By: Dadapeer Agraharam Shaik, Department of Computer Science and Technology, Student of Computer Science and technology, Madanapalle Institute of Technology and Science, Angallu,517325, Andhra Pradesh.
Abstract:
Phishing is still one of the most significant and frequent threats to individuals because hackers target specific aspects of human nature to make them disclose personal information. Quite traditionally, the awareness and identification of phishing threats as well as attempted preventive measures are not sufficient to protect users from sophisticated attacks. This paper seeks to establish how organisations are using AI in the fight against phishing attacks, the advantages, approach and the difficulties that come with it. Further, due to various Machine learning algorithms, natural language processing and behavioural analysis AI has the possibility of being a sophisticated solution in the scenarios for the recognition, anticipation, and containment of phishing. The fusion of AI into the cybersecurity models is expected to revolutionize the companies’ ability to prevent the sophisticated menace of phishing since integrated tools are stronger and far more efficient than singular models.
Keyword’s: Artificial Intelligence, Cyber-attacks, Phishing, Combat.
1.Introduction
Another common day type of cyber-attack is the Phishing where the attackers use appeal to emotion techniques that will compel the targets to disclose personal information like usernames, passwords, and credit card details. These attacks are gradually evolving, and this is posing a problem in terms of dealing with them, especially for traditional forms of security. Since con artists are actively developing their approaches, it is necessary to use enhanced tools for the identification and prevention of phishing. Hence, Artificial Intelligence (AI) come out as a strong tool in this fight, providing new methods to improve cybersecurity protection. Since machine learning is a branch of AI, it can use a large database to establish the correlation between the patterns and anomalies related to phishing activities. AI use Natural Language Processing (NLP) for it to analyse the content of emails and messages be it genuine or contain phishing messages. Further, behavioural analysis to detect the changes in user activity as it could be swerving in the direction of a typical phishing attack. Indeed, this article explores the use of AI in fighting the menace of phishing attacks as well as the opportunities, methods, and risks that must be acknowledged when implementing this approach.
2.Background on phishing attacks
The two are typically used differently by hackers and scammers to gain access to computers. Almost all these attacks incorporate a particular program that will gain full control of the user’s computer. Phishing attacks, in simple terms, is defined as the process of conveying invitational and consoling messages with the intention of extracting some values with the preteens of coming from an authentic source, mostly in the form of emails. Some of the objectives of the phishing attack include getting user login information together with the passwords and credit card information. These attacks may also incorporate posting malicious code on the users’ machines and then extorting money from them to have the code uninstalled[1].
Perhaps an everyday example of whaling would involve a user clicking a link in an email possibly from a fake sender and entering her/his credentials on what seems to be a legitimate website. Since the user tends to think that the website is a correct one, the user inputs the details required by the attacker, thus awarding the attacker with details that are strictly sensitive. Some of the prominent types that exist are email phishing, spear phishing, voice phishing, and the social media phishing. Phishing is one of the oldest tricks used by hackers and scammers Explaining the domain name, Raphael states that phishing is among the most common ways of attacking an organization. Another survey suggested that as many as 36% of all cyber-attacks are a result of phishing. The vice has recently grown rampant especially because of the growing phenomena of the use of the internet which makes people to easily fall prey with such attacks. This vice remains prevalent today since phishing is still vividly present in the modern world.
The use of phishing has been enhanced by the creation of technology especially the advanced intelligence in technology. AI and machine learning have also been used in the attacks and the attackers took it a notch high with phishing attacks becoming more complex. At present, the instances of phishing attacks have been on the rise, and within the last few years, there has been a high reportage. Thus, despite the defenders’ efforts and their attempt to establish cybersecurity in the digital world, new methods are being invented, and phishing is still a pressing issue internationally. The increasing complexity of these attacks show that there is a great need for staking up good security measures. Machine learning particularly artificial intelligence cut a promising picture in strengthening the defences against phishing [2].
3.Machine Learning (ML) For Phishing Attacks.
Different machine learning (ML) techniques have recently been used in solving the problem of detection of phishing sites, and subsequently the problem was turned into a classification one. For a training data to be used for developing a learning-based detection system, the data must contain features associated with the phishing and legitimate website classes. There exist several classifiers used for the purpose of detecting phishing attacks, this literature has established that there is high accuracy if appropriate and efficient machine learning classification is applied. Some of the feature selection methods are also used to minimize the chosen features so that the models’ efficiency is enhanced[3].
From the previously mentioned classifiers that are used in different studies and the ones that depict high accuracy in the detection of phishing attacks, the following are the most significant classifiers: 5, KNN (K-nearest neighbour), Linear, Polar, and SVM (Support Vector Machine). There are classifiers formulated from the Decision Trees like C4. 5 that increases the maximum chances of accurately identifying the attacks as well as enhancing efficiency. However, according to the literature, there are certain limitations reported in some of the studies like absence of use of ensemble learning schemes, insufficient feature selection.
For example C4 classifiers, etc. The employed techniques that include, 5, IBK (Instance-Based K), Naive Bayes (NB), and SVM has enhanced the detection accuracy. Random Forest (RF) has also been applied for distinguishing between the phishing attacks from the genuine web sites accurately. The ANN/FIS model that has combined the strength of easy and simple schemes and incorporated it by using several features has been applied for detecting and preventing Phishing attacks. With these classifiers, the different strengths help to boost the possibilities of detecting phishing.
Modern Approaches in the Use of Artificial Neural Networks in Phishing Detection
- Ensemble Learning Techniques: Ensemble learning therefore involves using many classifiers in order to come up with a better result in predicting the outcome. Other approaches like bagging, boosting or stacking are employable in ways that in developing an improved model which introduces the advantages and eliminates the vices of single classifiers. For instance, Decision Trees used in conjunction with such techniques as Random Forests or Gradient Boosting can increase the efficiency of phishing detection by several times.
- Deep Learning Approaches: Neural networks as a part of deep learning algorithms have been used in the identification of the phishing attacks. Artificial technologies such as Convolutional Neural Networks (CNNs) and Recurrent Neural Networks can be used in attempting to analyse the contents and organising structure of web pages, emails, and URLs in a bid to trying to identify potential phishing scams. They are able to learn more sophisticated patterns and features which might be beyond the capacity of the conventional models in the ML field.
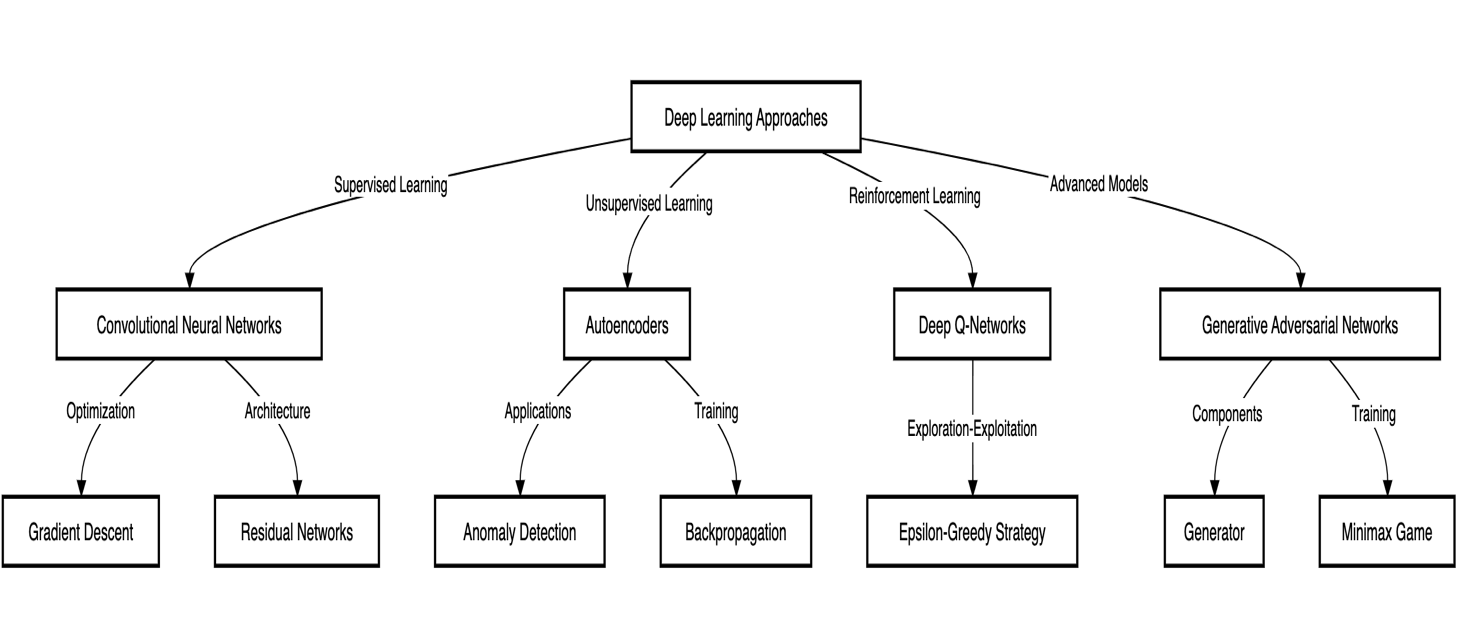
- Feature Engineering and Selection: This paper showed that selected features have a significant impact on models’ performance and depends on feature engineering. Based on previous studies, PCA analysis, RFE analysis, and skill such as Information Gain can be used to determine the best suited features for classifying a site as scraping. When the feature set is kept small, it becomes easy to cut costs on the aspect of overfitting and enhance model interpretability.
- Behavioural Analysis: It can be noted that using behavioural analysis in the development of ML models of phishing detection can improve communication. Data on analysed user characteristics like browsing patterns and login patterns can estimate such exceptions to detect the phishing attacks. This form can be used in conjunction with conventional content-based detection techniques for better protection.
- Hybrid Models: To boost the detection accuracy, w and hybrid models that include rules and ML should be used. They can capture recognizable sophisticated patterns that can be defined by rule-based systems, while at the same time, the new and emergent sophisticated phishing attacks can be captured by the ML models. This in turn creates a strong protection layer that can provide appropriate protection depending on the existing threats.
- Automated Training and Updating: This means that training as well as updating the models used in ML automation must all be done automatically to maintain the required detection rates. Hence, application of CI/CD pipelines can be useful for triggering the retraining process of such models and make it in sync with contemporary phishing strategies. It is useful in ensuring that the models do not become outdated and irrelevant in performing their tasks [4].
Conclusion:
In conclusion, Machine learning is proving to be highly useful in deterring phishing attacks with higher detection rates that give improved results as compared to traditional security measures. Through classifiers such as C4, one should be able to overcome the challenges and achieve the required learning outcomes. k-NN, SVM and classifier, ensemble learning, as well as the deep learning methods like 5, k-NN and SVM make the ML models efficient in the detection and prevention of phishing threats with good accuracy. There are still limitations which are data quality, changes in phisher’s behaviour, and the requirement of explain ability of AI models; yet the incorporation of ML as a part of the phishing detection systems offers reliable and self-improving protection. Ongoing research and combining efforts when creating and improving such technologies remain key for staying one step ahead of the black hats and keep the delicate and vital information safe from malicious acts and the integrity of the virtual space.
Reference:
- C.-Y. Lin, M. Rahaman, M. Moslehpour, S. Chattopadhyay, and V. Arya, “Web Semantic-Based MOOP Algorithm for Facilitating Allocation Problems in the Supply Chain Domain,” Int. J. Semantic Web Inf. Syst., vol. 19, pp. 1–23, Jan. 2023, doi: 10.4018/IJSWIS.330250.
- M. F. Ansari, P. Sharma, and B. Dash, “Prevention of Phishing Attacks Using AI-Based Cybersecurity Awareness Training,” vol. 3, pp. 61–72, Mar. 2022, doi: 10.47893/IJSSAN.2022.1221.
- K. T. Putra, A. Z. Arrayyan, R. Z. Syahputra, Y. A. Pamungkas, and M. Rahaman, “Design a Two-Axis Sensorless Solar Tracker Based on Real Time Clock Using MicroPython,” Emerg. Inf. Sci. Technol., vol. 4, no. 1, Art. no. 1, May 2023, doi: 10.18196/eist.v4i1.18697.
- A. Basit, M. Zafar, X. Liu, A. R. Javed, Z. Jalil, and K. Kifayat, “A comprehensive survey of AI-enabled phishing attacks detection techniques,” Telecommun. Syst., vol. 76, no. 1, pp. 139–154, Jan. 2021, doi: 10.1007/s11235-020-00733-2.
- Gupta, B. B., & Nedjah, N. (Eds.). (2020). Safety, Security, and Reliability of Robotic Systems: Algorithms, Applications, and Technologies. CRC Press.
- Gupta, B. B., & Srinivasagopalan, S. (Eds.). (2020). Handbook of research on intrusion detection systems. IGI Global.
- Gupta, B. B., Chui, K. T., Gaurav, A., Arya, V., & Chaurasia, P. (2023). A novel hybrid convolutional neural network-and gated recurrent unit-based paradigm for IoT network traffic attack detection in smart cities. Sensors, 23(21), 8686.
Cite As
Shaik D.A. (2024) Using AI to Combat Phishing Attacks, Insights2Techinfo, pp.1