By: Achit Katiyar1,2
1South Asian University, New Delhi, India.
2International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan.
Email: achitktr@gmail.com
Abstract
These days, people use their mobile devices especially smartphones more and more because of the many functions they offer. Attackers are now focusing on mobile device users because these devices are incredibly small in size and offer many features that are comparable to desktop PCs. However, because desktop and mobile phishing attacks have different structures, detecting a mobile phishing assault presents a significant challenge. Furthermore, given the lack of study in this area, accurately identifying mobile phishing attacks is a critical research problem. This article’s main goal is to provide a brief study of mobile phishing attack methods and defense strategies.
Introduction
The security of smartphones is exploited by cyberthreats such Social Engineering, Distributed Denial of Service (DDoS) attacks, viruses, malware, unwanted emails, and malicious software. Phishing attacks are one such cyberthreat. Phishing is a sort of online spoofing that uses social engineering communications to trick people into doing actions that benefit the attacker[1].
Phone-based phishing, which directly engages victims, remains uncontrolled. In Q1 2024, OpSec discovered more than 20% of fraud-related assets using phone numbers. In Q1 2024, APWG recorded 963,994 phishing assaults, the lowest quarterly number since Q4 2021 (https://apwg.org/trendsreports/). Mobile device users are more vulnerable to phishing attacks than desktop users due to factors such as small screens, lack of identity indicators, inconvenience of input, switching between applications, and personal preferences. Users lack awareness about how to avoid phishing attempts[2].
Phishing attacks can be identified using a variety of approaches, including blacklisting, heuristic analysis, static detection, and detection based on the Universal Resource Locator (URL). Certain people utilize anti-phishing software that is readily accessible in the market. With a focus on the different tactics employed by attackers and the remedies suggested by researchers, this article aims to provide a general overview of mobile phishing attempts.
Background
The phrase “phishing” was first used in 1996 when several fraudulent users enrolled on the America Online (AOL) website using fictitious credit card information. As a result of system user error, attackers exploit vulnerabilities in the system. The most vulnerable link in cyber security is people. Phishing attacks are successful mostly because consumers are unaware of their presence. Numerous functions, including calling, texting, emailing, downloading, gaming, and playing music and video, are available to users of smartphones. Numerous consumers have been drawn to these extensive functions [3]. The number of smartphone owners rises annually. The global smartphone user base is currently 6.84 billion, and by 2020, it is predicted to reach 7.1 billion (https://whatsthebigdata.com/smartphone-stats/). Attackers target smartphone users using SMS, emails, websites, and mobile applications.
Mobile phishing attacks include the following phases[4]:
- Planning phase
- Phishing phase
- Penetration phase
- Data gathering phase
Security issues with smartphones
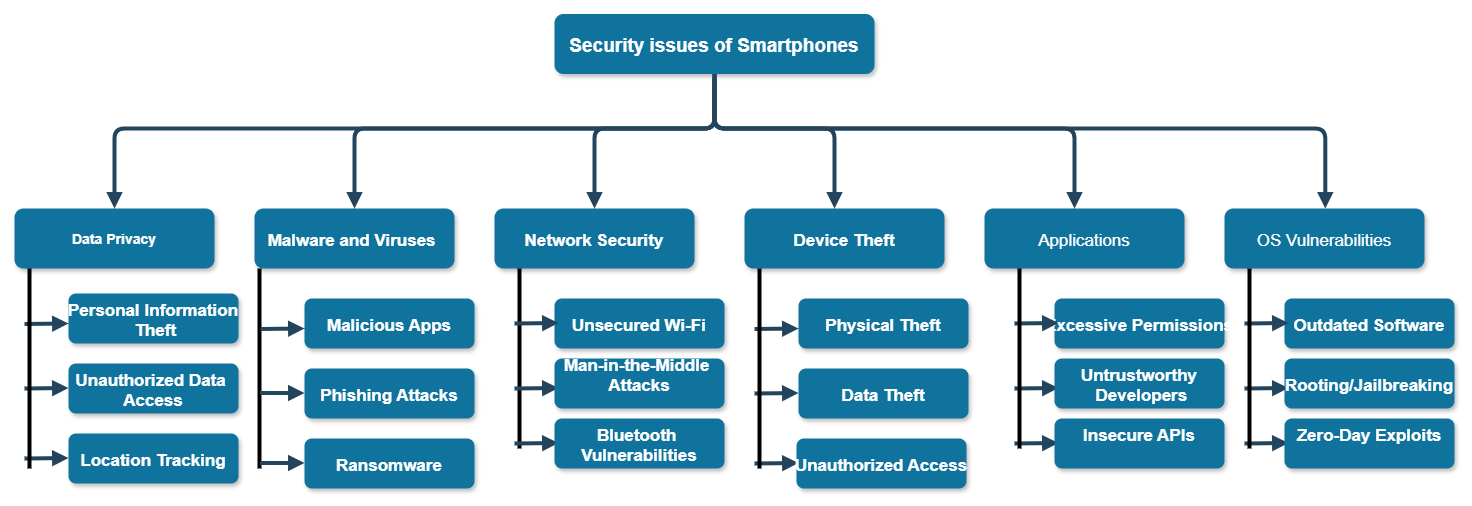
Cybercriminals target smartphones because they contain a wealth of personal data. Hacking/loss risks, malware infections, app vulnerabilities, network vulnerabilities, privacy breaches involving data, and vulnerability to phishing attempts are some of the major security challenges[4]. The key protections are safe app permissions, secure passwords, and frequent OS upgrades. Figure 1 shows various security concerns of smartphones.
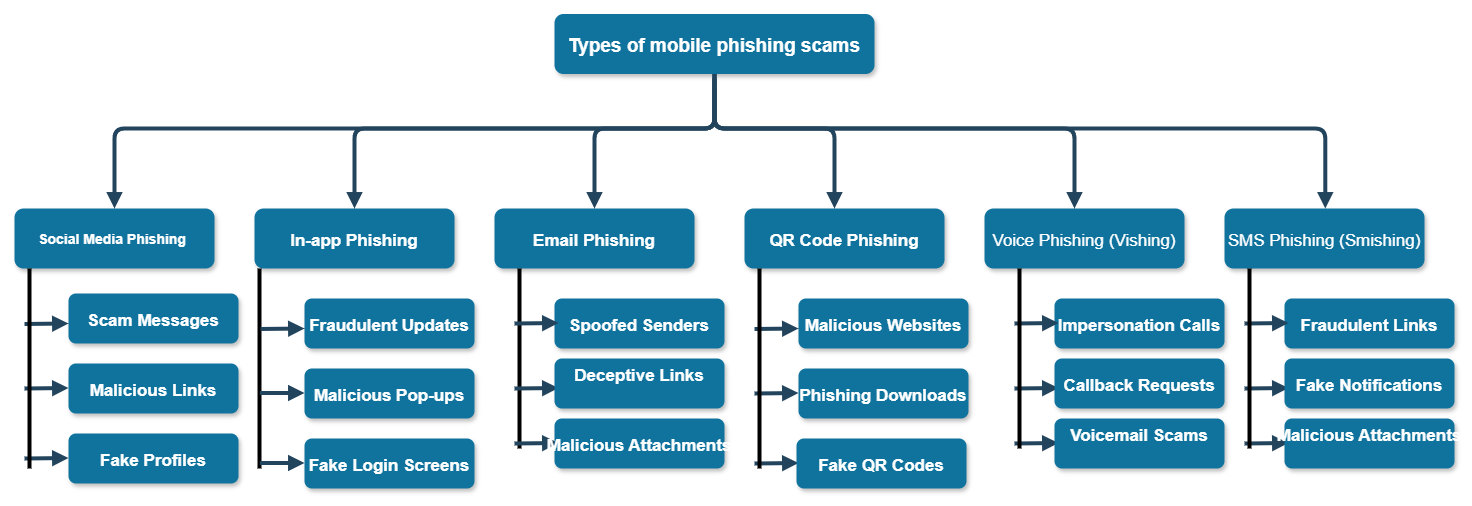
Types of mobile phishing scams
Figure 2 illustrates the classification of mobile phishing attempts.
Mobile phishing scams may be classed into social engineering, mobile applications, malware, websites for social networks, information injection, and wireless media[4].
The classification of mobile phishing defense systems
This section discusses numerous techniques to detecting and protecting against mobile phishing attempts. Figure 3 shows anti-phishing methods for various mobile phishing assaults.
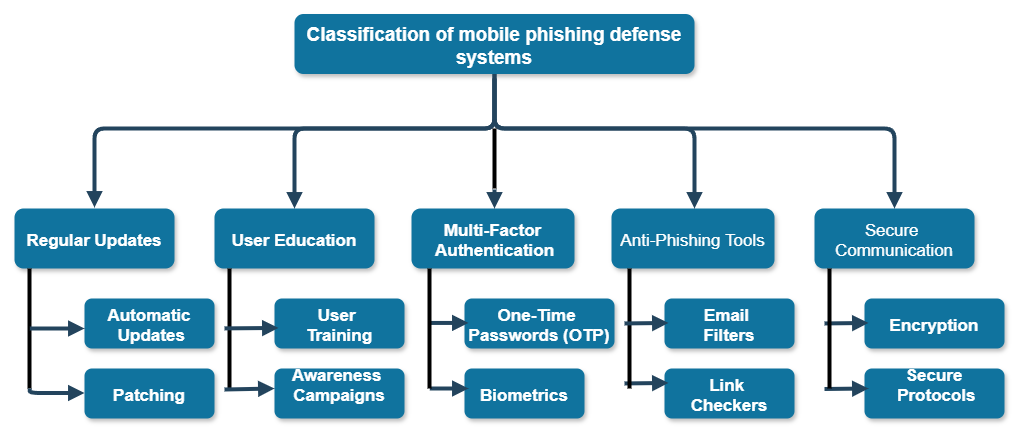 Figure 3 : Classification of mobile phishing defense systems
Figure 3 : Classification of mobile phishing defense systems
Challenges
Researchers have proposed many strategies to identify and avoid mobile phishing attempts, however no one approach is effective for all types of assaults. Researchers efforts to combat phishing assaults are often countered by attackers who identify vulnerabilities in existing solutions. There are some following open problems that need to be solved[4-7].
- Zero-day phishing attacks
- Update the criteria for list-based techniques
- Determining appropriate threshold values
- Language dependencies
- Selection of appropriate classifier
Conclusion
Phishing attacks try to obtain individual’s private data. Phishing attacks have traditionally targeted desktop users, but have recently switched to mobile devices. Mobile websites differ from desktops in content, style, and operation, necessitating unique strategies to prevent assaults. Fake websites, emails, and SMS messages are commonly used in social engineering to get user information. Victims are contacted through fraudulent communications to update their personal information. Malicious software can be installed on a user’s smartphone via malicious links or from the app store. SMS messages might be tough to ignore on mobile devices. A classification of phishing defense mechanisms can enhance user comprehension of the issue. Research may be conducted to build safeguards versus mobile phishing attacks, taking into account device variations.
References
- M. Khonji, Y. Iraqi, and A. Jones, “Phishing Detection: A Literature Survey,” IEEE Commun. Surv. Tutor., vol. 15, no. 4, pp. 2091–2121, 2013, doi: 10.1109/SURV.2013.032213.00009.
- “Recent survey of various defense mechanisms against phishing attacks: Journal of Information Privacy and Security: Vol 12 , No 1 – Get Access.” Accessed: Jul. 03, 2024. [Online]. Available: https://www.tandfonline.com/doi/full/10.1080/15536548.2016.1139423
- A. Carroll and G. Heiser, “An analysis of power consumption in a smartphone,” in Proceedings of the 2010 USENIX conference on USENIX annual technical conference, in USENIXATC’10. USA: USENIX Association, Jun. 2010, p. 21.
- D. Goel and A. K. Jain, “Mobile phishing attacks and defence mechanisms: State of art and open research challenges,” Comput. Secur., vol. 73, pp. 519–544, Mar. 2018, doi: 10.1016/j.cose.2017.12.006.
- Jain, A. K., et al. (2022). A content and URL analysis‐based efficient approach to detect smishing SMS in intelligent systems. International Journal of Intelligent Systems, 37(12), 11117-11141.
- Jain, A. K., et al. (2018). Rule-based framework for detection of smishing messages in mobile environment. Procedia Computer Science, 125, 617-623.
- Vajrobol, V., et al. (2024). Mutual information based logistic regression for phishing URL detection. Cyber Security and Applications, 2, 100044.
Cite As
Katiyar A. (2024) Mobile phishing attacks and defense strategies: Current state of the art and unrestricted research issues, Insights2Techinfo, pp.1