By: G. Praneeth, K. Psannis, K. T.Chui
After computers and the Internet, smartphones became the third revolution in this digital age and made computing possible everywhere through remote access and control over information. Android dominates the market for smartphones as the most popularly accepted operating system. Android’s popularity also makes it cyber attackers and hackers’ primary targets. There are several forms of cyber-attacks aimed at the Android ecosystem. The smartphone is the concept of digital communications that incorporates telecommunications and Internet infrastructure into a single unit as it blends mobile phone portability with computer computing and networking capacity. As illustrated in Fig 1, Smartphones have linked the two primary services, Internet and telecommunications networks, as endpoints of both networks.
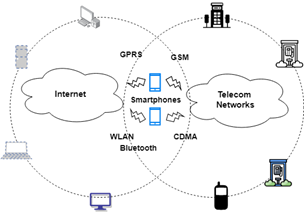
The main explanation for this trend is the simplicity and low cost of implementing modern integrated telecommunications and Internet services. Creation of ease of service includes standard operating systems (OSes). Because smartphones are typically as powerful as a couple of year-old computers, their operating systems have evolved to be pretty much complete. Although detailed design and functionality differ among these OS vendors, they all share the following characteristics [1]:
- Cellular network connectivity with different cellular standards, including GSM / CDMA and UMTS.
- Internet connectivity with different network interfaces such as infrared, Bluetooth, GPRS / CDMA1X, and 802.11; and standard TCP / IP stack protocol to unite the Internet.
- Multitasking for the simultaneous running of various applications.
- Synchronization of data with Desktop personal computers.
- Public APIs to develop applications.
Although conventional Operating systems, open APIs, and modern technologies allow vital services, they also build shared ground and chances for security breaches and increase the potential for virus or worm spread. Software bugs seem unavoidable for their OSes and applications despite the PC-like existence of smartphones and the rise of full-fledged operating systems. Also, with Internet vulnerability, smartphones have made a perfect target for Internet viruses or worms as smartphones are continuously steadily on overtime, and their client community will probably exceed that of computers, as seen from the occurrence of mobile phone use today.
Taxonomy of Smartphone Attacks
If a smartphone has been hacked through the Internet, it can become a starting point of animosity for the telecommunications networks it can access. However, the attacks mentioned here can also be extended to other popular cellular networks, such as CDMA. A smartphone can be compromised from the following three areas [7-11].
- Web attacks: Because smartphones are often web endpoints, they can be infected s by Trojan horses, viruses, or worms. A famous game application was identified as the first Symbian-based Trojan [2].
- Infection from breached PCs at the time of data synchronization: In General, Users of smartphones will be synchronizing their emails, schedules, or other types of data along with their desktop Devices via synchronization applications such as ActiveSync [3]. As a result, there will be some trust connections between smartphones and respective synchronization PCs. As a result, the attacker will first infect their synchronization computer for any infection or an attack on a smartphone. Eventually, the smartphone can be affected in the next synchronization period [12, 13].
- Smartphone infection or attack: A compromised smartphone will actively search and infect peer smartphones via its Wireless Personal Area Networks (WPAN) app, such as UWB (ultra-wideband) or Bluetooth. As smartphones are mobile devices, they are capable of infecting new victims at different locations. The first smartphone worm, Cabir, uses this method.
Defense Strategies
- Reduction of Surface Attacks (Feature Reduction):
The primary responsibility would be to decrease as much as needed the attack layer, which is probed that affects the system[4]. However, this defensive scheme has been extended to PCs [5] with moderate progress because it disrupts typical applications such as file sharing and network printers. However, this approach could be more appropriate for smartphones because the smartphone use model varies to PCs. While a smartphone is on, it doesn’t need to have many of its functions involved. Consider an instance, the PC portion of the phones can be switched off when users make an outward phone call or write a Text message (unless otherwise directed, say, whenever a client downloads a film) [14-16].
- Harden the OS:
With hardened operating systems, until an attacker could subvert a smartphone Operating system instead of being observed, a smartphone user could more easily identify an intrusion of suspicious user level script behavior. Additional security regulations are also in place to strengthen OS’s, like using bug fixes and security fixes for applications, restricting user privileges, and removing unnecessary processors.
Users possess long preferred features over safety and protection and are unwilling to spend attention towards the security schemes [6] price, which is inconvenienced. Functionality interaction requires flexibility and calls for malicious attachments for extensibility. Considering the modern trend, we don’t hope to reduce smartphone power and functionalities unless the government effectively mandates the confined smartphone extensibility.
In the case of obsolete personal computers that are most exposed to risk, it’s noteworthy that implementing the restricted configuration guidelines applicable to websites, email clients, or PDF viewers is insufficient protection compared to upgrading to new ones. While mobile phones are more vulnerable to solely remote compromise, especially in comparison to old personal computers, their assemblage of features and capabilities provide an intruder of far larger abilities for collecting information and remote connections. These kinds of exploits also include monitoring the conversation with the help of a microphone, tracking of a location, surveillance cameras. These capabilities have a small impact on a compromised device that belongs to an ordinary citizen but may reveal critical classified data from a superior administration.
Efficient compromise detection remains a top priority, which depends on the cooperation of vendors on the platform. Detection is obstructed on specific platforms by the safety mechanisms themselves. For example, Application sandboxing restricts any security-enhancing application not offered as part of the user operating system by the platform vendor. Also, mobile devices by a believed or secured boot method, which is an important feature that usually helps to stop direct access for verifying purposes to the primary storage space of the device. Low-level device assistance for integrity examining could address the problem of vendors choosing to provide. Such design gives assurance that even a breached operating system does not give false integrity data.
References:
- Vaughan-Nichols, S. J. (2003). OSs battle in the smartphone market. Computer, 36(6), 10-12.
- Peikari, C. (2004, August 6). Summer Brings Mosquito-Borne Malware (Part 3 of 3) | InformIT. Inform IT.
- ActiveSync 4.5. (2007, February 13). Microsoft.
- He, D., Chan, S., & Guizani, M. (2015). Mobile application security: malware threats and defenses. IEEE Wireless Communications, 22(1), 138-144.
- Schmudlach, M. (2004, June 14). Virus News: Viruses move to mobile phones. CNET.
- Lampson, B. W. (2004). Computer security in the real world. Computer, 37(6), 37-46.
- Sharma, K., et al. (2016). Multi-layer defense against malware attacks on smartphone wi-fi access channel. Procedia Computer Science, 78, 19-25.
- Yamaguchi, S., et al. (2021). Malware threat in Internet of Things and its mitigation analysis. In Research Anthology on Combating Denial-of-Service Attacks (pp. 371-387). IGI Global.
- Akhtar, T., et al. (2018, January). Malware propagation effects on SCADA system and smart power grid. In 2018 IEEE International Conference on Consumer Electronics (ICCE) (pp. 1-6). IEEE.
- Li, S., Qin, D., Wu, X., Li, J., Li, B., & Han, W. (2022). False Alert Detection Based on Deep Learning and Machine Learning. International Journal on Semantic Web and Information Systems (IJSWIS), 18(1), 1-21.
- Rastogi, S., Bhushan, K., et al. (2016). Android applications repackaging detection techniques for smartphone devices. Procedia Computer Science, 78, 26-32.
- Pan, X., Yamaguchi, S., Kageyama, T., & Kamilin, M. H. B. (2022). Machine-Learning-Based White-Hat Worm Launcher in Botnet Defense System. International Journal of Software Science and Computational Intelligence (IJSSCI), 14(1), 1-14.
- Rastogi, S., Bhushan, K., et al. (2015). A framework to detect repackaged android applications in smartphone devices. International Journal of Sensors Wireless Communications and Control, 5(1), 47-57.
- John, N., & Sam, S. (2021). Provably Secure Data Sharing Approach for Personal Health Records in Cloud Storage Using Session Password, Data Access Key, and Circular Interpolation. International Journal on Semantic Web and Information Systems (IJSWIS), 17(4), 76-98.
- Mishra, A., et al. (2011, September). A comparative study of distributed denial of service attacks, intrusion tolerance and mitigation techniques. In 2011 European Intelligence and Security Informatics Conference (pp. 286-289). IEEE.
- Gaurav, A., Psannis, K., & Peraković, D. (2022). Security of Cloud-Based Medical Internet of Things (MIoTs): A Survey. International Journal of Software Science and Computational Intelligence (IJSSCI), 14(1), 1-16.