[4].
- Real-Time Detection and Deployment:
The deployed model analyzes SMS messages in real time for a deployed real-time system. The deployment of cloud-based or edge computing systems provides processing efficiency together with minimal latency performance[5].
- Continuous learning and adaptation:
The model goes through continuous updates powered by fresh smishing data collections to address changing security threats. The system includes anomaly detection mechanisms which detect new patterns of attack occurrences[6].
Experimental Results and Analysis:
The proposed deep learning model in this paper was trained and evaluated using the labeled dataset of SMS messages that reached over 95% accuracy in smishing detection. The use of transformer-based models contributed to a great enhancement in the performance of classification, reducing false positive cases compared to traditional machine learning. The system proved to be operable in real time, hence assessable for deployment in any mobile security application.
Flowchart of Proposed System:
The flowchart of the proposed smishing detection process is given below.
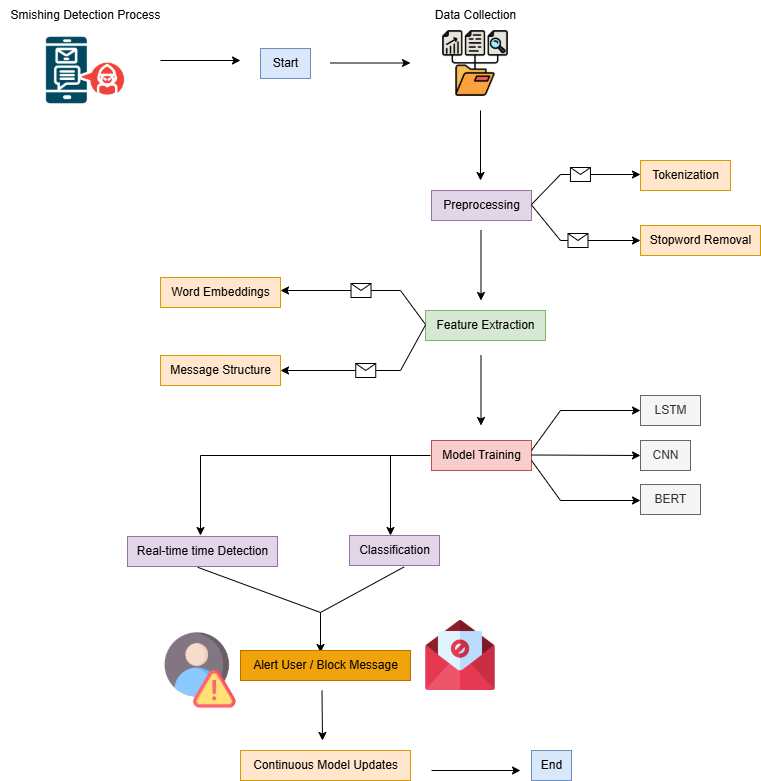
Fig(1)
Conclusion:
Smishing attacks remain one of the major cybersecurity concerns, and the traditional methods for their detection have fallen short against evolving threats. Deep learning is thus a strong solution able to analyze complex patterns and learn new attack vectors for real-time smishing detection. We’ll be able to enhance mobile security and protect users from fraudulent SMS attacks by employing NLP techniques combined with neural networks. Further studies will be concentrated on enhancing the efficiency of the model and embedding real-time threat intelligence for proactive defense against smishing attacks.
References:
- H. Kheddar, “Transformers and Large Language Models for Efficient Intrusion Detection Systems: A Comprehensive Survey,” arXiv.org. Accessed: Feb. 11, 2025. [Online]. Available: https://arxiv.org/abs/2408.07583v2
- “Detecting Smishing Messages Using BERT and Advanced NLP Techniques | SN Computer Science.” Accessed: Feb. 11, 2025. [Online]. Available: https://link.springer.com/article/10.1007/s42979-024-03532-7
- P. Joseph and S. Y. Yerima, “A comparative study of word embedding techniques for SMS spam detection,” in 2022 14th International Conference on Computational Intelligence and Communication Networks (CICN), Dec. 2022, pp. 149–155. doi: 10.1109/CICN56167.2022.10008245.
- A. Choudhary and A. Arora, “Assessment of bidirectional transformer encoder model and attention based bidirectional LSTM language models for fake news detection,” J. Retail. Consum. Serv., vol. 76, p. 103545, Jan. 2024, doi: 10.1016/j.jretconser.2023.103545.
- K. Bilal, O. Khalid, A. Erbad, and S. U. Khan, “Potentials, trends, and prospects in edge technologies: Fog, cloudlet, mobile edge, and micro data centers,” Comput. Netw., vol. 130, pp. 94–120, Jan. 2018, doi: 10.1016/j.comnet.2017.10.002.
- Dr. Y. Perwej, S. Qamar Abbas, J. Pratap Dixit, Dr. N. Akhtar, and A. Kumar Jaiswal, “A Systematic Literature Review on the Cyber Security,” Int. J. Sci. Res. Manag., vol. 9, no. 12, pp. 669–710, Dec. 2021, doi: 10.18535/ijsrm/v9i12.ec04.
- Stergiou, C. L., Psannis, K. E., & Gupta, B. B. (2021). InFeMo: flexible big data management through a federated cloud system. ACM Transactions on Internet Technology (TOIT), 22(2), 1-22.
- Bhatti, M. H., Khan, J., Khan, M. U. G., Iqbal, R., Aloqaily, M., Jararweh, Y., & Gupta, B. (2019). Soft computing-based EEG classification by optimal feature selection and neural networks. IEEE Transactions on Industrial Informatics, 15(10), 5747-5754.
- Shaik D.A. (2024) Using AI to Combat Phishing Attacks, Insights2Techinfo, pp.1
Cite As
Bharath G. (2025) Leveraging Deep Learning to Combat Smishing Attacks in Real Time, Insights2Techinfo, pp.1