By: Rishitha Chokkappagari, Department of Computer Science &Engineering, student of Computer Science & Engineering, Madanapalle Institute of Technology & Science, Angallu (517325), Andhra Pradesh. chokkappagaririshitha@gmail.com
Abstract
In the modern world where the number and sophistication of the threats are increasing, firewalls act as the first layer of protection. The following article aims at focusing on the approaches to strengthen the firewall, which can help counter highly technical cyber threats. The prime attention is paid to the enhancement of the firewall by employing fresh technologies, like AI and ML. When looking at the probability of contemporary threats, such as malware, phishing, or zero-day exploits, this article suggests the framework for firewall security. These include the process of anomaly detection, real time threat intelligence and response mechanisms based on the current threat proliferations. Moreover, we explain how firewall strength is dependent on an active update and patching policy and good user awareness. The results highlight the requirement for the multiple layer security model to employ not only the modern technology progress in the field but also further development of proactive security measures against the rising level of threats.
Keywords: firewalls, cyber risks, AI, ML, anomalous behaviour, learning security response, layered security.
Introduction
This is even more of a concern now that the world has become a global village. Thus the need to incorporate strong cybersecurity measures. Cyber threats in recent years have played significant role and continues to do so, because most of the world’s population connect to the Internet and indulge in electronic transactions. As the components of networks’ security systems, firewalls carry out the functions of protection of valuable information and preserving the stability of virtual systems. They operate under a policy referred to as the security policy, where they monitor and filter the traffic of a network based on security parameters set and can be regarded as a barrier between an organization’s local area network and the internet. To summarize, firewalls as have been discussed earlier are very important in protecting networks and systems from cyber threats but cannot do this on their own. Firewalls are still an exposed target since attackers are constantly devising on how to circumvent it, for instance, using malware, phishing, DoS and the relatively recent APTs. Hence, it is necessary to develop the manner of the firewall to prevent these new difficulties in the future adequately.
This article therefore analyses the measures and tools that enhance the contributions of firewalls in combating current threats. Continuing the above progression of thought, AI and ML can be used to deliver firewalls intelligent; pattern learning capabilities that in the presence of new threats respond in real time to the patterns of perceived deviance[1]. Likewise, the implementation of threat intelligence coupled with instant response can improve the functions of a firewall in terms of threats.
The following sections of this article will provide an overview of the current literature on firewalls, examine standard threats operating in the cyber space, and describe method of enhancing a firewalls security system. Emphasis will be placed on how individual high-tech technologies and the industry-accepted methods of security will be integrated into a comprehensive defence line. Thus, the given strategy describes all the aspects and indicates the primary objectives for inventions and creating a shield to counter unrelenting cyber threats.
- The Evolving Threat Landscape
Indeed, there has been advancement as far as the nature and severity of threats that are exercised in the online domain is concerned. The conventional approaches such as firewalls are somewhat useful in addressing the general threats. However, they are not very efficient in newer and complex threats. Common threats include:
- Malware: Any kind of software code that is designed to harm in any of the manner like corrupting the systems, stealing data or to gain an unauthorized access[2].
- Phishing: This can be defined as deceitful activities one applies, in an electro media environment, to acquire reputation of genuine intentions to obtain personal information[3].
- Denial-of-Service (DoS) Attacks: A discrete method of employing an improper large number of requests to make a definite machine or Network resource inaccessible to its expected users.
- Advanced Persistent Threats (APTs): More protracted and distant actions with focus on the acquisition of data or an act of spying against specific organizations.
These threats have given an implication that it is inevitable to grow and sharpen the firewalls to achieve the maximum protection level. [4]
- Enhancing Firewall Protection
Hence the new and constantly evolving complicated threats must be combatted by the firewall protection which requires that it be complex and layered. Key strategies include:
Figure process of enhancing firewall protection
- Integration of AI and ML: AI and Machine learning has the capacity to advance the possibility of any firewall system that is in use. They can sift through immense data transiting through networks on the lookout for trace of would-be cyber incidences. This makes it possible to get to the active threats’ identification and elimination rather than behaving hysterically and holding a brochure with rules.
- Real-Time Threat Intelligence: Real threat intelligence feed in firewalls ensures that the firewall is equipped with updated information threat. This in turn helps nowadays to respond to the new attack methods as fast and efficiently as it is required by the threat.
- Anomaly Detection: AIDS conducts a look-up within the network traffic since it will always be in a different form if there is an intrusion. Such kind of anomalies are better detected to fight with the attacks from other computers and this is made by the firewalls as they prevent the huge losses.
Multi-Layered Security Approach
The protection strategy with a firewall should include several barriers with the help of superior technologies and, primarily, attention to the security options[5]. Thus, it enhances the concept of security in its broad sense because it provides various aspects of guarding the computer system from cyber menace. Key components of this approach include:
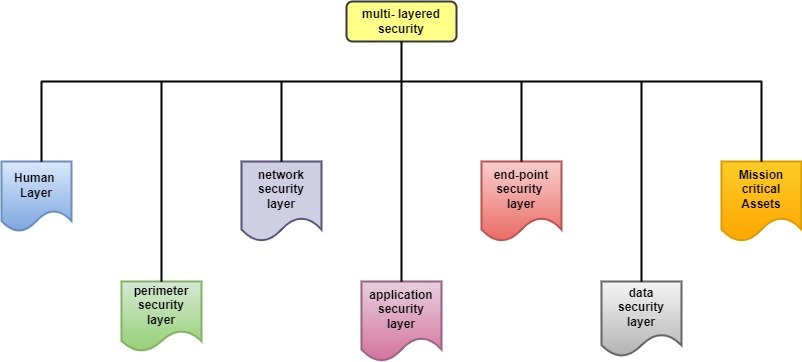
Network Segmentation
Network segmentation can be described as the process of partitioning a network into several parts or sector or other smaller sub networks. This hampers the transfer of an attack and restricts the kind of damage as regardless of how a particular portion of the company network has been penetrated, the attacker is unable to move on to the other segment of the same network.
These entrances cannot transfer to a new region on their own, thus the segmentation has a way of restraining an attacker in the region it penetrates, irrespective of the sphere it enters. It provides improved performance. Improved Performance is because by partitioning a given network it becomes easy to control traffic within a given partition and therefore increase the kinetics of traffic and other performances of the network if any. Each segment can decide on the amount of security they require and the level at which they would want it to be held at.
Virtual Local Area Networks (VLANs): At the campus level, the network physical design must be logically split through VLANs.
Subnets: Subnet each part of the network with another independent IP address schema.
Access Control Lists (ACLs): Communication can only be done that which is allowed and therefore ACL’s that cover the segments must be put in place.
This comes as an essential realization that applies the specific approach it also applies the unspecific approach and through this, there has been an improvement of the protection measures.
Intrusion Detection and Prevention Systems (IDPS)
IDSs are constitutive components and work together with firewalls to detect invasions and Sieges. These systems oversee operations in local communication and system for unlawful or prohibited behaviour. It Keeps attacks through the traffic analysis in which the traffic is compared with certain attack patterns or through statistical means.
It responds to threats that it has categorized to consist of and may perform such functions as sending out messages of caution or even dropping the said packets. Also helps alters to inform the security officers of any possible security threats for follow up.
Data Encryption
Encryption is the process of transforming the normal readable form data into an encoded form which the characters and privilege of anyone who intercepted the past message or data or stored during passing or used it in any other way can readily decipher unless he or she has the decryption code. In this manner, it is possible to eliminate one’s access to data even if he has managed to penetrate the data domain.
Conclusion
Thus, it is possible to state that the nature of threats in cyber space is rather dynamic and requires constant evolutions in its turn, firewall protection needs to be more instrumental and non-monotonous. The conventional firewalls remain critical to the security of the networks even as they need to step up to scalable threats to achieve the intended results. This paper has thus emphasized on the need to adopt new technologies like AI and ML to improve the sophistication and dynamism of firewalls. Thus, applying AI and ML to the firewalls will allow them to transgress from static rules used for protection to intelligent threat identification and action plans. Technologies, which allow the detection of the abnormalities, the ultra-fast searching through the TBs of contents, and self-organized defence mechanism, thus enhancing the firewall’s effectiveness of defence against the attackers in a rampant way. Also, periodic feeding of threat intelligence feeds into firewalls guarantees that firewalls are always enriched with the latest threats knowledge that will enhance their setting responses to threats.
Furthermore, cloning site’s firewall protection should address update and patch issues and educate users concerning the same. Another way of advancing a security feature in addressing risks is making sure that software and hardware working as firewalls have the most recent security update. In this context, informing users of the Website about secure use of Internet and existent risks is another significant part of strengthening the security layer. The threats are only going to increase in nature over the year and so will the defences have to. With the help of utilizing AI and ML, updating systems’ software, and constantly increasing awareness within the company, organizations take their firewall protection to a new level and protect their precious data from the unending waves of cyber threats.
References
- K. Thakur, M. Qiu, K. Gai, and M. L. Ali, “An Investigation on Cyber Security Threats and Security Models,” in 2015 IEEE 2nd International Conference on Cyber Security and Cloud Computing, Nov. 2015, pp. 307–311. doi: 10.1109/CSCloud.2015.71.
- D. G. Jakka, N. Yathiraju, and D. M. F. Ansari, “Artificial Intelligence in Terms of Spotting Malware and Delivering Cyber Risk Management,” J. Posit. Sch. Psychol., vol. 6, no. 3, Art. no. 3, Apr. 2022.
- L. Burita, P. Matoulek, K. Halouzka, P. Kozak, and Department of Informatics and Cyber Operations, University of Defence, 65 Kounicova Street, 66210 Brno, Czech Republic, “Analysis of phishing emails,” AIMS Electron. Electr. Eng., vol. 5, no. 1, pp. 93–116, 2021, doi: 10.3934/electreng.2021006.
- P. Pappachan, Sreerakuvandana, and M. Rahaman, “Conceptualising the Role of Intellectual Property and Ethical Behaviour in Artificial Intelligence,” in Handbook of Research on AI and ML for Intelligent Machines and Systems, IGI Global, 2024, pp. 1–26. doi: 10.4018/978-1-6684-9999-3.ch001.
- J. Alves-Foss, C. Taylor, and P. Oman, “A multi-layered approach to security in high assurance systems,” in 37th Annual Hawaii International Conference on System Sciences, 2004. Proceedings of the, Jan. 2004, p. 10 pp.-. doi: 10.1109/HICSS.2004.1265709.
- Aldweesh, A., Alauthman, M., Al Khaldy, M., Ishtaiwi, A., Al-Qerem, A., Almoman, A., & Gupta, B. B. (2023). The meta-fusion: A cloud-integrated study on blockchain technology enabling secure and efficient virtual worlds. International Journal of Cloud Applications and Computing (IJCAC), 13(1), 1-24.
- M. Casillo, F. Colace, B. B. Gupta, A. Lorusso, F. Marongiu and D. Santaniello, “Blockchain and NFT: a novel approach to support BIM and Architectural Design,” 2022 International Conference on Innovation and Intelligence for Informatics, Computing, and Technologies (3ICT), Sakheer, Bahrain, 2022, pp. 616-620, doi: 10.1109/3ICT56508.2022.9990815.
Cite As
Chokkappagari R (2024) Protection of Firewall against Cyber Threats, Insights2Techinfo, pp.1