By: Gonipalli Bharath Vel Tech University, Chennai, India International Center for AI and Cyber Security Research and Innovations, Asia University, Taiwan, Gmail: gonipallibharath@gmail.com
Abstract:
Phishing and spear phishing remain among the top cyber-attacks that people and organizations face globally. In as much as they are both dubious ways to steal sensitive data, spear phishing bears more sophistication in target and means than phishing. This article explores with the explanation of key differences between phishing and spear phishing, their techniques, and their real-world impacts. By gaining an idea of these cyber threats, these individuals and businesses can put in more appropriate security measures to reduce risks. It also presents a comparative analysis in tabular form and a flowchart depicting the attack methodologies of phishing and spear phishing.
Introduction:
In recent times, cybersecurity threats have been increasing alarmingly. Two of the most dangerous methods of cyber-attack are phishing and spear phishing. These forms of attacks involve using human vulnerabilities instead of technical loopholes, hence making them all the more effective. It becomes very important to understand the distinction between these two forms of cyberattacks so that individuals and organizations can establish a robust defense mechanism[1].
What is Phishing?
Phishing is a general cyberattack approach whereby attackers impersonate a target’s trusted entities, such as banks or online services, to dupe users into divulging confidential information. These kinds of attacks generally happen through emails, fake websites, and social engineering methods. Most phishing attacks are automated and are cast on a wide number of individuals at any one time[2].
Common Types of Phishing:
- Scam emails asking for personal information.
- Fake websites that impersonate real sites.
- Scam links that point to websites hosting malware.
- Spoofed messages from trusted brands.
What is Spear Phishing?
Spear phishing is a more sophisticated, highly targeted form of phishing. In contrast to the wide net, the bad actor will focus on particular individuals or organizations, crafting personalized messages that seem highly credible. In some cases, spear phishing attacks may be linked to deep research on targets in pursuit of success[3].
Common Spear Phishing Techniques:
- Emails coming from a known contact.
- Messages including personal details, such as job title and recent activities.
- Attachments with malware pretending to be official documents.
- Requests to take urgent actions like wire transfers or verification of credentials.
Key differences between phishing and spear phishing are shown below in the table:
Feature | Phishing | Spear Phishing |
Target | Large groups, random individuals. | Specific individuals or organizations. |
Personalization | Generic messages. | Highly personalized and researched. |
Attack Method | Mass emails, Fake websites. | Custom emails, social engineering. |
Success Rate | Lower due to broad targeting. | Higher due to credibility and specificity. |
Common Victims | General internet users. | High-profile individuals, executives, employees. |
How these attacks work (Flowchart Representation):
Here is a flowchart representing how phishing and spear phishing attacks occur:
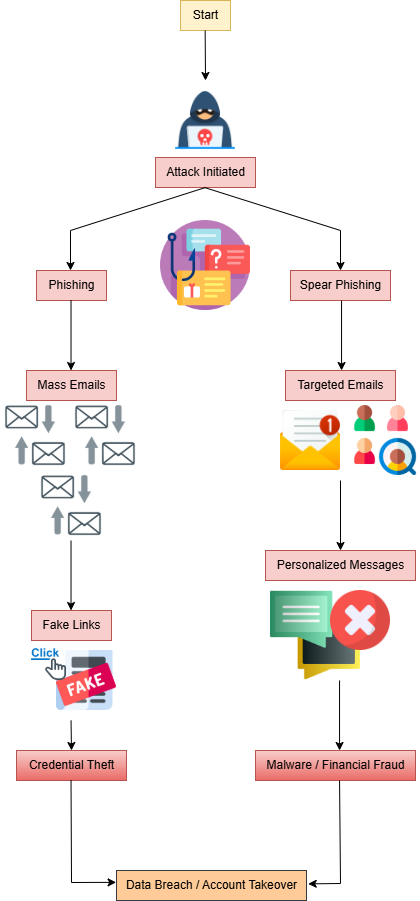
Fig(1)
Prevention Strategies:
To minimize the risks emanating from phishing and spear phishing, individuals and organizations should consider the following measures for security[4]:
Individuals:
- ‘Do not click on suspicious links within emails’.
Most phishing attacks rely on users clicking on links that are malicious. Verify the sender and hover over links before clicking to check their legitimacy[5].
- ‘Verify a sender’s email address before responding’.
Attackers use email spoofing to make messages appear to be from a particular sender. Check for small changes in domain names and verify unexpected emails with the sender through another communication method[6].
- ‘Multi-factor authentication enhances security’.
MFA is the next level of security because one has to input another form of verification apart from the password. Even when hackers acquire login credentials, MFA may deny access[5].
- ‘Change passwords and security software regularly’.
Password changes minimize chances of stolen credentials. Also, updated antivirus will detect and block phishing attempts[6].
Organizations:
- Regular training in cybersecurity awareness: Employees are usually the first line of defense against phishing. Training programs help them to identify suspicious emails, links, and other social engineering tactics[7].
- Implement email filtering and anti-phishing solutions: Advanced security tools can also spot phishing emails and filter them out before they even reach employees. Adding protocols for email authentication, like DMARC, SPF, and DKIM, helps reduce spoofing attempts[7].
- Monitor network activities for signs of targeted attacks: Most of the time, larger cyberattacks start with spear phishing. Any sudden activity, like repeated login attempts or unexpected data transfers, on the network needs to be acted upon immediately[8].
- Encourage your employees to immediately report suspicious e-mails: Designate a reporting process for attempted phishing so the security teams take quick action in mitigating possible threats before the damage is really done.
Conclusion:
While both phishing and spear phishing are considered high-level cybersecurity threats, spear phishing may be more threatening because it targets its victim with highly plausible deceptions. Knowing the difference between these two methods of attack, as well as practicing good security, helps place individuals and organizations in a better position to defend against such potential cyber threats. Cyber awareness and proactive mechanisms of defense remain key in trying to contain such ever-evolving threats. Organizations should work towards inculcating cybersecurity awareness among their employees to make them vigilant and adopt best practices continuously. Multi-layered security featuring artificial intelligence-driven threat detection and zero-trust security models will further ensure resilience against phishing attacks. With continuous improvement in security tactics and strategies, user education will enable a strong battle against phishing and spear phishing, reducing the potential for cyber incidents and financial loss.
References:
- Z. Alkhalil, C. Hewage, L. Nawaf, and I. Khan, “Phishing Attacks: A Recent Comprehensive Study and a New Anatomy,” Front. Comput. Sci., vol. 3, Mar. 2021, doi: 10.3389/fcomp.2021.563060.
- S. Baki and R. M. Verma, “Sixteen Years of Phishing User Studies: What Have We Learned?,” IEEE Trans. Dependable Secure Comput., vol. 20, no. 2, pp. 1200–1212, Mar. 2023, doi: 10.1109/TDSC.2022.3151103.
- “Spear-Phishing campaigns: Link Vulnerability leads to phishing attacks, Spear-Phishing electronic/UAV communication-scam targeted | IEEE Conference Publication | IEEE Xplore.” Accessed: Feb. 07, 2025. [Online]. Available: https://ieeexplore.ieee.org/abstract/document/9676394
- A. Yasin, R. Fatima, Z. JiangBin, W. Afzal, and S. Raza, “Can serious gaming tactics bolster spear-phishing and phishing resilience? : Securing the human hacking in Information Security,” Inf. Softw. Technol., vol. 170, p. 107426, Jun. 2024, doi: 10.1016/j.infsof.2024.107426.
- Z. Alkhalil, C. Hewage, L. Nawaf, and I. Khan, “Phishing Attacks: A Recent Comprehensive Study and a New Anatomy,” Front. Comput. Sci., vol. 3, Mar. 2021, doi: 10.3389/fcomp.2021.563060.
- “Avoiding the Hook: Influential Factors of Phishing Awareness Training on Click-Rates and a Data-Driven Approach to Predict Email Difficulty Perception | IEEE Journals & Magazine | IEEE Xplore.” Accessed: Feb. 07, 2025. [Online]. Available: https://ieeexplore.ieee.org/abstract/document/9893815
- O. Sarker, A. Jayatilaka, S. Haggag, C. Liu, and M. A. Babar, “A Multi-vocal Literature Review on challenges and critical success factors of phishing education, training and awareness,” J. Syst. Softw., vol. 208, p. 111899, Feb. 2024, doi: 10.1016/j.jss.2023.111899.
- “Frontiers | Phishing Attacks: A Recent Comprehensive Study and a New Anatomy.” Accessed: Feb. 07, 2025. [Online]. Available: https://www.frontiersin.org/journals/computer-science/articles/10.3389/fcomp.2021.563060/full?ref=based.inc
- Lu, J., Shen, J., Vijayakumar, P., & Gupta, B. B. (2021). Blockchain-based secure data storage protocol for sensors in the industrial internet of things. IEEE Transactions on Industrial Informatics, 18(8), 5422-5431.
- Singh, A., & Gupta, B. B. (2022). Distributed denial-of-service (DDoS) attacks and defense mechanisms in various web-enabled computing platforms: issues, challenges, and future research directions. International Journal on Semantic Web and Information Systems (IJSWIS), 18(1), 1-43.
- Navaneeth J. (2024) The Future of Cyber Defense: Machine Learning and Phishing, Insights2Techinfo, pp.1
Cite As
Bharath G. (2025) Phishing vs Spear Phishing: Understanding the Key Differences Insights2Techinfo, pp.1